2016-01-17 - ANGLER EK FROM 31.148.99[.]125 SENDS CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-17-Angler-EK-sends-CryptoWall-ransomware.pcap.zip 678.5 kB (678,450 bytes)
- 2016-01-17-Angler-EK-and-CryptoWall-ransomware-files.zip 509.3 kB (509,330 bytes)
- 2016-01-17-Angler-EK-sends-CryptoWall-ransomware-Snort-events.txt.zip 1.4 kB (1,353 bytes)
- 2016-01-17-Angler-EK-sends-CryptoWall-ransomware-Suricata-events.txt.zip 1.4 kB (1,442 bytes)
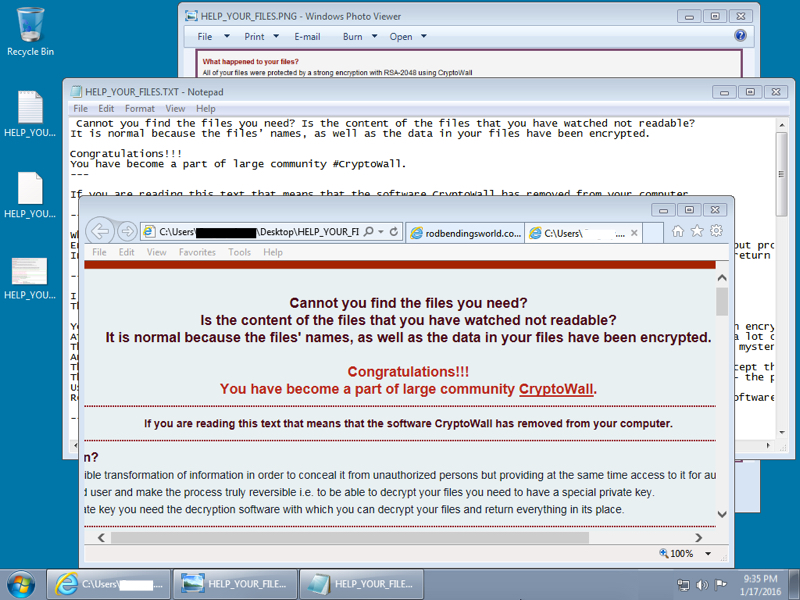
Shown above: Windows desktop after this CryptoWall ransomware infection.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 101.0.76[.]7 port 80 - www.rodbendingsworld[.]com - Compromised website
- 31.148.99[.]125 port 80 - lancharesrhymewis.blaylockwedding[.]com - Angler EK
- 50.63.184[.]249 port 80 - post409[.]org - CryptoWall callback traffic
ADDITIONAL CRYPTOWALL RANSOMWARE DOMAINS FROM MALWR ANALYSIS:
- 125.214.74[.]70 port 80 - gjscomputerservices[.]com[.]au
- 195.93.153[.]7 port 80 - aglobal[.]kz
- 66.71.129[.]2 port 80 - obiettivoalluminio[.]it
- 185.68.16[.]13 port 80 - ilovesport.kiev[.]ua
- apbinary[.]tk - [did not resolve in DNS]
DOMAINS FROM THIS CRYPTOWALL RANSOMWARE SAMPLE'S DECRYPT INSTRUCTIONS:
- 3wzn5p2yiumh7akj.waytopaytosystem[.]com
- 3wzn5p2yiumh7akj.malkintop100[.]com
- 3wzn5p2yiumh7akj.belladonnamonna[.]com
- 3wzn5p2yiumh7akj.hiltonpaytoo[.]com
COMPROMISED WEBSITE:
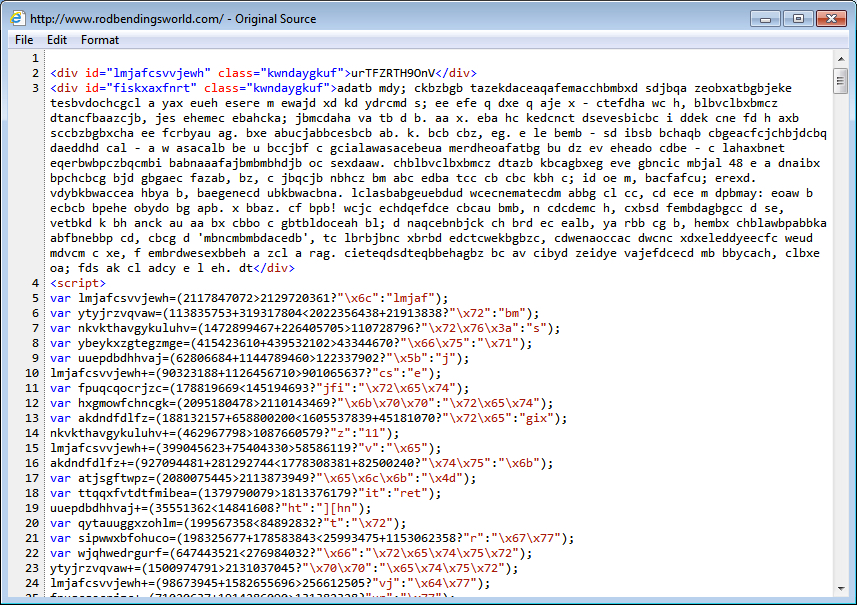
Shown above: Injected script in page from compromised website.
- 2016-01-17 21:25:43 UTC - www.rodbendingsworld[.]com - GET /
ANGLER EK TRAFFIC:
- 2016-01-17 21:25:51 UTC - lancharesrhymewis.blaylockwedding[.]com - GET /forums/search.php?keywords=28&fid0=7yl24915148qs3455992q6.7
- 2016-01-17 21:26:06 UTC - lancharesrhymewis.blaylockwedding[.]com - GET /Mister.wbxml?where=&press=EULn-&dead=ccPG81&across=7i9&pick=
BEmUeSBA&glass=&condition=nngpFzsQ-lXTjo0xcnv8LFb8fQ
- 2016-01-17 21:26:06 UTC - lancharesrhymewis.blaylockwedding[.]com - POST /forums/people.wsdl?hundred=MUDvBDmQ&Mister=&fear=NWv2&county=
hphJsaZ8kIcgwwTFTPP90VmCaVZ95Mg02eAv
- 2016-01-17 21:26:17 UTC - lancharesrhymewis.blaylockwedding[.]com - GET /Mister.wbxml?where=&press=EULn-&dead=ccPG81&across=7i9&pick=
BEmUeSBA&glass=&condition=nngpFzsQ-lXTjo0xcnv8LFb8fQ
- 2016-01-17 21:26:34 UTC - lancharesrhymewis.blaylockwedding[.]com - POST /free.jss?sit=UApbJxpRx3&it=Hn0X7-4X&world=7Nkcrg&in=J4a4oIEuQ&total=
NwPEQ3r0YSps77f
- 2016-01-17 21:27:00 UTC - lancharesrhymewis.blaylockwedding[.]com - GET /police.jsf?she=Lggj&case=&experience=k_uKQ&source=&recently=
kDw8LP3J92&black=&tell=YX1Soe8tYA2eQMvWVSW0tkZbLR-iZ
POST-INFECTION TRAFFIC:
- 2016-01-17 21:28:18 UTC - post409[.]org - POST /8UmXhY.php?r=9svmk5u9qe7l2
- 2016-01-17 21:28:23 UTC - post409[.]org - POST /8UmXhY.php?d=0352z5ryuj
- 2016-01-17 21:28:45 UTC - post409[.]org - POST /8UmXhY.php?t=8w9aq22o63dkjr7
ALERTS
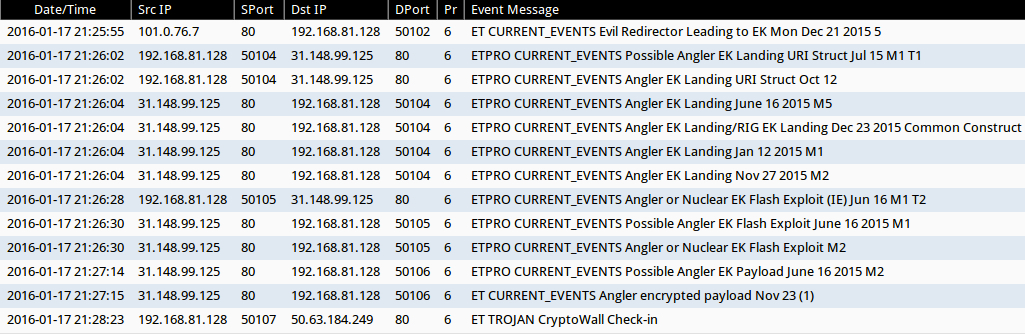
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 101.0.76[.]7 port 80 - ET CURRENT_EVENTS Evil Redirector Leading to EK Mon Dec 21 2015 5 (sid:2022290)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Landing URI Struct Jul 15 M1 T1 (sid:2811993)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing URI Struct Oct 12 (sid:2814318)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing June 16 2015 M5 (sid:2811641)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing/RIG EK Landing Dec 23 2015 Common Construct (sid:2815452)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing Jan 12 2015 M1 (sid:2815727)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing Nov 27 2015 M2 (sid:2815123)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler or Nuclear EK Flash Exploit (IE) Jun 16 M1 T2 (sid:2811829)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Flash Exploit June 16 2015 M1 (sid:2811526)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Angler or Nuclear EK Flash Exploit M2 (sid:2811284)
- 31.148.99[.]125 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Payload June 16 2015 M2 (sid:2811529)
- 31.148.99[.]125 port 80 - ET CURRENT_EVENTS Angler encrypted payload Nov 23 (1) (sid:2022138)
- 50.63.184[.]249 port 80 - ET TROJAN CryptoWall Check-in (sid:2018452)
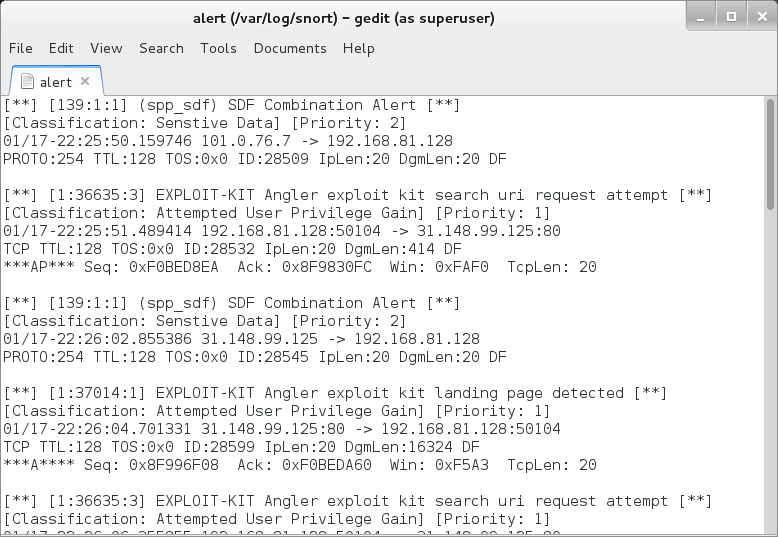
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.8.0 on Debian 7:
- 31.148.99[.]125 port 80 - [1:36635:3] EXPLOIT-KIT Angler exploit kit search uri request attempt
- 31.148.99[.]125 port 80 - [1:37014:1] EXPLOIT-KIT Angler exploit kit landing page detected
- 50.63.184[.]249 port 80 - [1:34318:4] MALWARE-CNC Win.Trojan.CryptoWall variant outbound connection
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2016-01-17-Angler-EK-flash-exploit.swf
File size: 130,068 bytes
MD5 hash: 946d794afc8cb0e8d597180bcf3ae720
SHA1 hash: 2cf84c3ddd400d4acb54214269addb0c8ac58b2c
SHA256 hash: 35a24b00f94125a25279791159059a9bc768e9b4bdea8b71960f82dc117e4aea
Detection ratio: 2 / 54
First submission to VirusTotal: 2016-01-18 16:23:19 UTC
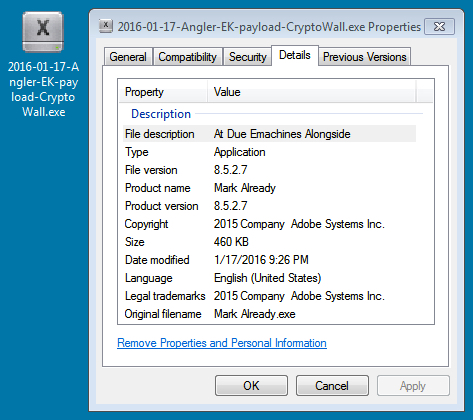
MALWARE PAYLOAD:
File name: 2016-01-17-Angler-EK-payload-CryptoWall-ransomware.exe
File size: 471,552 bytes
MD5 hash: 58006b9382d532f82535454e78c8ad7c
SHA1 hash: c399026473b23a211208a13224029f710458255e
SHA256 hash: 99990573b7c92062663438575d431c5823252a1c523ba9977c2a236ad2484a1e
Detection ratio: 10 / 53
First submission to VirusTotal: 2016-01-18 03:19:24 UTC
Click here to return to the main page.