2016-01-29 - ANGLER EK FROM 5.135.104[.]85 SENDS CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-29-Angler-EK-sends-CryptoWall-ransomware.pcap.zip 1.2 MB (1,153,072 bytes)
- 22016-01-29-Angler-EK-and-CryptoWall-ransomware-files.zip 464.3 kB (464,320 bytes)
TRAFFIC
INFECTION TRAFFIC:
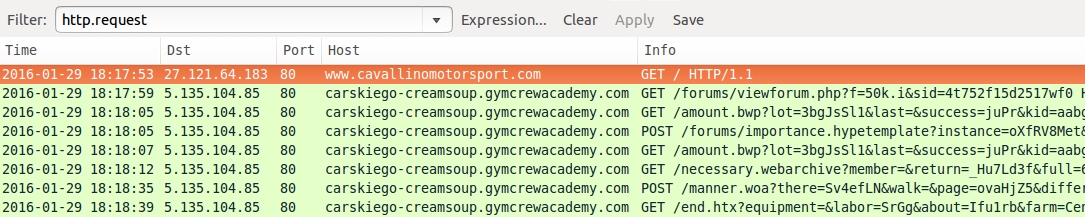
- 27.121.64[.]183 port 80 - www.cavallinomotorsport[.]com - Compromised website
- 5.135.104[.]85 port 80 - carskiego-creamsoup.gymcrewacademy[.]com - Angler EK
IP ADDRESSES AND DOMAINS FOR CALLBACK TRAFFIC FROM CRYPTOWALL RANSOMWARE SAMPLE:
- 5.9.152[.]4 port 80 - wallpapersau[.]net
- 23.95.44[.]180 port 80 - dunwoodypress[.]com
- 23.239.20[.]126 port 80 - vancouverdispensarycoalition[.]ca
- 23.253.242[.]110 port 80 - liberal[.]com[.]mx
- 31.28.166[.]249 port 80 - itt-pushkino[.]org
- 46.28.105[.]79 port 80 - grafitti-photo[.]com
- 46.28.105[.]96 port 80 - daddysground[.]cz
- 46.30.212[.]115 port 80 - yardstickglobal[.]in
- 52.17.164[.]149 port 80 - t-firma-en.itech-websolutions[.]com
- 52.76.5[.]221 port 80 - itvsoft[.]asia
- 54.84.180[.]20 port 80 - calsalumni.iastate.edu.staging.sites.flyinghippo[.]com
- 62.210.148[.]123 port 80 - apptitudes[.]fr
- 65.254.47[.]82 port 80 - hatha[.]it
- 68.171.223[.]109 port 80 - igotocd[.]com
- 69.30.206[.]170 port 80 - apexminerals[.]com[.]au
- 70.32.114[.]99 port 80 - myteaminspired[.]com
- 74.50.31[.]127 port 80 - jjcampbell[.]com
- 77.236.98[.]174 port 80 - vinastudio[.]at
- 79.141.171[.]15 port 80 - neoad[.]de
- 79.143.190[.]57 port 80 - goldenangels[.]com[.]tr
- 81.17.254[.]72 port 80 - premierdisneyvilla[.]com
- 81.88.32[.]191 port 80 - emotionwerbung[.]de
- 81.88.35[.]222 port 80 - emotionwerbung[.]de
- 91.121.103[.]182 port 80 - conseils-finance[.]com
- 91.192.36[.]16 port 80 - bem-bakery[.]com
- 91.212.191[.]167 port 80 - pc.all-to-all[.]com
- 92.222.16[.]214 port 80 - international.woptimo[.]com
- 93.125.99[.]40 port 80 - hand-made[.]by
- 94.23.248[.]80 port 80 - bulksmsdealer[.]com
- 94.113.246[.]147 port 80 - behejbrno[.]com
- 94.156.77[.]8 port 80 - villisplace[.]info
- 101.2.169[.]10 port 80 - aspectdesigns[.]com[.]au
- 103.234.38[.]33 port 80 - giaohang[.]org
- 104.245.232[.]254 port 80 - acmm[.]org[.]au
- 104.28.0[.]24 port 80 - avazuinc[.]com
- 104.28.1[.]24 port 80 - avazuinc[.]com
- 104.28.30[.]51 port 80 - muel.altervista[.]org
- 104.28.31[.]51 port 80 - muel.altervista[.]org
- 107.170.239[.]172 port 80 - mangohills[.]net
- 107.178.108[.]52 port 80 - acie.edu[.]np
- 108.160.148[.]247 port 80 - directoryassistanceamerica[.]com
- 109.237.211[.]174 port 80 - macphoto[.]nl
- 112.78.4[.]229 port 80 - en.theolympiaschools[.]edu[.]vn
- 162.242.155[.]80 port 80 - empiredigitalmarketing[.]com
- 162.243.50[.]143 port 80 - jlprotect[.]ca
- 173.10.110[.]108 port 80 - stevesyachtrepair[.]com
- 178.32.72[.]112 port 80 - london-escorts-agency[.]org[.]uk
- 178.32.72[.]113 port 80 - event-travel[.]co[.]uk
- 178.33.159[.]131 port 80 - ifawindow[.]co[.]uk
- 184.170.245[.]75 port 80 - noahwilbanks[.]com
- 188.166.40[.]166 port 80 - thebesttshirtsonline[.]com
- 192.163.220[.]71 port 80 - edlenimaging[.]com
- 195.154.209[.]137 port 80 - indonesiandomains[.]com
- 195.154.209[.]137 port 80 - jadwalpialadunia[.]in
- 195.154.209[.]137 port 80 - taftee[.]in
- 195.154.209[.]137 port 80 - turbosol[.]asia
- 197.85.182[.]25 port 80 - telecom-sa[.]com
- 198.27.102[.]189 port 80 - thebeautythesis[.]com
- 199.217.118[.]196 port 80 - jogos.testeqi[.]com[.]br
- 200.68.105[.]19 port 80 - monicasalvador[.]com[.]ar
- 202.46.170[.]8 port 80 - larosa[.]com[.]au
- 203.170.80[.]250 port 80 - australianmotorinns[.]com
- 203.189.109[.]152 port 80 - dining-bar[.]com
- 205.234.198[.]60 port 80 - dolphinworld[.]org
- 206.72.195[.]44 port 80 - ihadthat[.]com
- 208.117.9[.]72 port 80 - morainecare[.]com
- 209.190.97[.]210 port 80 - acie.edu.np
- 212.71.250[.]78 port 80 - uzmankirala[.]com
- 216.97.235[.]60 port 80 - jameswbos[.]com
- 217.146.99[.]59 port 80 - zolty[.]eu
- 217.76.132[.]229 port 80 - kskillsmobility[.]eu
- 217.70.180[.]134 port 80 - dentiste-paris-20[.]fr
- 219.122.252[.]2 port 80 - campaignforyoungamerica[.]org
IMAGES
Shown above: Today's pcap filtered in Wireshark.
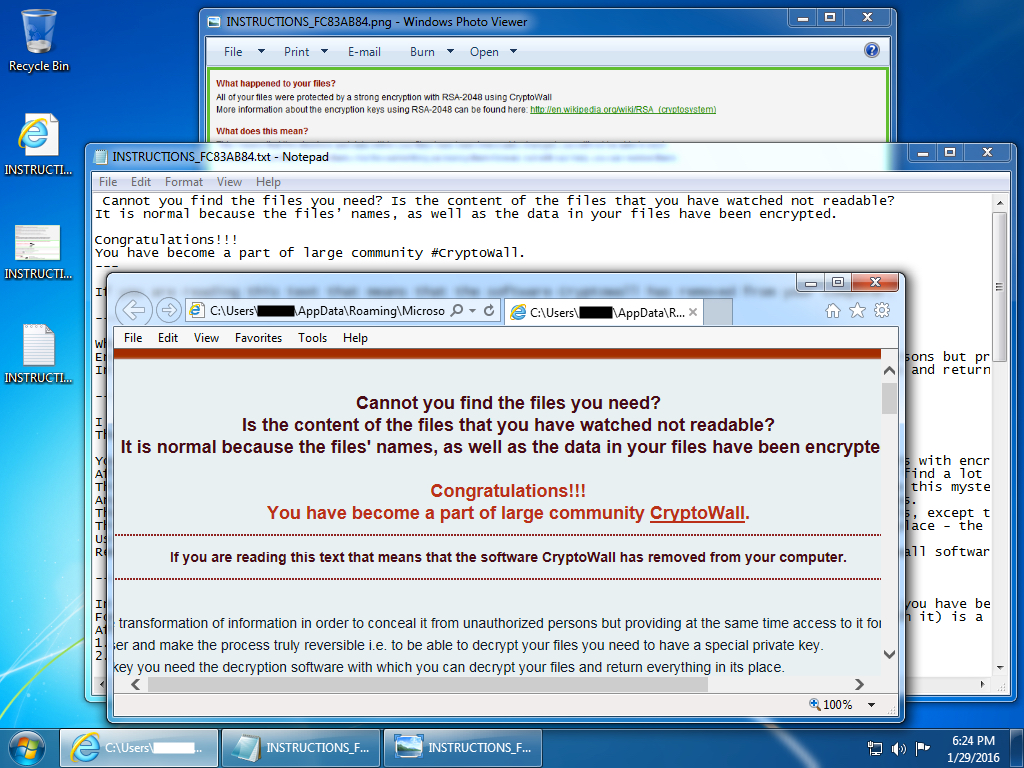
Shown above: Today's CryptoWall ransomware sample infecting a Windows desktop.
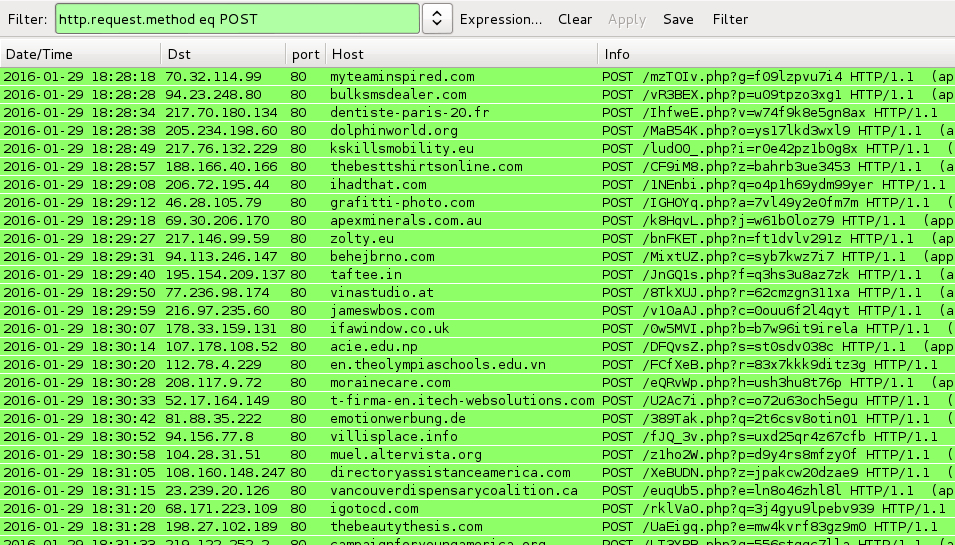
Shown above: CryptoWall ransomware callback traffic when I tested the malware sample.
Click here to return to the main page.