2016-04-27 - LOCKY RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-27-Locky-ransomware-files.zip 398.6 kB (398,645 bytes)
- 2016-04-27-Locky-ransomware-email-tracker.csv (3,534 bytes)
- 2016-04-27-Locky-ransomware-infection.pcap (200,735 bytes)
- attachments/
- attachments/019D5_richard_E89FD5.rar (1,685 bytes)
- attachments/5D77E_craig_DE2B6B.rar (1,683 bytes)
- attachments/ACDD4_linda_7E9306.rar (1,674 bytes)
- attachments/AEAE2_gage_F71707.rar (1,691 bytes)
- attachments/craig-client_bill_F85DFB.rar (1,692 bytes)
- attachments/E9EB4_richard_FFEAEB.rar (1,688 bytes)
- attachments/jennifer-bill_BAD28D.rar (1,679 bytes)
- attachments/jennifer-client_bill_AEB977.rar (1,684 bytes)
- attachments/linda-bill_0DDC3B.rar (1,685 bytes)
- attachments/linda-bill_63B29F.rar (1,686 bytes)
- attachments/patricia-client_bill_889605.rar (1,685 bytes)
- attachments/richard-bill_3DEF40.rar (1,675 bytes)
- attachments/richard-bill_67FE66.rar (1,687 bytes)
- attachments/richard-bill_E937AC.rar (1,676 bytes)
- attachments/richard-client_bill_052E85.rar (1,679 bytes)
- attachments/timmy-client_bill_9A5FC4.rar (1,682 bytes)
- emails/
- emails/2016-04-27-1020-UTC.eml (3,924 bytes)
- emails/2016-04-27-1023-UTC.eml (3,945 bytes)
- emails/2016-04-27-1051-UTC.eml (3,969 bytes)
- emails/2016-04-27-1057-UTC.eml (3,955 bytes)
- emails/2016-04-27-1101-UTC.eml (3,986 bytes)
- emails/2016-04-27-1103-UTC.eml (4,001 bytes)
- emails/2016-04-27-1109-UTC.eml (3,958 bytes)
- emails/2016-04-27-1111-UTC.eml (3,955 bytes)
- emails/2016-04-27-1116-UTC.eml (3,974 bytes)
- emails/2016-04-27-1119-UTC.eml (3,930 bytes)
- emails/2016-04-27-1120-UTC.eml (3,962 bytes)
- emails/2016-04-27-1121-UTC.eml (4,013 bytes)
- emails/2016-04-27-1122-UTC.eml (3,929 bytes)
- emails/2016-04-27-1123-UTC.eml (3,994 bytes)
- emails/2016-04-27-1126-UTC.eml (3,950 bytes)
- emails/2016-04-27-1151-UTC.eml (3,972 bytes)
- extracted-js-files/
- extracted-js-files/01c4b975.js (3,311 bytes)
- extracted-js-files/048a35.js (3,319 bytes)
- extracted-js-files/298ba6d.js (3,306 bytes)
- extracted-js-files/2e1226.js (3,300 bytes)
- extracted-js-files/4e5036c3.js (3,317 bytes)
- extracted-js-files/6d5e6a.js (3,300 bytes)
- extracted-js-files/9b2129a0.js (3,308 bytes)
- extracted-js-files/9f6ed08.js (3,312 bytes)
- extracted-js-files/af18f.js (3,303 bytes)
- extracted-js-files/bac9b964.js (3,298 bytes)
- extracted-js-files/c0c0e1c.js (3,311 bytes)
- extracted-js-files/c225e93.js (3,312 bytes)
- extracted-js-files/cc22f6bf.js (3,305 bytes)
- extracted-js-files/cf7f9.js (3,309 bytes)
- extracted-js-files/ecdbe.js (3,316 bytes)
- Locky-ransomware-files-from-an-infected-host/
- Locky-ransomware-files-from-an-infected-host/2016-04-27-Locky-ransomware.exe (179,200 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-27-Locky-ransomware_HELP_instructions.bmp (3,864,030 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-27-Locky-ransomware_HELP_instructions.txt (1,121 bytes)
NOTES:
- Emails pushing Locky ransomware are really coming in today...
- This is the same wave of emails pushing Locky ransomware that was reported in Dynamoo's blog ( link ).
- In addition to Dynamoo's wave, today I saw different subject lines used for other waves of email pushing Locky ransomware.
THE EMAILS
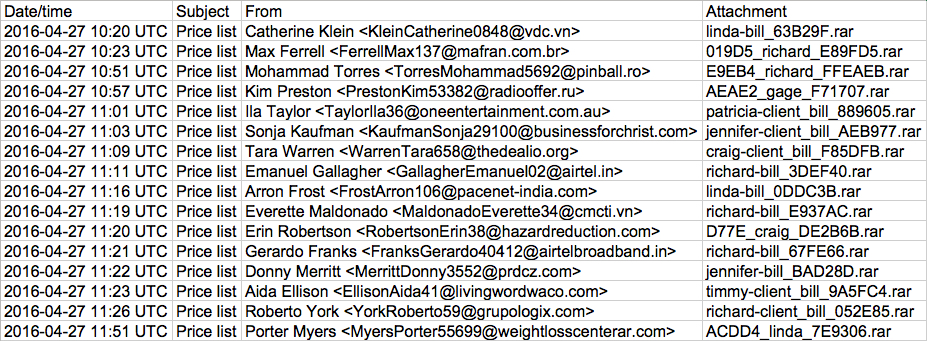
Shown above: Data on 16 of emails from this wave of emails pushing Locky ransomware.
DESCRIPTION:
- Sender: Various senders
- Subject: Price list
- Attachment: .rar archive containing a malicious .js file
TEXT OF THE MESSAGES:
Thank you. Our latest price list is attached. For additional information, please contact your local ITT office.
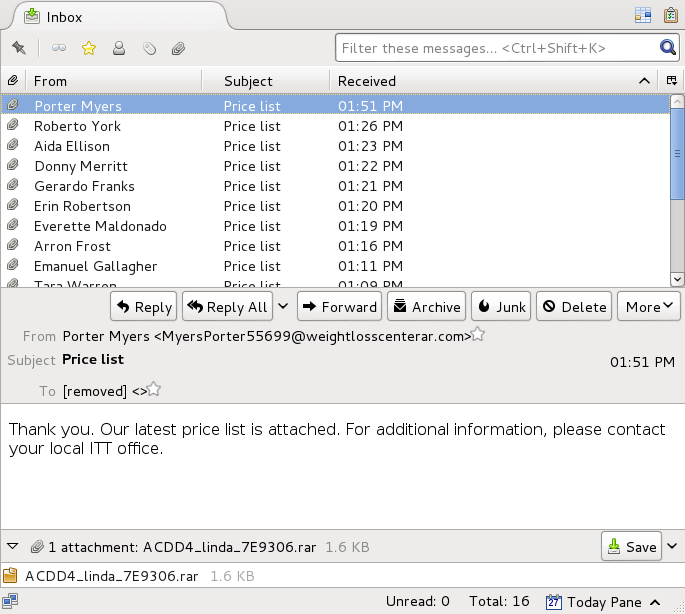
Shown above: An example of the messages from this wave of emails pushing Locky ransomware.
THE ATTACHMENTS
(Read: Attachment name -- Extracted .js file -- HTTP GET request from the .js file)
- linda-bill_63B29F.rar -- ecdbe.js -- aaacollectionsjewelry[.]com - GET /ur8fgs
- 019D5_richard_E89FD5.rar -- 9f6ed08.js -- myehelpers[.]com - GET /j3ykf
- E9EB4_richard_FFEAEB.rar -- 01c4b975.js -- soccerinsider[.]net - GET /mys3ks
- AEAE2_gage_F71707.rar -- 4e5036c3.js -- warcraft-lich-king[.]ru - GET /i4ospd
- patricia-client_bill_889605.rar -- cc22f6bf.js -- lbbc[.]pt - GET /n8wisd
- jennifer-client_bill_AEB977.rar -- c225e93.js -- pediatriayvacunas[.]com - GET /q0wps
- craig-client_bill_F85DFB.rar -- 048a35.js -- onlinecrockpotrecipes[.]com - GET /k2tspa
- richard-bill_3DEF40.rar -- 6d5e6a.js -- lbbc[.]pt - GET /n8wisd
- linda-bill_0DDC3B.rar -- c0c0e1c.js -- mavrinscorporation[.]ru - GET /hd7fs
- richard-bill_E937AC.rar -- 2e1226.js -- jurang[.]tk - GET /n2ysk
- D77E_craig_DE2B6B.rar -- cf7f9.js -- directenergy[.]tv - GET /l2isd
- richard-bill_67FE66.rar -- af18f.js -- rayzan24[.]co - GET /m3usjd
- jennifer-bill_BAD28D.rar -- 298ba6d.js -- directenergy[.]tv - GET /l2isd
- timmy-client_bill_9A5FC4.rar -- 9b2129a0.js -- games-k[.]ru - GET /n8eis
- richard-client_bill_052E85.rar -- 298ba6d.js -- directenergy[.]tv - GET /l2isd
- ACDD4_linda_7E9306.rar -- bac9b964.js -- lbbc[.]pt - GET /n8wisd
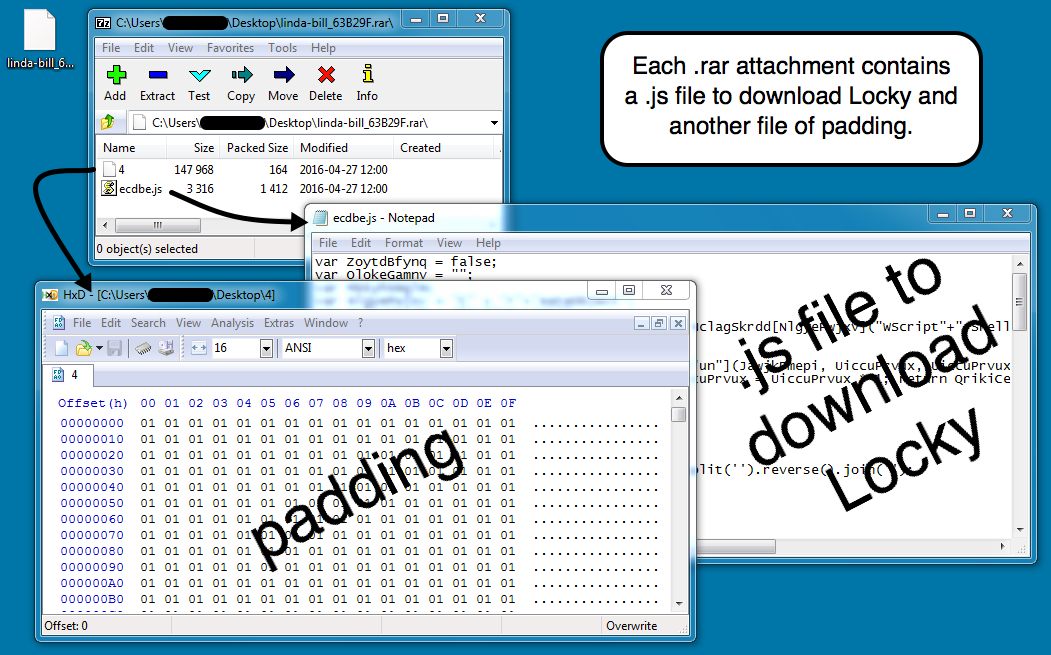
Shown above: Contents from one of the .rar attachments.
TRAFFIC
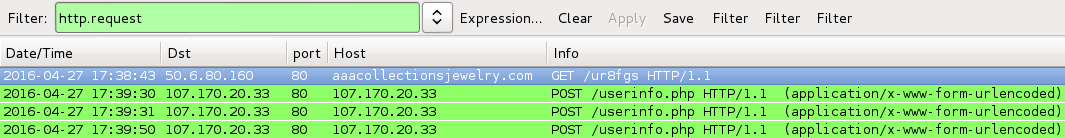
Shown above: Traffic filtered in Wireshark after infecting a Windows host with one of the .js files.
HTTP REQUESTS:
- 2016-04-27 17:38:43 UTC - 50.6.80[.]160 port 80 - aaacollectionsjewelry[.]com GET /ur8fgs
- 2016-04-27 17:39:30 UTC - 107.170.20[.]33 port 80 - 107.170.20[.]33 - POST /userinfo.php
- 2016-04-27 17:39:31 UTC - 107.170.20[.]33 port 80 - 107.170.20[.]33 - POST /userinfo.php
- 2016-04-27 17:39:50 UTC - 107.170.20[.]33 port 80 - 107.170.20[.]33 - POST /userinfo.php
IMAGES
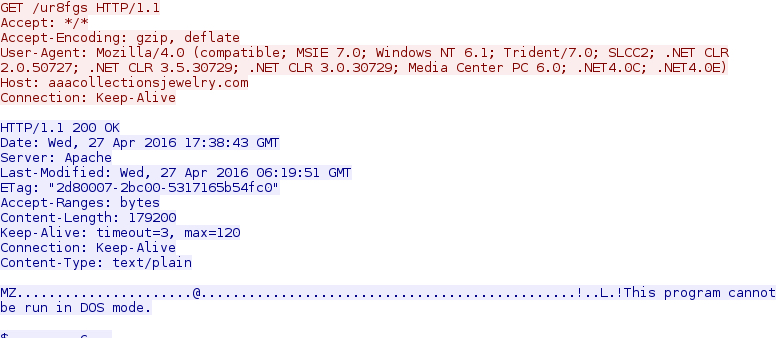
Shown above: HTTP GET request for the Locky ransomware.
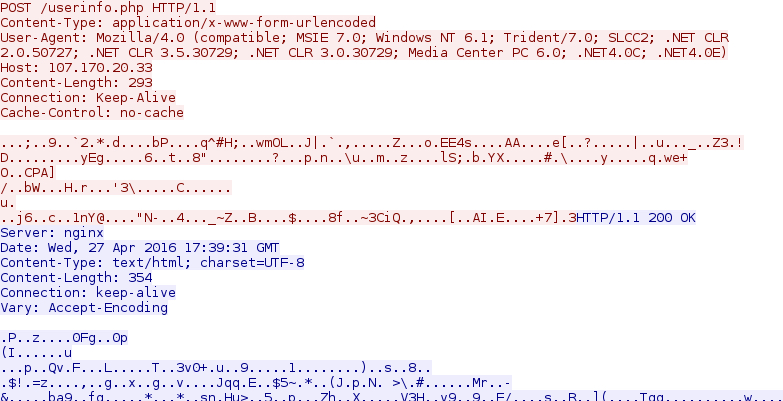
Shown above: Locky ransomware post-infection traffic.
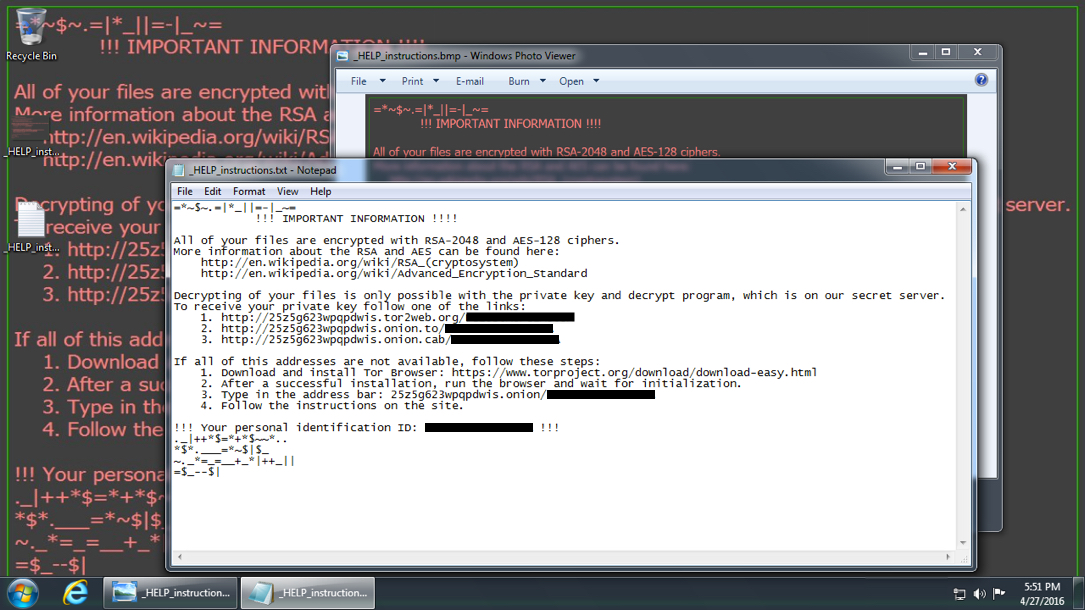
Shown above: The host's desktop after being infected with Locky ransomware.
Click here to return to the main page.
