2016-04-29 - ANGLER AND NEUTRINO EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-29-Angler-and-Neutrino-EK-data-dump-8-pcaps.zip 13.5 MB (13,527,048 bytes)
- 2016-04-29-Angler-and-Neutrino-EK-data-dump-malware-and-artifacts.zip 3.2 MB (3,224,778 bytes)
NOTES:
There's too much to write about in detail for each of the pcaps. Today's post has four pcaps with EITest Angler EK (a different payload each time), two pcaps with pseudo-Darkleech Angler EK sending Bedep and CryptXXX ransomware, and two pcaps with Neutrino EK sending something else. You'll have to review the pcaps for details.
- Background on the EITest campaign can be found here.
- Background on the pseudo-Darkleech campaign is available here.
- Proofpoint's blog on Angler EK spreading CryptXXX ransomware can be found here.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections is located here.
Two other items...
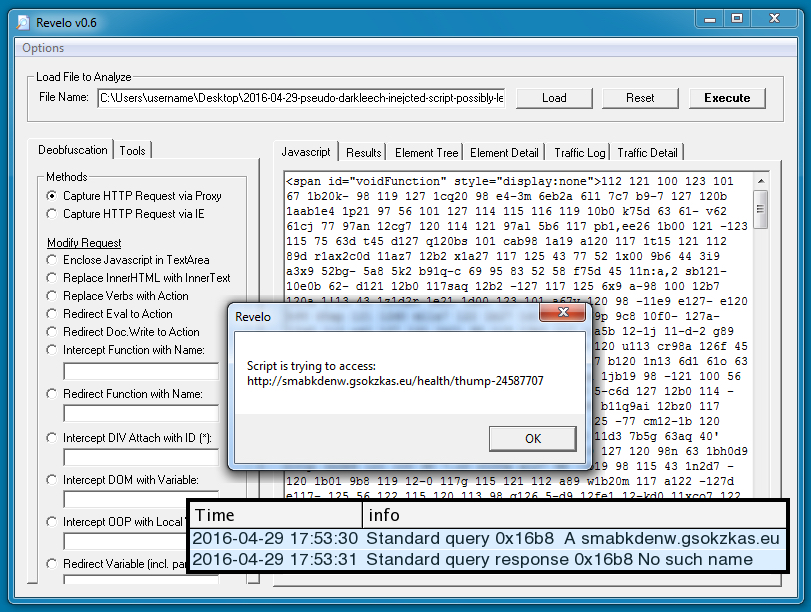
ITEM 1: The past day or two, I've seen a few examples of injected pseudo-Darkleech script point to .eu domains, but they don't go anywhere. Why? Because the domain is not resolved in DNS. Here's an example:
Whenever I've seen pseudo-Darkleech script generate a URL with an .eu domain, it never works. And the URLs using those .eu domains look a little like Neutrino EK. I can't say if they actually are Neutrino EK, though. I suppose I'll figure it out if those domains ever start resolving.
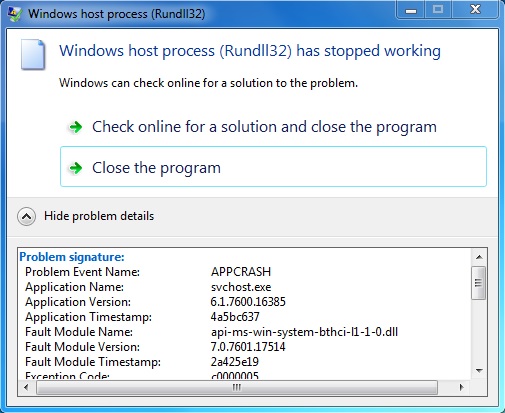
ITEM 2: In today's two Angler EK/Bedep/CryptXXX infections, svchost.exe was dropped in the same folder with the CryptXXX ransomware .dll. For example:
- C:\Users\[username]\AppData\Local\Temp\{89699C55-6CDA-4C22-A60F-5DB51EE71726}\api-ms-win-system-bthci-l1-1-0.dll
- C:\Users\[username]\AppData\Local\Temp\{89699C55-6CDA-4C22-A60F-5DB51EE71726}\svchost.exe
That svchost.exe is actually rundll32.exe. It's a legitimate Windows file (VirusTotal link). But in this case, it's being used to load the CryptXXX ransomware .dll file. I got an error during today's first CryptXXX ransomware infection on a 64-bit Windows host. I didn't see an error during the second infection on a 32-bit host.
In both cases, the CryptXXX ransomware .dll file wasn't deleted like it normally is. Except for TCP port 443 callback traffic associated with CryptXXX ransomware, I didn't find any other signs of CryptXXX on the two infected hosts. The click-fraud traffic normally seen after Bedep still seemed normal, though.
CONTENTS OF TODAY'S ZIP ARCHIVES
EIGHT PCAPS IN THE PCAP ARCHIVE:
- 2016-04-28-EITest-Angler-EK-first-run.pcap (997,009 bytes)
- 2016-04-28-EITest-Angler-EK-second-run.pcap (951,877 bytes)
- 2016-04-28-EITest-Angler-EK-third-run.pcap (4,225,141 bytes)
- 2016-04-29-EITest-Angler-EK.pcap (1,006,368 bytes)
- 2016-04-29-Neutrino-EK-first-run.pcap (1,890,676 bytes)
- 2016-04-29-Neutrino-EK-second-run.pcap (844,973 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-first-run.pcap (3,091,933 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-second-run.pcap (3,069,963 bytes)
ITEMS IN THE MALWARE AND ARTIFACTS ARCHIVE:
- 2016-04-28-EITest-Angler-EK-flash-exploit.swf (54,445 bytes)
- 2016-04-28-EITest-Angler-EK-landing-page-first-run.txt (69,668 bytes)
- 2016-04-28-EITest-Angler-EK-landing-page-second-run.txt (91,196 bytes)
- 2016-04-28-EITest-Angler-EK-landing-page-third-run.txt (91,222 bytes)
- 2016-04-28-EITest-Angler-EK-payload-first-run.dll (167,936 bytes)
- 2016-04-28-EITest-Angler-EK-payload-second-run.exe (266,449 bytes)
- 2016-04-28-EITest-Angler-EK-payload-third-run.exe (155,648 bytes)
- 2016-04-28-EITest-flash-file-used-in-gate-traffic-also-seen-on-2016-04-29.swf (15,596 bytes)
- 2016-04-28-and-29-EITest-Angler-EK-extracted-DLL-from-silverlight-exploit.dll (209,408 bytes)
- 2016-04-28-and-29-EITest-Angler-EK-silverlight-exploit.xap (169,132 bytes)
- 2016-04-29-EITest-Angler-EK-flash-exploit.swf (54,495 bytes)
- 2016-04-29-EITest-Angler-EK-landing-page.txt (91,226 bytes)
- 2016-04-29-EITest-Angler-EK-payload.exe (295,688 bytes)
- 2016-04-29-Neutrino-EK-flash-exploit-first-run.swf (72,211 bytes)
- 2016-04-29-Neutrino-EK-flash-exploit-second-run-1-of-2.swf (71,161 bytes)
- 2016-04-29-Neutrino-EK-flash-exploit-second-run-2-of-2.swf (71,161 bytes)
- 2016-04-29-Neutrino-EK-landing-page-first-run.txt (1,038 bytes)
- 2016-04-29-Neutrino-EK-landing-page-second-run.txt (972 bytes)
- 2016-04-29-Neutrino-EK-payload-both-runs.exe (300,544 bytes)
- 2016-04-29-page-from-mamaok_pl-with-injected-pseudo-Darkleech-script.txt (646,564 bytes)
- 2016-04-29-page-from-yoursdental_in-with-injected-pseudo-Darkleech-script.txt (40,232 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-CryptXXX-ransomware-first-run.dll (619,520 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-CryptXXX-rasomware-run.dll (338,944 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-click-fraud-malware-first-run.dll (421,536 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-click-fraud-malware-second-run.dll (311,296 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-flash-exploit-both-runs.swf (66,918 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-landing-page-first-run.txt (91,228 bytes)
- 2016-04-29-pseudo-Darkleech-Angler-EK-landing-page-second-run.txt (91,234 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
- 85.93.0[.]68 port 80 - bexythy[.]tk - EITest gate on 2016-04-28
- 85.93.0[.]68 port 80 - biinee[.]tk - EITest gate on 2016-04-29
- 185.141.25[.]161 port 80 - vln0z.t54grp0l[.]top - Angler EK [EITest]
- 185.117.73[.]114 port 80 - mnqt.ba1qc2jiu[.]top - Angler EK [EITest]
- 185.117.73[.]116 port 80 - u2j.gm7pi4x[.]top and bry8ei.uagd6ekm[.]top - Angler EK [EITest]
- 85.25.107[.]219 port 80 - deskevichescotty.cubabarrelshipping[.]com - Angler EK [pseudo-Darkleech]
- 188.138.57[.]69 port 80 - csfcunreturningly.cubashipping[.]net - Angler EK [pseudo-Darkleech]
- 45.32.156[.]88 port - rtuqmdjr.afthis[.]top and drejzeyok.afthis[.]top - Neutrino EK [first time]
- 45.32.156[.]88 port - hfqmww.afthis[.]top and jolouc.afthis[.]top - Neutrino EK [second time]
- Various IP addresses and domains for the callback traffic. Review the pcaps for details.
Click here to return to the main page.