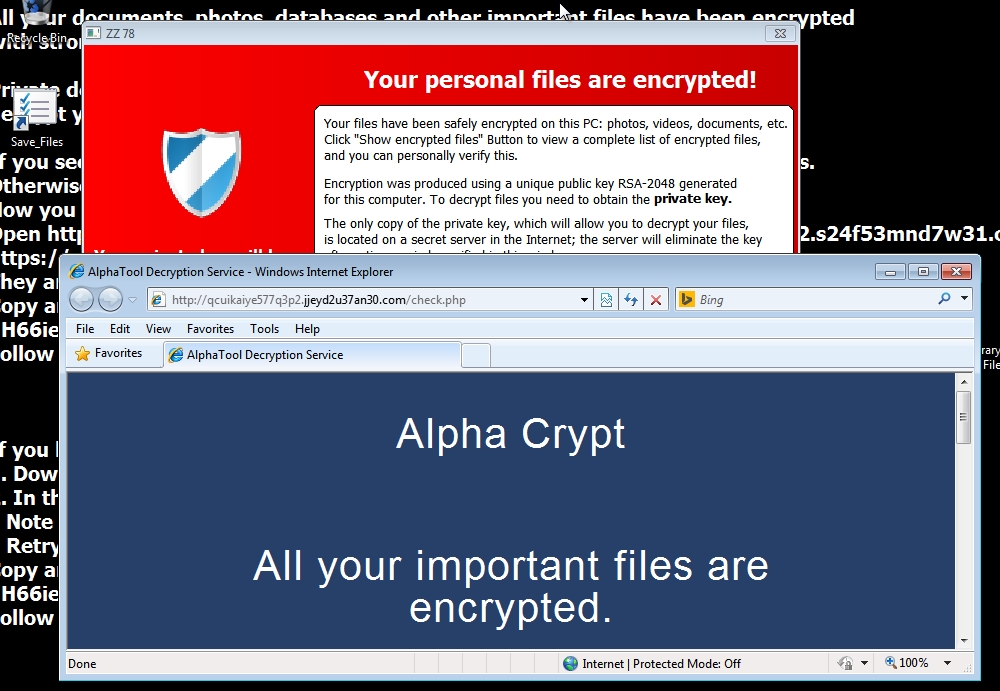
2015-04-30 - ANGLER EK SENDS ALPHA CRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-04-30-Angler-EK-sends-Alpha-Crypt-ransomware.pcap.zip
- 2015-04-30-Angler-EK-malware-and-Alpha-Crypt-ransomware-files.zip
NOTES:
- This "Alpha Crypt" ransomware appears to be another CryptoLocker clone.
- Bitcoin address for ransomware payment is: 1H66iejHkDY9SZJRrFrnhLjHff6MRMhKu6
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.162.78[.]253 port 80 - portcullisesposturen.europartsplus[.]org - Angler EK
- port 80 - ipinfo[.]io - IP address check by the malware
- 104.28.28[.]165 port 80 - dpckd2ftmf7lelsa.jjeyd2u37an30[.]com - Alpha Crypt ransowmare post-infection traffic
- 104.28.29[.]165 port 80 - qcuikaiye577q3p2.jjeyd2u37an30[.]com - Alpha Crypt ransowmare post-infection traffic
ANGLER EK:
- 2015-04-29 23:52:23 UTC - portcullisesposturen.europartsplus[.]org - GET /gels-contrariness-domain-punchable/548828415920276748
- 2015-04-29 23:52:26 UTC - portcullisesposturen.europartsplus[.]org - GET /IMvOBBZKDLqAJYIDe02t5hMMNyzBLN_q4kafJkVNqJVTnTmd
- 2015-04-29 23:52:27 UTC - portcullisesposturen.europartsplus[.]org - GET /UX7n1YkbNn8FUV6QVtEZLj-p-gLvRKlWEWmz3r7Ug8suRiY_
- 2015-04-29 23:54:22 UTC - portcullisesposturen.europartsplus[.]org - GET /rMvYNVG0kPLtf29am1rkzlKZn-_zPrF1o4yOMiFuI5p3EATZ
POST-INFECTION TRAFFIC:
- 2015-04-29 23:52:33 UTC - ipinfo[.]io - GET /ip
- 2015-04-29 23:52:33 UTC - dpckd2ftmf7lelsa.jjeyd2u37an30[.]com - GET /tsdfewr2.php?U3ViamVjdD1QaW5nJmtleT0y[long string of characters]
- 2015-04-29 23:53:14 UTC - dpckd2ftmf7lelsa.jjeyd2u37an30[.]com - GET /tsdfewr2.php?U3ViamVjdD1DcnlwdGVkJmtl[long string of characters]
- 2015-04-30 00:27:03 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /?enc=1H66iejHkDY9SZJRrFrnhLjHff6MRMhKu6
- 2015-04-30 00:27:04 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /check.php
- 2015-04-30 00:27:05 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /style.css
- 2015-04-30 00:27:06 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /img/curr.svg
- 2015-04-30 00:27:06 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /img/decrypt.svg
- 2015-04-30 00:27:08 UTC - qcuikaiye577q3p2.jjeyd2u37an30[.]com - GET /favicon.ico
ALERTS
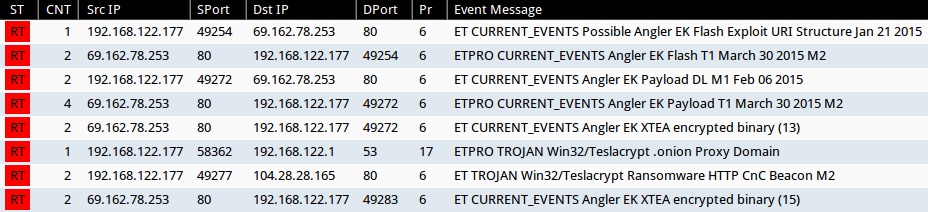
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 69.162.78[.]253 port 80 - ET CURRENT_EVENTS Possible Angler EK Flash Exploit URI Structure Jan 21 2015 (sid:2020234)
- 69.162.78[.]253 port 80 - ETPRO CURRENT_EVENTS Angler EK Flash T1 March 30 2015 M2 (sid:2810330)
- 69.162.78[.]253 port 80 - ET CURRENT_EVENTS Angler EK Payload DL M1 Feb 06 2015 (sid:2020385)
- 69.162.78[.]253 port 80 - ETPRO CURRENT_EVENTS Angler EK Payload T1 March 30 2015 M2 (sid:2810333)
- 69.162.78[.]253 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (13) (sid:2020592)
- DNS query for dpckd2ftmf7lelsa.jjeyd2u37an30[.]com - ETPRO TROJAN Win32/Teslacrypt .onion Proxy Domain (sid:2810820)
- 69.162.78[.]253 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (15) (sid:2020594)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.2 on Debian 7:
- 69.162.78[.]253 port 80 - [1:33182:1] EXPLOIT-KIT Angler exploit kit outbound Adobe Flash request
- 69.162.78[.]253 port 80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- ping to 104.41.150[.]68 - [1:29456:2] PROTOCOL-ICMP Unusual PING detected
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-04-30-Angler-EK-Flash-exploit.swf
File size: 55,255 bytes
MD5 hash: 7d876df50581deb711df9af0029f64e4
Detection ratio: 2 / 57
First submission to VirusTotal: 2015-04-29 16:07:35 UTC<
MALWARE PAYLOAD (ALPHA CRYPT RANSOMWARE):
File name: 2015-04-30-Angler-EK-payload-Alpha-Crypt-ransomware.exe
File size: 420,864 bytes
MD5 hash: 1c71d29bede55f34c9b17e24bd6a2a31
Detection ratio: 5 / 57
First submission to VirusTotal: 2015-04-30 00:40:49 UTC
Click here to return to the main page.