2015-01-21 - UPATRE/DYRE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
DATA ON EMAILS PUSING UPATRE/DYRE:
- Began: 2015-01-21 12:43 UTC
- Ended: 2015-01-21 13:21 UTC
- Duration: 38 minutes
- From: no-replay@invoice[.]com
- Subject: Employee Documents - Internal Use
EXAMPLE
MESSAGE TEXT:
From: invoice <no-replay@invoice[.]com>
Sent: Wednesday, January 21, 2015 6:43 AM CST
To: [redacted]
Subject: Employee Documents - Internal Use
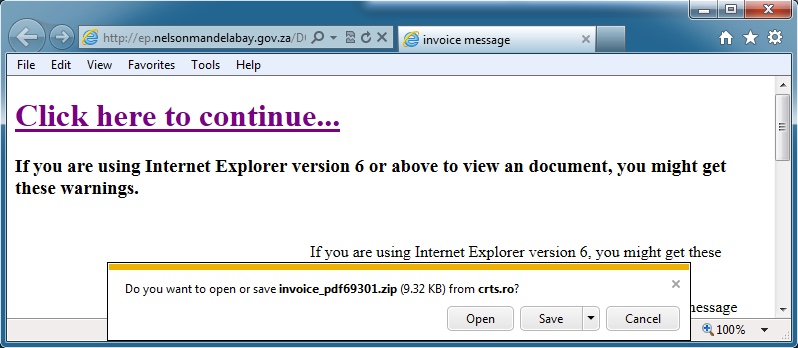
DOCUMENT NOTIFICATION, Powered by NetDocuments
DOCUMENT NAME: Employee Documents
DOCUMENT LINK: hxxp[:]//ep.nelsonmandelabay[.]gov[.]za/DOCUMENT~STORAGE_DATA/get.last_invoice.html
Documents are encrypted in transit and store in a secure repository
---------------------------------------------------------------------------------
This message may contain information that is privileged and confidential.
If you received this transmission in error, please notify the sender by reply email and delete the message and any attachments.
FOLLOWING THE LINK:
INFECTION TRAFFIC
CLICKING ON LINK FROM THE EMAIL:
- 2015-01-21 15:46:19 UTC - 41.191.89[.]2 port 80 - ep.nelsonmandelabay[.]gov[.]za - GET /DOCUMENT~STORAGE_DATA/get.last_invoice.html
- 2015-01-21 15:46:19 UTC - 50.87.63[.]202 port 80 - afreshperspective[.]com - GET /js/jquery-1.41.15.js
- 2015-01-21 15:46:19 UTC - 92.60.66[.]184 port 80 - imisnc[.]it - GET /js/jquery-1.41.15.js
- 2015-01-21 15:46:19 UTC - 216.113.194[.]26 port 80 - www.rosewoodmanor[.]org - GET /js/jquery-1.41.15.js
- 2015-01-21 15:46:19 UTC - 89.42.216[.]133 port 80 - crts[.]ro - GET /js/jquery-1.41.15.js
- 2015-01-21 15:46:28 UTC - 41.191.89[.]2 port 80 - ep.nelsonmandelabay[.]gov[.]za - GET /favicon.ico
- 2015-01-21 15:46:28 UTC - 89.42.216[.]133 port 80 - crts[.]ro - GET /js/jquery-1.41.15.js?aCNDrnl3=[user-agent string]&hjmcSOLrVb5fK5a=1846&
kZuJV1OyPrXdK0=1267859342&OjyOcmABhJHuu=gDyC5hx734Wu1.js - 2015-01-21 15:46:30 UTC - 41.191.89[.]2 port 80 - ep.nelsonmandelabay[.]gov[.]za - GET /DOCUMENT~STORAGE_DATA/ie_top.gif
- 2015-01-21 15:46:30 UTC - 89.42.216[.]133 port 80 - crts[.]ro - GET /js/jquery-1.41.15.js?get_message=3290013886
RUNNING THE DOWNLOADED MALWARE ON A VM:
- 2015-01-21 15:50:03 UTC - 202.153.35[.]133 port 44141 - 202.153.35[.]133:44141 - GET /2101uk22/WIN-BS4EUJ1KO34/0/61-SP1/0/
- 2015-01-21 15:50:04 UTC - 202.153.35[.]133 port 44141 - 202.153.35[.]133:44141 - GET /2101uk22/WIN-BS4EUJ1KO34/1/0/0/
- 2015-01-21 15:50:05 UTC - 209.235.144[.]9 port 80 - dipford[.]com - GET /mandoc/info22.pdf
- 2015-01-21 15:50:09 UTC - 202.153.35[.]133 port 44161 - 202.153.35[.]133:44161 - GET /2101uk22/WIN-BS4EUJ1KO34/41/7/4/
- 2015-01-21 15:50:19 UTC - 173.194.73[.]127 port 19302 - UDP STUN traffic to stun1.l.google[.]com
- 2015-01-21 15:50:27 UTC - 50.7.245[.]130 port 443 - encrypted SSL session
- 2015-01-21 15:50:58 UTC - 91.185.239[.]153 port 443 - encrypted SSL sessions
- 2015-01-21 15:51:14 UTC - 86.106.30[.]102 port 80 - utokatalin[.]ro - GET /administrator/ml2from2.tar
- 2015-01-21 15:51:15 UTC - 176.114.0[.]58 port 1025 - encrypted SSL session
- 2015-01-21 15:51:46 UTC - 93.190.137[.]149 port 443 - encrypted SSL sessions
ALERTS FROM SANDBOX ANALYSIS
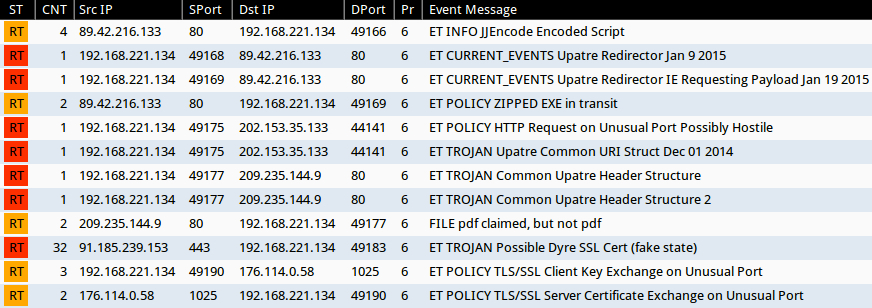
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 89.42.216[.]133 port 80 - ET CURRENT_EVENTS Upatre Redirector Jan 9 2015 (sid:2020159)
- 89.42.216[.]133 port 80 - ET CURRENT_EVENTS Upatre Redirector IE Requesting Payload Jan 19 2015 (sid:2020212)
- 202.153.35[.]133 port 44141 - ET TROJAN Upatre Common URI Struct Dec 01 2014 (sid:2019847)
- 209.235.144[.]9 port 80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 209.235.144[.]9 port 80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 91.185.239[.]153 port 443 - ET TROJAN Possible Dyre SSL Cert (fake state) (sid:2019833)
Sourcefire VRT/Talos ruleset from Snort 2.9.7.0 on Debian 7 (not counting preprocessor events):
- 89.42.216[.]133 port 80 - [1:27875:3] EXPLOIT-KIT Javascript obfuscation technique - has been observed in Rmayana/DotkaChef/DotCache exploit kit (x2)
- 202.153.35[.]133 port 44141 - [1:33146:1] MALWARE-CNC Win.Trojan.Upatre variant outbound connection
PRELIMINARY MALWARE ANALYSIS
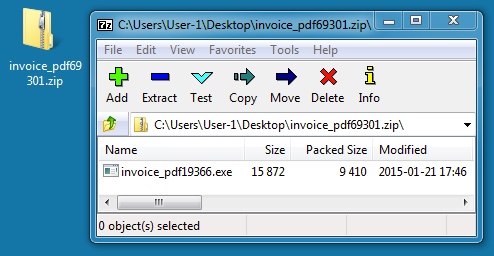
ZIP FILE FROM LINK:
File name: invoice_pdf69301.zip
File size: 9,548 bytes
MD5 hash: 0bdf685d380e5550bf13ae9f6cdd154f
Detection ratio: 8 / 55
First submission: 2015-01-21 18:09:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/5d317f6cc8d7af18c57ff4fa13c6cad2b40ced075b833c8b548ec1bec6bc80c9/analysis/
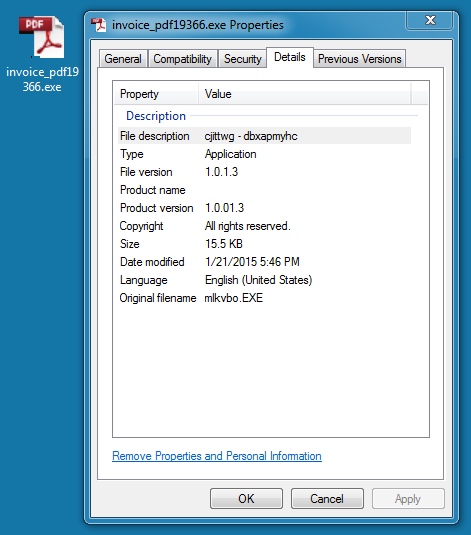
EXTRACTED MALWARE - UPATRE:
File name: invoice_pdf19366.exe
File size: 115,872 bytes
MD5 hash: 706378854efad81d13203303161f41cf
Detection ratio: 8 / 49
First submission: 2015-01-21 18:10:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/6f8cf43e41ca954b99fcd45ad878e168bd76d3764b7c87cbe28656d8ce2edf78/analysis/
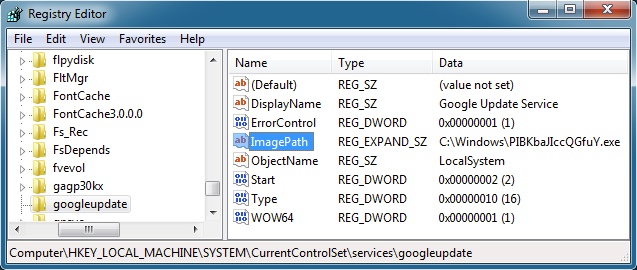
DROPPED MALWARE ON INFECTED VM (1 OF 2) - DYRE:
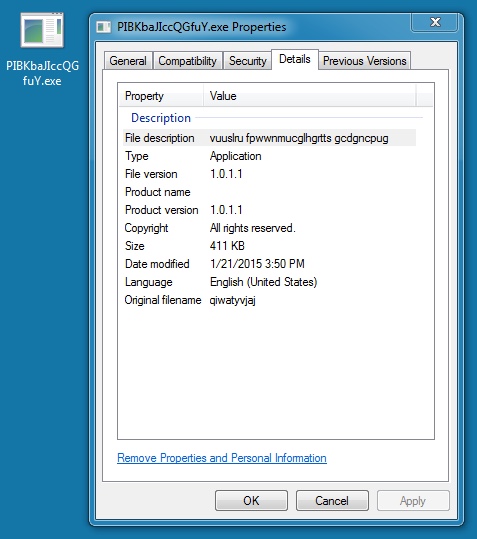
File name: C:\Windows\PIBKbaJIccQGfuY.exe
File size: 420,864 bytes
MD5 hash: ed74d93a7507471879385205fe92dd3c
Detection ratio: 4 / 56
First submission: 2015-01-21 13:32:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/e21a3d32dfc55ff70d1241defdbc36b6c65bcdda4b14c2ceabfaf25f68f35c07/analysis/
DROPPED MALWARE ON INFECTED VM (2 OF 2) - DYRE-RELATED:
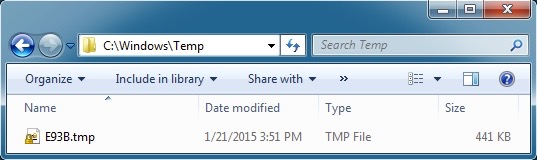
File name: C:\Windows\Temp\E93B.tmp
File size: 451,584 bytes
MD5 hash: 4df95e133ed489ef4f0736eabb16ba2e
Detection ratio: 20 / 54
First submission: 2015-01-21 16:41:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/51d2a9844f0aa605bcfa13ad2fd1679939d5b4accf18a8d2f55168f4f625ccd6/analysis/
Click here to return to the main page.