2015-10-30 - NUCLEAR EK FROM 188.166.65[.]14
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-30-Nuclear-EK-traffic.pcap.zip 2.0 MB (1,982,829 bytes)
- 2015-10-30-Nuclear-EK-malware-and-artifacts.zip 1.4 MB (1,404,626 bytes)
CHAIN OF EVENTS
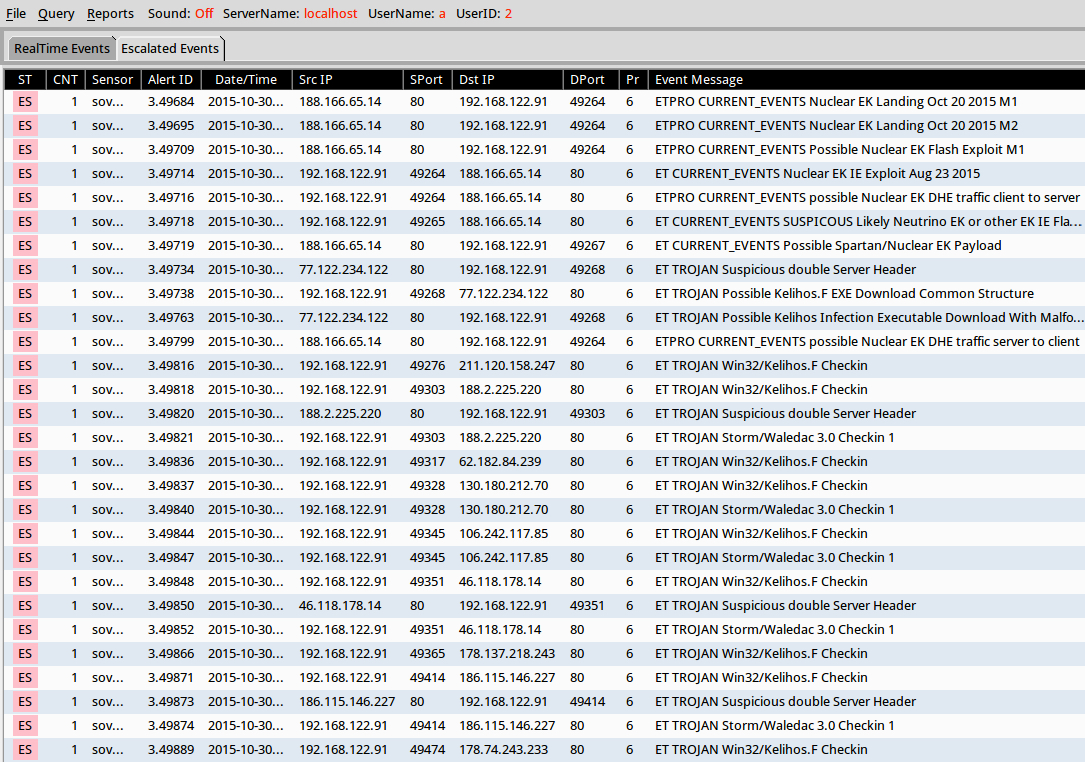
Shown above: Results in Security Onion after using tcpreplay on the pcap.
ASSOCIATED DOMAINS:
- 104.28.28[.]185 port 80 - gasfiliera[.]it - Compromised website
- 188.166.65[.]14 port 80 - yjlvh61dby62cvao5[.]ml - Nuclear EK
- 77.122.234[.]122 port 80 - 77.122.234[.]122 - Post-infection traffic - GET /harsh02.exe
- 188.2.225[.]220 port 80 - 188.2.225[.]220 - Post-infection traffic - GET /welcome.htm - GET /home.htm
- 130.180.212[.]70 port 80 - 130.180.212[.]70 - Post-infection traffic - GET /online.htm
- 106.242.117[.]85 port 80 - 106.242.117[.]85 - Post-infection traffic - GET /setup.htm
- 46.118.178[.]14 port 80 - 46.118.178[.]14 - Post-infection traffic - GET /file.htm - GET /install.htm
- 186.115.146[.]227 port 80 - 186.115.146[.]227 - Post-infection traffic - GET /index.htm - GET /file.htm
IMAGES FROM THE TRAFFIC

Shown above: Injected script in page from the compromised website.
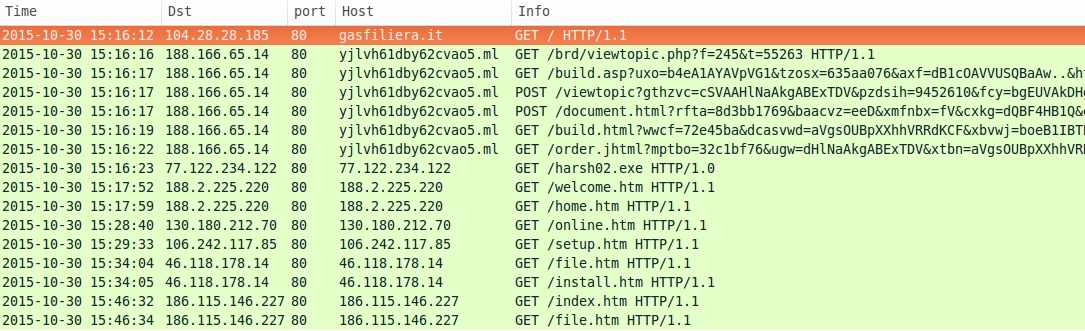
Shown above: HTTP requests during the traffic.
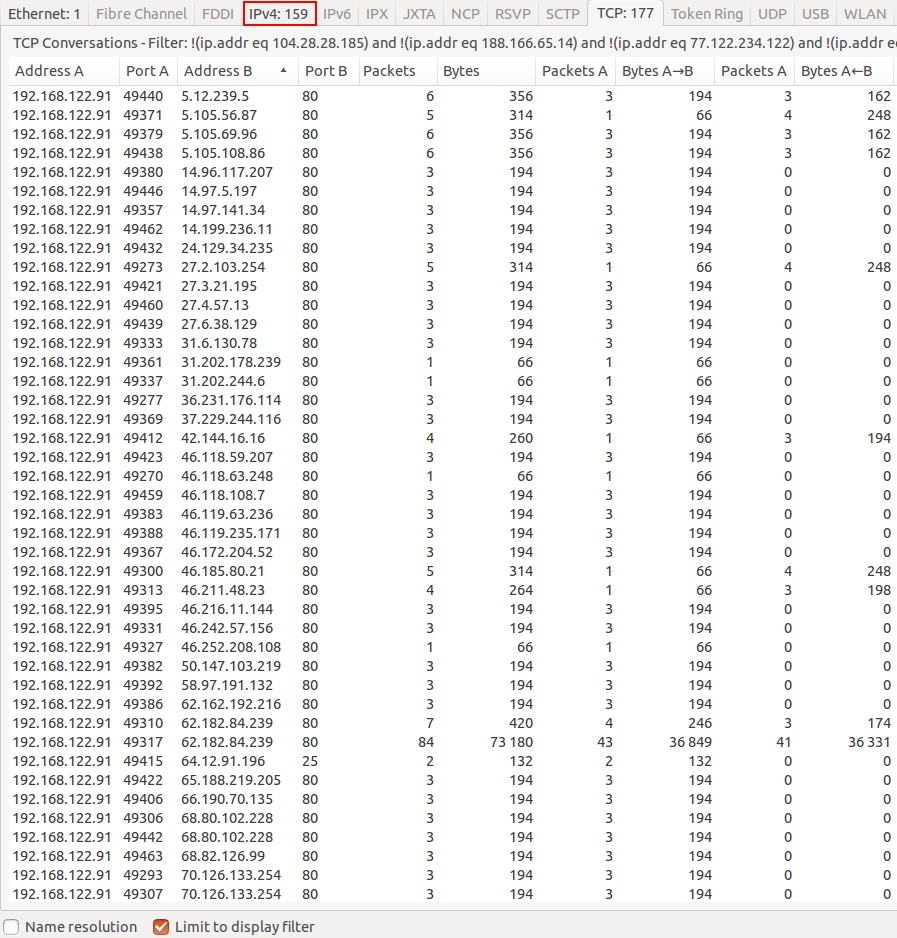
Shown above: Filtering the traffic in Wireshark, you'll find more than 150 IP addresses the infected host reached out to.
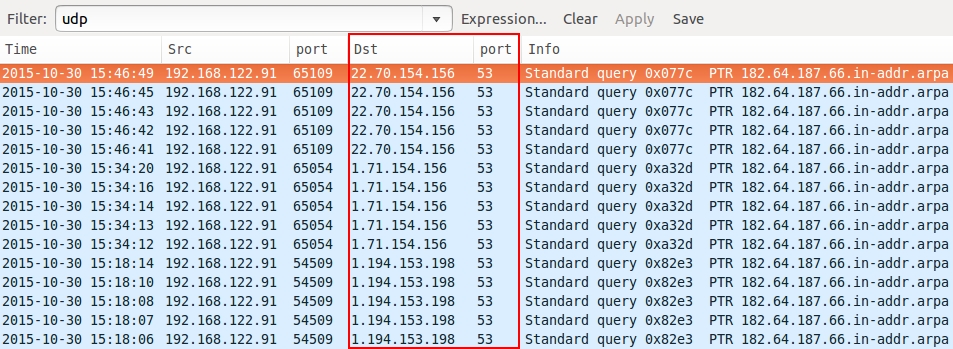
Shown above: Post-infection traffic also shows DNS queries to unusual IP addresses.
Click here to return to the main page.
