2015-08-13 - ANGLER EK FROM 176.9.197[.]68 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-08-13-Angler-EK-sends-CryptoWall-3.0-ransomware.pcap.zip
- 2015-08-13-Angler-EK-and-CryptoWall-ransomware-files.zip
NOTES:
- On Monday 2015-08-10, FireEye published an article about the Angler exploit kit (EK) using an Inernet Explorer (IE) exploit based on CVE-2015-2419.
- Kafeine at the Malware Don't Need Coffee blog did a write-up on it, along with Jérôme Segura at Malwarebytes (link), and I'm sure others by now.
- This and my previous blog entry on Angler EK from 2015-08-10 have traffic using the CVE-2015-2419 IE exploit.
- Bitcoin address for this CryptoWall 3.0 ransomware sample's payment was: 1LY58fiaAYFKgev67TN1UJtRveJh81D2dU
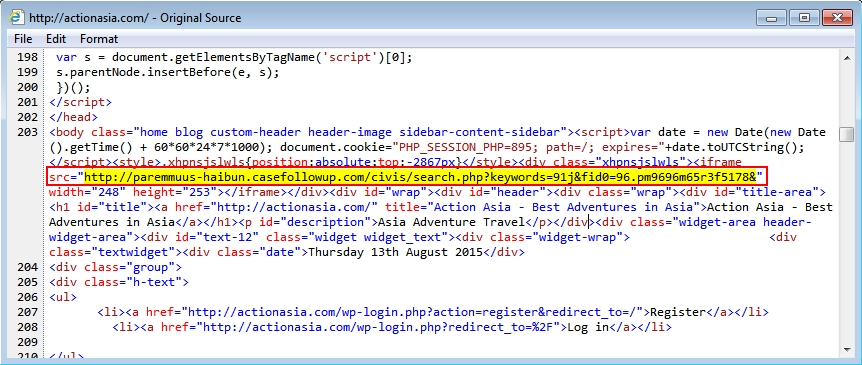
Shown above: Malicious script in page from compromised website. The iframe points to an Angler EK landing page.
Shown above: Part of the CryptoWall 3.0 ransomware decrypt instructions from a browser window.
TRAFFIC
ASSOCIATED DOMAINS:
- actionasia[.]com - Compromised website
- 176.9.197[.]68 port 80 - paremmuus-haibun.casefollowup[.]com - Angler EK
- 192.185.241[.]107 port 80 - content-into-cash[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 69.89.31[.]99 port 80 - cprnash[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 208.113.240[.]70 port 80 - conopizzavenezuela[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 109.73.172[.]51 port 80 - aplikacii[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 192.185.182[.]83 port 80 - couponsonakeychain[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 72.167.1[.]128 port 80 - futurecomtechnologies[.]com - Post-infection callback by CryptoWall 3.0 ransomware
- 80.78.251[.]170 port 80 - 6i3cb6owitcouepv.spatopayforwin[.]com - User viewing the decrypt instructions
- 46.108.156[.]176 port 80 - 6i3cb6owitcouepv.bythepaywayall[.]com - User viewing the decrypt instructions
- 6i3cb6owitcouepv.lowallmoneypool[.]com - Domain for decrypt instructions that didn't resolve in DNS
- 6i3cb6owitcouepv.transoptionpay[.]com - Domain for decrypt instructions that didn't resolve in DNS
COMPROMISED WEBSITE:
- 2015-08-13 12:59:59 UTC - actionasia[.]com - GET /
ANGLER EK:
- 2015-08-13 13:00:05 UTC - paremmuus-haibun.casefollowup[.]com - GET /civis/search.php?keywords=91j&fid0=96.pm9696m65r3f5178&
- 2015-08-13 13:00:07 UTC - paremmuus-haibun.casefollowup[.]com - GET /area.jss?army=&party=IgT7O&on=&remain=THELsSg_tn&
good=zUjVPAsUKa&word=sKTcLSi__FqW1ZgP4kT-Qu0
- 2015-08-13 13:00:07 UTC - paremmuus-haibun.casefollowup[.]com - POST /civis/before.zul?demand=&city=3MapGK&along=&but=MTVzrNav&
anyone=lp6XWQNCZ4tLWTZfXpf5OV_M-LxSNCACnT
- 2015-08-13 13:00:10 UTC - paremmuus-haibun.casefollowup[.]com - GET /attitude.codasite?machine=&into=PrPXA5d9PT&responsibility=&
number=Uy6&anyone=&cell=W6f68&during=XdneYH&top=lhfcSuovyz3bH9jUYynb8uOn
- 2015-08-13 13:00:17 UTC - paremmuus-haibun.casefollowup[.]com - GET /kill.cfm?patient=iawJf&describe=ACx1WfgDs&will=5qzHxk&an=&
country=pMV6&mean=Y10Nxz4KP&report=24N0zyV3u&saint=oNjghq
POST-INFECTION CALLBACK BY CRYPTOWALL 3.0:
- 2015-08-13 13:00:19 UTC - ip-addr[.]es - GET /
- 2015-08-13 13:00:19 UTC - content-into-cash[.]com - POST /wp-content/plugins/pretty-link/cc.php?c=ktnk6wssy2s5lx
- 2015-08-13 13:02:23 UTC - ip-addr[.]es - GET /
- 2015-08-13 13:02:24 UTC - content-into-cash[.]com - POST /wp-content/plugins/pretty-link/cc.php?t=m8rm1qr8q3q3d
- 2015-08-13 13:02:28 UTC - cprnash[.]com - POST /wp-content/themes/twentytwelve/c.php?l=m8rm1qr8q3q3d
- 2015-08-13 13:02:31 UTC - conopizzavenezuela[.]com - POST /wp-content/plugins/stickyfooter/ccccc.php?n=m8rm1qr8q3q3d
- 2015-08-13 13:02:32 UTC - aplikacii[.]com - POST /openx/www/delivery/ccc.php?s=m8rm1qr8q3q3d
- 2015-08-13 13:02:35 UTC - couponsonakeychain[.]com - POST /wp-content/plugins/wp-smushit/ccc.php?i=m8rm1qr8q3q3d
- 2015-08-13 13:02:39 UTC - conopizzabrasil[.]com - POST /wp-content/plugins/revision-control/ccc.php?k=m8rm1qr8q3q3d
- 2015-08-13 13:02:40 UTC - futurecomtechnologies[.]com - POST /wp-content/plugins/jetpack/ccccc.php?l=m8rm1qr8q3q3d
- 2015-08-13 13:02:42 UTC - content-into-cash[.]com - POST /wp-content/plugins/pretty-link/cc.php?i=t2ofm9adha31sj4
- 2015-08-13 13:02:52 UTC - cprnash[.]com - POST /wp-content/themes/twentytwelve/c.php?j=t2ofm9adha31sj4
- 2015-08-13 13:02:56 UTC - conopizzavenezuela[.]com - POST /wp-content/plugins/stickyfooter/ccccc.php?g=t2ofm9adha31sj4
- 2015-08-13 13:02:56 UTC - aplikacii[.]com - POST /openx/www/delivery/ccc.php?i=t2ofm9adha31sj4
- 2015-08-13 13:03:00 UTC - couponsonakeychain[.]com - POST /wp-content/plugins/wp-smushit/ccc.php?g=t2ofm9adha31sj4
- 2015-08-13 13:03:02 UTC - conopizzabrasil[.]com - POST /wp-content/plugins/revision-control/ccc.php?f=t2ofm9adha31sj4
- 2015-08-13 13:03:03 UTC - futurecomtechnologies[.]com - POST /wp-content/plugins/jetpack/ccccc.php?e=t2ofm9adha31sj4
- 2015-08-13 13:03:06 UTC - content-into-cash[.]com - POST /wp-content/plugins/pretty-link/cc.php?d=ngo3ltzupfcsr
- 2015-08-13 13:03:10 UTC - cprnash[.]com - POST /wp-content/themes/twentytwelve/c.php?h=ngo3ltzupfcsr
- 2015-08-13 13:03:14 UTC - conopizzavenezuela[.]com - POST /wp-content/plugins/stickyfooter/ccccc.php?j=ngo3ltzupfcsr
- 2015-08-13 13:03:14 UTC - aplikacii[.]com - POST /openx/www/delivery/ccc.php?w=ngo3ltzupfcsr
- 2015-08-13 13:03:19 UTC - couponsonakeychain[.]com - POST /wp-content/plugins/wp-smushit/ccc.php?q=ngo3ltzupfcsr
- 2015-08-13 13:03:20 UTC - conopizzabrasil[.]com - POST /wp-content/plugins/revision-control/ccc.php?z=ngo3ltzupfcsr
- 2015-08-13 13:03:21 UTC - futurecomtechnologies[.]com - POST /wp-content/plugins/jetpack/ccccc.php?c=ngo3ltzupfcsr
- 2015-08-13 13:03:30 UTC - content-into-cash[.]com - POST /wp-content/plugins/pretty-link/cc.php?u=wy1p1k2jjsn93
- 2015-08-13 13:03:40 UTC - cprnash[.]com - POST /wp-content/themes/twentytwelve/c.php?w=wy1p1k2jjsn93
- 2015-08-13 13:03:42 UTC - conopizzavenezuela[.]com - POST /wp-content/plugins/stickyfooter/ccccc.php?z=wy1p1k2jjsn93
- 2015-08-13 13:03:44 UTC - aplikacii[.]com - POST /openx/www/delivery/ccc.php?n=wy1p1k2jjsn93
- 2015-08-13 13:03:46 UTC - couponsonakeychain[.]com - POST /wp-content/plugins/wp-smushit/ccc.php?m=wy1p1k2jjsn93
- 2015-08-13 13:03:48 UTC - conopizzabrasil[.]com - POST /wp-content/plugins/revision-control/ccc.php?k=wy1p1k2jjsn93
- 2015-08-13 13:03:49 UTC - futurecomtechnologies[.]com - POST /wp-content/plugins/jetpack/ccccc.php?g=wy1p1k2jjsn93
WHERE THE USER CLICKED ON LINKS, ENTERED THE CAPTCHA, AND VIEWED THE DECRYPT PAGES:
- 2015-08-13 13:17:25 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /[info removed]
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/style.css
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/us.png
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/it.png
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/fr.png
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/es.png
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/de.png
- 2015-08-13 13:17:28 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /picture.php?k=[info removed]&41a2517c80260a2dafab46d799fe624e
- 2015-08-13 13:17:29 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/lt.png
- 2015-08-13 13:17:30 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/rt.png
- 2015-08-13 13:17:30 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/lb.png
- 2015-08-13 13:17:30 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/rb.png
- 2015-08-13 13:17:32 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /favicon.ico
- 2015-08-13 13:17:38 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - POST /[info removed]
- 2015-08-13 13:17:40 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/flags/gb.png
- 2015-08-13 13:17:40 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/bitcoin.png
- 2015-08-13 13:17:40 UTC - 6i3cb6owitcouepv.spatopayforwin[.]com - GET /img/button_pay.png
- 2015-08-13 13:17:58 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /[info removed]
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/style.css
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/us.png
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/fr.png
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/es.png
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/it.png
- 2015-08-13 13:18:00 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/de.png
- 2015-08-13 13:18:01 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /picture.php?k=[info removed]&36890bfcb99df47dac0bc35008a70389
- 2015-08-13 13:18:01 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/lt.png
- 2015-08-13 13:18:01 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/rt.png
- 2015-08-13 13:18:01 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/lb.png
- 2015-08-13 13:18:01 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/rb.png
- 2015-08-13 13:18:03 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /favicon.ico
- 2015-08-13 13:18:07 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - POST /[info removed]
- 2015-08-13 13:18:10 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/flags/gb.png
- 2015-08-13 13:18:10 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/bitcoin.png
- 2015-08-13 13:18:10 UTC - 6i3cb6owitcouepv.bythepaywayall[.]com - GET /img/button_pay.png
Click here to return to the main page.