2016-05-16 - EITEST ANGLER EK FROM 185.117.75[.]131 SENDS RAMNIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-16-EITest-Angler-EK-2-pcaps.zip 2.4 MB (2,410,612 bytes)
- 2016-05-16-EITest-Angler-EK-first-run.pcap (604,185 bytes - no infection)
- 2016-05-16-EITest-Angler-EK-second-run.pcap (2,145,231 bytes - infection)
- 2016-05-16-EITest-Angler-EK-artifacts-and-malware.zip 581.5 kB (581,499 bytes)
- 2016-05-16-EITest-Angler-EK-flash-exploit-first-run.swf (54,489 bytes)
- 2016-05-16-EITest-Angler-EK-flash-exploit-second-run.swf (31,028 bytes)
- 2016-05-16-EITest-Angler-EK-landing-page-first-run.txt (66,373 bytes)
- 2016-05-16-EITest-Angler-EK-landing-page-second-run.txt (77,963 bytes)
- 2016-05-16-EITest-Angler-EK-payload-ramnit.exe (334,080 bytes)
- 2016-05-16-EITest-Angler-EK-silverlight-exploit.zip (169,132 bytes)
- 2016-05-16-EITest-flash-redirector-from-ip.iphistory_co_uk.swf (15,540 bytes)
- 2016-05-16-page-from-prg.usp_br-with-injected-EITest-script-first-run.txt (59,861 bytes)
- 2016-05-16-page-from-prg.usp_br-with-injected-EITest-script-second-run.txt (60,128 bytes)
NOTES:
- Background on the EITest campaign is available here.
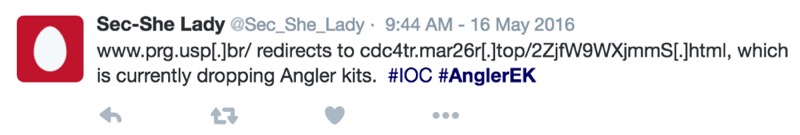
- Shout out to @Sec_She_Lady for originally tweeting the #AnglerEK #IOC that led to this blog entry.
Shown above: Tweet that allowed me to generate today's infection.
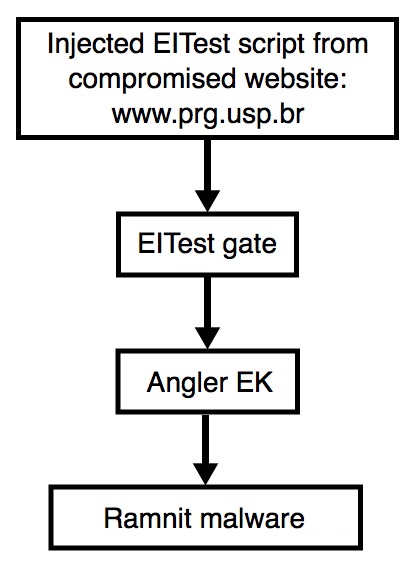
Shown above: Chain of events for today's infection.
TRAFFIC
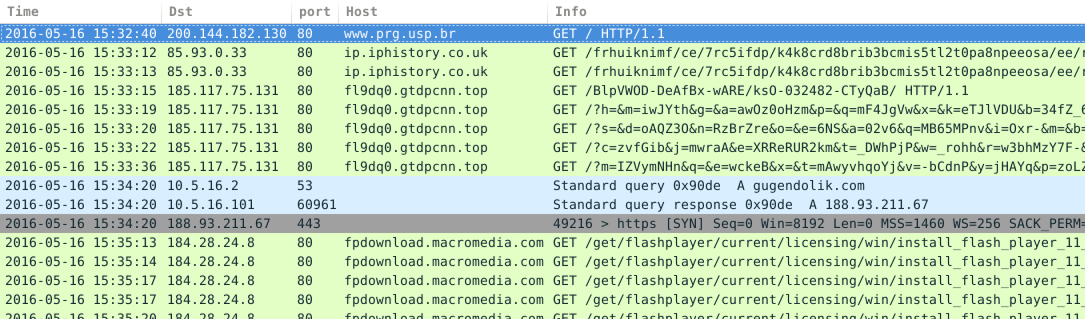
Shown above: Second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 85.93.0[.]33 port 80 - ip.iphistory[.]co[.]uk - EITest gate
- 185.117.75[.]131 port 80 - fl9dq0.gtdpcnn[.]top - Angler EK
- 188.93.211[.]67 port 443 - gugendolik[.]com - Ramnit post-infection traffic (encrypted) - Second pcap only
IMAGES
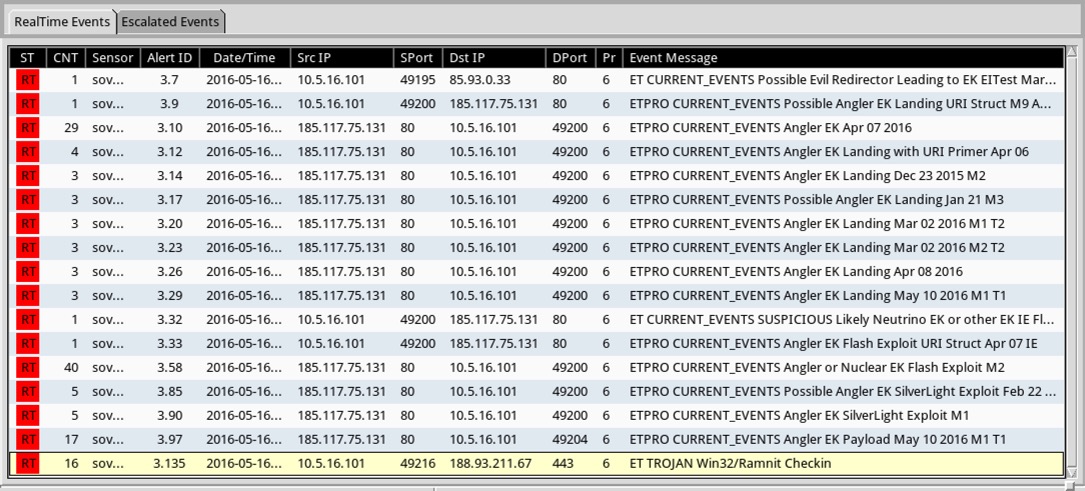
Shown above: Alerts from Security Onion for the second pcap using Suricata and the EmergingThreats Pro signature set.
Click here to return to the main page.