2015-11-09 - NUCLEAR EK FROM 178.62.8[.]117 SENDS ANDROMEDA/CTB-LOCKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-09-Nuclear-EK-traffic.pcap.zip 1.6 MB (1,583,454 bytes)
- 2015-11-09-Nuclear-EK-malware-and-artifacts.zip 1.5 MB (1,517,370 bytes)
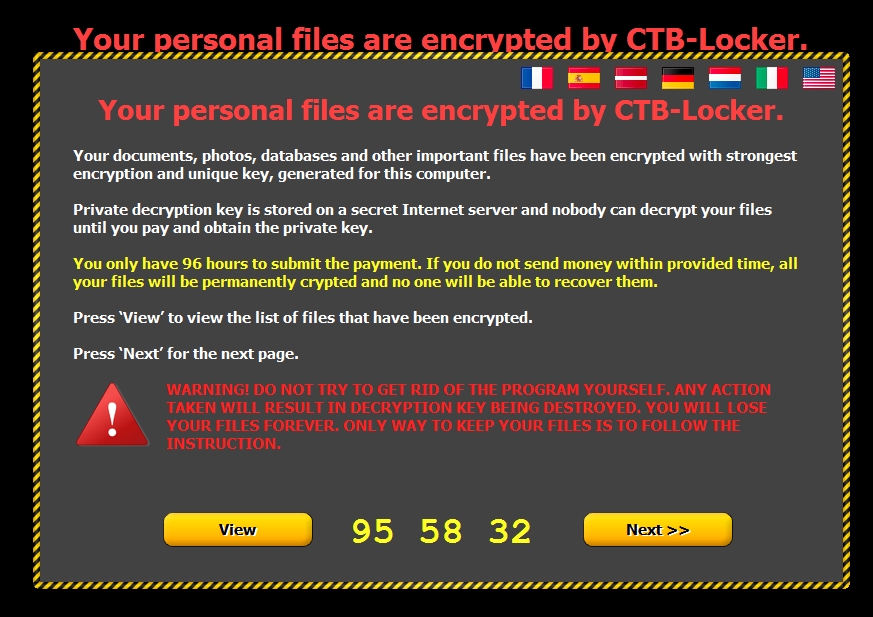
Shown above: Desktop background from infected Windows host.
TRAFFIC
ASSOCIATED DOMAINS:
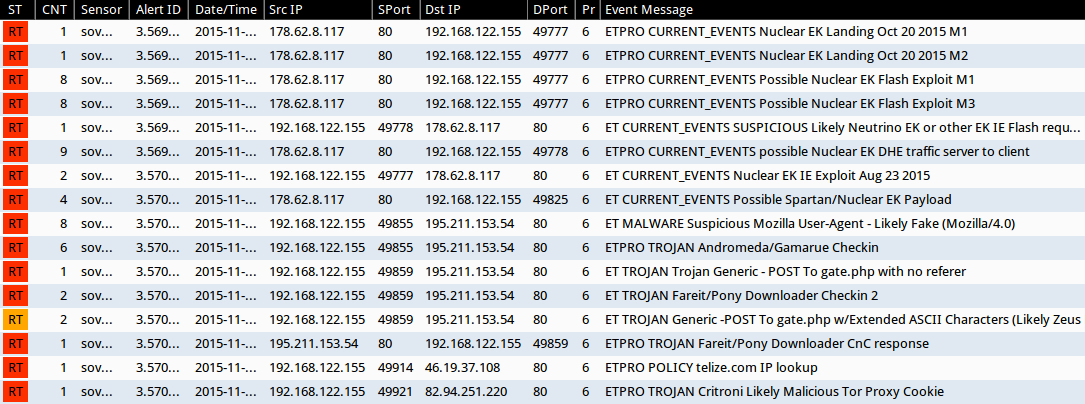
Shown above: Events generated after using tcpreplay on the pcap in Security Onion.
- www.bikerumor[.]com - Compromised website
- 195.211.153[.]54 port 80 - securemaxcdn[.]com - Redirect (gate)
- 178.62.8[.]117 port 80 - cachemaxbootstrap[.]pw - Nuclear EK
- 195.211.153[.]54 port 80 - bootstrap4cache[.]info - Andromede post-infection check in
- 31.24.30.91 port 80 - bootstrap4cache[.]info - Andromeda post-infection (same domain as above, but with different IP address)
- 50.63.69[.]1 port 80 - robzombie[.]com - Andromeda downloading CTB-Locker
- 46.19.37[.]108 port 80 - ip.telize[.]com - IP address check by CTB-Locker
- 82.94.251[.]220 port 80 - x2h6roismjroam63[.]onion[.]lt - More post-infection by CTB-Locker
COMPROMISED WEBSITE AND REDIRECT:
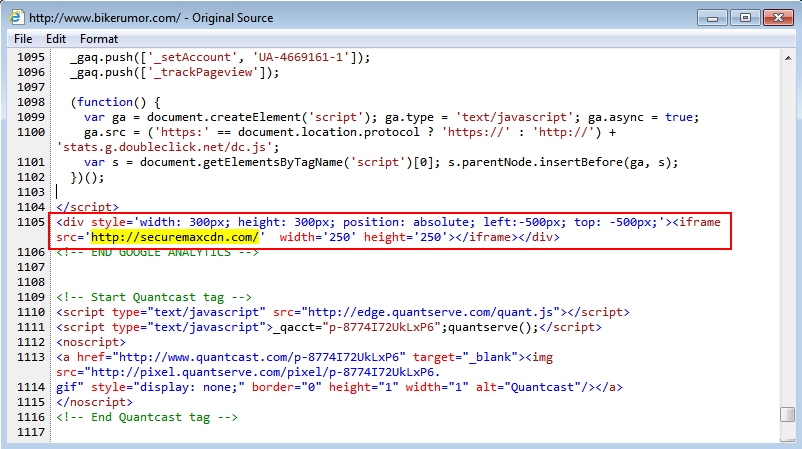
Shown above: Injected script in page from compromised website.
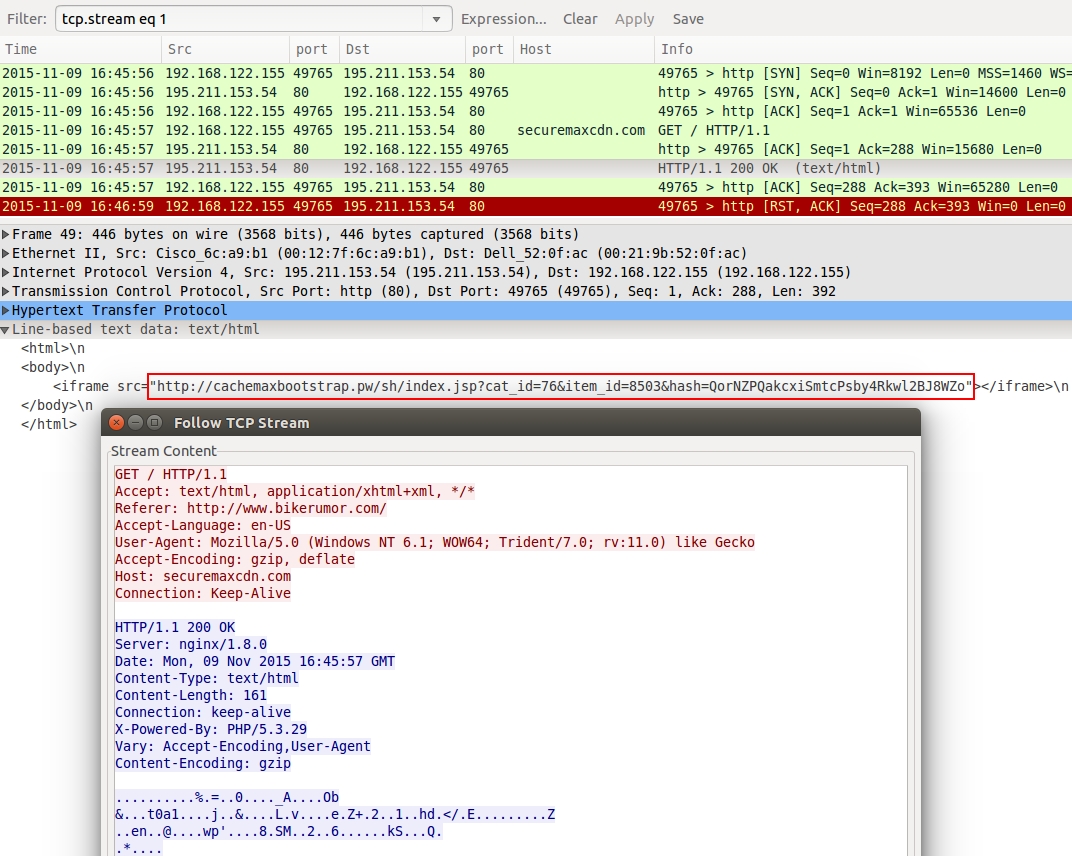
Shown above: Redirect URL leading to Nuclear EK landing page.
- 2015-11-09 16:45:54 UTC - www.bikerumor[.]com - GET /
- 2015-11-09 16:45:57 UTC - securemaxcdn[.]com - GET /
NUCLEAR EK:
- 2015-11-09 16:45:58 UTC - cachemaxbootstrap[.]pw - GET /sh/index.jsp?cat_id=76&item_id=8503&hash=QorNZPQakcxiSmtcPsby4Rkwl2BJ8WZo
- 2015-11-09 16:45:59 UTC - cachemaxbootstrap[.]pw - GET /amount?pftm=eJA10C&peuvflh=aVhtFGUVAUFFJVE0CTwBUBllUXgJNB15eRxBBF1BBHRNCG&
rmkohpo=1cff14a&ulazcxw=cHVEEGQAFB1Q&wfbghie=bQIAHVAbVAQG&xcqx=1ed1351&lecnxnh=dFXQYEBlt
- 2015-11-09 16:46:00 UTC - cachemaxbootstrap[.]pw - POST /build.jhtml?qmftg=87daf9b0&nrprvpq=876409b7&vfrztm=cVB8CHVIAUh8&zpu=dDAh8EU&zuozl=
eQUGA1sCUAQJT1I.&ugagg=aVwtqD0JNRxJWV01SUgB&ammhel=bdAFxQSwFaCkVCRxFUFR9BRB8G
- 2015-11-09 16:46:00 UTC - cachemaxbootstrap[.]pw - POST /cart.xml?bmnyanl=84c50ccc87&dbiilpl=2bebac9697&qrxf=dJBF&ywvnne=bDUhMbFUZNAFIbVh8
ABlQbVwBNA&vohf=aVwtqA11QQAsHGUVAUFFJBlBSWwZYBElTXAxBFkV&dgsezsk=eYAXU0A&uktznd=clcBUgE
- 2015-11-09 16:46:03 UTC - cachemaxbootstrap[.]pw - GET /document.xml?qwe=979e87cd81&vff=cNCGQIAHVAbVAQGHVEEGQAFB1QFXQYEBltJUk&qahmq=
aVQpZAE1FQgAHGQBNTwBUB&hmojffe=bllUXgJNB15eRxBBF1BBHR&cdzrvp=9b7c5e45&oheqqu=d15QiRQIXZ5fDFtGQM.
- 2015-11-09 16:46:04 UTC - cachemaxbootstrap[.]pw - GET /including.aspx?ezscskt=cAB1cCVQkGBlYNGQZNQ&kwqcppz=006c15921&wwwp=dQJADmBcYQtM
IU0A&bvj=bVg5UHVNeXBdGEUNQQ01FEk0CAk0GSwAEBE0HVE0&tktdrct=6d433e&ydlhiak=aVQpZAE1FQgAHGQBNAB9WBFJZ
POST-INFECTION TRAFFIC:
- 2015-11-09 16:46:29 UTC - bootstrap4cache[.]info POST /count/counter.php
- 2015-11-09 16:46:32 UTC - robzombie[.]com - GET /wp-includes/images/smilies/lol.gif
- 2015-11-09 16:46:33 UTC - bootstrap4cache[.]info - POST /count/counter.php
- 2015-11-09 16:46:35 UTC - robzombie[.]com - GET /wp-includes/images/smilies/wink.gif
- 2015-11-09 16:46:38 UTC - bootstrap4cache[.]info - POST /panel/gate.php
- 2015-11-09 16:46:39 UTC - bootstrap4cache[.]info - POST /count/counter.php
- 2015-11-09 16:47:06 UTC - ip.telize[.]com - GET /
- 2015-11-09 16:47:07 UTC - x2h6roismjroam63[.]onion[.]lt - GET /DIPIkSl2QBPx&vvZ0TjmsGlywj=FHlS-FiqzzJAQC&0-25FcnBROu=P-5PmYcdVGg&TYZPNWN3rro=
PHzgx8vwn&xs+QlEo7gX=0aaON-pyBiEPHM&pki+ctrB4oQ9lq=Brk91rHHlOB5q&uA0t4i6L
PRELIMINARY MALWARE ANALYSIS
NUCLEAR EK ARTIFACTS:
- 2015-11-09-Nuclear-EK-flash-exploit.swf - VirusTotal link
- 2015-11-09-Nuclear-EK-payload.exe - VirusTotal link
ARTIFACTS RETRIEVED FROM THE INFECTED HOST:
- C:\ProgramData\mssez.exe [same file hash as the Nuclear EK payload]
- C:\Users\[username]\AppData\Local\Temp\cdo944428177.dll [cdosys.dll from Windows 7, not actual malware]
- C:\Users\[username]\AppData\Local\Temp\fylhsnj.exe - VirusTotal link
- C:\Users\[username]\AppData\Local\Temp\KB01008842.exe [same file hash as fylhsnj.exe]
Click here to return to the main page.