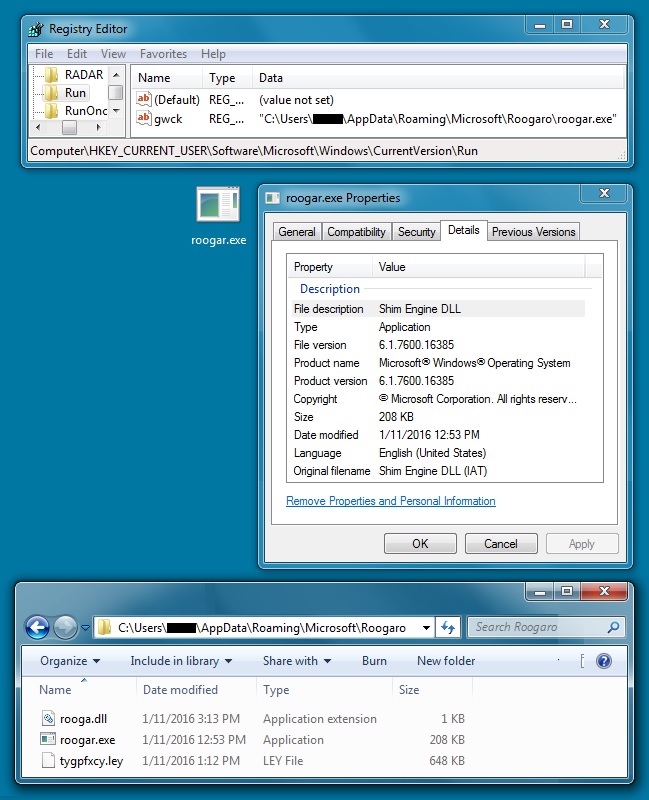
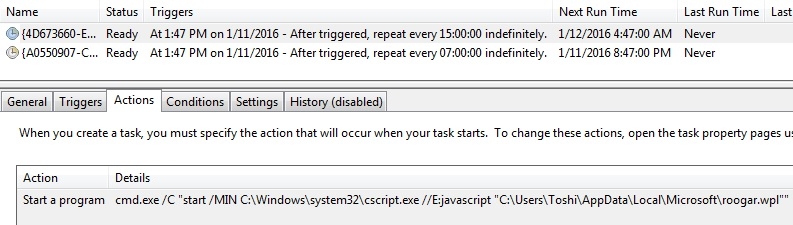
2016-01-11 - RIG EK FROM 46.30.43[.]79 SENDS QBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-11-Rig-EK-sends-Qbot.pcap.zip 544.2 kB (544,155 bytes)
- 2016-01-11-Rig-EK-and-Qbot-malware-and-artifacts.zip 223.9 kB (223,855 bytes)
NOTES:
- I've documented recent activity by this actor in two diaries at the Internet Storm Center (ISC) at:
- The above two diaries should explain the traffic below (how the gate is used by this particular actor). Today's traffic is more of the same stuff.
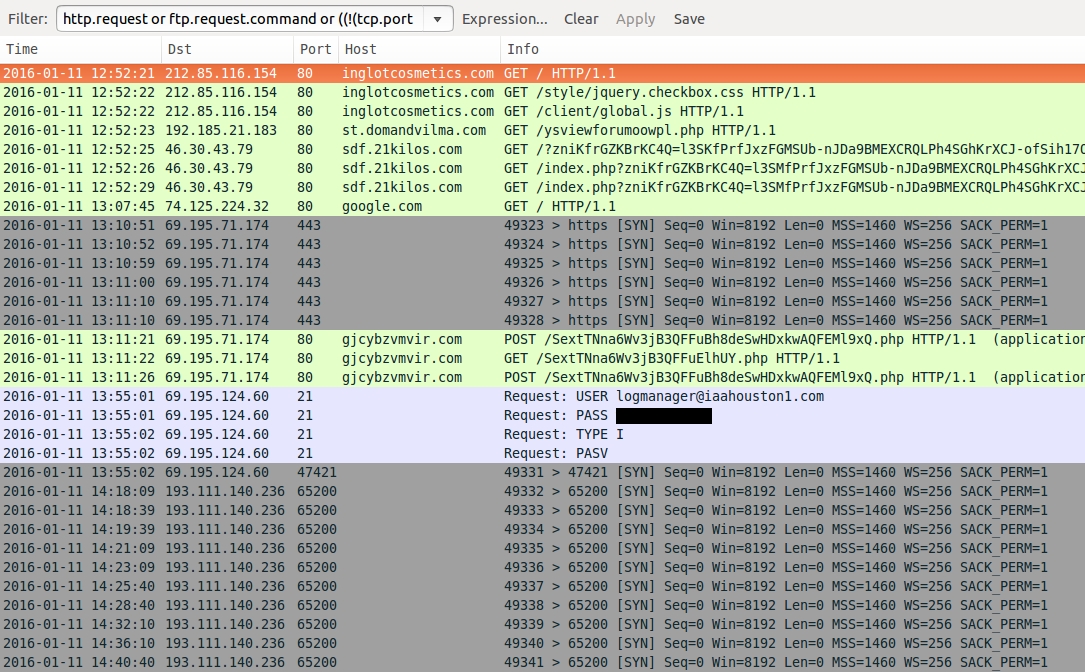
Shown above: Pcap of the infection traffic filtered in Wireshark.
TRAFFIC
ASSOCIATED DOMAINS:
- 212.85.116[.]154 port 80 - inglotcosmetics[.]com - Compromised website
- 192.185.21[.]183 port 80 - st.domandvilma[.]com - Gate
- 46.30.43[.]79 port 80 - sdf.21kilos[.]com - Rig EK
- 69.195.71[.]174 port 80 - gjcybzvmvir[.]com - Post-infection Qbot check-in
- 69.195.124[.]60 port 21 - FTP traffic (Qbot Exfil via FTP)
- 193.111.140[.]236 port 65200 - More post-infecion traffic (attempted connections, not successful)
MALICIOUS JAVASCRIPT IN .JS FILE FROM COMPROMISED WEBSITE:
- 2016-01-11 12:52:22 UTC - inglotcosmetics[.]com - GET /client/global.js
VARIABLE RETURNED FROM GATE:
- 2016-01-11 12:52:23 UTC - st.domandvilma[.]com - GET /ysviewforumoowpl.php
RIG EK:
- 2016-01-11 12:52:25 UTC - sdf.21kilos[.]com - GET /?zniKfrGZKBrKC4Q=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ceSF7Ju2wmgyLcTect0khTR4WADnr9PWgtC5V4RmK7KBKqE
- 2016-01-11 12:52:26 UTC - sdf.21kilos[.]com - GET /index.php?zniKfrGZKBrKC4Q=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ceSF7Ju2wmgyLcTect0khTR4WADnr9PWgtC5V4RmK7KBKqKp0N6RgBnEB_CbJQlqw-
BF3H6PXl5gv2pHn4oieWX_PF0n5YmmA
- 2016-01-11 12:52:29 UTC - sdf.21kilos[.]com - GET /index.php?zniKfrGZKBrKC4Q=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ceSF7Ju2wmgyLcTect0khTR4WADnr9PWgtC5V4RmK7KBKqKp0N6RgBnEB_CbJQlqw-
fECT6PXl5gv2pHn4oieWX_P52n5Es3lM&dop=2154
POST-INFECTION QBOT ACTIVITY - TCP TRAFFIC:
- 2016-01-11 13:07:45 UTC - google[.]com - GET /
- 2016-01-11 13:10:51 UTC - 69.195.71[.]174 port 443 - attempts at HTTPS traffic to gjcybzvmvir[.]com
- 2016-01-11 13:11:21 UTC - gjcybzvmvir[.]com - POST /SextTNna6Wv3jB3QFFuBh8deSwHDxkwAQFEMl9xQ.php
- 2016-01-11 13:11:22 UTC - gjcybzvmvir[.]com - GET /SextTNna6Wv3jB3QFFuElhUY.php
- 2016-01-11 13:11:26 UTC - gjcybzvmvir[.]com - POST /SextTNna6Wv3jB3QFFuBh8deSwHDxkwAQFEMl9xQ.php
- 2016-01-11 13:55:01 UTC - 69.195.124[.]60 port 21 - FTP traffic, user: logmanager@iaahouston1[.]com
- 2016-01-11 14:18:09 UTC - 193.111.140[.]236 port 65200 - start of attempted TCP connections (server didn't respond)
POST-INFECTION QBOT ACTIVITY - DNS TRAFFIC:
- 2016-01-11 13:07:46 UTC - DNS query - NS (authoritative name server) - dcbuwccouispn[.]info (No such name)
- 2016-01-11 13:07:56 UTC - DNS query - NS (authoritative name server) - nykoantpydkvsmqqrjtctt[.]info (No such name)
- 2016-01-11 13:08:06 UTC - DNS query - NS (authoritative name server) - uvaphhxjmijvuvobqfezgnc[.]com (Server failure)
- 2016-01-11 13:08:22 UTC - DNS query - NS (authoritative name server) - ljiececesruwqsiaafspjb[.]biz (Server failure)
- 2016-01-11 13:08:38 UTC - DNS query - NS (authoritative name server) - dzgddgiowhm[.]info (No such name)
- 2016-01-11 13:08:49 UTC - DNS query - NS (authoritative name server) - kqcpbgcxbgylzgsadxb[.]org (No such name)
- 2016-01-11 13:08:59 UTC - DNS query - NS (authoritative name server) - qtbtqnuubwzibkriqg[.]org (No such name)
- 2016-01-11 13:09:09 UTC - DNS query - NS (authoritative name server) - dslmkpgjvuisnqa[.]com (No such name)
- 2016-01-11 13:09:19 UTC - DNS query - NS (authoritative name server) - dpsjwmwzuwnicaq[.]biz (No such name)
- 2016-01-11 13:09:29 UTC - DNS query - NS (authoritative name server) - coxrwiuxkcausxnlbgjmakxrw[.]net (No such name)
- 2016-01-11 13:09:39 UTC - DNS query - NS (authoritative name server) - bxlwdhpnkbrmw[.]com (No such name)
- 2016-01-11 13:09:49 UTC - DNS query - NS (authoritative name server) - qtcoickldqbvtrwyfqjflt[.]org (No such name)
- 2016-01-11 13:09:59 UTC - DNS query - NS (authoritative name server) - jutngoyfcngragcdei[.]info (No such name)
- 2016-01-11 13:10:09 UTC - DNS query - NS (authoritative name server) - cenpksygb[.]org (No such name)
- 2016-01-11 13:10:19 UTC - DNS query - NS (authoritative name server) - ripygqgosebdxtmbfbueiixa[.]org (No such name)
- 2016-01-11 13:10:29 UTC - DNS query - NS (authoritative name server) - yqwjvhxgaiszygziq[.]org (No such name)
- 2016-01-11 13:10:40 UTC - DNS query - NS (authoritative name server) - ygjqujokmwmccld[.]org (No such name)
- 2016-01-11 13:54:44 UTC - DNS query - PTR (domain name pointer) - 5.82.164[.]184.in-addr[.]arpa
- 2016-01-11 14:08:45 UTC - DNS query - A (host address) - google[.]com
- 2016-01-11 14:08:59 UTC - DNS query - A (host address) - microsoft[.]com
- 2016-01-11 14:09:14 UTC - DNS query - A (host address) - cnn[.]com
- 2016-01-11 14:16:16 UTC - DNS query - A (host address) - sanjose.speedtest.comcast[.]net
- 2016-01-11 14:16:40 UTC - DNS query - A (host address) - boston.speedtest.comcast[.]net
- 2016-01-11 14:17:04 UTC - DNS query - A (host address) - jacksonville.speedtest.comcast[.]net
- 2016-01-11 14:17:28 UTC - DNS query - A (host address) - houston.speedtest.comcast[.]net
- 2016-01-11 14:17:52 UTC - DNS query - PTR (domain name pointer) - 5.82.164[.]184.in-addr[.]arpa
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2016-01-11-Rig-EK-flash-exploit.swf
File size: 14,191 bytes
MD5 hash: 25c89ea76c405b600345f6418ad53eba
SHA1 hash: b2908859caca1f2f38cd54a8efc0e059ad7a8208
SHA256 hash: 527dc4ff26309ecfb6003ca4fc2d8b5e695c90994baf6f12a30ee5b7727aa43f
Detection ratio (at the time of submission): 4 / 54
First submission to VirusTotal: 2016-01-11 19:47:12 UTC
MALWARE PAYLOAD:
File name: 2016-01-11-Rig-EK-malware-payload-Qbot.exe
File size: 212,992 bytes
MD5 hash: 1dfc0905de2dc77f69a97376f1c02f63
SHA1 hash: 228ba1685199684adcfdf8f272bab88a106b7bcc
SHA256 hash: 020356457e95f7607c1941e03294b4c16e23daa402d7e79cfd2ba91b23969480
Detection ratio (at the time of submission): 11 / 54
First submission to VirusTotal: 2016-01-11 19:47:26 UTC
ANOTHER POST-INFECTION ARTIFACT:
File name: C:\Users\[username]\AppData\Local\Microsoft\roogar.wpl (ASCII C program text)
File size: 9,051 bytes
MD5 hash: fae4b24538aef6bca3959fc3680990c2
SHA1 hash: b8872fcce3d7deff30116dee41cdaa905a26ac68
SHA256 hash: 32663f468165c47a7d898df1f36d6f282ceb63d8544933e0edb87d111b208f91
Detection ratio (at the time of submission): 0 / 52
First submission to VirusTotal: 2016-01-11 19:58:31 UTC
This is another post-infection artifact (ASCII C program text) on the infected host kept persistent by a scheduled task.
Click here to return to the main page.