2015-10-21 - NEUTRINO EK FROM 89.38.150[.]119 SENDS NECURS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-21-Neutrino-EK-traffic.pcap.zip 364.1 kB (364,124 bytes)
- 2015-10-21-Neutrino-EK-malware-and-artifacts.zip 201.4 kB (201,453 bytes)
NOTES:
- Pretty much the same thing seen last week on 2015-10-13, except this time, Neutrino EK by this actor was using port 80.
- In this case, I am unable to share information on the compromised website.
- Todays infection is a different actor than the Magento server infections associated with Neutrino EK that Sucuri (link) and Malwarebytes (link) have blogged about... Different traffic patterns.
CHAIN OF EVENTS
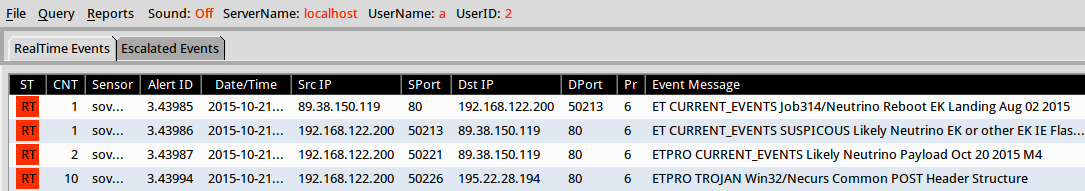
Shown above: Results in Security Onion after using tcpreplay on the pcap.
ASSOCIATED DOMAINS:
- 178.33.200[.]128 port 80 - vid.fotografofamoso[.]com[.]br - Redirect/Gate pointing to Neutrino EK
- 89.38.150[.]119 port 80 - btsjywn.xmqbsmyofchd[.]gq - Neutrino EK
- 95.22.28[.]194 port 80 - 195.22.28[.]194 - Necurs-related post-infection callback
- 195.22.28[.]222 port 80 - sso.anbtr[.]com - Post-infection traffic
- various IP addresses, various ports - UDP traffic and attempted TCP connections (see pcap for details)
REDIRECT/GATE:

- 2015-10-21 00:44:44 UTC - vid.fotografofamoso[.]com[.]br - GET /js/script.js
NEUTRINO EK:
- 2015-10-21 00:44:45 UTC - btsjywn.xmqbsmyofchd[.]gq - GET /1999/04/17/visit/band/back/everywhere-consult-view.html
- 2015-10-21 00:44:45 UTC - btsjywn.xmqbsmyofchd[.]gq - GET /mister/kindness-platform-column-10247547
- 2015-10-21 00:44:46 UTC - btsjywn.xmqbsmyofchd[.]gq - GET /southern/emd1bnE
- 2015-10-21 00:44:47 UTC - btsjywn.xmqbsmyofchd[.]gq - GET /yesterday/cnRsa2E
- 2015-10-21 00:44:49 UTC - btsjywn.xmqbsmyofchd[.]gq - GET /2009/06/20/lawn/short/feast/hour-exceeding-knowledge-young-mankind-shine-bloom.html
POST-INFECTION TRAFFIC:
- 2015-10-21 00:45:12 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:45:13 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:45:19 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:45:19 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:45:38 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:45:38 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:45:56 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:45:56 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:46:10 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:46:11 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:46:25 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:46:25 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:46:31 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:46:31 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:46:46 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:46:47 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
- 2015-10-21 00:46:49 UTC - 195.22.28[.]194 - POST /forum/db.php
- 2015-10-21 00:46:49 UTC - sso.anbtr[.]com - GET /domain/195.22.28[.]194
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-10-21-Neutrino-EK-flash-exploit.swf
File size: 95,138 bytes
MD5 hash: 97bedff81331b2198b0f07b1088d6bcb
SHA1 hash: 1b3777daf1090eb60559e57f388f22342b7751df
SHA256 hash: 497a23fa67dd737b81e00481240e9e9e3e4e1bab7d6f74f211717a2873a203d5
Detection ratio: 0 / 56
First submission: 2015-10-21 16:46:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/497a23fa67dd737b81e00481240e9e9e3e4e1bab7d6f74f211717a2873a203d5/analysis/
MALWARE PAYLOAD:
File name: 2015-10-21-Neutrino-EK-malware-payload.exe
File name: C:\Windows\Installer\{D9420F8B-C520-4316-D4D2-8B77B4998B1C}\syshost.exe
File size: 199,168 bytes
MD5 hash: 3251e5ebe7c0e61aac2d2f74b3423e12
SHA1 hash: f752e081246dda766aa87ff89615824d684a9d40
SHA256 hash: 3e2a76ed82bd9320700deb079a8d6fdcb5236c37b8f5c2b0e72683fd8dacb048
Detection ratio: 8 / 56
First submission: 2015-10-21 08:41:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/3e2a76ed82bd9320700deb079a8d6fdcb5236c37b8f5c2b0e72683fd8dacb048/analysis/
REGISTRY KEYS:

Shown above: One of the registry keys created or updated by this malware.
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\syshost32
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\syshost32
- Value name: ImagePath
- Value type: REG_EXPAND_SZ
- Value data: "C:\Windows\Installer\{D9420F8B-C520-4316-D4D2-8B77B4998B1C}\syshost.exe" /service
Click here to return to the main page.
