2014-10-07 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-07-email-tracker.csv.zip
- 2014-10-07-running-the-malware-in-a-VM.pcap.zip
- 2014-10-07-malware-samples.zip
NOTES:
- This one has characteristics of an Asprox botnet email:
- The URL for downloading the zip file has the same pattern I've noticed in other Asrpox botnet emails (see below).
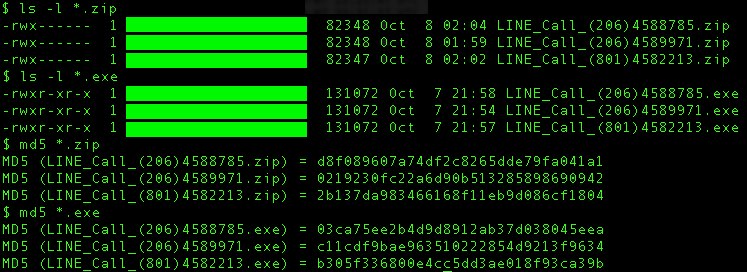
- The same URL gave different file names when I downloaded it by proxying through different IP addresses:
- Those different file names have different file hashes for what's really the same malware:
- Post-infection traffic from the infected VM is similar to some of the traffic I've seen before with malware from Asprox botnet emails.
- A good description of recent Asprox botnet meail activity can be found at: https://stopmalvertising.com/malware-reports/asprox-update-version-2050.html
- I've included a spreadsheet listing the dates, times, and senders on 494 emails with the same subject line. This particular wave of emails started on Thursday, 2014-10-02.
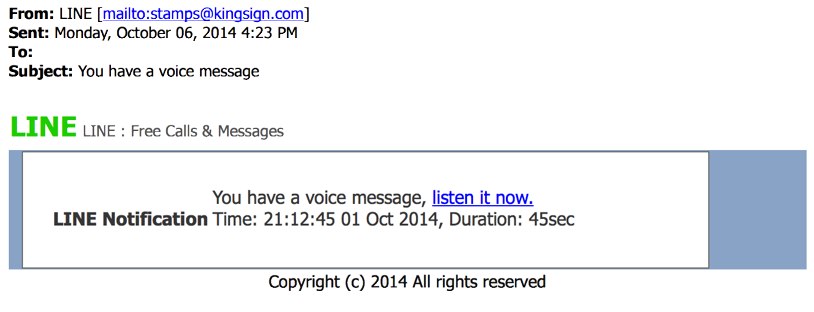
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: LINE <stamps@kingsign[.]com>
Sent: Monday, October 06, 2014 4:23 PM
To:
Subject: You have a voice message
LINE LINE: Free Calls & Messages
You have a voice message, listen it now
LINE NOTIFICATION Time: 21:12:45 01 Oct 2014, Duration: 45sec
Coypright (c) 2014 All rights reserved
PRELIMINARY MALWARE ANALYSIS
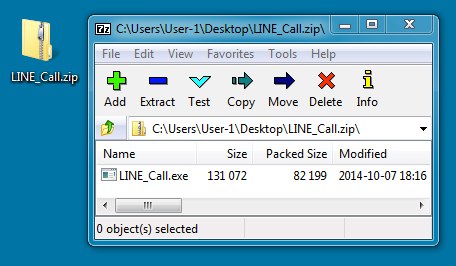
EMAIL ATTACHMENT:
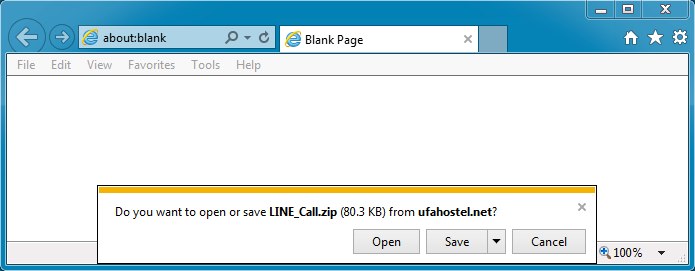
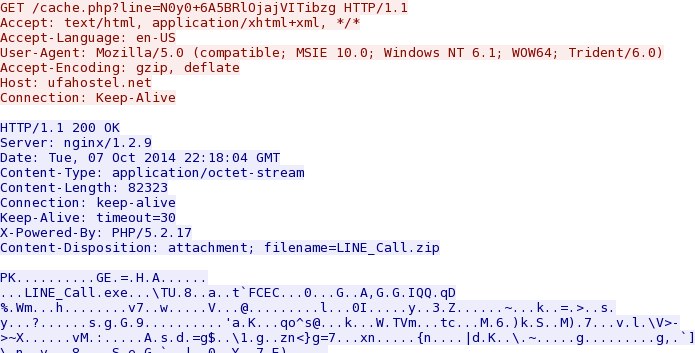
File name: LINE_Call.zip
File size: 82,323 bytes
MD5 hash: 92d86a4847988aad3eaef5d609308c97
Detection ratio: 5 / 55
First submission: 2014-10-07 23:18:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/7929c2c9b585ef354bcd5e89a8ddc0fda68254b6bcfb6b6e5f08d4233e023a63/analysis/
EXTRACTED MALWARE:
File name: LINE_Call.exe
File size: 131,072 bytes
MD5 hash: 68edcf990db2e27af7d0f42abf8740ba
Detection ratio: 5 / 54
First submission: 2014-10-07 23:18:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/e4ac9107b13fed461776035c4e7abf99b95f6d6eec4ce813804118168e96dc70/analysis/
INFECTION TRAFFIC
DOWNLOADING AND EXECUTING THE MALWARE ON A VM:
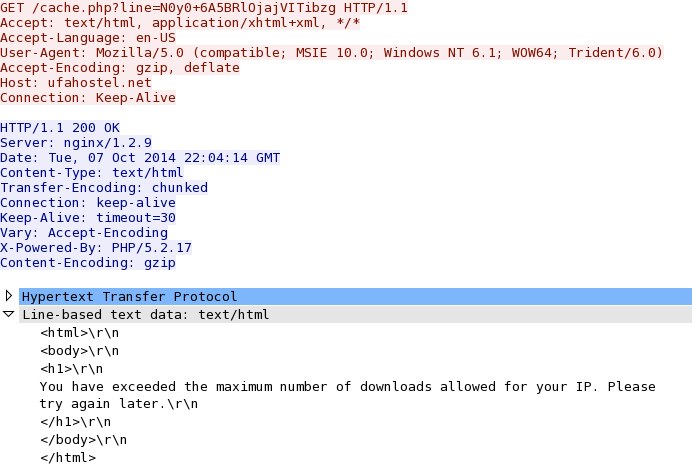
- 2014-10-07 22:21:47 UTC - 5.101.153[.]13:80 - ufahostel[.]net - GET /cache.php?line=N0y0+6A5BRlOjajVITibzg
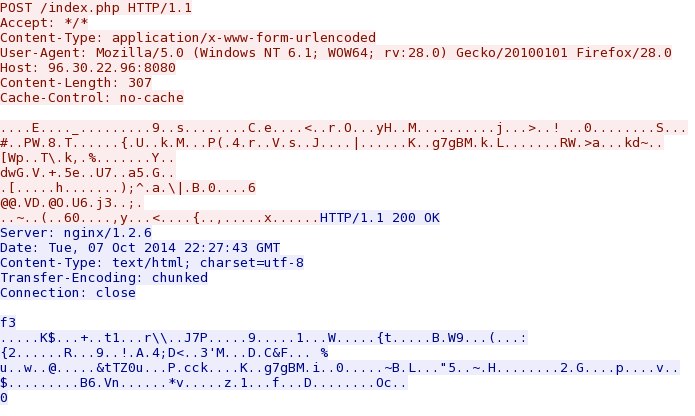
- 2014-10-07 22:31:27 UTC - 96.30.22[.]96:8080 - 96.30.22[.]96:8080 - POST /index.php
SNORT EVENTS FROM VM INFECTION

Emerging Threats events from Sguil on Security Onion:
- 2014-10-07 22:21:54 UTC - 5.101.153[.]13:80 - ET POLICY ZIPPED EXE in transit (sid:2001404)
- 2014-10-07 22:31:27 UTC - 96.30.22[.]96:8080 - ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
- 2014-10-07 22:31:27 UTC - 96.30.22[.]96:8080 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 2 (sid:2018359)
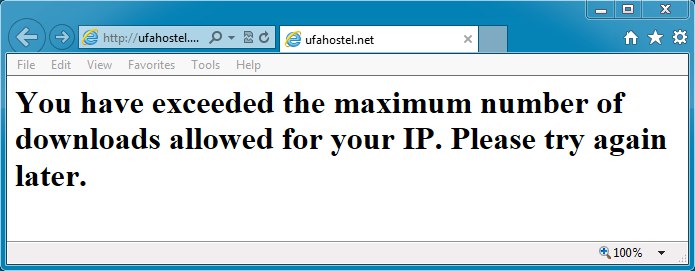
SCREENSHOTS FROM THE TRAFFIC
When you try the link, and it doesn't like your source IP address, you get the following message:
I got this one by proxying through a Canadian IP address:
Kuluoz/Asprox-style callback traffic from the infected VM:
Click here to return to the main page.