2015-02-03 - GUEST BLOG ENTRY BY JACK MOTT - MALSPAM - SUBJECT: INVOICE FROM LIBERTY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-02-03-Word-document-run-on-VM.pcap.zip 593.8 kB (593,843 bytes)
- 2015-02-03-Chanitor-sample-run-on-a-physical-host.pcap.zip 81.2 kB (81,241 bytes)
NOTES:
- This blog post was submitted by Jack Mott, an information security analyst in based in Denver, Colorado (United States).
- Jack would like to thank to Francis Trudeau for his assistance on the analysis.
- I've done some formatting, made editorial changes, and ensured the pcaps were sanitized.
- The downloaded executable is called either "Chanitor" or "Chaintor" (I've seen both). From what I understand, this sample is supposed to install Vawtrak.
MALSPAM DETAILS
Date/Time range: 2015-02-02 from 09:12 to 11:36 UTC
Observed Subjects:
- Invoice from Liberty
- Invoice
- Invoice from Liberty CFS NV, Inc.
Observed attachments: invoice[10 random digits].doc/.docm
Observed Senders:
- freshh@gator2025.hostgator[.]com
- marcodd@gator3080.hostgator[.]com
- dopewoit@melkus.websitewelcome[.]com
- nycwaite@gator3140.hostgator[.]com
- v8gra678@br262.hostgator[.]com.br
- invoice@libertycfs[.]com
- khamyai@khamyaiubon[.]go[.]th
- wwwcabin@falcon.websitewelcome[.]com
- sdco@patriot.websitewelcome[.]com
- cupidelf@gator3057.hostgator[.]com
- tanyadil@dime106.dizinc[.]com
- phumi@gator2017.hostgator[.]com
- jmdubhye@splinter.aserv[.]co[.]za
- wwwcabin@falcon.websitewelcome[.]com
- incline1@gator4049.hostgator[.]com
- bestdiet@ip-50-62-74-28.ip.secureserver[.]net
- victoria@gator3299.hostgator[.]com
- mrhhosting@gmail[.]com
- tshear@gator3092.hostgator[.]com
- webdsgn3@gator3154.hostgator[.]com
- ecps@gator2010.hostgator[.]com
EMAIL SCREENSHOT:
EMAIL TEXT:
Dear XXXX XXXX
Your paid invoice is attached.
Thank you for your business - we appreciate it very much.
Sincerely,
Liberty CFS NV, Inc.
TRAFFIC FROM INFECTED VM
- 2015-02-03 00:57:16 UTC - 1.1.2[.]2 - ICMP Echo Request
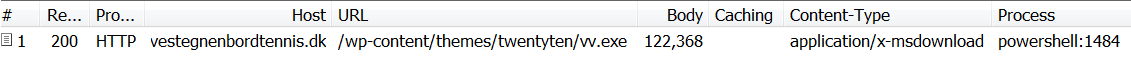
- 2015-02-03 00:57:30 UTC - 31.193.237[.]133 - vestegnenbordtennis[.]dk - GET /wp-content/themes/twentyten/vv.exe (download from .doc)
- 2015-02-03 00:58:22 UTC - 54.225.211[.]214 - HTTPS traffic to: api.ipify[.]org
- 2015-02-03 00:58:23 UTC - 23.3.68[.]208 - download.windowsupdate[.]com - GET /msdownload/update/v3/static/trustedr/en/authrootstl.cab
- 2015-02-03 00:58:26 UTC - 38.229.70[.]4 - HTTPS traffic to: o3qz25zwu4or5mak.tor2web[.]org
SNORT EVENTS
Signature hits from the Emerging Threats and ETPRO rulesets:
- ETPRO TROJAN Win32/Chanitor.A .onion Proxy domain lookup [**] [Classification: A Network Trojan was Detected] [Priority: 1] {UDP}
- ETPRO TROJAN Win32/Chanitor.A .onion Proxy domain lookup [**] [Classification: A Network Trojan was Detected] [Priority: 1] {UDP}
- ET POLICY Possible IP Check api.ipify[.]org [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 54.225.211[.]214 port 443
- ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) [**] [Classification: A Network Trojan was Detected] [Priority: 1] {TCP} 194.150.168[.]70 port 443
- ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) [**] [Classification: A Network Trojan was Detected] [Priority: 1] {TCP} 194.150.168[.]70 port 443
- ET POLICY Possible IP Check api.ipify.org [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 54.235.186[.]52 port 443
- ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) [**] [Classification: A Network Trojan was Detected] [Priority: 1] {TCP} 194.150.168[.]70 port 443
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: invoice7040125066.doc
File size: 38.5 KB (39,489 bytes)
MD5 hash: cd5fdb7574010fd23f9501523fdc2aa4
Detection ratio: 15 / 56
First submission: 2015-02-02 16:43:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/386990fb92835fdcf1c6e9c0bfdf04cf6b23ac16ba89e0a1a03d5ef001f34756/analysis/
NOTES:
- The word document uses Powershell to call and download the first stage malware.
- Attempt at actual interaction/tricking user--Question marks become text after enabling macros.
Document before running the Macro, enticing users to click to reveal actual content:
Document after enabling Macros, which reveals the "content" and leads users to believe the attachment is legitimate.
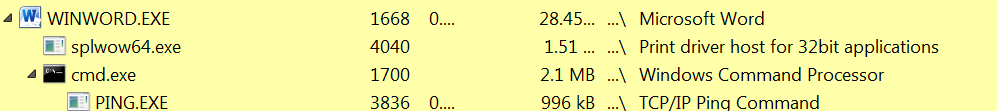
The malicious Word document first spawns cmd and uses ping.exe to test connectivity. Once successful, it then spawns cscript.exe to run a PowerShell instance to download the first stage malware (vv.exe / winlogin.exe / 444.exe).
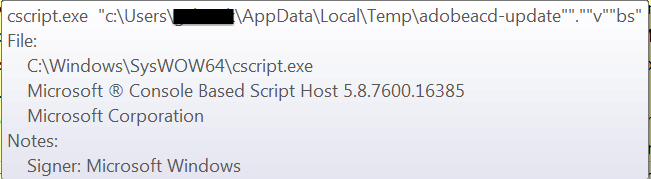
Observed cscript.exe command: cscript.exe "c:\Users\[username]\AppData\Local\Temp\adobeacd-update.vbs"
Observed PowerShell command: powershell.exe -noexit -ExecutionPolicy bypass -noprofile -file C:\Users\[username]\AppData\Local\Temp\adobeacd-update.ps1
MALWARE PAYLOAD:
File name: C:\Users\[username]\AppData\Roaming\Windows\winlogin.exe
File size: 119.5 KB ( 122368 bytes )
MD5 hash: 235b02e0d243e7bdebefe68d6a0ec8ec
Detection ratio: 28 / 56
First submission: 2015-02-02 16:49:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/4c78b0b7e26f32b6a1b59ea4aa2a9ba7d46471ec99bff3adf724a0c66a2ea2d4/analysis/
Click here to return to the main page.