2015-08-06 - ADWIND INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-08-06-Adwind-infection-traffic.pcap.zip
- 2015-08-06-adwind-email-tracker.csv.zip
- 2015-08-06-emails-pushing-Adwind-11-examples.zip
- 2015-08-06-Adwind-JAR-files-10-samples.zip
- 2015-08-06-Adwind-infection-additional-artifacts.zip
NOTES:
Since about mid-July 2015, I've noticed an increase of malicious spam (malspam) with Adwind-based malware as .jar (Java archive) attachments. More info on Adwind (also known as Unrecom) can be found here and here.
I did some digging for the past 10 days and came up with 10 malware samples and several email examples for today's blog entry.
DETAILS
Here's what I found for the last 10 days since 2015-07-27 for Adwind malspam:
[ READ: Date/Time received -- Sender -- Subject -- Attachment ]
- 2015-07-27 16:58 CDT -- noreply@googlemail[.]com -- Purchasing order -- PURCHASING Order.jar
- 2015-07-28 09:50 CDT -- noreply@googlemail[.]com -- Purchasing order -- PURCHASING Order.jar
- 2015-07-29 02:23 CDT -- noreply@googlemail[.]com -- Purchasing order -- PURCHASING Order.jar
- 2015-07-30 11:12 CDT -- sales.qnijewels@gmail[.]com -- Fwd: Outstanding Invoices -- SOA AS OF JUly.jar
- 2015-07-30 11:29 CDT -- sales.qnijewels@gmail[.]com -- Fwd: Outstanding Invoices -- SOA AS OF JUly.jar
- 2015-07-30 11:52 CDT -- sales.qnijewels@gmail[.]com -- Fwd: Outstanding Invoices -- SOA AS OF JUly.jar
- 2015-07-30 12:02 CDT -- sales.qnijewels@gmail[.]com -- Fwd: Outstanding Invoices -- SOA AS OF JUly.jar
- 2015-07-30 19:16 CDT -- a.macesic@inspectorate-croatia[.]hr -- Scanned DUC-Invoice -- Invoice.jar
- 2015-07-31 00:20 CDT -- andrea@intl.westernunion[.]com -- Wupos Update -- Wupos_update_0940002TT12212.jar
- 2015-07-31 01:30 CDT -- andrea@intl.westernunion[.]com -- Wupos Update -- Wupos_update_0940002TT12212.jar
- 2015-07-31 18:41 CDT -- office@regcon-asia[.]kz -- Find the swift copy for the balance payment !! -- payment.invoice.1.jar
- 2015-08-03 03:07 CDT -- noreply@googlemail[.]com -- Purchasing Order -- Purchasing Order..jar
- 2015-08-03 06:26 CDT -- top@jviincentthailand[.]com -- Re: PO 6785435 30-08-2015 -- PO 6785435 30-08-2015 PDF.jar
- 2015-08-03 11:03 CDT -- top@jviincentthailand[.]com -- Re: PO 6785435 30-08-2015 -- PO 6785435 30-08-2015 PDF.jar
- 2015-08-03 16:31 CDT -- top@jviincentthailand[.]com -- Re: PO 6785435 30-08-2015 -- PO 6785435 30-08-2015 PDF.jar
- 2015-08-06 02:17 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 02:57 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 03:09 CDT -- info@al-rddadi[.]com[.]sa -- Re: Payment Processed. -- PI-Invoice-0972-DUC.jar
- 2015-08-06 04:35 CDT -- sales11@laurence-chocolate[.]gr -- Re: Enquiry -- P.O_001_UST-TRADE.jar
- 2015-08-06 04:44 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:46 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:47 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:52 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:55 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:56 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 04:59 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:04 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:37 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:39 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:41 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:42 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 05:49 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:07 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:12 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:12 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:14 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:21 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:24 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:30 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:31 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:33 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-06 06:34 CDT -- vinita.sharma@frrforex[.]in -- Re: P.0 18003. -- P.O_18003.jar
Here's a list of the 10 adwind samples I found, sorted by MD5 hash:
- 15afefd6bd1cb68909023ebe272f909c - PURCHASING Order.jar
- 1aaf890bb3b089ac8ec06bcacf47f247 - PI-Invoice-0972-DUC.jar
- 30331dfb853757e82a1c6d0cdb76c6c9 - Wupos_update_0940002TT12212.jar
- 3743cdf0878c5a804251d71dd940cbb2 - Purchasing Order..jar
- 9d0a2a943af15d84dd8068888d000db9 - SOA AS OF JUly.jar
- be3e67412e8a0a36d8eb25cf5fbeed64 - P.O_18003.jar
- c038b8baa2104818f6b39b184dd9295c - PO 6785435 30-08-2015 PDF.jar
- cdca00fa3cfbdb6b045a3bf6c1516373 - P.O_001_UST-TRADE.jar
- fabaa582731529871b879a1135c839f1 - Invoice.jar
- fe64795f05714fde47a35a238c67a970 - payment.invoice.1.jar
TRAFFIC
I infected a Windows 7 host with a sample from this morning: MD5 hash be3e67412e8a0a36d8eb25cf5fbeed64, file name P.O_18003.jar. Here's what we saw in the traffic:
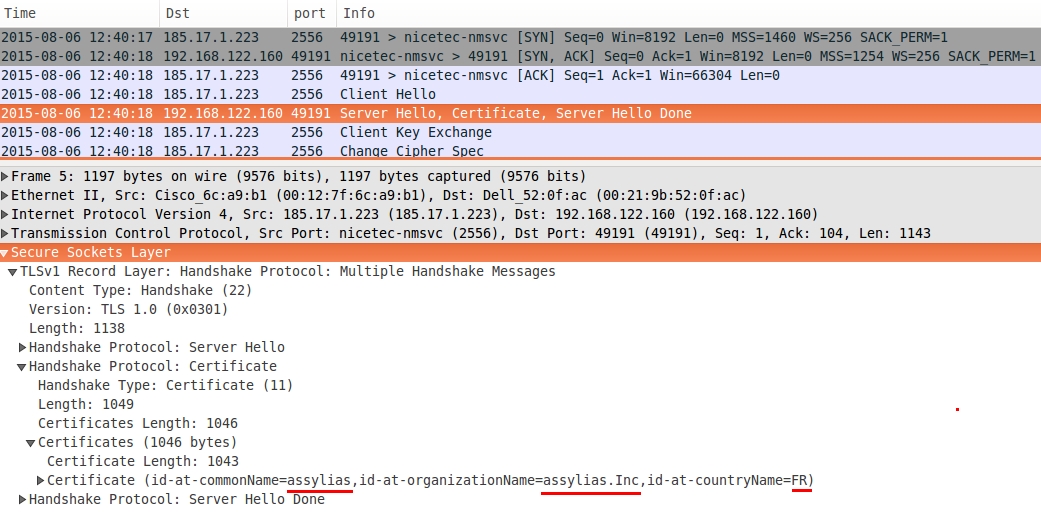
- 185.17.1[.]233 TCP port 2556 - encrypted traffic
- 185.17.1[.]233 TCP port 9033 - encrypted traffic
185.17.1[.]233 is a Russian IP address. The traffic on port 2556 was SSL, and it used a certificate with the following information:
- commonName = assylias
- organizationName = assylias.Inc
- countryName = FR
POST-INFECTION
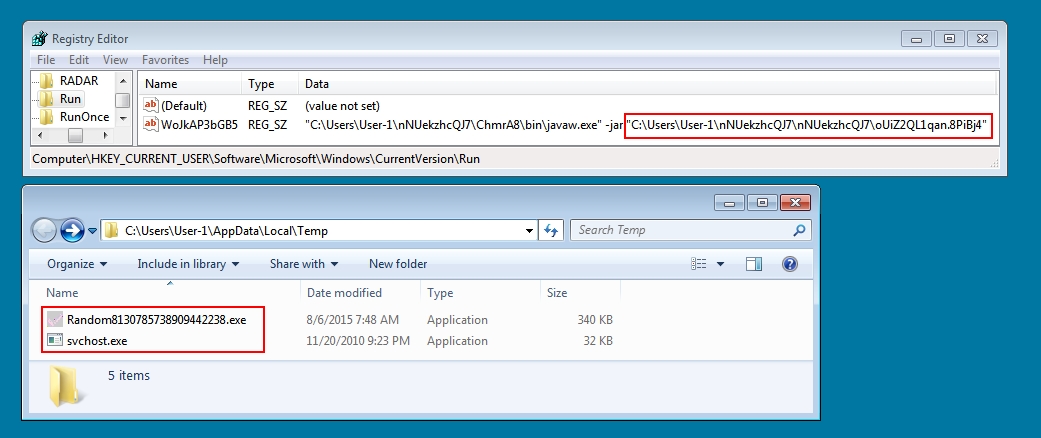
The malware created a folder at C:\Users\[username]\nNUekzhcQJ7 with multiple sub-directories and a large number of files. I've got a complete list in a text file "list-of-other-files.txt" in the archive 2015-08-06-Adwind-infection-additional-artifacts.zip. About 8 minutes after opening the Adwind .jar file, two files appeared in the C:\Users\[username]\AppData\Loca\Temp (see image below).
The svchost.exe file is not inherently malicious. However, it's original file name is regsvcs.exe, which I don't think is normal. Also, it shouldn't be showing up in the user's AppData\Local\Temp directory like that.
The other file, Random8130785738909442238.exe, appears malicious, but I haven't had time to examine it.
File name: Random8130785738909442238.exe
File size: 348,160 bytes
MD5 hash: bfe8b5b2c1e7d5c7d871d5b9ec991a4f
SHA256 hash : 2a6015cbc160df29cdce35dc7eef062658303c83de82e0a453b929a2dbc7a736
Detection ratio: 1 / 55
First submission to VirusTotal: 2015-08-06 17:08:30 UTC
Click here to return to the main page.