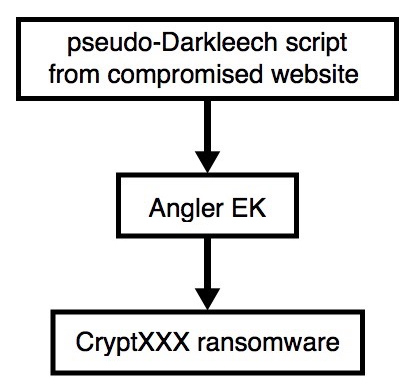
2016-06-01 - PSEUDO-DARKLEECH ANGLER EK SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-01-pseudoDarkleech-Angler-EK-7-pcaps.zip 8.1 MB (8,063,689 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-hideandseek.leadconcept_net.pcap (1,437,366 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-infinitepowersolutions_com.pcap (1,472,747 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-joellipman_com.pcap (1,457,125 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-lidcombeprogram_org.pcap (1,023,667 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-medicalandspa_com.pcap (1,403,339 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-northpoleitalia_it.pcap (717,042 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-after-oilsofjoy_us.pcap (1,341,960 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-malware-and-artifacts.zip 930.0 kB (930,026 bytes)
- 2016-06-01-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-01-CryptXXX-ransomware-decrypt-instructions.html (5,715 bytes)
- 2016-06-01-CryptXXX-ransomware-decrypt-instructions.txt (987 bytes)
- 2016-06-01-page-from-hideandseek.leadconcept_net-with-injected-pseudoDarkleech-script.txt (99,731 bytes)
- 2016-06-01-page-from-infinitepowersolutions_com-with-injected-pseudoDarkleech-script.txt (70,049 bytes)
- 2016-06-01-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (84,572 bytes)
- 2016-06-01-page-from-lidcombeprogram_org-with-injected-pseudoDarkleech-script.txt (68,013 bytes)
- 2016-06-01-page-from-medicalandspa_com-with-injected-pseudoDarkleech-script.txt (26,326 bytes)
- 2016-06-01-page-from-northpoleitalia_it-with-injected-pseudoDarkleech-script.txt (29,037 bytes)
- 2016-06-01-page-from-oilsofjoy_us-with-injected-pseudoDarkleech-script.txt (57,209 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-flash-exploit-sample-1-of-2.swf (40,836 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-flash-exploit-sample-2-of-2.swf (40,825 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-hideandseek.leadconcept_net.txt (102,228 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-infinitepowersolutions_com.txt (102,222 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-joellipman_com.txt (102,236 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-lidcombeprogram_org.txt (102,220 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-medicalandspa_com.txt (102,270 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-oilsofjoy_us.txt (102,248 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-landing-page-after-northpoleitalia_it.txt (102,184 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-payload-CryptXXX-ransomware-sample-1-of-2.dll (507,392 bytes)
- 2016-06-01-pseudoDarkleech-Angler-EK-payload-CryptXXX-ransomware-sample-2-of-2.dll (204,800 bytes)
NOTES:
- Captured 7 pcaps of Angler exploit kit (EK) caused by the pseudoDarkleech campaign.
- This shows how the domains and IP addresses change, but also how the malware generally stays the same.
- Today the pseudoDarkleech campaign switched from Angler EK --> Bedep --> CryptXXX ransomware back to Angler EK --> CryptXXX ransomware.
SOME HISTORY ON PSEUDO-DARKLEECH AND CRYPTXXX RANSOMWARE:
- On 2016-03-22, PaloAlto Networks posted a blog that provides background on the pseudoDarkleech campaign (link).
- On 2016-04-23, I posted an ISC diary about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX ransomware infections (link).
- On 2016-04-28, PaloAlto Networks reported another campaign called "Afraidgate" had switched from Locky ramsomware to delivering CryptXXX ransomware (link).
- On 2016-05-09, Proofpoint issued another report on CryptXXX, now at version 2.0 (link).
- On 2016-05-24, BleepingComputer reported CryptXXX ransomware was updated to version 3.0 (link) two days before I saw it on 2016-05-26 (link).
Shown above: PseudoDarkleech campaign is back to this again.
TRAFFIC
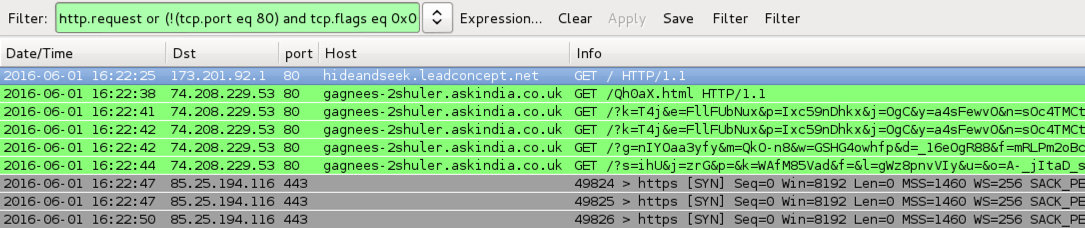
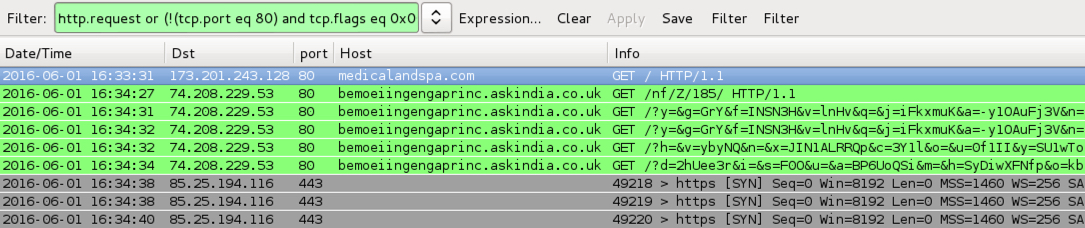
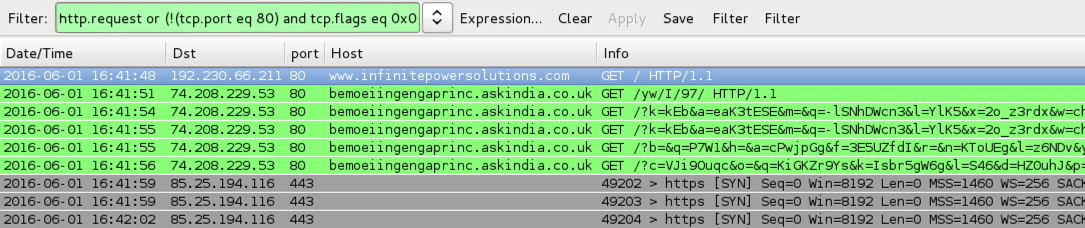
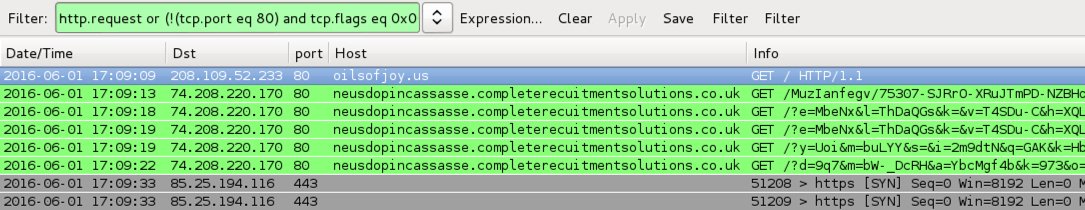
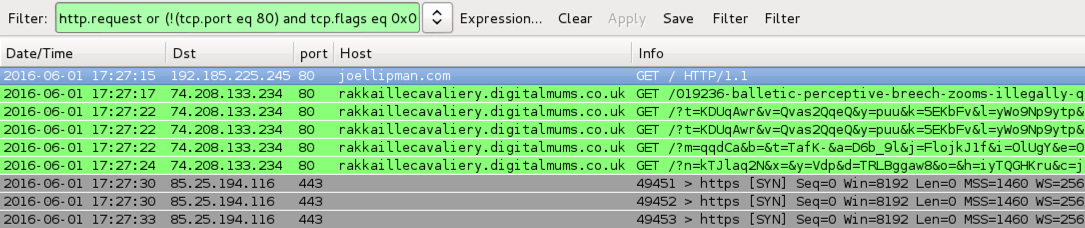
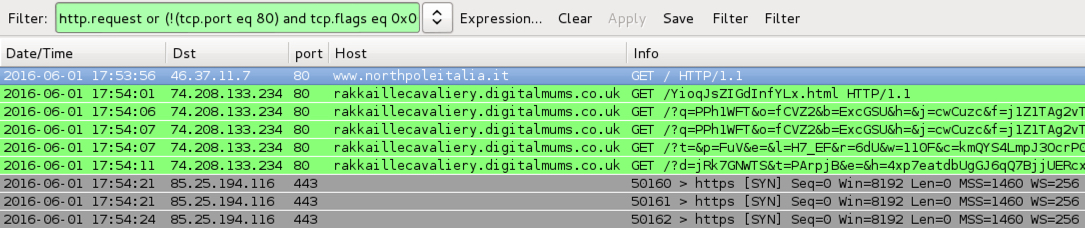
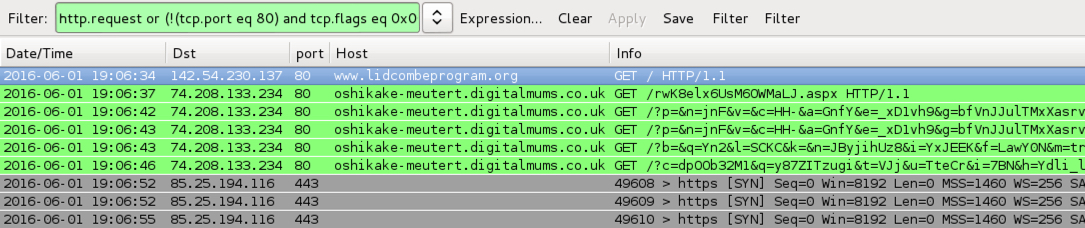
Shown above: Traffic from the pcaps filtered in Wireshark using the filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- hideandseek.leadconcept[.]net - Compromised website
- 16:22 UTC - 74.208.229[.]53 port 80 - gagnees-2shuler.askindia[.]co[.]uk - Angler EK
- CryptXXX ransomware sample 1 of 2
- medicalandspa[.]com - Compromised website
- 16:34 UTC - 74.208.229[.]53 port 80 - bemoeiingengaprinc.askindia[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 1 of 2
- www.infinitepowersolutions[.]com - Compromised website
- 16:41 UTC - 74.208.229[.]53 port 80 - bemoeiingengaprinc.askindia[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 1 of 2
- oilsofjoy[.]us - Compromised website
- 17:09 UTC - 74.208.220[.]170 port 80 - neusdopincassasse.completerecuitmentsolutions[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 1 of 2
- joellipman[.]com - Compromised website
- 17:27 UTC - 74.208.133[.]234 port 80 - rakkaillecavaliery.digitalmums[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 1 of 2
- www.northpoleitalia[.]it - Compromised website
- 17:54 UTC - 74.208.133[.]234 port 80 - rakkaillecavaliery.digitalmums[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 1 of 2
- www.lidcombeprogra[m].org - Compromised website
- 19:06 UTC - 74.208.133[.]234 port 80 - oshikake-meutert.digitalmums[.]co[.]uk - Angler EK
- Angler EK payload: CryptXXX ransomware sample 2 of 2
POST-INFECTION TRAFFIC:
- 85.25.194[.]116 port 443 - CryptXXX ransomware callback traffic, custom encoding
Click here to return to the main page.