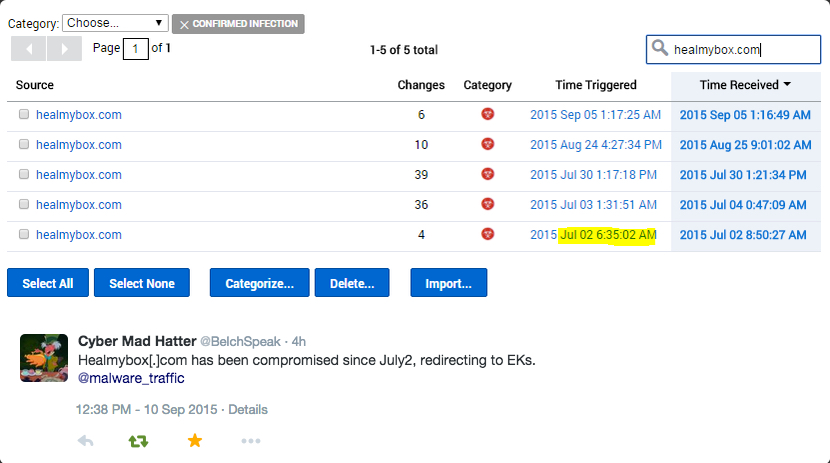
2015-09-10 - ANGLER EK FROM 62.109.9[.]60
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-10-Angler-EK-traffic.pcap.zip
- 2015-09-10-Angler-EK-malware-and-artifacts.zip
- 2015-09-10-malwr.com-analysis-of-payload.pcap.zip
NOTES:
- No ransomware noted like we've been seeing with Angler EK lately, so maybe there's a different actor behind this traffic.
- Apparently, the compromised website has a history of being compromised.
IMAGES FROM THE TRAFFIC
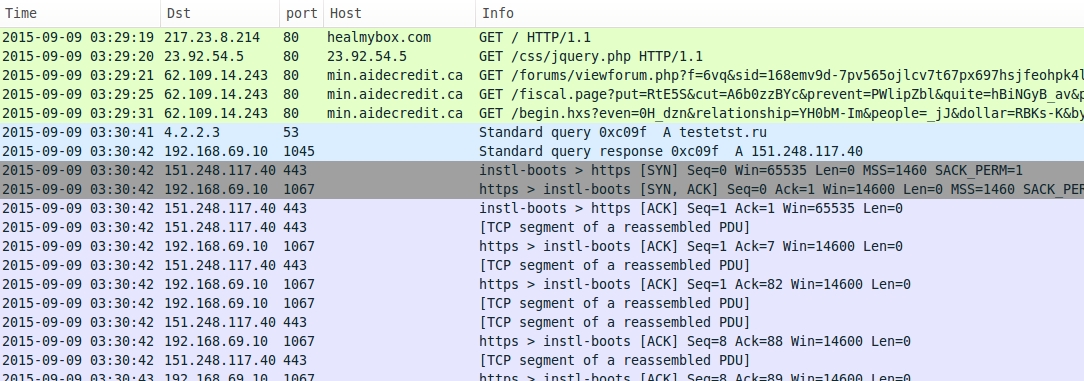
Shown above: Infection chain of events from the Threatglass pcap on 2015-09-09.
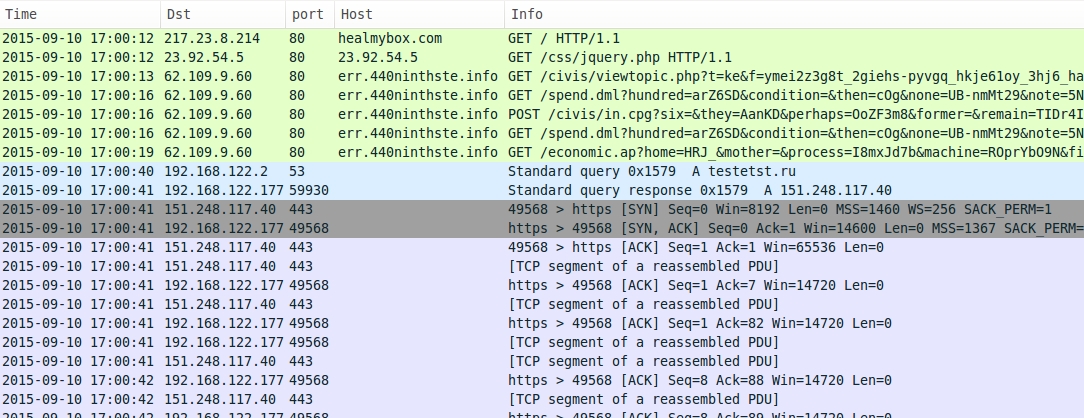
Shown above: Infection chain of events from my pcap on 2015-09-10.
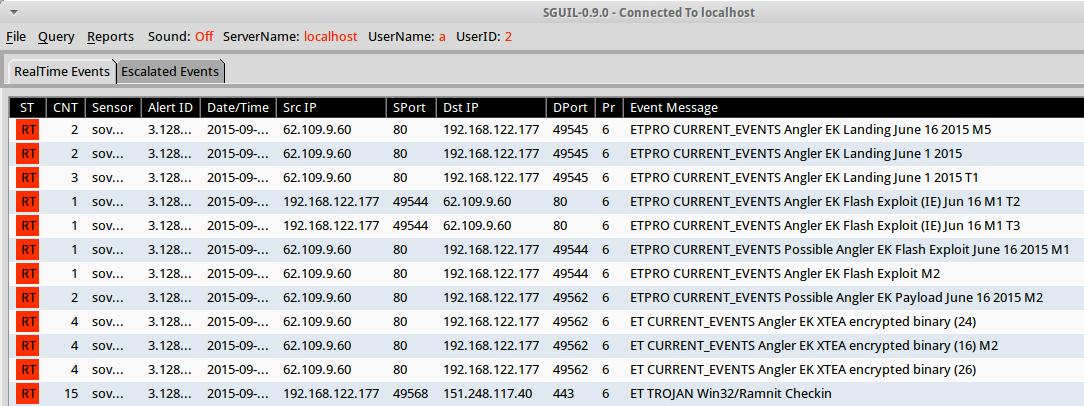
Shown above: Security Onion events seen after using tcpreplay on my pcap from 2015-09-10.
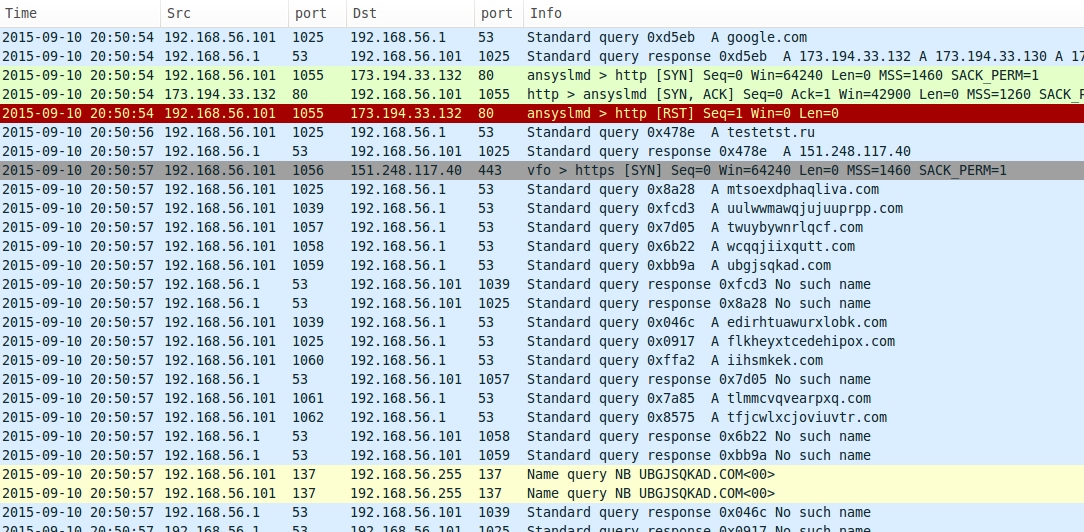
Shown above: Some DNS queries for DGA domains seen on malwr.com's analysis of the 2015-09-10 malware.
ASSOCIATED DOMAINS
healmybox[.]com - compromised website
23.92.54[.]5 port 80 - 23.92.54[.]5 - Gate/redirect (to the EK landing page)
62.109.14[.]243 port 80 - min.aidecredit[.]ca - Angler EK from Threatglass pcap on 2015-09-09
62.109.9[.]60 port 80 - err.440ninthste[.]info - Angler EK from my pcap on 2015-09-10
151.248.117[.]40 port 443 - testetst[.]ru - Post-infection traffic
PRELIMINARY MALWARE ANALYSIS
File name: 2015-09-10-Angler-EK-malware-payload.exe
File size: 315,392 bytes
MD5 hash: 6be221f3b83caf84d4ff426f736a527f
SHA1 hash: b595a300b94c9c0b33ee4e23bba7ee50fc9a0a4c
SHA256 hash: 2c1a78ee76cb282ba03e9fd4739896ee497c6895c984c3b9bfddbb2ed4dcce6c
Detection ratio: 4 / 56
First submission: 2015-09-10 17:28:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c1a78ee76cb282ba03e9fd4739896ee497c6895c984c3b9bfddbb2ed4dcce6c/analysis/
File name: C:\Users\Username\AppData\Local\Temp\lkjkmogr.exe
File size: 632,832 bytes
MD5 hash: 70386f16d2fff1e26f2a68f99b2bf700
SHA1 hash: 0757626327772a2b6f26e433d82d092d393315b5
SHA256 hash: 58363118b31772195e77cf30814c571d8c3ff4751f6b77664ad0259aee4c61a1
Detection ratio: 33 / 56
First submission: 2015-09-10 21:29:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/58363118b31772195e77cf30814c571d8c3ff4751f6b77664ad0259aee4c61a1/analysis/
Click here to return to the main page.